Terraform is a popular open-source infrastructure as code tool used to create and manage infrastructure resources. The state of the infrastructure resources managed by Terraform is stored in a backend, which can be a remote storage location such as Amazon S3.
To configure Terraform to use an S3 backend, you will need to perform the following steps:
- Create an S3 bucket – create a new S3 bucket or use an existing one for storing the Terraform state file.
- Create an S3 access key – generate an access key and secret key with the appropriate permissions for accessing the S3 bucket.
- Configure Terraform backend – add the following code block to your Terraform configuration file, replacing the values with your specific S3 bucket and access key information:
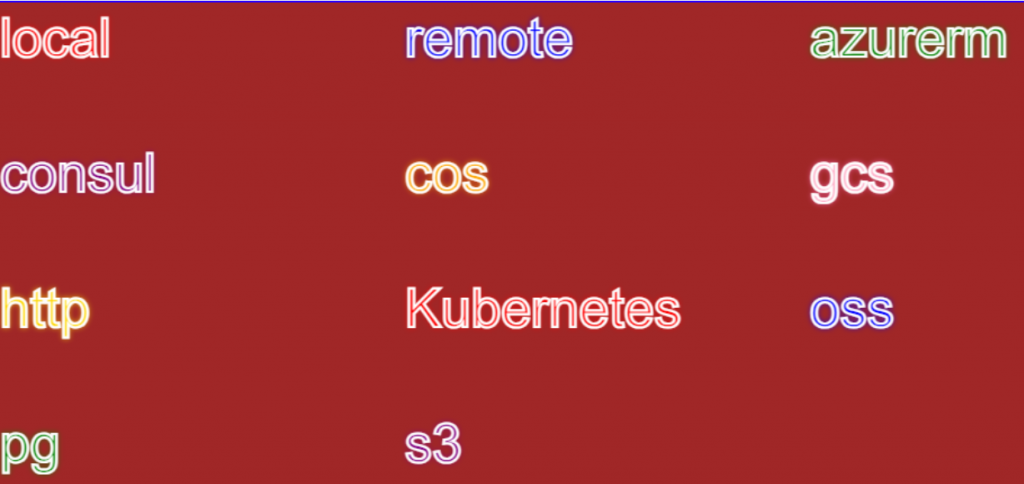
List of Terraform Backends Options
Terraform uses backends to determine how the state is loaded and how an operation such as apply is executed. The backend configuration can control where the state is stored and how the operations are executed.
Here’s a list of commonly used Terraform backends:
- Local:
- Stores state on the local filesystem.
- Executes operations locally.
- Remote:
- Uses the Terraform Cloud to store state and optionally execute operations.
- It’s the default backend for Terraform Cloud workspaces.
- Consul:
- Stores the state in Consul’s key/value store.
- Executes operations locally.
- AzureRM:
- Stores the state in an Azure Storage Blob.
- Executes operations locally.
- S3:
- Stores state in an Amazon S3 bucket.
- It can use DynamoDB for state locking and consistency.
- Executes operations locally.
- Google Cloud Storage (GCS):
- Stores state in a Google Cloud Storage bucket.
- Executes operations locally.
- Swift:
- Stores state in OpenStack Swift.
- Executes operations locally.
- Artifactory:
- Stores state in JFrog Artifactory.
- Executes operations locally.
- Etcd V2 & V3:
- Store the state in Etcd’s key/value store.
- Executes operations locally.
- Manta:
- Stores the state in Joyent’s Manta service.
- Executes operations locally.
- OSS:
- Stores state in Alibaba Cloud Object Storage Service.
- Executes operations locally.
- Pg:
- Stores state within a configured PostgreSQL database.
- Executes operations locally.
- Kubernetes:
- Stores state within a Kubernetes Secret.
- Executes operations locally.
terraform {
backend "s3" {
bucket = "your-bucket-name"
key = "path/to/terraform.tfstate"
region = "your-aws-region"
access_key = "your-access-key"
secret_key = "your-secret-key"
}
}Initialize the backend – run the terraform init command to initialize the backend configuration and create the state file in the S3 bucket.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "~> 4.0"
}
}
backend "s3" {
bucket = "art54654654546546456"
key = "aug"
region = "ap-south-1"
access_key = ""
secret_key = ""
}
}
# Configure the AWS Provider
provider "aws" {
region = "ap-south-1"
access_key = ""
secret_key = ""
}Terraform Backend Credentail Pass Through Command line
$ terraform init -backend-config=”access_key=ASSSSSSSSSSSSSY” -backend-config=”secret_key=VddddddddddddddG” -reconfigure
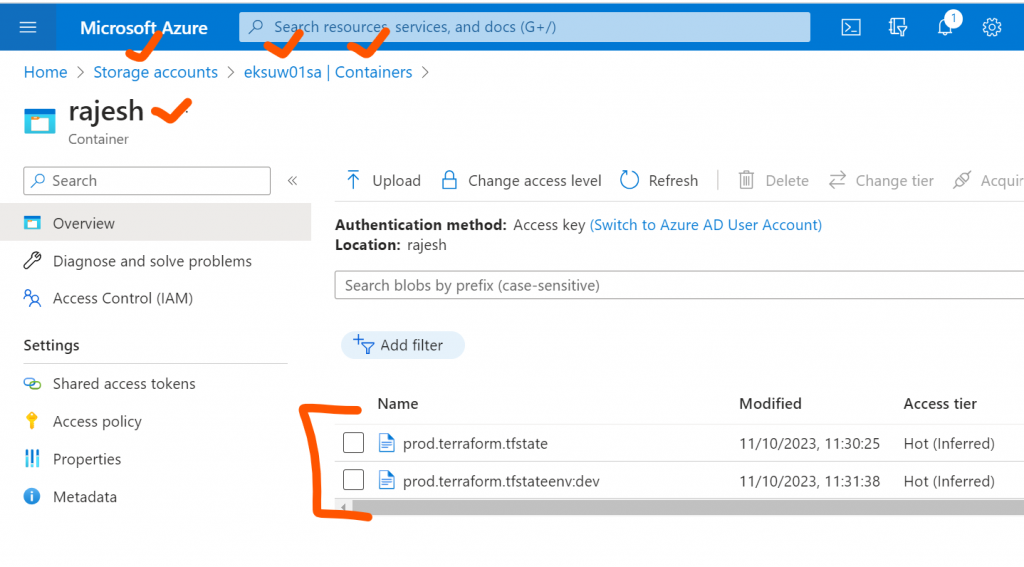
How to Setup Terraform Backend with Azure Blob Container?
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "3.75.0"
}
aws = {
source = "hashicorp/aws"
version = "5.20.0"
}
github = {
source = "integrations/github"
version = "5.39.0"
}
}
backend "azurerm" {
resource_group_name = "eksuw01-rg"
storage_account_name = "eksuw01sa"
container_name = "rajesh"
key = "prod.terraform.tfstate"
subscription_id = "b3dbe884-c3dc"
client_id = "6046fe74-dfd2-4"
client_secret = "3XJ8Q~uvlwVL"
tenant_id = "f34c8fc4-16b"
}
}
provider "azurerm" {
features {}
subscription_id = "b3dbe884c"
client_id = "6046fe74-d"
client_secret = "3XJ8Q~uvlwV"
tenant_id = "f34c8fc4-1"
}I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
