What is RSA SecurID?

RSA SecurID is a widely used multi-factor authentication (MFA) solution developed by RSA, the security division of Dell Technologies. It is designed to enhance security by requiring users to provide multiple authentication factors during login.
RSA SecurID typically involves the use of hardware or software tokens that generate one-time codes at regular intervals. Users must enter these codes along with their passwords to gain access. The tokens can take various forms, including hardware tokens, mobile apps, or software tokens on a user’s computer.
This multi-factor authentication solution is widely adopted across industries and is known for its strong security features, making it a valuable tool for protecting sensitive data and resources.
Top 10 use cases of RSA SecurID:
Here are the top 10 use cases for RSA SecurID:
- Secure Remote Access: Provide secure remote access to corporate networks, applications, and resources for remote and mobile employees.
- User Authentication: Verify the identity of users by requiring them to enter a unique one-time code generated by the RSA SecurID token, along with their regular username and password.
- Two-Factor Authentication (2FA): Implement 2FA by combining something the user knows (password) with something they have (RSA SecurID token), adding an extra layer of security to access control.
- Privileged Access: Enhance security for privileged accounts and administrators by requiring them to use RSA SecurID tokens to access critical systems and resources.
- Secure VPN Access: Protect virtual private network (VPN) access by requiring users to authenticate using RSA SecurID tokens, ensuring that only authorized individuals can connect remotely.
- Cloud Security: Extend MFA to cloud-based applications and services, ensuring secure access to platforms like Microsoft 365, AWS, and Google Workspace.
- Identity Federation: Integrate RSA SecurID with identity federation solutions to enable users to access federated services securely.
- Secure Transactions: Ensure secure transactions, especially in financial institutions, by requiring RSA SecurID authentication for access to sensitive data and transactions.
- Customer Authentication: Implement MFA for customer-facing applications and services to enhance security and protect customer data.
- Compliance Requirements: Meet regulatory and compliance requirements by implementing strong authentication measures, as required by industry standards like GDPR, HIPAA, and PCI DSS.
- Phishing Prevention: Mitigate the risk of phishing attacks by requiring a dynamic one-time code from the RSA SecurID token, which cannot be used by attackers who have stolen static credentials.
- Mobile and Remote Workforce: Securely authenticate mobile and remote workers accessing corporate resources from various locations and devices.
What are the feature of RSA SecurID?
RSA SecurID is a multi-factor authentication (MFA) solution known for its robust security features. It works by requiring users to provide two or more authentication factors during the login process to enhance security. Below are the key features of RSA SecurID, followed by an overview of how it works and its architecture:
Key Features of RSA SecurID:
- Two-Factor Authentication (2FA): RSA SecurID combines something the user knows (typically a password) with something they have (a hardware or software token) to authenticate users.
- Hardware Tokens: Hardware tokens are physical devices that generate one-time codes at regular intervals. Users enter these codes along with their passwords for authentication.
- Software Tokens: Software tokens are typically mobile apps or software applications installed on users’ devices. They generate one-time codes, eliminating the need for hardware tokens.
- Dynamic One-Time Codes: RSA SecurID generates time-based or event-based one-time codes that are valid for a limited time, reducing the risk of replay attacks.
- Remote Access Security: It provides secure remote access to corporate networks and resources, ensuring that only authorized users can connect remotely.
- Mobile Authentication: RSA SecurID supports mobile authentication, allowing users to use their smartphones as software tokens, enhancing convenience and security for mobile users.
- Integration Capabilities: It integrates with a wide range of applications, services, and VPN solutions, making it versatile for use across various environments.
- Self-Service Portal: RSA SecurID often includes a self-service portal where users can manage their tokens, PINs, and authentication settings.
- Risk-Based Authentication: Some versions of RSA SecurID incorporate risk-based authentication, which evaluates the risk level of login attempts and adapts authentication requirements accordingly.
- Phishing Protection: By requiring a dynamic one-time code in addition to static credentials, RSA SecurID helps protect against phishing attacks.
How RSA SecurID works and Architecture?
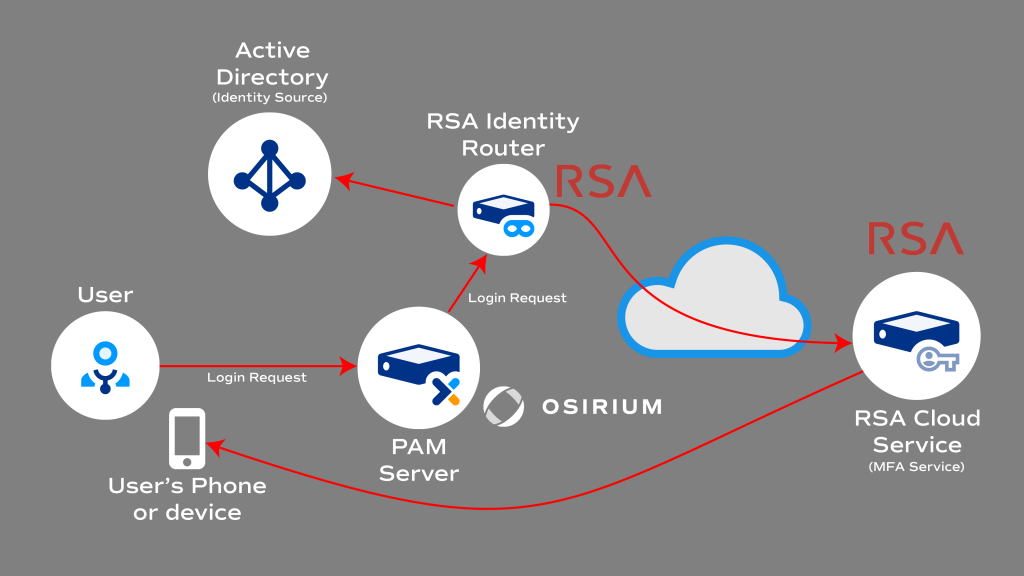
- User Enrollment: Users are enrolled in the RSA SecurID system and provided with either hardware tokens or software tokens (mobile apps) associated with their accounts.
- Authentication Request: When a user attempts to access a secured resource or log in, they provide their username and password.
- Token Generation: The RSA SecurID token (hardware or software) generates a one-time code based on a time-based or event-based algorithm.
- Code Entry: The user enters the one-time code displayed on their token device within a certain time window (usually 30-60 seconds) along with their password.
- Authentication Validation: The RSA SecurID server validates the one-time code entered by the user, along with their password, to determine if access should be granted.
- Access Granted or Denied: If the authentication is successful, the user gains access to the requested resource. Otherwise, access is denied.
The architecture of RSA SecurID typically includes the following components:
- RSA Authentication Manager: This is the central management server responsible for managing tokens, user accounts, authentication policies, and authentication requests.
- Hardware or Software Tokens: Tokens generate one-time codes that users enter during authentication. Hardware tokens are physical devices, while software tokens are typically mobile apps or software applications.
- Authentication Agents: These agents are responsible for communicating between the authentication manager and the target resources or applications that need to be protected.
- User Database: Stores user account information, including usernames and associated tokens.
- Self-Service Portal: Often included as part of the solution, this portal allows users to manage their tokens, PINs, and authentication settings.
RSA SecurID is known for its strong security and is widely used across industries to protect sensitive data and resources. It adds an additional layer of authentication to enhance security beyond traditional username and password-based authentication.
How to Install RSA SecurID?
To install RSA SecurID, you will need to download the RSA SecurID software from the RSA website. The software is available for Windows, macOS, and mobile devices.
To install RSA SecurID on Windows:
- Download the RSA SecurID software from the RSA website.
- Double-click the installation file to begin the installation process.
- Implement the on-screen instructions to fulfill the installation.
To install RSA SecurID on macOS:
- Download the RSA SecurID software from the RSA website.
- Double-click the installation file to begin the installation process.
- Implement the on-screen instructions to fulfill the installation.
To install RSA SecurID on a mobile device:
- Download the RSA SecurID software from the Google Play Store or the Apple App Store.
- Open the software and follow the on-screen instructions to create an account and add your SecurID token.
Once you have installed RSA SecurID, you can start using it to generate one-time passwords for two-factor authentication.
Some additional tips for installing RSA SecurID:
- Make sure that you have your own latest version of the operating system installed.
- Close all other applications before installing RSA SecurID.
- If you are having trouble installing RSA SecurID, contact your IT administrator for assistance.
Basic Tutorials of RSA SecurID: Getting Started

The following steps are the Basic Tutorials of RSA SecurID:
1. Generating a One-Time Password (OTP)
- Open the RSA SecurID software or mobile app.
- Enter your PIN and press Enter.
- The RSA SecurID software or mobile app will generate a one-time password (OTP).
- Enter the OTP in the appropriate field and press Enter.
2. Adding a SecurID Token
- Open the RSA SecurID software or mobile app.
- Tap or click the Add Token button.
- Select the type of SecurID token you have.
- Follow the on-screen instructions to add your SecurID token.
3. Enrolling in Two-Factor Authentication (2FA)
- Contact your IT administrator to find out if 2FA is available for your organization.
- If 2FA is available, your IT administrator will provide you with the necessary instructions to enroll.
- Follow the instructions to enroll in 2FA.
4. Logging in with RSA SecurID
- Go to the website or application that you want to log in to.
- Enter your username and password.
- Enter the OTP that is generated by the RSA SecurID software or mobile app.
- Click or tap the Log In button.
Some additional tips for using RSA SecurID:
- Keep your SecurID token safe and do not share it with anyone.
- Change your PIN regularly.
- If you lose your SecurID token, contact your IT administrator immediately.
- You can use the RSA SecurID software or mobile app to generate OTPs for multiple SecurID tokens.
- You can also use the RSA SecurID software or mobile app to generate OTPs for other authentication methods, such as SMS and Google Authenticator.
- If you are having trouble using RSA SecurID, contact your IT administrator for assistance.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
