Step – Setup Dedicated AWS VPC
Step – Deploy EKS
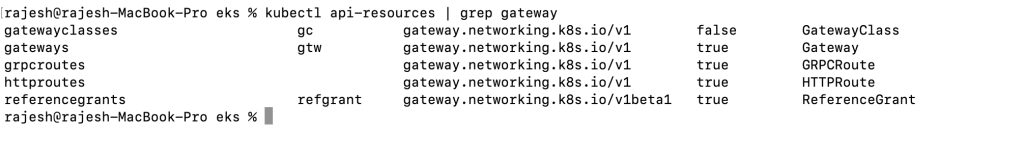
Step – Installing a Kubernetes Gateway API
$ kubectl apply -f https://github.com/kubernetes-sigs/gateway-api/releases/download/v1.2.0/standard-install.yaml
$ kubectl api-resources | grep gateway
Step – AWS Security group Change Requirement
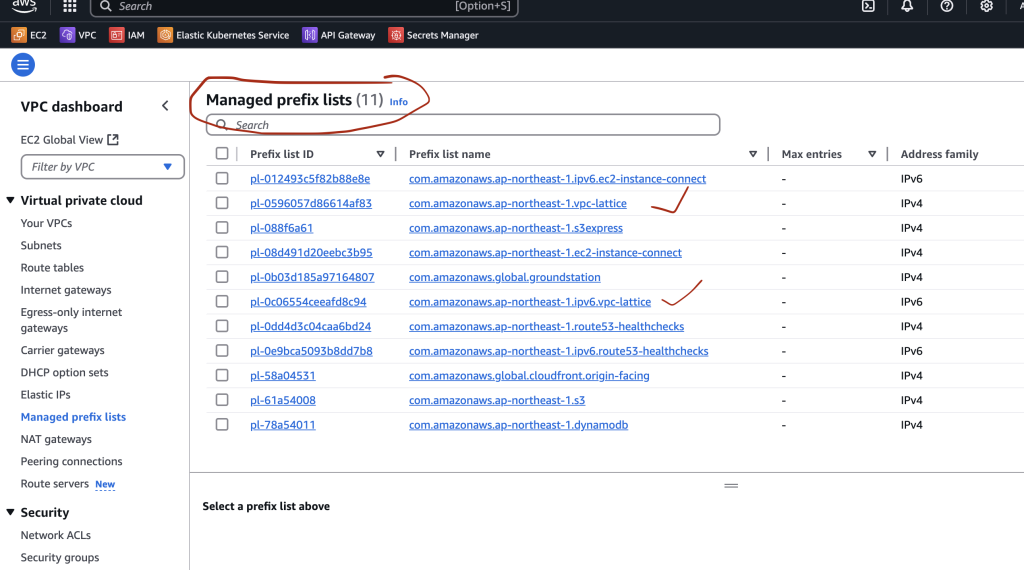
Amazon VPC Lattice is a fully managed service by AWS that simplifies service-to-service communication across VPCs and accounts. The CIDR blocks used by VPC Lattice are assigned and managed by AWS and are available through managed prefix lists for both IPv4 and IPv6.
To allow communication between your workloads (e.g., Pods in EKS) and VPC Lattice services, you must configure security groups, network ACLs, or resource policies to allow traffic from these AWS-managed prefix lists
Prefix List: A prefix list is a set of CIDR blocks (e.g., 192.0.2.0/24 for IPv4 or 2001:db8::/32 for IPv6) that represent a group of IP addresses.
AWS-managed prefix lists for services like VPC Lattice can be used in:
Security Groups
Route Tables
Network ACLs
Resource Policies
Security Groups Created by AWS for EKS
- Cluster Security Group (Control Plane to Worker Nodes)
- Node Security Group (Worker Nodes)
- Fargate Profile Security Group (if using AWS Fargate)
| How to know Cluster Security Group? | |
| $ export AWS_REGION=<cluster_region> | |
| $ export CLUSTER_NAME=<cluster_name> | |
| $ export AWS_REGION=ap-northeast-1 | |
| $ export CLUSTER_NAME=test-1 | |
| $ CLUSTER_SG=$(aws eks describe-cluster --name $CLUSTER_NAME --output json| jq -r '.cluster.resourcesVpcConfig.clusterSecurityGroupId') | |
| $ echo $CLUSTER_SG | |
| How to Configure the EKS nodes' security group to receive traffic from the VPC Lattice network. | |
| $ PREFIX_LIST_ID=$(aws ec2 describe-managed-prefix-lists --query "PrefixLists[?PrefixListName=="\'com.amazonaws.$AWS_REGION.vpc-lattice\'"].PrefixListId" | jq -r '.[]') | |
| $ echo $PREFIX_LIST_ID | |
| $ aws ec2 authorize-security-group-ingress --group-id $CLUSTER_SG --ip-permissions "PrefixListIds=[{PrefixListId=${PREFIX_LIST_ID}}],IpProtocol=-1" | |
| $ PREFIX_LIST_ID_IPV6=$(aws ec2 describe-managed-prefix-lists --query "PrefixLists[?PrefixListName=="\'com.amazonaws.$AWS_REGION.ipv6.vpc-lattice\'"].PrefixListId" | jq -r '.[]') | |
| $ echo $PREFIX_LIST_ID_IPV6 | |
| $ aws ec2 authorize-security-group-ingress --group-id $CLUSTER_SG --ip-permissions "PrefixListIds=[{PrefixListId=${PREFIX_LIST_ID_IPV6}}],IpProtocol=-1" |


I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
 by
by 