History & Origin of HashiCorp Boundary
Mitchell Hashimoto and Armon Dadgar, HashiCorp’s co-founders, met at the University of Washington in 2008, where they worked on a research project together — an effort to make the groundbreaking public cloud technologies then being developed by Amazon and Microsoft available to scientists.
After graduating, they both moved to San Francisco. There — recognizing early on the impact this technology was poised to have on the world — Mitchell founded HashiCorp, with Armon joining him as a co-founder the next year.
As cloud adoption expanded, they recognized that organizations would eventually need to adopt multiple clouds, and would consequently require a consistent and reliable set of automation tools to seamlessly deploy and connect their applications to any combination of multiple cloud and on-premises environments.
What is HashiCorp Boundary

HashiCorp Boundary is an open-source identity access management (IAM) tool that facilitates secure user access to dynamic hosts and critical infrastructure across environments. However, if you need a simple and secure way to manage access to databases, Kubernetes clusters, cloud CLIs, switches, routers, or internal web applications, there are other services to consider. In this blog post, we’ll take a look at a few alternatives and discuss the strengths and weaknesses of each. First, a quick side-by-side comparison of the features you may want to consider.
Hashicorp Boundary
Brief product summary
HashiCorp released Boundary in 2020 as an answer to Vault users’ need for a session management (as opposed to credential management) solution. The project aims to simplify onboarding and create a dynamic workflow for system access, especially in high-automation environments, by granting authenticated and authorized users access to sensitive systems. It uses the principle of least privilege, allowing developers and operators just enough access to perform the required job. This limits access to larger networks, reducing the risk of compromise. Boundary also monitors and logs session metadata.
How HashiCorp Boundary works aka HashiCorp Boundary architecture?
ashiCorp Boundary is a secure remote access solution that provides an easy way to allow access to applications and critical systems with fine-grained authorizations based on trusted identities. Across clouds, local data centers, low-trust networks, Boundary provides an easier way to protect and safeguard access to application and critical systems by trusted identities without exposing the underlying network
- Platform-agnostic proxy for dynamic targets
- No SSH keys or VPN credentials to manage
- Just-in-time credentials via HashiCorp Vault
Use case of HashiCorp Boundary

Use cases
- Hashicorp Boundary is open-source and free identity-based security.
- Role-based and logical service authorization.
- Uses SSO to manage, onboard, and offboard users.
- Integrate with existing tools and APIs.
Pluses
- Dynamic resource catalogs.
- Planned integration with Terraform, AWS/GCP/Azure, Kubernetes for live updating of catalogs based on tags in v0.2.
- Dynamic credentials.
- Integration with Vault and others for end-to-end dynamic credentials.
- Authenticate with identity provider already in use.
Minuses
- Tools are confusing.
- Complex setup with lots of “moving parts”. Users have trouble figuring out what to run together and how to integrate.
- Requires a third tool, Consul, to manage services and machine-to-machine access.
Feature and Advantage of using HashiCorp Boundary
Identity-based access
Enables privileged sessions for users and applications based on user identity and role.
Session visibility and audit logs
Visibility into session metrics, events, logs, and traces with the ability to export data to business intelligence and event monitoring tools.
Seamless IDP integration
Integrate with IDP of choice, including Azure Active Directory, Okta, and many others that support Open ID Connect.
Dynamic secrets management
Leverage Vault integration for the brokering of Vault secrets to Boundary clients via the command line and desktop clients for use in Boundary sessions.
Dynamic service discovery
Automate service discovery and access configuration as workloads are deployed or changed. Coming soon.
Infrastructure as code
Define policies and manage Boundary with an Infrastructure as Code approach. Terraform provider supports the full breadth of Boundary configurations.
Best Alternative of HashiCorp Boundary
- AWS IAM. It enables you to manage access to AWS services and resources securely. …
- Teleport.
- AWS Service Catalog.
- SailPoint.
- BeyondTrust.
- Thycotic Secret Server.
- Oathkeeper.
- ManageEngine PAM360.
Best Resources, Tutorials and Guide for HashiCorp Boundary
Free Video Tutorials of HashiCorp Boundary
Interview Questions and Answer for HashiCorp Boundary
Q1. What is Hashicrop Boundary?
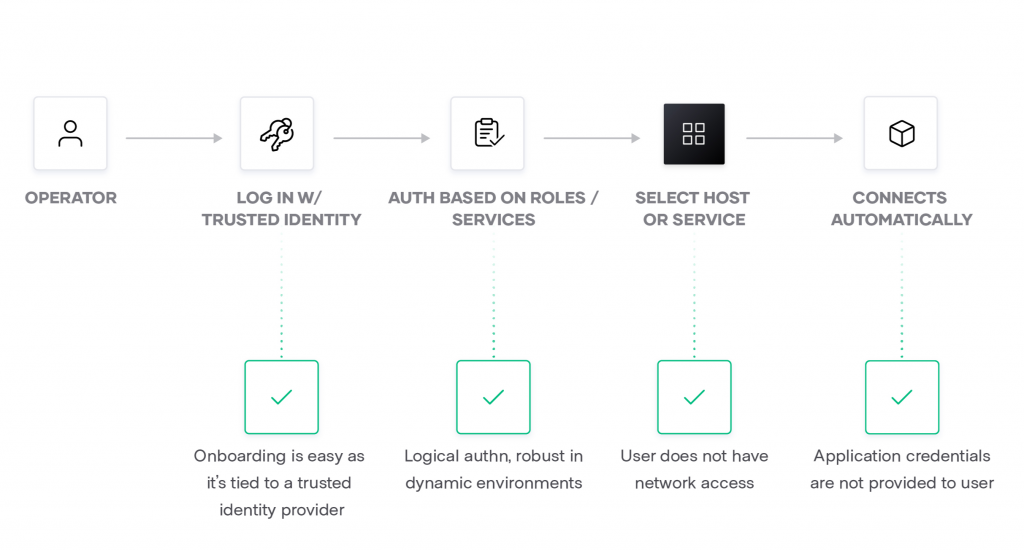
The HashiCorp Boundary is a very safe remote access solution that gives you an easy way to allow access to applications and critical systems with fine-grained authorizations based on trusted identities.
Q2. What are the benefits of Boundary?
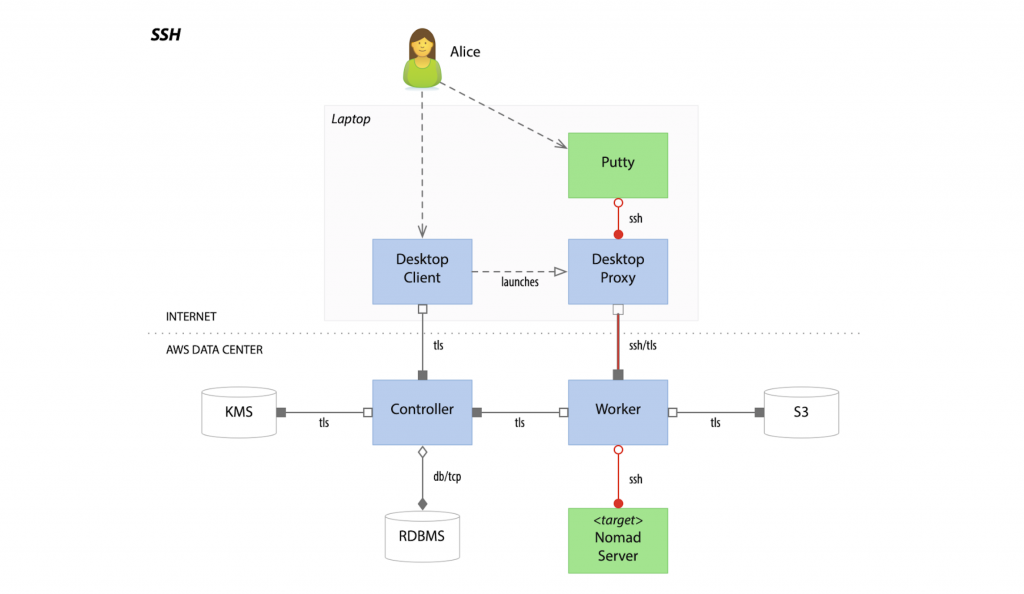
It gives you to manage access to AWS services and resources securely. By Using (IAM), you can create and manage AWS users and groups, and use permissions to allow and deny their access to AWS resources. The Teleport makes it easy for users to securely access infrastructure and meet the toughest compliance requirements.
Q3. What is the use of Boundary?
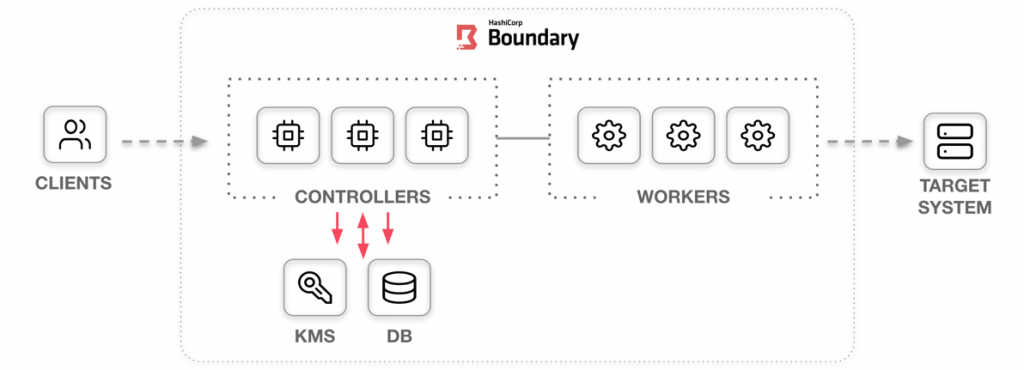
The hashicrop Boundary provides a secure way to access hosts and critical systems without having to manage credentials or expose your network, and is fully open source.
Q4. What is an ORM tool?
It is basically a technique that maps the object that is stored in the database. An ORM tool helps in simplifying data creation, manipulation, and access. It internally uses the Java API to interact with the databases.
Q5. Why use Hibernate Framework?
- Hibernate overcomes the shortcomings of other technologies like JDBC.
- It overcomes the database dependency faced in the JDBC.
- Changing of the databases cost a lot working on JDBC, hibernate overcomes this problem with flying colors.
- Code portability is not an option while working on JDBC. This is easily handled by Hibernate.
- Hibernate strengthens the object level relationship.
- It overcomes the exception-handling part which is mandatory while working on JDBC.
- It reduces the length of code with increased readability by overcoming the boilerplate problem.
Q6. What are the different functionalities supported by Hibernate?
- Hibernate is an ORM tool.
- Hibernate uses Hibernate Query Language(HQL) which makes it database-independent.
- It supports auto DDL operations.
- This Java framework also has an Auto Primary Key Generation support.
- Supports cache memory.
- Exception handling is not mandatory in the case of Hibernate.
Q7. What are the technologies that are supported by Hibernate?
Hibernate supports a variety of technologies, like:
- XDoclet Spring
- Maven
- Eclipse Plug-ins
- J2EE
Q8. What is HQL?
HQL is the acronym of Hibernate Query Language. It is an Object-Oriented Query Language and is independent of the database.
Q9. How to achieve mapping in Hibernate?
Association mappings are one of the key features of Hibernate. It supports the same associations as the relational database model. They are:
One-to-One associations
Many-to-One associations
Many-to-Many associations
You can map each of them as a uni- or bidirectional association.
Q10. Name some of the important interfaces of the Hibernate framework?
Hibernate interfaces are:
SessionFactory (org.hibernate.SessionFactory)
Session (org.hibernate.Session)
Transaction (org.hibernate.Transaction)
Q11. What is One-to-One association in Hibernate?
In this type of mapping, you only need to model the system for the entity for which you want to navigate the relationship in your query or domain model. You need an entity attribute that represents the association, so annotate it with an @OneToOne annotation.
Q12. What is the One-to-Many association in Boundary?
In this type of association, one object can be associated with multiple/different objects. Talking about the mapping, the One-to-Many mapping is implemented using a collection that does not have any redundant elements. This One-to-Many element of the set indicates the relation of one object to multiple objects.
Q13. What is Many-to-Many association in Boundary?
Many-to-Many mapping requires an entity attribute and a @ManyToMany annotation. It can either be unidirectional and bidirectional. In Unidirectional, the attributes model the association and you can use it to navigate it in your domain model or JPQL queries. The annotation tells Hibernate to map a Many-to-Many association. bidirectional relationship, mapping allows you to navigate the association in both directions.
Q14. How to integrate boundary and Spring?
Boundary is also one of the most commonly used Java frameworks in the market today. Spring is a JavaEE Framework and Hibernate is the most popular ORM framework. This is why Spring Hibernate combination is used in a lot of enterprise applications.
The following are the steps you should follow to integrate Spring and Hibernate.
Add Hibernate-entity manager, Hibernate-core, and Spring-ORM dependencies.
Create Model classes and corresponding DAO implementations for database operations. The DAO classes will use SessionFactory that will be injected by the Spring Bean configuration.
Note that you don’t need to use Hibernate Transaction Management, as you can leave it to the Spring declarative transaction management using @Transactional annotation.
Q15. What do you mean by Boundary Configuration File?
Boundary Configuration File mainly contains database-specific configurations and are used to initialize SessionFactory. Some important parts of the Hibernate Configuration File are Dialect information, so that hibernate knows the database type and mapping file or class details.
Q16. Mention some important annotations used for Boundary mapping?
Boundary supports JPA annotations. Some of the major annotations are:
- javax.persistence.Entity: This is used with model classes to specify they are entity beans.
- javax.persistence.Table: It is used with entity beans to define the corresponding table name in the database.
- javax.persistence.Access: Used to define the access type, field or property. The default value is field and if you want Hibernate to use the getter/setter methods then you need to set it to a property.
- javax.persistence.Id: Defines the primary key in the entity bean.
- javax.persistence.EmbeddedId: It defines a composite primary key in the entity bean.
- javax.persistence.Column: Helps in defining the column name in the database table.
- javax.persistence.GeneratedValue: It defines the strategy to be used for the generation of the primary key. It is also used in conjunction with javax.persistence.GenerationType enum.
Q17. What is Session in Boundary and how to get it?
Boundary Session is the interface between the Java application layer and Hibernate. It is used to get a physical connection with the database. The Session object created is lightweight and designed to be instantiated each time an interaction is needed with the database. This Session provides methods to create, read, update, and delete operations for a constant object. To get the Session, you can execute HQL queries, SQL native queries using the Session object.
Q18. What is Hibernate SessionFactory?
SessionFactory is the factory class that is used to get the Session objects. The SessionFactory is a heavyweight object so usually, it is created during application startup and kept for later use. If you are using multiple databases then you would have to create multiple SessionFactory is a thread-safe object which is used by all the threads of an application. I SessionFactory objects.
Q19. What is the difference between openSession and getCurrentSession?
This getCurrentSession() method returns the session bound to the context and for this to work, you need to configure it in the Hibernate configuration file. Since this session object belongs to the context of Hibernate, it is okay if you don’t close it. Once the SessionFactory is closed, this session object gets closed.
openSession() method helps in opening a new session. You should close this session object once you are done with all the database operations. And also, you should open a new session for each request in a multi-threaded environment.
Q20. What do you mean by Boundary configuration file?
- The following steps help in configuringHibernatefile:
- First, identify the POJOs (Plain Old Java Objects) that have a database representation.
- Identify which properties of POJOs need to be continued.
- Annotate each of the POJOs in order to map the Java objects to columns in a database table.
- Create a database schema using the schema export tool which uses an existing database, or you can create your own database schema.
- Add Hibernate Java libraries to the application’s classpath.
- Create a Hibernate XML configuration file that points to the database and the mapped classes.
- In the Java application, you can create a Hibernate Configuration object that refers to your XML configuration file.
- Also, build a Hibernate SessionFactory object from the Configuration object.
- Retrieve the Hibernate Session objects from the SessionFactoryand write down the data access logic for your application (create, retrieve, update, and delete).
- Best AI tools for Software Engineers - November 4, 2024
- Installing Jupyter: Get up and running on your computer - November 2, 2024
- An Introduction of SymOps by SymOps.com - October 30, 2024


