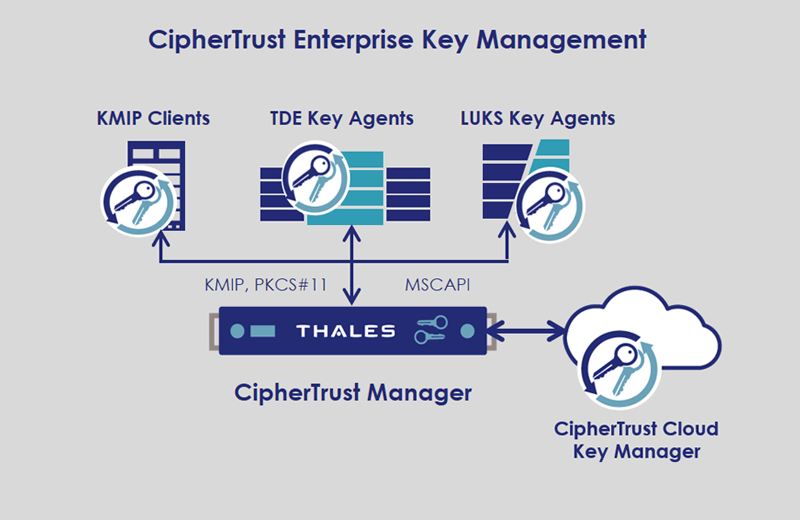
The following are the best encryption and key management tools:
- HashiCorp Vault is a popular open-source tool for secrets management. It can be used to store and manage encryption keys, passwords, and other sensitive data. Vault is highly scalable and can be deployed on-premises or in the cloud.
- Microsoft Azure Key Vault is a cloud-based key management service that can be used to store and manage encryption keys. Key Vault is highly secure and offers a variety of features, such as key rotation, auditing, and role-based access control.

- AWS Key Management Service (KMS) is a cloud-based key management service that is offered by Amazon Web Services. KMS is highly scalable and can be used to store and manage encryption keys for a variety of AWS services.
- Google Cloud Key Management Service is a cloud-based key management service that is offered by Google Cloud Platform. Key Management Service is highly scalable and can be used to store and manage encryption keys for a variety of Google Cloud Platform services.
- Venafi Trust Protection Platform is a comprehensive key management solution that can be used to protect sensitive data in transit and at rest. Trust Protection Platform offers a variety of features, such as key rotation, auditing, and role-based access control.

These are just a few of the many encryption and key management tools available. The best tool for you will depend on your specific needs and requirements.
Some factors to consider when choosing an encryption and key management tool:
- The type of data you need to protect. Some tools are better suited for protecting certain types of data, such as passwords or credit card numbers.
- The size of your organization. Some tools are more scalable than others and can be used by organizations of all sizes.
- Your budget. Encryption and key management tools can range in price from free to thousands of dollars per year.
- Your security requirements. Some tools offer more security features than others.
It is important to carefully evaluate your needs and requirements before choosing an encryption and key management tool. By doing so, you can help to ensure that your data is protected from unauthorized access.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
