Step 1:
Creating IAM role for EKS cluster (for manage purpose)
Role Name – EKS_Cluster
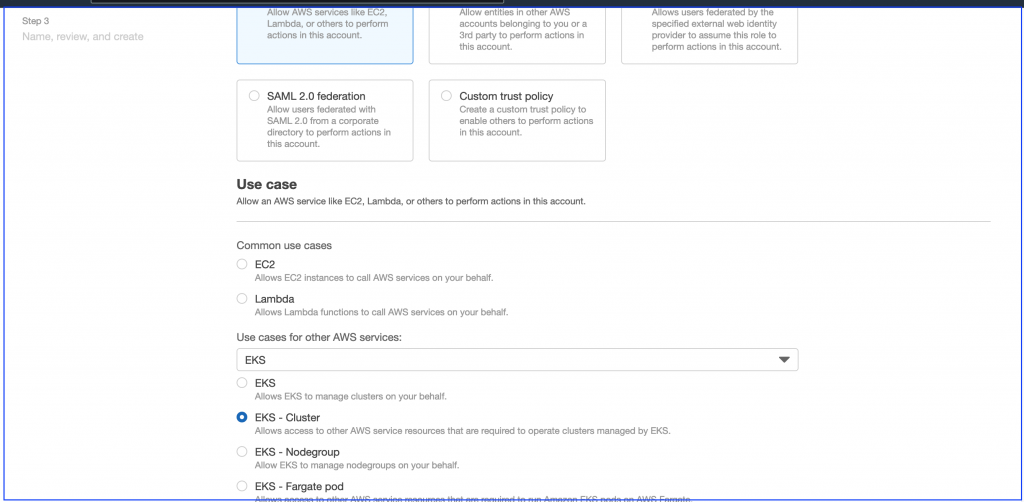
Step 2:
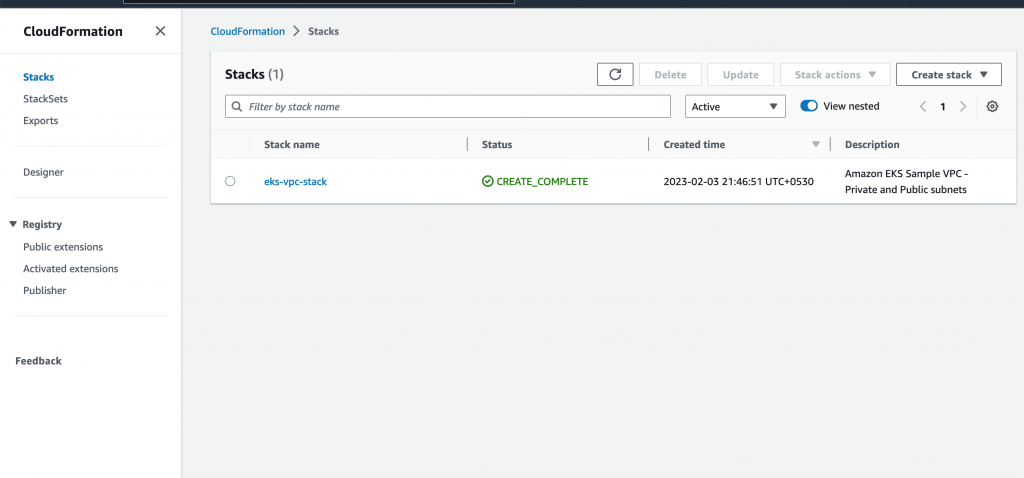
To Create VPC – Go to Cloud Formation – Stack
It helps in creating private cloud -i.e. network , route table and sub network
Use attached file to create VPC
amazon-eks-vpc-private-subnets.yaml
Step 3:
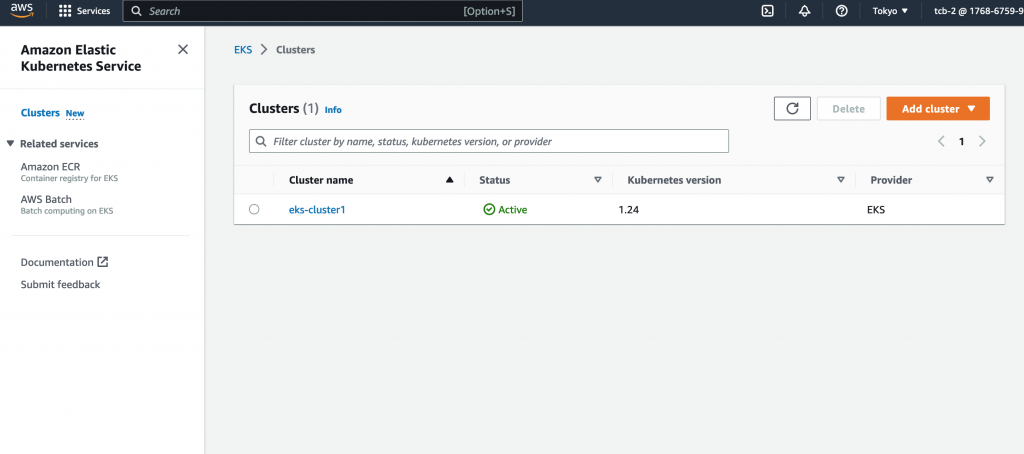
Create EKS cluster — Search EKS service
while creating please choose role EKS_Cluster (which created in step 1) under Cluster service role.
Under networking please choose step 3 VPC
Step 4
Create one instance
- configure AWS in machine – they will ask AWS Account and Access Keys
- Follow link for the same – https://docs.aws.amazon.com/powershell/latest/userguide/pstools-appendix-sign-up.html
intsall aws cli
Sudo apt install awscli
Install aws-iam-authenticator
- curl -Lo aws-iam-authenticator https://github.com/kubernetes-sigs/aws-iam-authenticator/releases/download/v0.5.9/aws-iam-authenticator_0.5.9_linux_amd64
- Apply execute permissions to the binary.
- chmod +x ./aws-iam-authenticator
- Copy the binary to a folder in your
$PATH. We recommend creating a$HOME/bin/aws-iam-authenticatorand ensuring that$HOME/bincomes first in your$PATH. - mkdir -p $HOME/bin && cp ./aws-iam-authenticator $HOME/bin/aws-iam-authenticator && export PATH=$PATH:$HOME/bin
- Test that the
aws-iam-authenticatorbinary works. - aws-iam-authenticator help
Install Kubectl
- before install check if it is available
- kubectl get svc
- To install or update
kubectlon Linux - curl -O https://s3.us-west-2.amazonaws.com/amazon-eks/1.24.9/2023-01-11/bin/linux/amd64/kubectl
- Apply execute permissions to the binary.
- chmod +x ./kubectl
- Copy the binary to a folder in your
PATH. If you have already installed a version ofkubectl, then we recommend creating a$HOME/bin/kubectland ensuring that$HOME/bincomes first in your$PATH. - mkdir -p $HOME/bin && cp ./kubectl $HOME/bin/kubectl && export PATH=$PATH:$HOME/bin
- After you install
kubectl, you can verify its version. - kubectl version –short –client
Step 5
Configure kubeconfig into profile (kubeconfig added into local profile)
aws eks –region region_name update-kubeconfig –name eks_cluster_name
export KUBECONFIG=~/.kube/config
kubectl get svc
if getting error :error: exec plugin: invalid apiVersion “client.authentication.k8s.io/v1alpha1”
intsall -sudo apt install python3-pip
pip3 install awscli –upgrade –user
vi ~/.kube/config
change apiVersion to apiVersion: client.authentication.k8s.io/v1beta1
kubectl get svc
kubectl get nodes
kubectl get ns
kubectl get pods
Step 6
Create worker role
select below policy
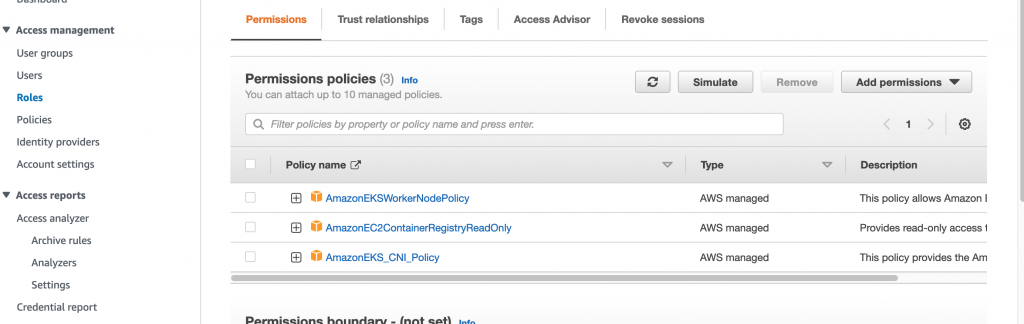
eksworkernoderole (for worker purpose)
Step 7
Go to eks service
Create worker nodes under eks cluster – select worker
Give worker worker role (step 6) under i am role name
It will create 2 instance (check under EC2 )
Check kubectl get nodes –watch
kubectl get pods – it will get nothing
Deploy app and db package
git clone https://github.com/learnitguide/kubernetes-knote.git
Edit
vi mongo.yaml — edit replicas = 2
vi knote.yaml — edit replicas = 2 and also type = loadbalancer
kubectl get svc
kubectl get pods -o wide
nslookup ae957e45b215c4f2b98054f331979c76-363953468.ap-northeast-1.elb.amazonaws.com
curl ae957e45b215c4f2b98054f331979c76-363953468.ap-northeast-1.elb.amazonaws.com
MotoShare.in is your go-to platform for adventure and exploration. Rent premium bikes for epic journeys or simple scooters for your daily errands—all with the MotoShare.in advantage of affordability and ease.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
