What is Burp Suite?

Burp Suite is a leading commercial cybersecurity tool specifically designed for web application security testing and vulnerability assessment. It is developed by PortSwigger, a company specializing in web security solutions. Burp Suite offers a wide range of features and capabilities to help security professionals, penetration testers, and developers identify and address security vulnerabilities in web applications.
Top 10 use cases of Burp Suite:
Here are the top 10 use cases for Burp Suite:
- Vulnerability Scanning: Burp Suite can perform automated scans of web applications to identify common security issues such as cross-site scripting (XSS), SQL injection, and more.
- Proxy Interception: It acts as an intercepting proxy, allowing users to capture and inspect HTTP and HTTPS traffic between their browser and the target web application. This is essential for identifying vulnerabilities in real-time.
- Crawling and Spidering: Burp Suite can crawl web applications to map their structure and discover new pages, forms, and functionality for testing.
- Manual Testing: Security professionals can use Burp Suite’s suite of tools for manual testing, including the Repeater, Intruder, and Sequencer, to conduct in-depth security assessments.
- Fuzz Testing: The tool supports fuzzing, allowing testers to send malformed data to web forms and APIs to discover input validation and security issues.
- Session Management Testing: Burp Suite helps identify vulnerabilities related to session management, including session fixation, hijacking, and cookie security issues.
- Authentication Testing: Testers can assess the security of authentication mechanisms, including brute force attacks, weak password policies, and authentication bypass vulnerabilities.
- API Security Testing: Burp Suite is capable of testing REST and SOAP APIs for security vulnerabilities, ensuring that API endpoints are secure from attacks.
- Intruder and Sniper: These tools within Burp Suite are used for automated vulnerability scanning and testing. Intruder allows for customized attacks on web applications, while Sniper focuses on single request/response testing.
- Customization and Integration: Burp Suite offers extensive customization options, including the ability to create custom extensions and integrations with other tools and services. This flexibility allows users to tailor their testing workflows to their specific needs.
Burp Suite’s rich set of features, combined with its user-friendly interface and strong community support, make it a popular choice among security professionals for web application security testing and assessment. It provides both automated scanning capabilities and a suite of manual testing tools to comprehensively evaluate the security of web applications.
What are the feature of Burp Suite?
Burp Suite is a comprehensive web application security testing tool known for its wide range of features and capabilities. Below are the key features of Burp Suite and an overview of how it works and its architecture:
Features of Burp Suite:
- Proxy: Acts as an intercepting proxy, allowing users to capture and manipulate HTTP and HTTPS traffic between their browser and the target web application.
- Scanner: Provides automated vulnerability scanning for web applications, identifying common security issues such as SQL injection, cross-site scripting (XSS), and more.
- Spider: Crawls and maps the structure of web applications to discover new pages, forms, and functionality for testing.
- Repeater: Enables manual testing by allowing users to modify and re-send requests to the target application.
- Intruder: Automates attacks against web applications, making it easier to identify vulnerabilities through brute force, fuzzing, and payload manipulation.
- Sequencer: Analyzes the quality of randomness in tokens and session identifiers, helping to identify session management vulnerabilities.
- Decoder: Provides tools for decoding and encoding various data formats, such as URL encoding, base64, and more.
- Comparer: Compares two requests or responses to highlight differences, useful for detecting issues like parameter manipulation.
- Extender: Allows users to create custom extensions and integrations with other tools and services, enhancing Burp Suite’s functionality.
- Collaborator: Provides a unique domain for each testing engagement, allowing testers to detect out-of-band vulnerabilities and interactions with external systems.
- Scanner Checks: Offers a wide range of predefined security checks for identifying vulnerabilities in web applications.
How Burp Suite Works and Architecture?
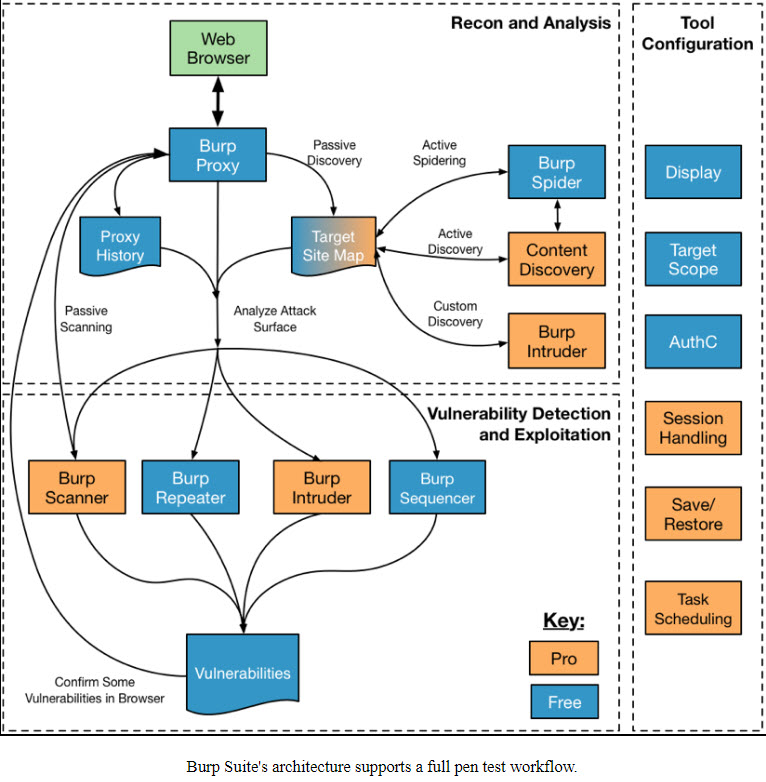
Burp Suite follows a proxy-based approach and consists of various components that work together to facilitate web application security testing:
- Proxy Server: The core component of Burp Suite is the proxy server, which intercepts HTTP and HTTPS traffic between the user’s browser and the target web application. This interception enables testers to view, modify, and analyze requests and responses.
- Crawler: The crawler component is responsible for exploring and mapping the structure of the target web application. It identifies links, forms, and parameters to build a comprehensive map for testing.
- Scanner Engine: Burp Suite’s scanner engine automates the detection of security vulnerabilities in the target application by sending payloads and probes to various input points.
- User Interface: Burp Suite provides a user-friendly graphical user interface (GUI) that allows testers to interact with the tool, review findings, and configure testing options.
- Extensions: Burp Suite supports custom extensions written in Java. These extensions can be used to add new functionality, customize behavior, or integrate with external tools and services.
- Report Generator: After testing, Burp Suite can generate detailed reports that include identified vulnerabilities, their severity, and recommended remediation steps. These reports can be exported in various formats.
- Session Handling: Burp Suite includes features for managing sessions and cookies, allowing testers to simulate different user interactions and scenarios during testing.
- Proxy Listener: Users configure their web browser to use Burp Suite as a proxy, directing traffic through the tool. This allows Burp Suite to intercept and manipulate requests and responses in real-time.
Overall, Burp Suite’s architecture and workflow are designed to provide a flexible and extensible platform for web application security testing. Its components work in concert to help security professionals identify and remediate vulnerabilities effectively.
How to Install Burp Suite?
To install Burp Suite, you can download the installer from the PortSwigger website. The installer is available for Windows, Linux, and macOS.
On Windows:
- Double-click on the Burp Suite installer to open the InstallShield Wizard.
- Apply the on-screen instructions to fulfill the installation.
On macOS:
- Open a Finder window.
- Navigate to the directory where you downloaded the Burp Suite installer.
- Double-click on the Burp Suite installer to open the installation wizard.
- Apply the on-screen instructions to fulfill the installation.
On Linux:
- Open a terminal window.
- Navigate to the directory where you downloaded the Burp Suite installer.
- Run the following command to install Burp Suite:
sudo sh burpsuite-<version>-<platform>.runCode language: HTML, XML (xml)Replace <version> with the version of Burp Suite you are installing, and replace <platform> with your operating system platform.
Once Burp Suite is installed, you can start using it to scan your web applications for vulnerabilities.
Additional tips:
- You can download a free Community Edition of Burp Suite, or you can purchase a Professional Edition with additional features.
- If you are new to Burp Suite, I recommend starting with the Community Edition. It has all the features you need to start scanning your web applications for vulnerabilities.
- Once you have installed Burp Suite, I recommend taking a look at the Burp Suite tutorials. They will teach you how to use Burp Suite to scan your web applications for vulnerabilities.
Basic Tutorials of Burp Suite: Getting Started

Following is the stepwise basic tutorial of Burp Suite:
- Start Burp Suite.
Once you have installed Burp Suite, you can start it by opening the Burp Suite desktop application.
- Create a new project.
When you start Burp Suite, you will be prompted to create a new project. A project is a collection of settings and data for a particular web application or group of web applications.
- Configure Burp Suite proxy.
Burp Suite can act as a proxy server, which means that it can intercept and modify all HTTP traffic between your browser and the web application you are testing. To configure Burp Suite as a proxy server, go to the Proxy tab and select the Manual proxy option. Then, enter the following proxy settings into your browser:
Proxy: 127.0.0.1
Port: 8080
Code language: CSS (css)- Browse to the web application you want to test.
Once you have configured Burp Suite as a proxy server, browse to the web application you want to test in your browser. Burp Suite will intercept and record all HTTP traffic between your browser and the web application.
- Start a scan.
Burp Suite comes with a variety of different scanners that you can use to scan your web application for vulnerabilities. To start a scan, go to the Scanner tab and select the scanner you want to use. Then, click the Start scan button.
- Review the scan results.
Once the scan has completed, you can review the results in the Scanner tab. The scan results will show you which vulnerabilities were found in your web application.
- Remediate vulnerabilities.
Once you have identified vulnerabilities, you need to take steps to remediate them. This may involve patching software, updating firmware, or implementing security controls.
Simple example of how to use Burp Suite to identify and remediate vulnerabilities:
- Create a new project for the web application you want to test.
- Configure Burp Suite as a proxy server.
- Browse to the web application you want to test in your browser.
- Start a scan using the Burp Suite Scanner.
- Review the scan results.
- Identify any vulnerabilities that need to be remediated.
- Prioritize the remediation of vulnerabilities based on their severity and risk.
- Take steps to remediate the vulnerabilities.
- Run the scanner again to verify that the vulnerabilities have been remediated.
You can repeat this process on a regular basis to ensure that your web applications are protected from known vulnerabilities.
Additional tips for using Burp Suite:
- Use Burp Suite to scan your web applications both before and after they are deployed to production.
- Use Burp Suite to scan your web applications on a regular basis to identify new vulnerabilities.
- Use Burp Suite’s reporting features to track your vulnerability management progress and identify trends.
- Use Burp Suite to integrate with other security tools, such as SIEM systems and ticketing systems.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

