
Have you ever wondered what the best practices for SecOps are? Well, wonder no more! In this article, we will dive deep into the world of SecOps and explore the best practices for maintaining a secure and efficient operation.
What is SecOps?
SecOps, short for Security Operations, is a term used to describe the integration of security practices into the DevOps process. It is a collaborative effort between security and operations teams that aims to ensure that security is integrated into the entire software development life cycle.
The goal of SecOps is to create a culture of security within organizations by implementing security practices early on in the development process and making security a shared responsibility across all teams.
The Importance of SecOps Best Practices
In today’s world, security threats are constantly evolving, and organizations need to be proactive in their approach to security. Implementing SecOps best practices is essential to ensure that an organization is prepared to deal with any security threats that may arise.
By following best practices, organizations can reduce the risk of security breaches, ensure compliance with regulations, and maintain the trust of their customers.
SecOps Best Practices
Now that we understand the importance of SecOps, let’s dive into the best practices that organizations should follow to maintain a secure and efficient operation.
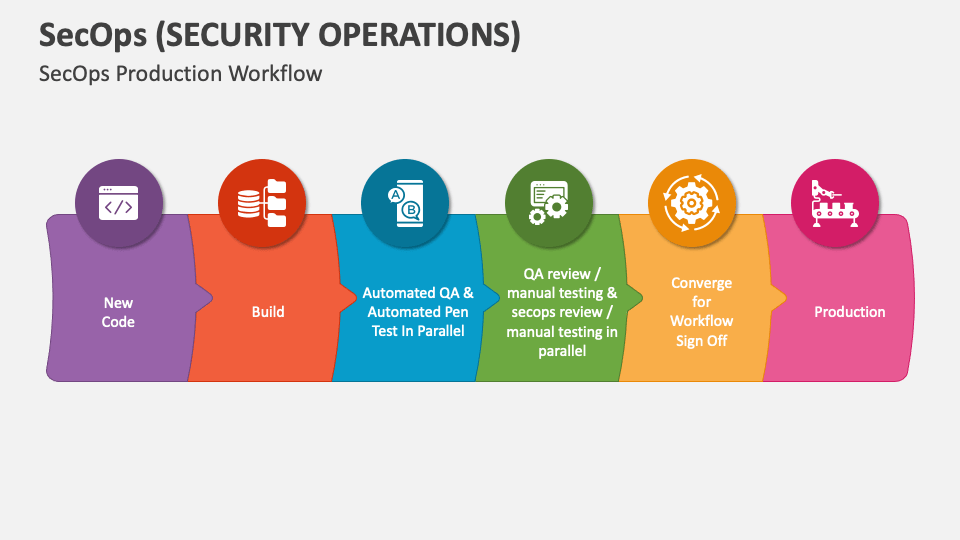
Integration of Security into DevOps
The first and most crucial best practice for SecOps is the integration of security into the DevOps process. This means that security should be considered at every stage of the software development life cycle, from planning to deployment.
By integrating security into DevOps, organizations can identify and address security issues early on in the development process, reducing the risk of security breaches.
Continuous Monitoring
Continuous monitoring is another best practice for SecOps. It involves monitoring systems and applications in real-time to identify any security threats or vulnerabilities.
By continuously monitoring systems, organizations can quickly detect and respond to any security incidents, reducing the impact of a security breach.
Risk Assessment
Risk assessment is the process of identifying potential security risks and vulnerabilities and assessing their likelihood and impact.
By conducting regular risk assessments, organizations can identify areas of weakness and take steps to mitigate potential risks.
Employee Training
Employee training is another critical best practice for SecOps. All employees, from developers to executives, should receive regular training on security best practices and policies.
By educating employees on security, organizations can create a culture of security, where everyone understands their role in maintaining a secure operation.
Incident Response
Incident response is the process of responding to a security incident, such as a data breach or cyber attack.
By having a well-defined incident response plan in place, organizations can respond quickly and effectively to any security incidents, minimizing the impact on the organization.
Compliance
Finally, compliance with regulatory requirements is a crucial best practice for SecOps. Organizations must comply with regulations such as GDPR, HIPAA, and PCI-DSS.
By complying with regulations, organizations can avoid costly fines and maintain the trust of their customers.
Conclusion

In conclusion, SecOps is a critical component of any organization’s security strategy. By following best practices such as integrating security into DevOps, continuous monitoring, risk assessment, employee training, incident response, and compliance, organizations can maintain a secure and efficient operation.
Remember, security is everyone’s responsibility, and by working together, we can create a culture of security that protects our organizations from the ever-evolving world of security threats.
Related video:
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
