
What is Security Configuration Management?
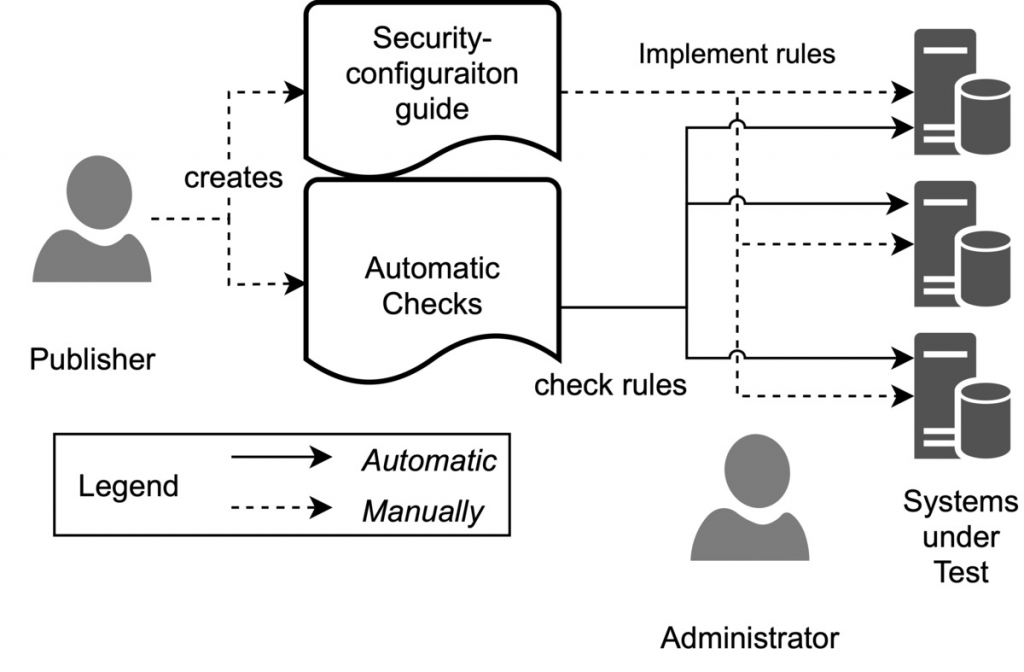
Security configuration management (SCM) is the process of establishing, maintaining, and monitoring the security configuration of information systems. It involves identifying, assessing, and remediating security risks that arise from misconfigurations.
SCM is a critical component of any organization’s security program. It helps to ensure that information systems are configured in a secure manner, and that security configurations are maintained over time.
The SCM process typically includes the following steps:
- Establish a baseline configuration: The first step is to establish a baseline configuration for each information system. This baseline configuration should represent the desired security state of the system.
- Monitor configuration changes: Once a baseline configuration has been established, it is important to monitor for changes to the system configuration. This can be done using a variety of tools and techniques, such as log analysis and configuration management tools.
- Identify and assess configuration risks: When configuration changes are identified, they should be assessed to determine whether they introduce any security risks. This assessment should take into account the nature of the change, the environment in which the system is operating, and the organization’s security posture.
- Remediate configuration risks: Any configuration risks that are identified should be remediated as soon as possible. This may involve reverting to the baseline configuration, or making changes to the configuration to mitigate the risk.
SCM is a continuous process, and organizations should regularly review and improve their SCM procedures. This helps to ensure that security configurations are maintained over time, and that new security risks are identified and remediated quickly.
Here are some of the benefits of security configuration management:
- Reduced risk of security breaches
- Improved compliance with industry regulations
- Increased efficiency and productivity of IT staff
- Reduced costs associated with security incidents
- Improved visibility into the security posture of information systems
Why we need Security Configuration Management?
Security Configuration Management (SCM) is a critical component of modern cybersecurity strategies. Here’s why it’s essential:
- Baseline Establishment: SCM helps organizations define and maintain a security baseline for systems. By establishing what’s “normal,” deviations can be easily spotted, indicating potential security incidents.
- Vulnerability Reduction: Misconfigured systems are a common vulnerability point. By regularly reviewing and hardening configurations, organizations can reduce the number of exploitable weaknesses.
- Regulatory Compliance: Many industry regulations require specific system configurations to ensure data protection. SCM aids in both achieving and demonstrating compliance with these regulations.
- Change Management: As systems evolve and change over time, there’s a risk that security configurations might get altered inadvertently. SCM helps in monitoring and managing these changes to ensure that security isn’t compromised.
- Auditing and Accountability: SCM tools often come with auditing capabilities. If a security incident does occur, having a comprehensive audit trail can help in determining the root cause and who (or what) made the change.
- Consistency Across Systems: Especially in larger organizations, ensuring that every system has the proper security configuration can be challenging. SCM solutions can apply consistent settings across multiple systems, ensuring uniform security measures.
- Automated Remediation: Advanced SCM tools can automatically detect and revert unauthorized changes, ensuring configurations remain in their desired state.
- Integration with Other Security Tools: SCM can be integrated with other cybersecurity tools to provide a more holistic view of security posture. For instance, integrating SCM with vulnerability management can provide insights into which vulnerabilities are due to misconfigurations.
- Reduced Attack Surface: Proper configuration management ensures services and applications that aren’t needed are disabled or removed, reducing potential entry points for attackers.
- Efficient Resource Utilization: By understanding and managing configurations, organizations can ensure that systems are not just secure but also optimized in their use of resources.
- Documentation: SCM provides comprehensive documentation of configurations and changes, which can be invaluable for troubleshooting, audits, and training.
- Increased Uptime: Misconfigurations can lead to system failures or disruptions. By managing and monitoring configurations, potential issues can be identified and rectified before they cause significant downtime.
List of Best Security Configuration Management Tools
AlienVault USM:
A unified security management system that brings together multiple advanced features, including vulnerability assessment and configuration monitoring. It’s valuable for its holistic view of an organization’s security posture.
Ansible:
A powerful IT automation tool that can manage configurations, while ensuring that systems are running in line with specified security standards. Its simplicity and agentless nature make it a popular choice for many.
AWS Config:
Tailored for the AWS environment, AWS Config monitors configurations of AWS resources and evaluates them against desired configurations, ensuring that security policies are consistently applied across the environment.
BMC BladeLogic:
An automation suite that manages, configures, and secures servers. Its robustness allows enterprises to maintain system compliance with security policies.
CFEngine:
One of the original configuration management tools, CFEngine provides automated configuration and maintenance of large-scale computer systems. Its lightweight nature is particularly attractive for security-focused environments.
Chef:
Known for infrastructure as code, Chef allows for automating the process of managing configurations, ensuring that systems adhere to security baselines and policies.
CIS CSC:
While not a tool in the traditional sense, the Center for Internet Security Critical Security Controls provides best practices and guidelines for securing systems. Tools built around these controls can provide comprehensive security coverage.
ISO 27001:
A globally recognized standard for information security management. Systems and tools compliant with ISO 27001 ensure a high standard of security configuration and management.
ManageEngine:
Offers a range of IT management software, including tools focused on security configuration management, ensuring systems are both efficient and secure.
NIST Cybersecurity:
The National Institute of Standards and Technology’s framework is a set of best practices for improving cybersecurity. Tools adhering to this framework have a strong foundation in security principles.
Nexpose:
By Rapid7, Nexpose is a vulnerability management tool that also provides insights into misconfigurations, ensuring that systems are both patched and correctly configured.
OpenSCAP:
An auditing tool that uses the SCAP protocol to check system configurations and vulnerabilities. It’s open-source and can ensure systems are compliant with various security standards.
Puppet:
A configuration management tool that automates the provisioning and management of machines, ensuring they align with desired security states.
Qualys:
A cloud-based security and compliance solution, providing a wide range of capabilities including monitoring of system configurations.
Qualys Policy Compliance:
An extension of Qualys, it provides continuous monitoring and auditing of configurations against a library of best practices and policies.
SaltStack:
An event-driven IT automation tool that can manage configurations, ensuring they are secure and up-to-date.
SCCM:
Microsoft’s System Center Configuration Manager manages large groups of Windows computers. It ensures systems are updated, patched, and configured according to best practices.
Tenable.sc:
Part of the Tenable Network Security suite, Tenable.sc provides continuous network monitoring, vulnerability identification, and configuration assessment.
Terraform:
A tool by HashiCorp, it allows infrastructure as code for provisioning and managing cloud resources, ensuring that infrastructure is provisioned securely and consistently.
Tripwire Enterprise:
A security configuration management tool that offers real-time monitoring, change auditing, and breach detection.
- Discover 7 Fascinating Careers in Game Design - October 14, 2024
- The Integration of AI and IoT: Enhancing Smart Systems - October 8, 2024
- Software Development Companies in Latin America and How To Choose One - October 1, 2024

