What is Kong?

Kong is an API gateway, open-source and microservices management platform. It acts as an intermediary between clients and your API-driven applications, providing a range of functionalities including:
- API Management: Route API requests, enforce rate limiting, implement authentication and authorization, and add security measures.
- Microservice Management: Facilitate communication between microservices, handle service discovery, and provide load balancing.
- Observability and Monitoring: Collect and analyze API traffic data, gain insights into performance, and troubleshoot issues.
- Scalability and Flexibility: Kong can be deployed on various platforms, scales horizontally to handle high traffic volumes, and offers plugins for customization.
In essence, Kong sits between your clients and your backend APIs, offering various tools to manage, secure, and improve the way your APIs function.
Top 10 use cases of Kong?
Top 10 Use Cases of Kong:
- API Gateway for Modern Applications: Manage numerous APIs, enforce policies, and provide a unified entry point for clients.
- Microservice Communication and API Mesh: Enable communication between microservices with features like service discovery and load balancing.
- API Security and Authentication: Implement authentication methods like OAuth, API keys, and JWTs to control access to your APIs.
- Traffic Management and Routing: Route API requests based on specific rules, implement rate limiting and circuit breakers.
- API Versioning and Transformation: Manage different API versions, adapt data formats, and handle compatibility issues.
- API Analytics and Monitoring: Gain insights into API performance, track metrics, and identify potential problems.
- Developer Portal and Documentation: Provide developers with a self-service portal to explore and understand your APIs.
- Integration with CI/CD Pipelines: Automate API deployment and management within your development workflow.
- Cloud-Native Deployments: Run Kong on various cloud platforms and integrate with cloud services.
- Hybrid and Multi-Cloud Environments: Manage APIs across different environments with centralized control and security.
These are just a few examples, and the specific use cases will vary depending on your needs and application architecture. Kong offers a versatile platform that can be adapted to various scenarios, making it a popular choice for modern API management and microservice deployments.
What are the feature of Kong?
Kong boasts a range of features that cater to various API management and microservice needs. Here are some key highlights:
API Management:
- Routing: Advanced routing based on paths, headers, methods, and plugins.
- Plugins: Extensive plugin ecosystem for custom functionality, including authentication, rate limiting, transformations, etc.
- Authentication and Authorization: Supports various methods like OAuth, basic auth, API keys, JWTs, and more.
- API Versioning: Manage different API versions with versioning strategies and backward compatibility options.
- API Security: Secure your APIs with features like request signing, validation, and bot detection.
- API Analytics and Monitoring: Track API metrics, visualize performance data, and gain insights into usage patterns.
- Developer Portal: Provide developers with a self-service portal to explore APIs, documentation, and access keys.
Microservice Management:
- Service Discovery: Discover and connect to microservices dynamically using various protocols.
- Load Balancing: Distribute traffic efficiently across available microservices for optimal performance.
- Fault Tolerance: Implement service resilience with circuit breakers, timeouts, and retries.
- Microservice Communication: Facilitate communication between microservices using different protocols like HTTP, TCP, and gRPC.
Additional Features:
- Scalability and Performance: Horizontal scaling to handle high traffic volumes and ensure fast response times.
- Platform Agnostic: Runs on various platforms, including cloud deployments and self-managed infrastructure.
- Open Source and Community Driven: Benefits from active development and contributions from the open-source community.
- Flexible Configuration: Configure Kong through a declarative configuration file, REST API, or web UI.
- Integrations: Integrates with other tools and technologies like Prometheus, Grafana, and Terraform.
Enterprise Features (Kong Enterprise):
- Role-Based Access Control (RBAC): Granular control over access to Kong resources and functionalities.
- Secrets Management: Securely store and manage sensitive data like API keys and certificates.
- Audit Logging: Track all activity within Kong for enhanced security and compliance.
- Advanced Analytics and Monitoring: Deeper insights into API performance with additional metrics and dashboards.
- Multi-Datacenter Deployments: Manage APIs across multiple datacenters for geographic distribution and disaster recovery.
Remember, the specific features you utilize will depend on your specific needs and the version of Kong you’re using. However, this overview provides a good starting point for understanding the wide range of capabilities that Kong offers.
How Kong works and Architecture?
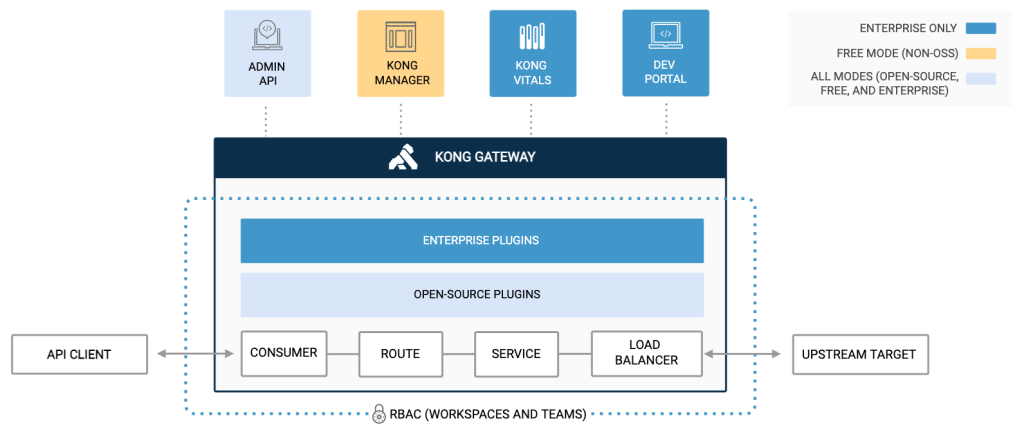
Kong’s internal workings and architecture involve several key components that interact to manage your APIs and microservices effectively. Here’s a breakdown:
Data Plane:
- HTTP Server: This core component receives incoming client requests and acts as the entry point for all traffic entering your system.
- Plugins: These modular extensions provide specific functionalities like authentication, rate limiting, transformation, and more. Different plugins are chained together to achieve desired behavior.
- Service Routing: Based on configuration and plugins, Kong routes requests to the appropriate backend service or API.
- Load Balancing: Distributes traffic efficiently across available backends to optimize performance and handle failures.
- Response Handling: Processes responses from backend services, applies any necessary transformations, and sends them back to the client.
Control Plane:
- Admin API: Enables configuration management and monitoring of Kong through a REST API.
- Configuration File: Defines settings for plugins, routing rules, services, and other aspects of Kong’s behavior.
- Database (Optional): Stores configuration data and plugin state persistently, depending on the deployment mode.
- Plugins (Optional): Certain control plane plugins can extend its functionality for tasks like authentication or data encryption.
Interaction and Flow:
- Client sends a request to the Kong data plane (HTTP server).
- Plugins intercept the request and may perform actions like authentication, rate limiting, and data transformation.
- Based on routing rules and service discovery, Kong forwards the request to the appropriate backend service.
- The backend service processes the request and sends a response back to Kong.
- Plugins can again intercept the response for further processing or transformation.
- Finally, Kong sends the response back to the client.
Key Architectural Concepts:
- Microservice-based architecture: Each component is modular and can be scaled independently.
- Data Plane vs. Control Plane Separation: Provides flexibility and improved manageability.
- Plugin ecosystem: Extends functionality and allows customization for specific needs.
- Declarative configuration: Configuration is defined in a human-readable format for easier management.
- API-driven management: You can manage and monitor Kong using the Admin API.
Understanding these core elements and their interactions will give you a solid foundation for appreciating how Kong works and how it can be utilized in your API management and microservice architecture.
How to Install Kong it?
Installing Kong can be done in several ways, depending on your environment and preferences. Following are some of the most common methods:
1. Precompiled Binaries:
This is the easiest and most common approach for basic use cases. Here’s how:
- Download the appropriate binary:
- Visit the official Kong download page from their official site.
- Choose the version and operating system that matches your needs.
- Download the appropriate
zipfile.
- Extract the binary:
- Extract the downloaded
zipfile to a desired location. - The
consulbinary will be inside the extracted folder.
- Extract the downloaded
- (Optional) Add to PATH:
- If you want to access
consulfrom any directory in your terminal, add the binary location to your PATH environment variable.
- If you want to access
- Start Kong:
- Open a terminal and navigate to the directory containing the
consulbinary. - Run the following command, replacing
<data_dir>with your desired data directory:
- Open a terminal and navigate to the directory containing the
consul agent -data-dir=<data_dir>
2. Install from Source:
This option gives you more control over the build process but requires compiling the code yourself. Here’s a general outline:
- Visit the Kong GitHub repository: [https://github.com/Kong/kong]
- Follow the instructions in the README file to build and install Kong from source.
3. Package Managers:
Many Linux distributions provide pre-built Kong packages through their package managers (e.g., apt, yum, dnf). This is a convenient way to install Kong on specific systems if available.
4. Containerized Deployment:
You can easily deploy Kong as a Docker container for a portable and isolated environment. Use the official Kong Docker image from Docker Hub site.
5. Cloud-based Deployments:
Most major cloud providers offer managed Kong services, allowing you to quickly deploy and manage Kong in your cloud environment.
Basic Tutorials of Kong: Getting Started

Kong is a powerful API gateway, offering features like traffic management, security, and observability for your microservices. so, let’s have a look at some step-by-step tutorials to get you started:
1. Installation:
- Docker:
- Pull the Kong Docker image:
docker pull kong:latest - Run the container:
docker run -d -p 8000:8000 kong:latest - Access Kong UI: http://localhost:8000
- Pull the Kong Docker image:
- Helm:
- Add the Kong Helm repository:
helm repo add kong https://charts.konghq.com/kong - Install Kong:
helm install kong kong/kong - Access Kong UI: http://localhost:8000
- Add the Kong Helm repository:
- Native Installation:
- Follow the official Kong installation guide.
2. Creating a Service:
- Go to the
Servicestab in the Kong UI. - Click
Add Service. - Enter a name for your service (e.g.,
my-api). - Optionally, enter the upstream host and port (e.g., your backend API server).
- Click
Save.
3. Creating a Route:
- Go to the
Routestab. - Click
Add Route. - Select the service you created.
- Enter a path for your route (e.g.,
/api/users). - Click
Save.
4. Testing your API:
- Use tools like Postman or curl to send requests to your Kong gateway endpoint (e.g., http://localhost:8000/api/users).
- If everything is configured correctly, you should receive a response from your backend API.
5. Additional Tutorials:
- Authentication & Authorization:
- <invalid URL removed>
- Rate Limiting & Traffic Management:
- <invalid URL removed>
- Adding Plugins:
- <invalid URL removed>
Tips:
- Use the Kong Playground (<invalid URL removed>) to experiment with Kong features before deploying to production.
Note:
- These tutorials provide a basic introduction to Kong.
- It’s crucial to understand your specific needs and environment before using Kong in production.
- Secure your Kong deployment with proper authentication, authorization, and access control measures.
By following these step-by-step tutorials and exploring the resources provided, you can gain a solid foundation for using Kong to manage and secure your APIs.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
