
The following are the best cloud security tools in 2023:
- Amazon Web Services (AWS) Security Hub is a unified console that provides a comprehensive view of your security posture across AWS services. It can help you identify and remediate security misconfigurations, monitor for threats, and comply with regulations.
- Microsoft Azure Security Center is a cloud-based service that helps you protect your Azure resources from threats. It provides insights into your security posture, helps you identify and remediate security vulnerabilities, and automates security tasks.

- Google Cloud Security Command Center is a unified console that provides visibility and control over your Google Cloud Platform (GCP) security posture. It can help you identify and remediate security risks, monitor for threats, and comply with regulations.
- Cisco Cloudlock is a cloud security platform that provides a wide range of security features, including threat protection, compliance monitoring, and data loss prevention. It can help you protect your cloud workloads from a variety of threats.
- Palo Alto Networks Prisma Cloud is a cloud security platform that provides a comprehensive view of your cloud security posture. It can help you identify and remediate security misconfigurations, monitor for threats, and comply with regulations.

These are just a few of the many cloud security tools available. The ideal tool for you will depend on your specific needs and demands.
Here are some other factors to consider when choosing a cloud security tool:
- The type of cloud environment you are using (AWS, Azure, GCP, etc.)
- The size and complexity of your cloud environment
- The specific security threats you are facing
- Your budget
It is important to have a comprehensive cloud security strategy in place to protect your data and applications. Cloud security tools can help you implement this strategy and protect your cloud environment from a variety of threats.
Some of the top 5 cloud computing security challenges:
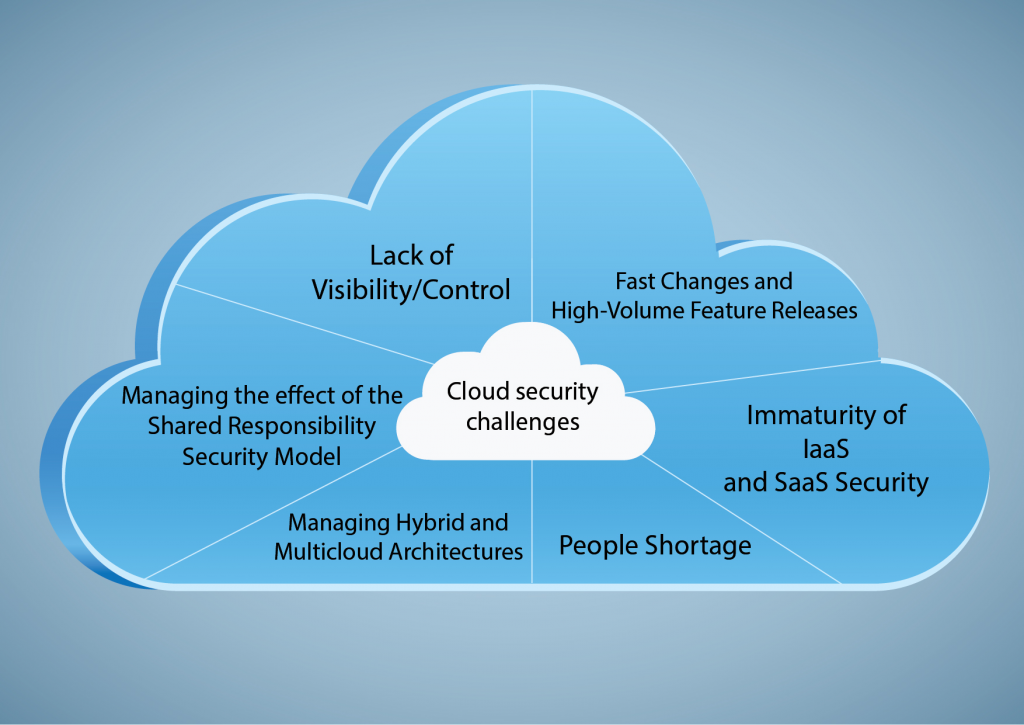
- Misconfiguration: This is the most common cloud security challenge. It happens when cloud resources are not configured correctly, which can leave them unsafe to attack.
- Unauthorized access: This can happen when someone gains access to your cloud resources without authorization. This can be done through stolen passwords, phishing attacks, or other means.
- Data loss: This can occur if your cloud data is not properly protected. This can happen through data breaches, ransomware attacks, or other means.
- Malware injection: This is when malicious code is injected into your cloud environment. This can be done through phishing attacks, infected websites, or other means.
- Restricted access to network operations: This can happen when cloud administrators do not have the right level of access to network operations. This can make it difficult to detect and respond to security threats.
By understanding the top cloud security challenges, you can take steps to mitigate them and protect your cloud environment.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
