Thanks for pointing that out! The AWS EKS authentication method has changed in 2025, and the aws-auth ConfigMap is no longer used for adding IAM roles. Instead, IAM Access entries are managed under the Access tab in the AWS Console.
Here are the updated steps to manually grant your Federated IAM User access to kubectl in AWS EKS.
 Step 1: Identify Your Federated IAM Role
Step 1: Identify Your Federated IAM Role
- Go to AWS Console → IAM → Roles
- Find the IAM Role associated with your Federated User (SSO/Federated Access).
- Copy the Role ARN, which looks like:
arn:aws:iam::329599659644:role/<Federated-Role-Name>
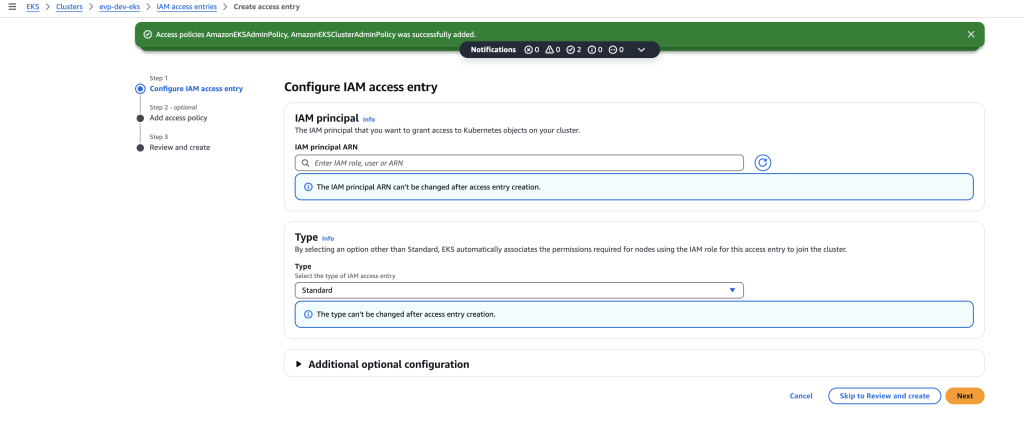
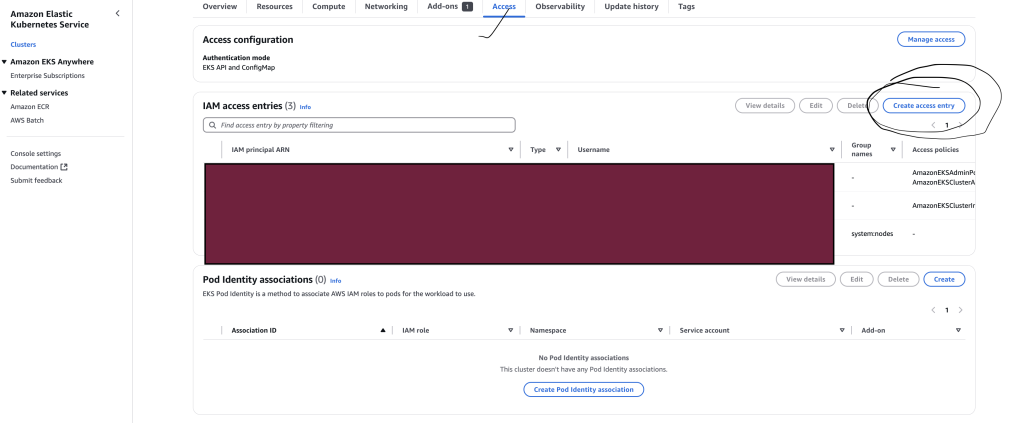
 Step 2: Add the Federated IAM Role in EKS “Access” Tab
Step 2: Add the Federated IAM Role in EKS “Access” Tab
- Go to AWS Console → EKS → Your Cluster (
evp-dev-eks) - Click the Access tab.
- Click “Add IAM access entry”.
- Select IAM Role.
- Paste your Federated Role ARN (
arn:aws:iam::329599659644:role/<Federated-Role-Name>). - Assign a Cluster Role:
- Choose Administrator Access (Full
kubectlpermissions) →system:masters - Alternatively, choose Read-Only Access (
View-Onlyrole).
- Choose Administrator Access (Full
- Click “Save Changes”.
 Step 3: Attach Required IAM Policies to the Federated Role
Step 3: Attach Required IAM Policies to the Federated Role
Your Federated IAM Role must have the following policies:
Attach Policies to Your Role
- Go to AWS Console → IAM → Roles →
<Federated-Role-Name> - Click Permissions → Attach Policies
- Add the following policies:
AmazonEKSClusterPolicyAmazonEKSWorkerNodePolicyAmazonEKSServicePolicyeks:AccessKubernetesApi
- Click Attach Policy.
 Step 4: Update
Step 4: Update kubeconfig for Federated User
Once IAM access is set, update your local kubeconfig to reflect the changes:
aws eks update-kubeconfig --name evp-dev-eks --region ap-northeast-1 --role-arn arn:aws:iam::329599659644:role/<Federated-Role-Name>
Then test access:
kubectl get nodes
 Step 5: Verify Access
Step 5: Verify Access
If kubectl get nodes still fails, check:
kubectl auth can-i list nodes --all-namespaces --verbose
- If “yes”, you have access.
- If “no”, IAM role or permissions need adjustment.
 Summary of AWS 2025 EKS Changes
Summary of AWS 2025 EKS Changes



I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
