Azure Network Security Groups (NSGs) act as firewalls to control inbound and outbound network traffic flowing to your Azure resources within a virtual network. They enforce security policies by allowing or denying traffic based on predefined rules.
Azure Network Security Groups (NSGs) are a fundamental component of Azure networking, providing a critical layer of security by implementing a set of filtering rules that control inbound and outbound traffic to network interfaces (NIC), virtual machine (VM) instances, and subnets. NSGs can be used to enforce and control network traffic flow at various levels of the Azure Virtual Network, offering both segmentation and protection of virtual networks and VMs. Here’s an overview of key aspects and functionality of NSGs:
Here’s a breakdown of key aspects of NSGs:
- Functionality: Filter network traffic to and from VMs and other Azure resources in your virtual network.
- Components:
- Security rules: Define what traffic is allowed (permit) or denied (deny) based on:
- Source and destination (IP addresses, CIDR blocks, service tags)
- Ports
- Protocol (TCP, UDP, etc.)
- Default security rules: NSGs come with pre-configured rules allowing basic communication. You can customize these rules.
- Security rules: Define what traffic is allowed (permit) or denied (deny) based on:
- Association:
- Attached to a subnet: The rules apply to all VMs within that subnet.
- Attached to individual VMs: Provides more granular control over specific VMs.
- Processing order:
- Outbound traffic: Evaluated by NSG on the network interface (if present) first, then by the subnet’s NSG (if applicable).
Benefits of NSGs:
- Improved security: Refine access to your resources by restricting unwanted traffic.
- Network segmentation: Isolate different parts of your virtual network for better security control.
- Simplified management: Apply security rules to a subnet for consistent policy enforcement across multiple VMs.
Here are some helpful resources to learn more about NSGs:
- Microsoft Azure documentation: https://learn.microsoft.com/en-us/azure/virtual-network/network-security-groups-overview
- How to create Azure network security groups (NSGs): https://docs.aviatrix.com/documentation/latest/network-security/secure-networking-intraVPC.html?expand=true
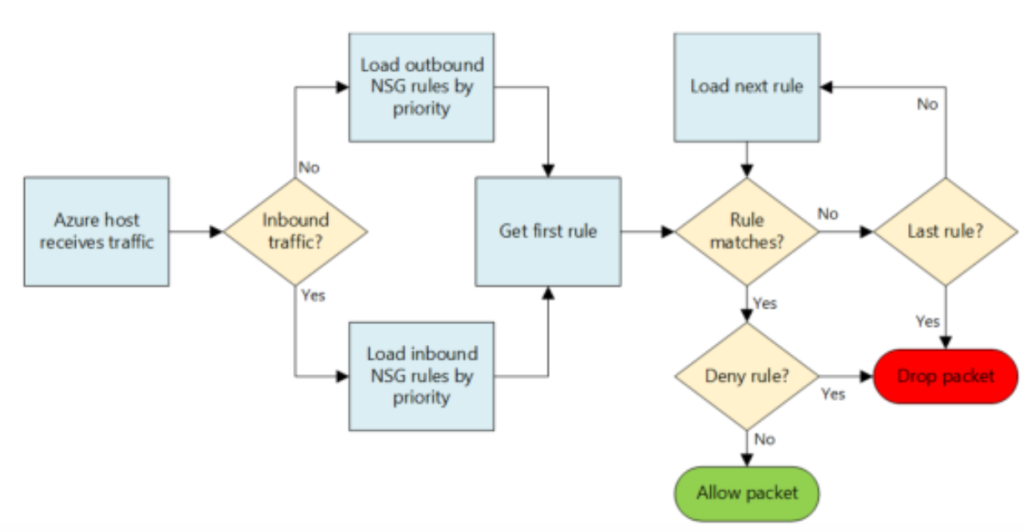
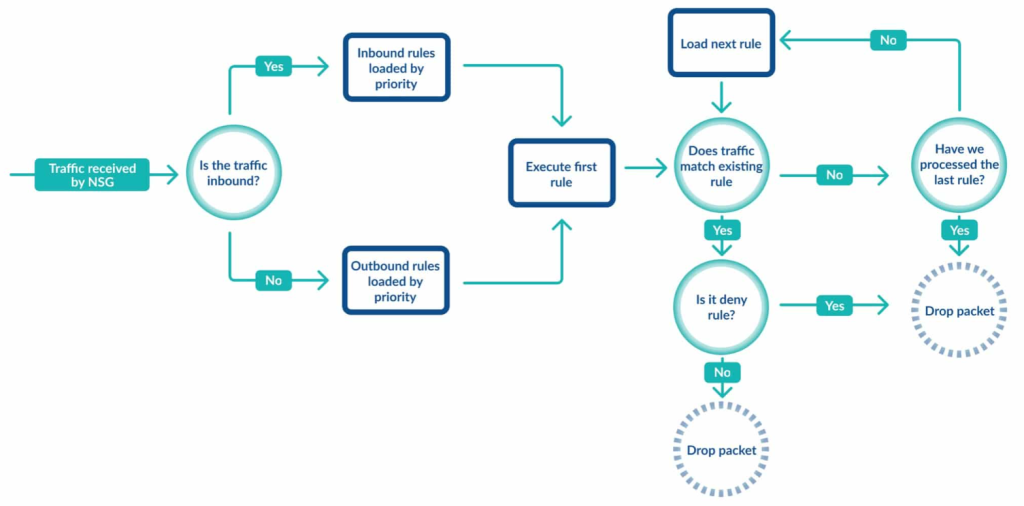
1. Functionality and Use Cases
- Traffic Filtering: NSGs filter traffic at the IP address, port, and protocol level. They can allow or deny network traffic to Azure resources based on several properties, including source/destination IP addresses, ports, and the protocol used for the traffic.
- Association: NSGs can be associated with either subnets within an Azure Virtual Network or individual VM instances. When associated with a subnet, the rules apply to all resources connected to the subnet. If associated directly with a VM, the rules apply only to that VM.
- Inbound and Outbound Rules: NSGs contain separate rules for inbound and outbound traffic, allowing granular control over the flow of data. Rules are processed in priority order, from lowest to highest, with the first rule that matches the traffic (based on priority) being applied.
2. Components of NSGs
- Rules: Each NSG contains a list of rules that define how traffic is filtered. These rules specify the direction (inbound or outbound), priority, source and destination address prefixes, source and destination ports, protocol (TCP, UDP, ICMP, etc.), and the action (allow or deny).
- Default Rules: NSGs come with default rules that ensure basic connectivity (e.g., allowing outbound internet access) and security (e.g., denying inbound access from the internet). These default rules have the lowest priority and can be overridden by user-defined rules with higher priority.
- Tags: NSGs support the use of service tags in rules. A service tag represents a group of IP address prefixes to help minimize the complexity of frequent updates and management.
3. Best Practices and Considerations
- Least Privilege: Apply the principle of least privilege by allowing only the necessary traffic to and from your Azure resources, and denying all other traffic by default.
- Rule Management: Organize and manage rules carefully, considering their priority and specificity to avoid conflicts and ensure the intended traffic flow.
- Monitoring: Utilize Azure Monitor and diagnostic logs to monitor NSG flow logs for auditing and troubleshooting network traffic to and from resources associated with NSGs.
- Integration with Other Azure Services: NSGs can be integrated with other Azure services like Azure Load Balancer and Azure Application Gateway for enhanced functionality and security.
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
