
SIEM stands for Security Information and Event Management (SIEM).
SIEM solutions provide a holistic view of what is happening on a network in real-time and help IT teams to be more proactive in the fight against security threats.

Introduction
Security information and event management (SIEM) is an approach that offers observability over an organization’s information security. By combining SIM (security information management) and SEM (security event management), it aims to aggregate log data across users, machines, and servers for real-time event log monitoring and correlations to find security threats and mitigate risks in real-time.
Notable Acronyms and Parts of SIEM
The acronyms SEM, SIM and SIEM have sometimes been used interchangeably, but generally refer to the different primary focus of products:
- Log management: Focus on simple collection and storage of log messages and audit trails
- Security information management (SIM): Long-term storage as well as analysis and reporting of log data.
- Security event manager (SEM): Real-time monitoring, correlation of events, notifications and console views.
- Security information and event management (SIEM): Combines SIM and SEM and provides real-time analysis of security alerts generated by network hardware and applications.
- Managed Security Service: (MSS) or Managed Security Service Provider: (MSSP): The most common managed services appear to evolve around connectivity and bandwidth, network monitoring, security, virtualization, and disaster recovery.
- Security as a service (SECaaS): These security services often include authentication, anti-virus, anti-malware/spyware, intrusion detection, Penetration testing and security event management, among others.
What is SIEM?
A key challenge in the realm of computer security is that cyber attacks are continually evolving as well as the race to prevent them. It is impossible to automate all security systems in advance of attacks and remove human involvement in security analysis retroactively.
SIEM is evolving in system security that incorporates all of the above mentioned technologies: Log Management Systems, Security Event Management, Security Information Management and Security Event Correlation. As these various security components became increasingly integrated and merged over the years, SIEM emerged as the generalized industry term for managing information generated from combined security infrastructure and controls.
There is also a movement from traditional on-premise SIEM solutions as organizations infrastructure and applications moved to the cloud and multi-cloud.
SIEM technology has been in existence for more than a decade, initially evolving from the log management discipline. It combined security event management (SEM) – which analyzes log and event data in real time to provide threat monitoring, event correlation and incident response – with security information management (SIM) which collects, analyzes and reports on log data.
Who is SIEM for?
One could get very lost in the weeds with all these security acronyms so it might be helpful to focus on who SIEM is for.
- Security Team – Primarily SIEM solutions primary users are the security personnel in your organization that gives them all the information, alerts and automation necessary to be two steps ahead of online threats.
- Operations Team – SRE, DevOps and your operations team also benefit from SIEM tools to get the company operations back online and back to business as usual. They need access to logs, events, security incidents to figure out the root cause and resolve issues as quickly as possible.
- Compliance Team – The handling of data has a growing number of rules from industry and government regulation (GDPR, HIPAA, PCI to name a few)
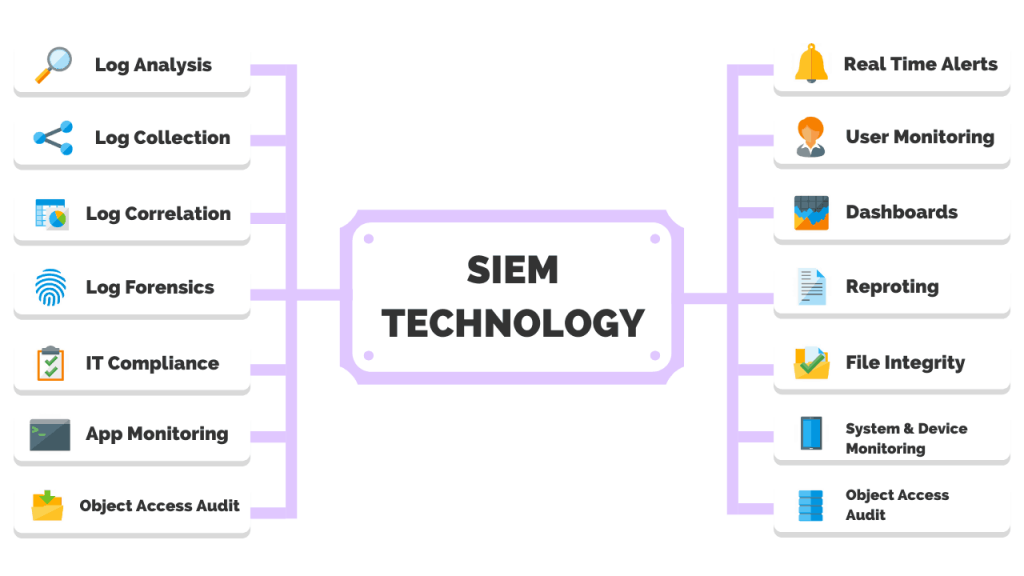
SIEM Components
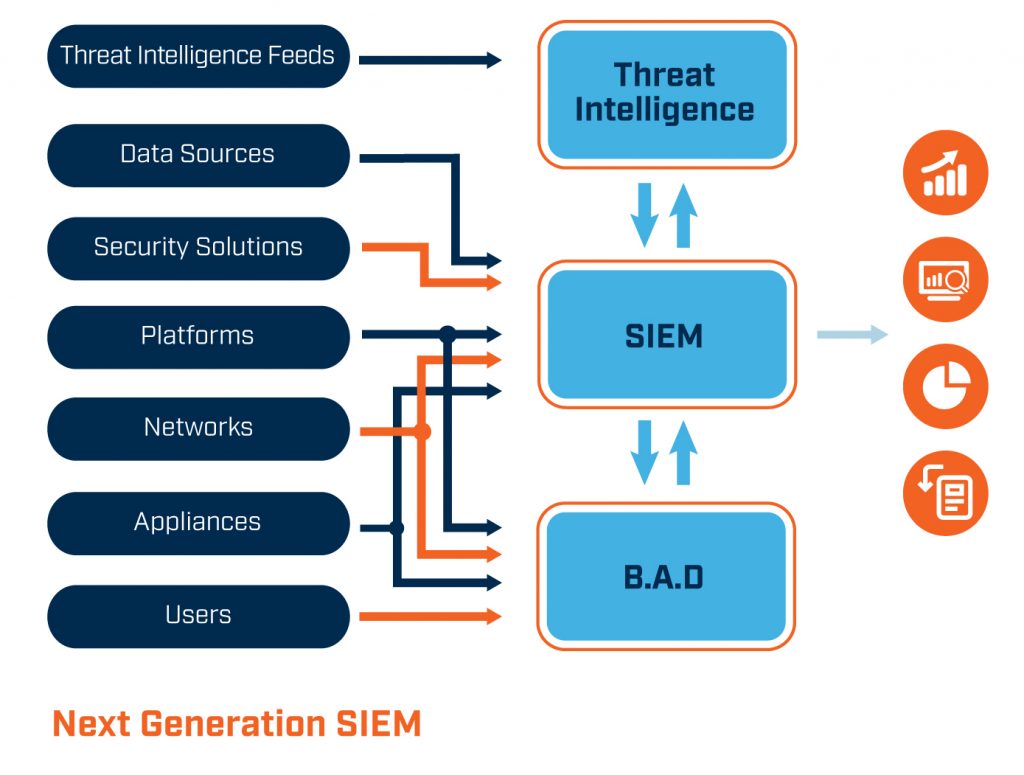
Logs Remain a Key SIEM Pillar
Logs are intrinsic to effective SIEM, particularly the mapping of a company’s business processes and infrastructure to those logs. And the more types of logs from as many sources as possible that a company can feed its SIEM system, the more actionable insights are generated.
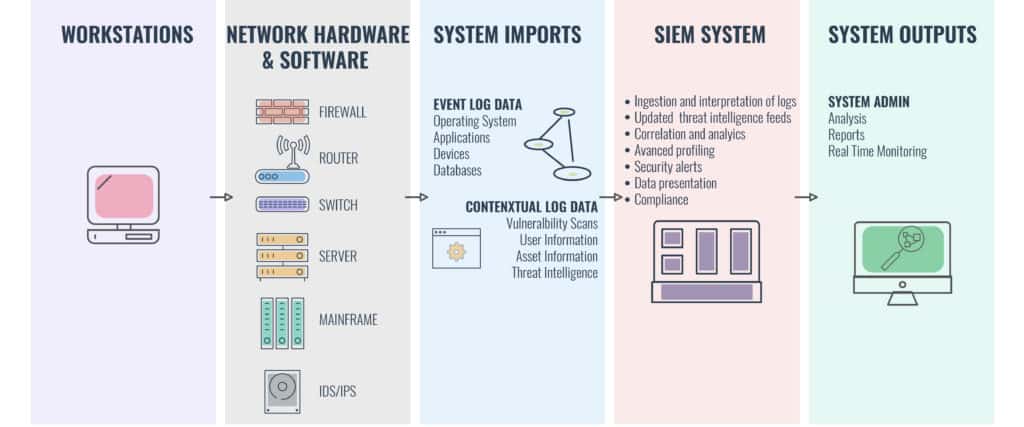
How SIEM works?
SIEM software collects and aggregates log data generated throughout the organization’s technology infrastructure, from host systems and applications to network and security devices such as firewalls and antivirus filters.
The software then identifies and categorizes incidents and events, as well as analyzes them. The software delivers on two main objectives, which are to provide reports on security-related incidents and events, such as successful and failed logins, malware activity and other possible malicious activities and send alerts if analysis shows that an activity runs against predetermined rulesets and thus indicates a potential security issue.
SIEM in the enterprise
SIEM software captures only a small portion of the total dollars spent on enterprise security worldwide, according to Gartner. Gartner estimates global spending on enterprise security at nearly $98.4 billion for 2017, with SIEM software garnering about $2.4 billion. Gartner predicts spending on SIEM technology will rise modestly, to nearly $2.6 billion in 2018 and $3.4 billion in 2021.
SIEM software is mostly used by large organizations and public companies, where compliance to regulations remains a strong factor in the use of this technology, according to analysts.
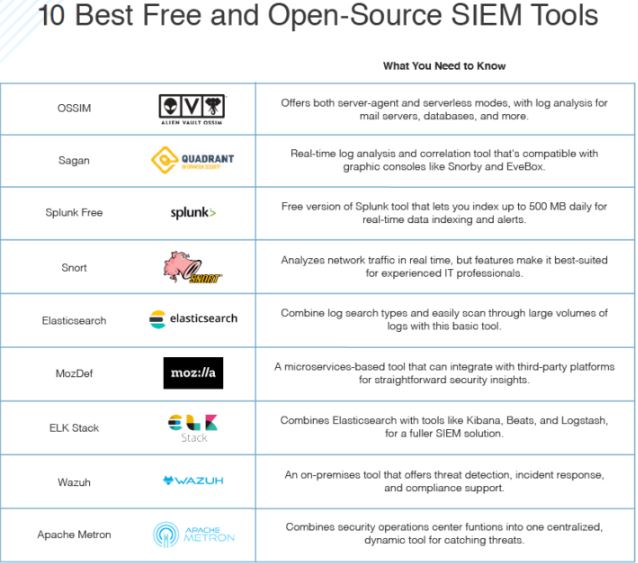
List of Popular SIEM tools
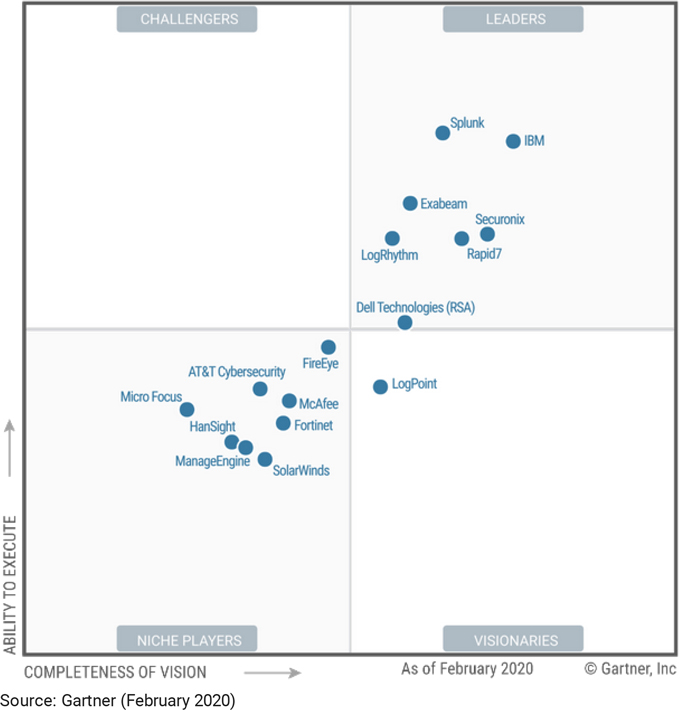
- Splunk – Splunk is a full on-prem SIEM solution that Gartner rates as a leader in the space. Splunk supports security monitoring and can provide advanced threat detection capabilities. Varonis integrates with Splunk through the Varonis DatAlert App for Splunk.
- IBM QRadar – QRadar is another popular SIEM that you can deploy as a hardware appliance, a virtual appliance, or a software appliance, depending on your organization’s needs and capacity. QRadar can integrate with Varonis to add Advanced Threat Detection capabilities. Look for the Varonis App for QRadar
- LogRhythm – LogRhythm is a good SIEM for smaller organizations. You can integrate LogRhythm with Varonis to get threat detection and response capabilities.
SIEM Tools Predictions
SIEM Process and Flow

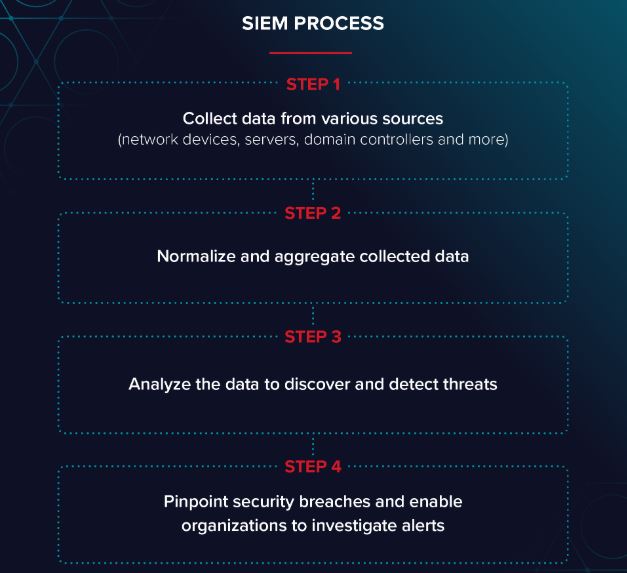
What Can a SIEM Help With and SIEM Capabilities?
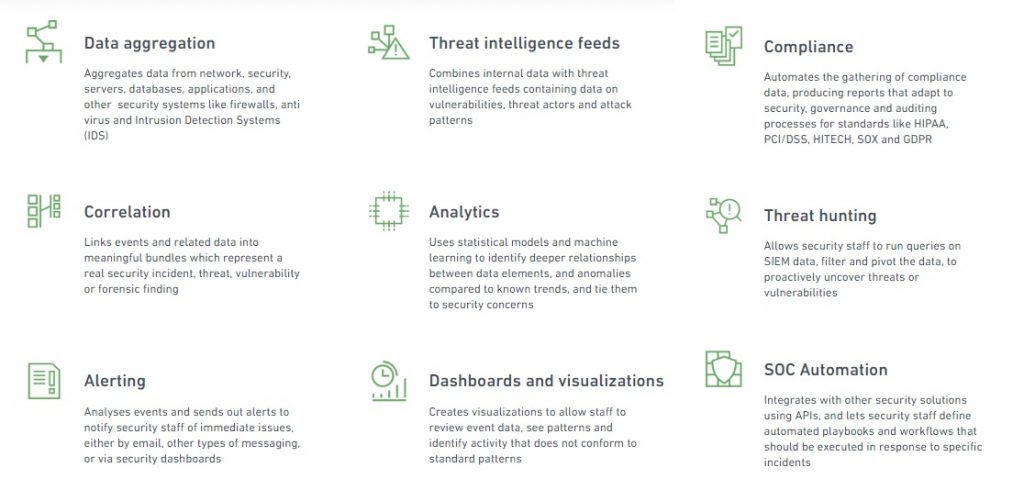
What are SIEMs Used For?

Criteria and requirement of SIEM
Enterprise security teams must use a security information and event management (SIEM) solution
that not only solves common security use cases, but advanced use cases as well. To keep up with the dynamic threat landscape, modern SIEMs are expected to be able to:
- Centralize and aggregate all security-relevant events as they’re generated from their source
- Support a variety of reception, collection mechanisms including syslog, file transmissions, file collections, etc.
- Add context and threat intelligence to security events
- Correlate and alert across a range of data
- Detect advanced and unknown threats
- Profile behavior across the organization
- Ingest all data (users, applications) and make them available for use — monitoring, alerting, investigation and ad hoc searching
- Provide ad hoc searching and reporting from data for advanced breach analysis
- Investigate incidents and conduct forensic investigations for detailed incident analysis
- Assess and report on compliance posture
- Use analytics and report on security posture
- Track attackers’ actions with streamlined ad hoc analyses and event sequencing
- Centrally automate retrieval, sharing and responses across the security stack
- Assess threats from the cloud, on-premises and hybrid apps and data sources
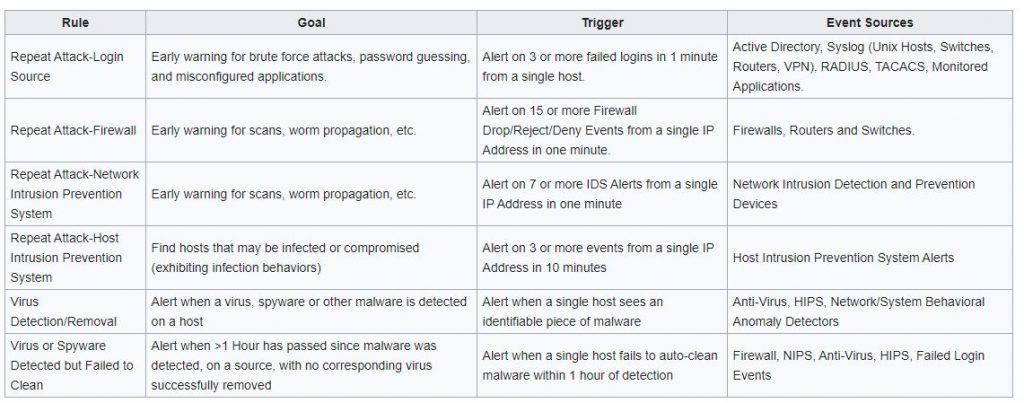
Alerting examples
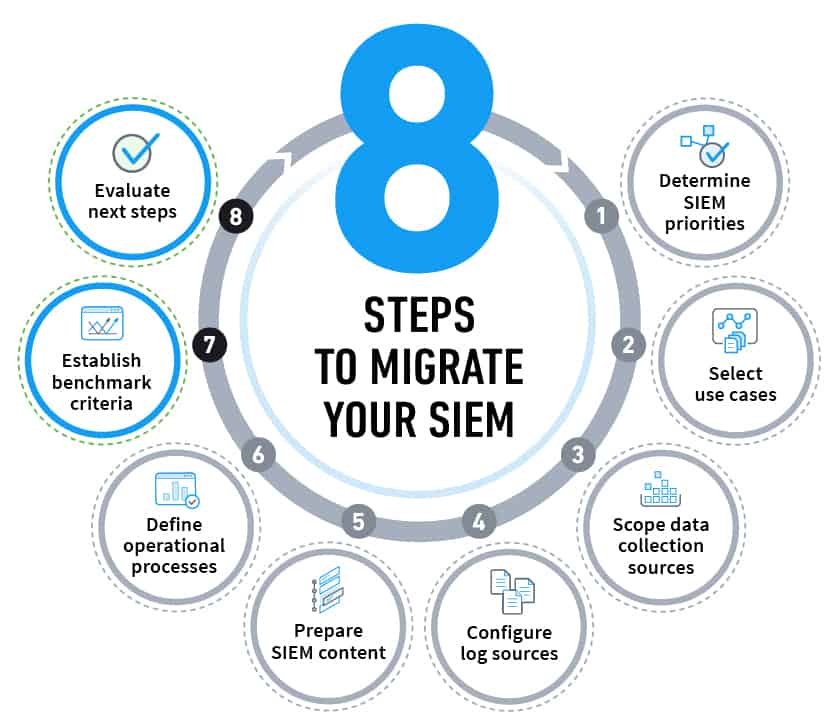
Steps to Implement SIEM in Enterprise
SIEM Best Practices

Reference
- https://www.exabeam.com/siem-guide/what-is-siem/
- https://en.wikipedia.org/wiki/Security_information_and_event_management
- Best AI tools for Software Engineers - November 4, 2024
- Installing Jupyter: Get up and running on your computer - November 2, 2024
- An Introduction of SymOps by SymOps.com - October 30, 2024

