What is CloudPassage?

CloudPassage is a cloud security platform designed to provide visibility and security automation for cloud infrastructure and applications. It offers a range of features and capabilities to help organizations secure their cloud environments effectively.
CloudPassage’s comprehensive security features make it a valuable solution for organizations looking to secure their cloud infrastructure, meet compliance requirements, and proactively address vulnerabilities and threats in cloud environments.
Top 10 use cases of CloudPassage:
Here are the top 10 use cases of CloudPassage:
- Vulnerability Management: CloudPassage scans cloud instances and containers for vulnerabilities and misconfigurations, helping organizations identify and remediate security risks before they can be exploited.
- Compliance Assurance: It assists in meeting regulatory compliance requirements by continuously monitoring cloud infrastructure and applications for adherence to industry standards and compliance frameworks.
- Host-Based Intrusion Detection: CloudPassage detects suspicious activity on cloud hosts by monitoring for signs of unauthorized access, malware, and other indicators of compromise.
- Security Configuration Management: Organizations can enforce security policies and best practices across their cloud infrastructure to ensure consistent security configurations.
- Asset Inventory and Discovery: It provides visibility into cloud assets, including virtual machines, containers, and services, helping organizations maintain an up-to-date inventory.
- Container Security: CloudPassage extends its security capabilities to containers, ensuring that containerized applications are secure and compliant with policies.
- Automated Remediation: It offers automated remediation for security vulnerabilities and misconfigurations, reducing the manual effort required to address security issues.
- File Integrity Monitoring: CloudPassage monitors critical files and directories for changes, helping organizations detect unauthorized modifications or tampering.
- Incident Response: It assists in incident response efforts by providing real-time alerts and insights into security incidents, helping organizations investigate and mitigate threats.
- Security Orchestration and Automation: CloudPassage can be integrated with security orchestration platforms to automate response actions and workflows in response to security events.
- Microsegmentation: Organizations can use CloudPassage to implement microsegmentation strategies in the cloud, restricting network access between workloads based on security policies.
- Container Orchestration Security: For cloud-native environments, CloudPassage helps secure container orchestration platforms like Kubernetes and Docker Swarm.
- Security Dashboards and Reporting: It offers customizable dashboards and reporting capabilities to visualize security data and generate compliance reports.
- Zero Trust Security: CloudPassage helps implement zero trust security principles by continuously verifying the security posture of cloud resources and applying access controls accordingly.
- Multi-Cloud Security: CloudPassage can be used to secure cloud environments across multiple cloud providers, ensuring consistent security policies.
What are the feature of CloudPassage?
CloudPassage is a cloud security platform designed to provide security visibility and automation for cloud infrastructure and applications. It offers a range of features and capabilities to help organizations secure their cloud environments effectively. Here are the key features of CloudPassage, along with an overview of how it works and its typical architecture:
Key Features of CloudPassage:
- Vulnerability Management: CloudPassage continuously scans cloud instances and containers for vulnerabilities and misconfigurations. It provides detailed reports and prioritizes remediation efforts based on risk.
- Compliance Assurance: Organizations can use CloudPassage to assess cloud resources against compliance standards and frameworks, ensuring adherence to regulatory requirements.
- Host-Based Intrusion Detection (HIDS): It offers host-based intrusion detection capabilities, monitoring for signs of unauthorized access, malware, and other security threats on cloud hosts.
- Security Configuration Management: CloudPassage enables organizations to enforce security policies and best practices consistently across their cloud infrastructure, ensuring that security configurations are maintained.
- Asset Inventory and Discovery: The platform provides visibility into cloud assets, allowing organizations to maintain an up-to-date inventory and detect unauthorized or rogue assets.
- Container Security: CloudPassage extends its security capabilities to containerized applications, helping organizations secure their container environments and ensuring compliance.
- Automated Remediation: CloudPassage offers automated remediation workflows, helping organizations address security vulnerabilities and misconfigurations without manual intervention.
- File Integrity Monitoring (FIM): It monitors critical files and directories for changes and alerts organizations to unauthorized modifications or tampering.
- Incident Response: CloudPassage provides real-time alerts and insights into security incidents, facilitating incident investigation and mitigation efforts.
- Security Orchestration and Automation: It can be integrated with security orchestration platforms to automate response actions and workflows in response to security events.
How CloudPassage works and Architecture?
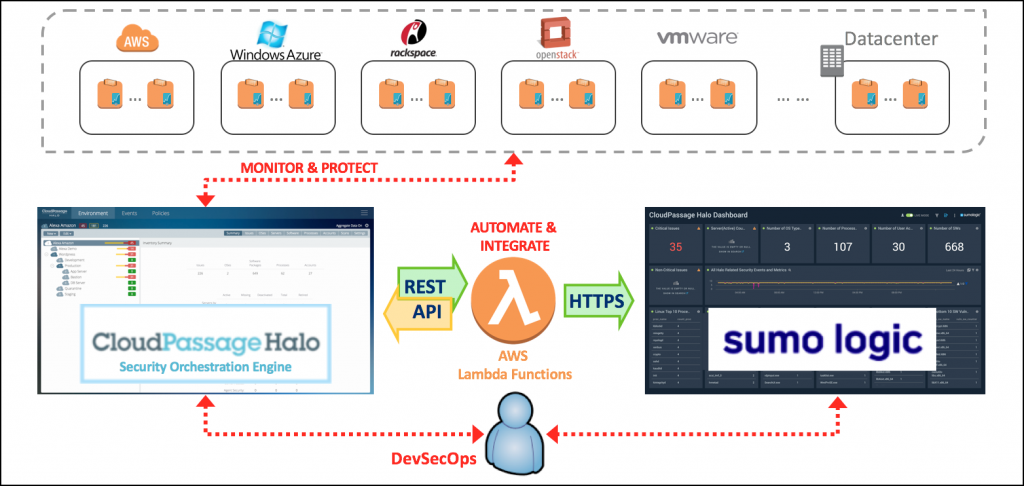
- Agent Deployment: CloudPassage typically deploys lightweight agents on cloud instances and containers. These agents collect security-related data and communicate it to the CloudPassage platform.
- Data Collection: The agents collect data on vulnerabilities, configurations, security events, and other relevant information from the cloud resources they are installed on.
- Analysis and Correlation: The collected data is analyzed in real-time by the CloudPassage platform. This analysis includes vulnerability assessments, compliance checks, intrusion detection, and security event correlation.
- Alerting and Reporting: CloudPassage generates alerts and notifications for security events, vulnerabilities, and compliance violations. It also provides customizable reports for security and compliance reporting.
- Automated Remediation: In cases of vulnerabilities or misconfigurations, CloudPassage can trigger automated remediation actions based on predefined policies and workflows.
CloudPassage’s architecture is designed to provide visibility and security automation for cloud environments. While specific configurations may vary based on the cloud provider and organization’s needs, here are the core components of CloudPassage:
- Halo Grid: This is the central component that manages and processes data from CloudPassage agents. It includes the Halo Portal, where administrators configure security policies and view security data.
- Halo Agents: These lightweight agents are deployed on cloud instances and containers to collect security-related data, including vulnerability scans, configuration information, and security events.
- Halo Daemon: The Halo Daemon runs on each protected cloud instance and communicates with the Halo Grid to relay security data and receive configuration updates.
- Halo API: CloudPassage provides an API that allows organizations to integrate CloudPassage data and functionality into their existing security tools and workflows.
- Halo Mobile: Administrators can access CloudPassage security data and alerts via a mobile app for monitoring cloud security while on the go.
CloudPassage’s architecture is designed to be flexible and scalable, enabling organizations to secure cloud resources across multiple cloud providers and adapt to their specific cloud security needs. The platform helps organizations maintain a strong security posture, reduce security risks, and automate security processes in cloud environments.
How to Install CloudPassage?
To install CloudPassage, you will need to:
- Create an account on the CloudPassage website.
- Install the CloudPassage Sensor on your cloud servers.
- Connect your cloud accounts to CloudPassage.
- Configure CloudPassage policies.
- Start monitoring and managing your cloud security posture.
More detailed tutorial on how to install CloudPassage:
- Create an account on the CloudPassage website. Go to the CloudPassage website and create an account.
- Install the CloudPassage Sensor on your cloud servers. The CloudPassage Sensor is a software package that collects data from your cloud servers and sends it to CloudPassage. You can download the CloudPassage Sensor from the CloudPassage website.
- Connect your cloud accounts to CloudPassage. You can connect your AWS, Azure, and Google Cloud Platform accounts to CloudPassage. Once you have connected your cloud accounts, CloudPassage will start collecting data from your servers.
- Configure CloudPassage policies. CloudPassage policies allow you to define the desired security posture for your cloud environment. You can create policies to detect and prevent common cloud security misconfigurations.
- Start monitoring and managing your cloud security posture. Once you have configured CloudPassage policies, you can start monitoring and managing your cloud security posture. CloudPassage will send you alerts when it detects a misconfiguration or other security issue.
Please note that CloudPassage is now part of Trend Micro.
Some additional tips for using CloudPassage:
- Use the CloudPassage Knowledge Base to learn more about CloudPassage and how to use it to protect your cloud environment.
- Join the CloudPassage community forum to ask questions and get help from other CloudPassage users.
- Take advantage of the CloudPassage free trial to try out CloudPassage before you commit to a paid subscription.
CloudPassage is a powerful cloud security posture management (CSPM) tool that can help you improve the security of your cloud environment. By following these basic tutorials, you can get started with CloudPassage quickly and easily.
Basic Tutorials of CloudPassage: Getting Started
The following are the steps of basic tutorial of CloudPassage:
- Create an account on the CloudPassage website.
Go to the Trend Micro website and create an account for CloudPassage.
- Install the CloudPassage Sensor on your cloud servers.
The CloudPassage Sensor is a software package that collects data from your cloud servers and sends it to CloudPassage. You can download the CloudPassage Sensor from the Trend Micro website.
- Connect your cloud accounts to CloudPassage.
You can connect your AWS, Azure, and Google Cloud Platform accounts to CloudPassage. Once you have connected your cloud accounts, CloudPassage will start collecting data from your servers.
- Configure CloudPassage policies.
CloudPassage policies allow you to define the desired security posture for your cloud environment. You can create policies to detect and prevent common cloud security misconfigurations.
- Start monitoring and managing your cloud security posture.
Once you have configured CloudPassage policies, you can start monitoring and managing your cloud security posture. CloudPassage will send you alerts when it detects a misconfiguration or other security issue.
Some additional tips for using CloudPassage:
- Use the CloudPassage Knowledge Base to learn more about CloudPassage and how to use it to protect your cloud environment.
- Join the CloudPassage community forum to ask questions and get help from other CloudPassage users.
- Take advantage of the CloudPassage free trial to try out CloudPassage before you commit to a paid subscription.
CloudPassage is a powerful cloud security posture management (CSPM) tool that can help you improve the security of your cloud environment. By following these basic tutorials, you can get started with CloudPassage quickly and easily.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
