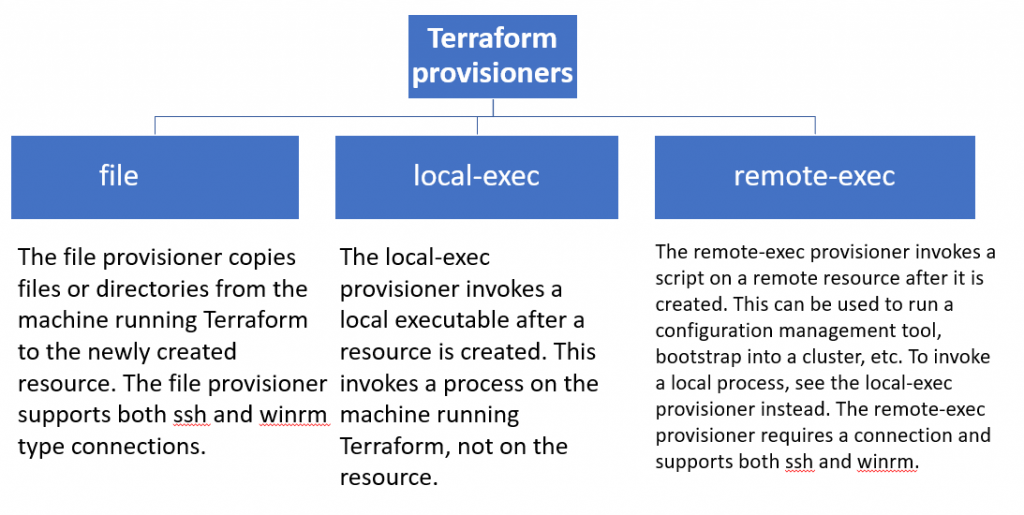
| resource "aws_instance" "first-ec2" { | |
| ami = "ami-03d5c68bab01f3496" # us-west-2 | |
| instance_type = "t2.micro" | |
| key_name = "rajesh-last" | |
| tags = { | |
| Name = "RajeshKumar" | |
| } | |
| connection { | |
| type = "ssh" | |
| user = "ubuntu" | |
| private_key = file("rajesh-last.pem") | |
| #host = aws_instance.web.public_ip | |
| host = self.public_ip | |
| } | |
| provisioner "local-exec" { | |
| command = "touch devopsschool-local" | |
| } | |
| provisioner "remote-exec" { | |
| inline = [ | |
| "sudo apt-get update", | |
| "sudo apt-get install apache2 -y", | |
| "sudo systemctl start apache2", | |
| ] | |
| } | |
| provisioner "file" { | |
| source = "terraform.tfstate.backup" | |
| destination = "/tmp/" | |
| } | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # ENVIRONMENT VARIABLES | |
| # Define these secrets as environment variables | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # AWS_ACCESS_KEY_ID | |
| # AWS_SECRET_ACCESS_KEY | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # REQUIRED PARAMETERS | |
| # You must provide a value for each of these parameters. | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| variable "key_pair_name" { | |
| description = "The EC2 Key Pair to associate with the EC2 Instance for SSH access." | |
| type = string | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # OPTIONAL PARAMETERS | |
| # These parameters have reasonable defaults. | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| variable "aws_region" { | |
| description = "The AWS region to deploy into" | |
| type = string | |
| default = "us-east-1" | |
| } | |
| variable "instance_name" { | |
| description = "The Name tag to set for the EC2 Instance." | |
| type = string | |
| default = "terratest-example" | |
| } | |
| variable "ssh_port" { | |
| description = "The port the EC2 Instance should listen on for SSH requests." | |
| type = number | |
| default = 22 | |
| } | |
| variable "ssh_user" { | |
| description = "SSH user name to use for remote exec connections," | |
| type = string | |
| default = "ubuntu" | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # PIN TERRAFORM VERSION TO >= 0.12 | |
| # The examples have been upgraded to 0.12 syntax | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| terraform { | |
| required_version = ">= 0.12" | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # DEPLOY AN INSTANCE, THEN TRIGGER A PROVISIONER | |
| # See test/terraform_ssh_example.go for how to write automated tests for this code. | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| provider "aws" { | |
| region = var.aws_region | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # DEPLOY THE EC2 INSTANCE WITH A PUBLIC IP | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| resource "aws_instance" "example_public" { | |
| ami = data.aws_ami.ubuntu.id | |
| instance_type = "t2.micro" | |
| vpc_security_group_ids = [aws_security_group.example.id] | |
| key_name = var.key_pair_name | |
| # This EC2 Instance has a public IP and will be accessible directly from the public Internet | |
| associate_public_ip_address = true | |
| tags = { | |
| Name = "${var.instance_name}-public" | |
| } | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # CREATE A SECURITY GROUP TO CONTROL WHAT REQUESTS CAN GO IN AND OUT OF THE EC2 INSTANCES | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| resource "aws_security_group" "example" { | |
| name = var.instance_name | |
| egress { | |
| from_port = 0 | |
| to_port = 0 | |
| protocol = "-1" | |
| cidr_blocks = ["0.0.0.0/0"] | |
| } | |
| ingress { | |
| from_port = var.ssh_port | |
| to_port = var.ssh_port | |
| protocol = "tcp" | |
| # To keep this example simple, we allow incoming SSH requests from any IP. In real-world usage, you should only | |
| # allow SSH requests from trusted servers, such as a bastion host or VPN server. | |
| cidr_blocks = ["0.0.0.0/0"] | |
| } | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # Provision the server using remote-exec | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| resource "null_resource" "example_provisioner" { | |
| triggers = { | |
| public_ip = aws_instance.example_public.public_ip | |
| } | |
| connection { | |
| type = "ssh" | |
| host = aws_instance.example_public.public_ip | |
| user = var.ssh_user | |
| port = var.ssh_port | |
| agent = true | |
| } | |
| // copy our example script to the server | |
| provisioner "file" { | |
| source = "files/get-public-ip.sh" | |
| destination = "/tmp/get-public-ip.sh" | |
| } | |
| // change permissions to executable and pipe its output into a new file | |
| provisioner "remote-exec" { | |
| inline = [ | |
| "chmod +x /tmp/get-public-ip.sh", | |
| "/tmp/get-public-ip.sh > /tmp/public-ip", | |
| ] | |
| } | |
| provisioner "local-exec" { | |
| # copy the public-ip file back to CWD, which will be tested | |
| command = "scp -o StrictHostKeyChecking=no -o UserKnownHostsFile=/dev/null ${var.ssh_user}@${aws_instance.example_public.public_ip}:/tmp/public-ip public-ip" | |
| } | |
| } | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| # LOOK UP THE LATEST UBUNTU AMI | |
| # --------------------------------------------------------------------------------------------------------------------- | |
| data "aws_ami" "ubuntu" { | |
| most_recent = true | |
| owners = ["099720109477"] # Canonical | |
| filter { | |
| name = "virtualization-type" | |
| values = ["hvm"] | |
| } | |
| filter { | |
| name = "architecture" | |
| values = ["x86_64"] | |
| } | |
| filter { | |
| name = "image-type" | |
| values = ["machine"] | |
| } | |
| filter { | |
| name = "name" | |
| values = ["ubuntu/images/hvm-ssd/ubuntu-xenial-16.04-amd64-server-*"] | |
| } | |
| } | |
| output "public_instance_id" { | |
| value = aws_instance.example_public.id | |
| } | |
| output "public_instance_ip" { | |
| value = aws_instance.example_public.public_ip | |
| } |
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
 by
by 