What is AlienVault?

AlienVault is a unified security management platform developed by AT&T Cybersecurity (formerly known as AlienVault). It provides a wide range of security and threat detection capabilities, including intrusion detection, vulnerability assessment, security information and event management (SIEM), and threat intelligence. AlienVault is designed to help organizations of all sizes improve their security posture and effectively respond to threats.
It’s worth noting that AlienVault has been integrated into the AT&T Cybersecurity portfolio and is now part of AT&T Managed Threat Detection and Response (MTDR) services. This integration enhances its capabilities and extends its reach for larger organizations. AlienVault is a versatile platform that can be tailored to specific security needs, making it a valuable asset for improving an organization’s overall cybersecurity posture.
Top 10 use cases of AlienVault:
Here are the top 10 use cases of AlienVault:
- Threat Detection: AlienVault collects and analyzes security event data from various sources, including network traffic, log files, and host-based data. It uses correlation rules and behavioral analysis to identify and alert on suspicious or malicious activity.
- SIEM (Security Information and Event Management): AlienVault acts as a SIEM platform, aggregating and correlating data from multiple sources, such as firewalls, intrusion detection systems, and endpoint devices. It provides a centralized view of security events and incidents.
- Intrusion Detection and Prevention: The platform includes intrusion detection and prevention capabilities that monitor network traffic and alert on potentially malicious activity or known attack patterns.
- Vulnerability Assessment: AlienVault can scan network assets and systems for vulnerabilities, providing organizations with insights into potential weaknesses that could be exploited by attackers.
- Log Management: It collects, stores, and manages logs and event data from various devices and applications, helping organizations comply with regulatory requirements and aiding in forensic investigations.
- Incident Response: AlienVault provides incident response capabilities, helping security teams investigate and respond to security incidents promptly and effectively.
- Asset Discovery: The platform can automatically discover and inventory assets on the network, helping organizations maintain an up-to-date asset inventory for security and compliance purposes.
- Threat Intelligence Integration: AlienVault integrates with threat intelligence feeds and databases to provide context and enrichment for security events, helping organizations stay informed about emerging threats.
- Compliance Management: AlienVault assists organizations in meeting compliance requirements by providing reports and documentation needed for compliance audits, such as PCI DSS, HIPAA, and GDPR.
- Security Awareness and Education: AlienVault includes features for security awareness and education, helping organizations train employees and raise security awareness throughout the organization.
What are the feature of AlienVault?
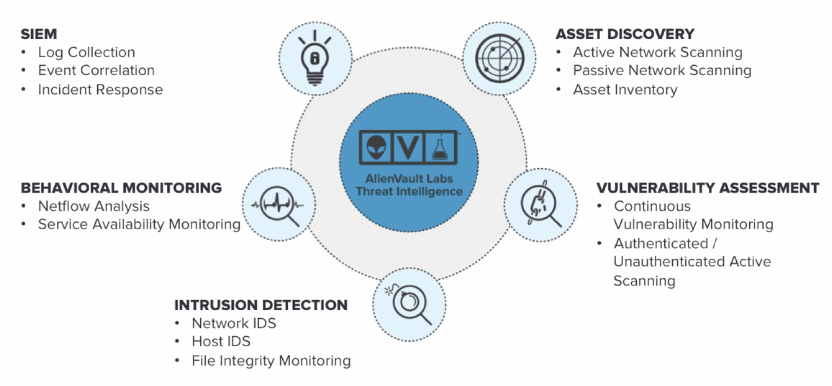
AlienVault, now known as AT&T Managed Threat Detection and Response (MTDR) services, is a comprehensive security platform that offers a wide range of features to help organizations manage and respond to security threats effectively. While I can provide a general overview of its features and functionality, it’s important to note that the specifics may evolve over time as new versions and updates are released. Here are some of the key features and components of AlienVault:
Key Features of AlienVault:
- SIEM (Security Information and Event Management): AlienVault provides SIEM capabilities, allowing organizations to collect, correlate, and analyze security event data from various sources, including network devices, servers, and applications.
- Asset Discovery: It automatically discovers and inventories assets on the network, helping organizations keep track of their infrastructure and identify vulnerabilities.
- Intrusion Detection and Prevention: AlienVault includes IDS/IPS (Intrusion Detection System/Intrusion Prevention System) functionality to detect and block known attack patterns and suspicious network activity.
- Vulnerability Assessment: The platform can scan systems and applications for vulnerabilities, helping organizations prioritize and remediate security issues.
- Threat Intelligence Integration: AlienVault integrates with threat intelligence feeds and sources to provide context and enrichment for security events, helping organizations stay informed about emerging threats.
- Log Management: It collects, normalizes, and stores log data from various devices and applications for compliance, forensic analysis, and threat detection.
- Incident Response: AlienVault supports incident response efforts with incident tracking, workflow management, and reporting capabilities.
- Security Orchestration and Automation: It includes features for automating security workflows and responses to reduce manual intervention and response times.
- Security Awareness and Training: AlienVault offers features for security awareness and education to help organizations train employees and raise security awareness throughout the organization.
- Compliance Management: The platform helps organizations demonstrate compliance with various regulatory requirements by providing reports and documentation for audits.
How AlienVault works and Architecture?
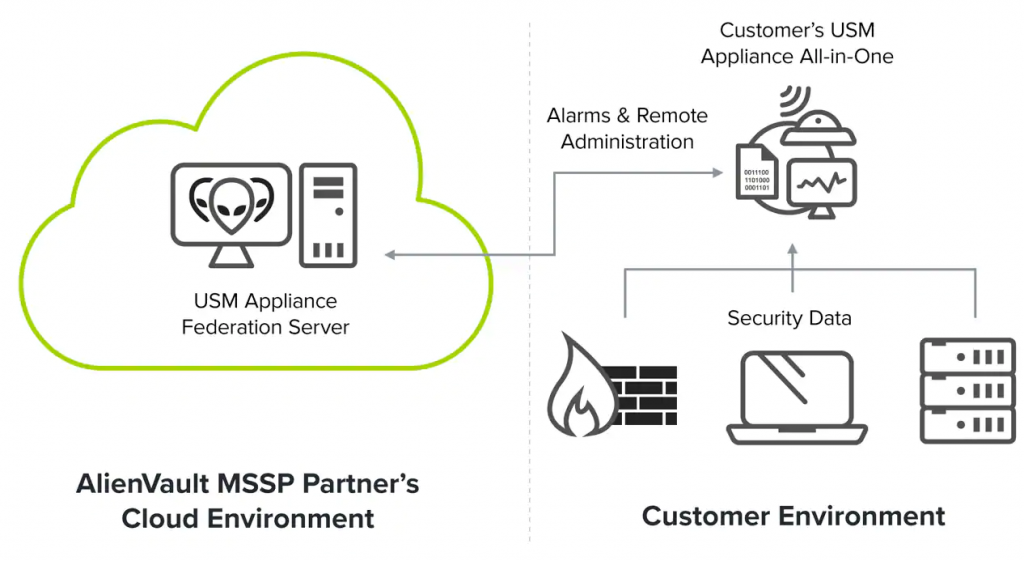
AlienVault operates as a unified security management platform that aggregates, correlates, and analyzes data from various security sources to provide a comprehensive view of an organization’s security posture. Here’s a simplified overview of how it works:
- Data Collection: AlienVault collects data from a wide range of sources, including network devices (e.g., firewalls, routers), servers, endpoints, applications, and security appliances. This data includes logs, events, network traffic, and more.
- Normalization: The collected data is normalized to ensure that it’s in a consistent format for analysis. Normalization helps make sense of data from diverse sources.
- Correlation: AlienVault correlates data from different sources to identify patterns and potential security threats. It uses correlation rules and threat intelligence feeds to detect anomalous and suspicious activities.
- Alerting and Reporting: When a security event or incident is detected, AlienVault generates alerts and provides real-time notifications to security teams. It also generates reports and dashboards for security analysis and compliance reporting.
- Threat Detection and Response: Security teams use AlienVault to investigate and respond to security incidents. It provides tools for analyzing incidents, determining their impact, and taking appropriate actions to mitigate threats.
- Integration with Threat Intelligence: AlienVault integrates with external threat intelligence sources to provide additional context and enrichment for security events, helping security teams make informed decisions.
- Asset Discovery and Vulnerability Scanning: AlienVault continuously discovers and inventories assets on the network. It can also conduct vulnerability assessments to identify and prioritize security weaknesses.
- Compliance Management: The platform assists organizations in maintaining compliance with regulatory requirements by providing compliance reports and documentation for audits.
AlienVault’s architecture typically includes a central server that manages data collection, correlation, and reporting, along with distributed sensors deployed across the network to collect data from various sources. The specifics of the architecture may vary based on the organization’s needs and the version of AlienVault in use.
How to Install AlienVault?
To install AlienVault OSSIM, you will need a virtual machine with the following system requirements:
- CPU: 8 cores
- Memory: 16-24 GB
- Storage: 500 GB-1 TB HDD
Instructions:
- Download the AlienVault OSSIM ISO file from the AlienVault website.
- Create a new virtual machine instance using the ISO as the installation source.
- Once you have initiated the new Debian 8. x 64-bit instance, choose Install AlienVault OSSIM (64 Bit) and press Enter.
- The installation then loads the essential components and detects settings.
- The IP address will be the web address you apply to access the AlienVault OSSIM web UI.
- The installer will then have you set up the root password.
Once the installation is complete, you can access the AlienVault OSSIM web UI at the IP address that was displayed during the installation process. The default username is admin and the password is the root password that you set up during the installation.
Additional Notes:
- AlienVault OSSIM does not favor paravirtualization and needs full virtualization for storage and network.
- If you are installing AlienVault OSSIM in a production environment, it is recommended to follow the AlienVault OSSIM hardening guide to secure your installation.
Some additional tips for installing AlienVault:
- Make sure that your virtual machine has enough resources allocated to it. AlienVault OSSIM is a resource-intensive application, so it is important to give it enough CPU, memory, and storage to run smoothly.
- If you are installing AlienVault OSSIM in a production environment, it is recommended to create a separate VLAN for the AlienVault OSSIM appliance. This will help to isolate the AlienVault OSSIM appliance from the rest of your network and improve security.
- It is also recommended to configure a firewall on the AlienVault OSSIM appliance to restrict access to only authorized users and IP addresses.
Once you have installed AlienVault OSSIM, you can start configuring it to monitor your network for security threats.
Basic Tutorials of AlienVault: Getting Started

Following is the stepwise Basic Tutorial of AlienVault:
1. Getting Started
- Log in to the AlienVault OSSIM web UI. The default username is admin and the password is the root password that you set up during the installation.
- Click the AlienVault logo in the top left corner of the page. This will take you to the main AlienVault OSSIM dashboard.
- Click the Help button in the top right corner of the page. This will open the AlienVault OSSIM help documentation.
- Review the Getting Started section of the help documentation. This will give you a basic overview of AlienVault OSSIM and how to use it.
2. Configuring AlienVault OSSIM
Once you have a basic understanding of AlienVault OSSIM, you can start configuring it to monitor your network for security threats.
- Click the Configuration tab in the top navigation bar.
- Click the Sensors link in the left navigation pane.
- Click the Add Sensor button.
- Select the type of sensor that you want to add and click the Next button.
- Enter the required information for the sensor and click the Finish button.
Repeat steps 3-5 to add all of the sensors that you need to monitor your network.
3. Monitoring Your Network
Once you have configured AlienVault OSSIM to monitor your network, you can start viewing the events that are being collected.
- Click the Monitoring tab in the top navigation bar.
- Click the Events link in the left navigation pane.
- The Events page will display a list of all of the events that have been collected by AlienVault OSSIM.
- You can filter the events by date, time, sensor, source, and other criteria.
4. Responding to Incidents
When AlienVault OSSIM detects a potential security threat, it will generate an alert.
- To view the alerts, click the Alerts tab in the top navigation bar.
- The Alerts page will display a list of all of the alerts that have been generated by AlienVault OSSIM.
- You can filter the alerts by date, time, severity, and other criteria.
- To investigate an alert, click on the alert. This will open the alert details page.
- The alert details page will provide you with more information about the alert, including the source of the event, the type of event, and the severity of the event.
- You can take appropriate action to respond to the incident, such as blocking the IP address of the source or isolating the infected system.
Additional Notes:
- AlienVault OSSIM is a complex application, and it can take some time to learn how to use it effectively.
- AlienVault offers a variety of resources to help you learn how to use AlienVault OSSIM, including training courses, documentation, and support forums.
- If you are new to AlienVault OSSIM, it is recommended that you start by reviewing the Getting Started section of the help documentation.
- You can also find a variety of tutorials and other resources on the AlienVault website.
Some additional tips for using AlienVault:
- Use the Rules and Correlations features to create custom rules to detect specific threats.
- Use the Threat Intelligence feature to stay up-to-date on the latest threats.
- Use the Reporting feature to generate reports on your security posture and threat activity.
- Monitor the System Health dashboard to ensure that your AlienVault OSSIM appliance is running properly.
AlienVault OSSIM is a powerful security tool that can help you to protect your network from security threats. By following the steps above, you can learn how to use AlienVault OSSIM to monitor your network, respond to incidents, and generate reports.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

