What is Aqua Security?

Aqua Security is a container security platform that specializes in securing containerized applications and microservices across various cloud environments. It offers a range of features and capabilities to protect container workloads, ensuring they are secure, compliant, and free from vulnerabilities.
Aqua Security offers a comprehensive approach to container security, helping organizations secure their containerized applications from development to production. It ensures that containers and microservices are protected against security threats, vulnerabilities, and compliance risks, enabling organizations to maintain a strong security posture in modern cloud-native environments.
Top 10 use cases of Aqua Security:
Here are the top 10 use cases of Aqua Security:
- Container Image Scanning: Aqua Security scans container images for known vulnerabilities, malware, and configuration issues during the development phase to prevent insecure images from being deployed.
- Runtime Protection: It provides runtime protection for containerized applications by monitoring and enforcing security policies for running containers, detecting and responding to suspicious activities and threats.
- Vulnerability Management: Aqua Security helps organizations manage vulnerabilities in container images and runtime environments by prioritizing and remediating issues based on their severity.
- Compliance Assurance: Aqua Security ensures containerized applications comply with security and compliance standards, such as CIS Docker Benchmark, NIST 800-190, and specific industry regulations.
- Microservices Security: Organizations can secure individual microservices within their containerized applications, implementing fine-grained access controls and network policies.
- Serverless Security: Aqua Security extends its security capabilities to serverless functions (e.g., AWS Lambda) to protect event-driven serverless applications.
- CI/CD Pipeline Integration: It integrates with continuous integration and continuous deployment (CI/CD) pipelines to automate security checks and enforce policies during image builds and deployments.
- Custom Security Policies: Users can define custom security policies to enforce specific security and compliance requirements tailored to their organization’s needs.
- Network Segmentation: Aqua Security enforces network segmentation policies to control communication between containers and microservices, reducing the attack surface.
- Incident Response: In the event of a security incident, Aqua Security provides incident response capabilities to investigate, contain, and remediate threats within containerized environments.
- Image Assurance in Registries: Aqua Security ensures that container images in registries are continuously assessed for vulnerabilities and compliance violations before being used in deployments.
- Container Registry Scanning: It scans container images stored in container registries to identify vulnerabilities and enforce security policies, ensuring that only secure images are used.
What are the feature of Aqua Security?
Aqua Security is a container security platform that helps organizations secure containerized applications and microservices across various cloud environments. It offers a range of features and capabilities to protect container workloads. Here are the key features of Aqua Security, along with an overview of how it works and its architecture:
Key Features of Aqua Security:
- Image Scanning: Aqua Security scans container images for vulnerabilities, malware, and misconfigurations before they are deployed, ensuring that only secure images are used.
- Vulnerability Management: It provides vulnerability assessment and management, allowing organizations to prioritize and remediate vulnerabilities based on their severity.
- Runtime Protection: Aqua Security monitors containerized applications in runtime, detecting and responding to suspicious activities and potential security threats.
- Compliance Assurance: Organizations can ensure compliance with security standards and industry regulations by using Aqua Security to enforce security policies and compliance checks.
- Microservices Security: Aqua Security offers fine-grained security controls for individual microservices within containerized applications.
- Network Segmentation: It enforces network segmentation policies to control communication between containers and microservices, reducing the attack surface.
- CI/CD Pipeline Integration: Aqua Security integrates with CI/CD pipelines to automate security checks during image builds and deployments, enabling DevSecOps practices.
- Custom Security Policies: Users can create custom security policies tailored to their organization’s specific security and compliance requirements.
- Serverless Security: Aqua Security extends its security capabilities to serverless functions (e.g., AWS Lambda) to protect event-driven serverless applications.
- Incident Response: In the event of a security incident, Aqua Security provides incident response capabilities to investigate, contain, and remediate threats within containerized environments.
How Aqua Security works and Architecture?
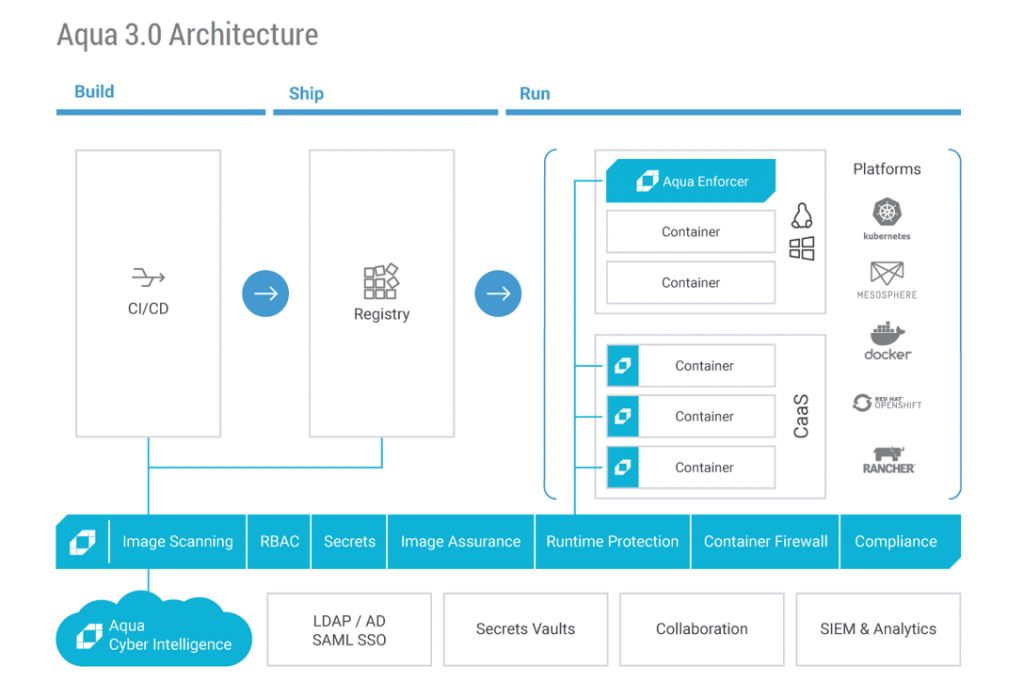
- Image Scanning: Aqua Security starts by scanning container images for vulnerabilities, malware, and configuration issues. It checks images for known vulnerabilities in libraries, packages, and dependencies.
- Policy Enforcement: Organizations can define security policies that specify which images are allowed to run, what security controls to apply, and compliance requirements.
- Runtime Protection: Aqua Security monitors running containers and microservices in real-time. It enforces security policies and alerts on suspicious activities or deviations from policies.
- Network Segmentation: Network policies are enforced to control communication between containers and microservices, helping to prevent lateral movement of attackers.
- CI/CD Pipeline Integration: Aqua Security integrates into the CI/CD pipeline, scanning container images during the build process and preventing the deployment of insecure images.
- Custom Policies: Organizations can create custom security policies and compliance checks to align with their specific requirements.
Aqua Security’s architecture is designed to provide comprehensive container security capabilities:
- Aqua Trivy Scanner: Trivy is Aqua Security’s open-source vulnerability scanner. It scans container images for vulnerabilities, misconfigurations, and package issues.
- Aqua Enforcer: The Aqua Enforcer is an agent deployed on each container host to enforce security policies and monitor running containers in real-time.
- Aqua Server: The Aqua Server is the central management component that orchestrates scans, enforces policies, and aggregates security data.
- Aqua Console: The Aqua Console is the user interface for managing and configuring security policies, viewing security findings, and responding to incidents.
- Integration Points: Aqua Security integrates with container orchestration platforms like Kubernetes, container registries, CI/CD pipelines, and other security tools to provide seamless security across the containerized environment.
Aqua Security’s architecture is designed to provide end-to-end security for containerized applications and microservices, from image scanning and build-time checks to runtime protection and incident response. It helps organizations ensure that their container workloads are secure, compliant, and free from vulnerabilities.
How to Install Aqua Security?
To install Aqua Security, you can use one of the following methods:
Using the Helm chart:
- Add the Aqua Helm repository:
helm repo add aqua-helm https://helm.aquasec.com- Update the Helm repository index:
helm repo update- Install the Aqua Server chart:
helm install aqua aqua-helm/server --namespace aqua- Install the Aqua Enforcer chart:
helm install enforcer aqua-helm/enforcer --namespace aqua- Install the Aqua KubeEnforcer chart:
helm install kube-enforcer aqua-helm/kube-enforcer --namespace aqua(Optional) Install the Aqua Scanner chart:
helm install scanner aqua-helm/scanner --namespace aqua(Optional) Install the Aqua Gateway chart:
helm install gateway aqua-helm/gateway --namespace aqua(Optional) Install the Aqua TenantManager chart:
helm install tenant-manager aqua-helm/tenant-manager --namespace aqua(Optional) Install the Aqua CyberCenter chart:
helm install cyber-center aqua-helm/cyber-center --namespace aqua(Optional) Install the Aqua CloudConnector chart:
helm install cloud-connector aqua-helm/cloud-connector --namespace aquaUsing the Aqua CLI:
- Install the Aqua CLI:
sudo wget https://download.aquasec.com/cli/latest/aquasec-cli-linux-64bit.tar.gz
sudo tar -xvf aquasec-cli-linux-64bit.tar.gz
sudo mv aquasec-cli /usr/local/bin- Create an Aqua account:
aquasec login- Connect to your Aqua server:
aquasec connect --url <aqua-server-url>- Install Aqua Security:
aquasec installOnce Aqua Security is installed, you can start using it to secure your cloud-native applications.
Basic Tutorials of Aqua Security: Getting Started

The following are the steps of basic tutorial of Aqua Security:
1. Install Aqua Security:
Follow the instructions in my previous response to install Aqua Security.
2. Connect to the Aqua Server:
Once Aqua Security is installed, you can connect to the Aqua Server using the Aqua CLI or the Aqua UI.
To connect to the Aqua Server using the Aqua CLI:
aquasec connect --url <aqua-server-url>
To connect to the Aqua Server using the Aqua UI:
- Open a web browser and go to the following URL:
https://<aqua-server-url>/ui
- Enter your Aqua account credentials and click Login.
3. Create a namespace:
Aqua Security uses namespaces to organize and manage your resources.
To create a namespace using the Aqua CLI:
aquasec namespace create <namespace-name>
To create a namespace using the Aqua UI:
- Click Namespaces in the left-hand menu.
- Click Create Namespace.
- Enter a name for your namespace and click Create.
4. Scan an image:
Aqua Security can scan your images for vulnerabilities and compliance violations.
To scan an image using the Aqua CLI:
aquasec scan image <image-name>
To scan an image using the Aqua UI:
- Click Images in the left-hand menu.
- Click the name of the image that you want to scan.
- Click Scan.
5. View the scan results:
Once the scan is complete, you can view the results in the Aqua UI.
To view the scan results in the Aqua UI:
- Click Images in the left-hand menu.
- Click the name of the image whose scan results you want to view.
- Click Vulnerabilities or Compliance to view the scan results.
6. Fix the vulnerabilities:
Once you have viewed the scan results, you can fix the vulnerabilities in your image.
To fix a vulnerability, you need to update the image to use a newer version of the vulnerable package or to patch the vulnerability.
Once you have fixed the vulnerabilities, you can scan the image again to verify that the vulnerabilities have been fixed.
Additional tips:
- Aqua Security can be integrated with your CI/CD pipeline to automate security checks.
- Aqua Security provides a variety of features to help you secure your cloud-native applications, such as:
- Vulnerability scanning: Aqua Security scans your images and containers for vulnerabilities.
- Compliance scanning: Aqua Security scans your images and containers for compliance with industry standards and regulations.
- Runtime security: Aqua Security monitors your running containers for suspicious activity.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
