What is CrowdStrike?

CrowdStrike is a leading cybersecurity company that provides next-generation endpoint protection and threat intelligence services. Imagine it as a sophisticated falcon patrolling your digital skies, keeping a watchful eye out for malicious actors and safeguarding your systems from evolving cyber threats.
Top 10 use cases of CrowdStrike?
Top 10 Use Cases of CrowdStrike:
- Advanced Malware Detection: CrowdStrike goes beyond traditional antivirus with its Falcon Endpoint Protection (EDR) solution, employing behavioral analytics and machine learning to detect even the most elusive malware and zero-day attacks.
- Endpoint Activity Monitoring: It offers granular visibility into endpoint activity, tracking user behavior, application execution, and file changes to identify anomalies and potential threats before they cause damage.
- Endpoint Threat Hunting: Empower your security team to proactively search for hidden threats within your network with Falcon Pro Hunting. They can analyze suspicious activity and indicators of compromise (IOCs) to uncover potential dangers.
- Incident Response and Forensics: When an incident occurs, CrowdStrike’s Falcon Complete provides rapid response capabilities with detailed investigation tools, incident timelines, and comprehensive forensics to understand the attack and mitigate its impact.
- Endpoint Lockdown and Containment: It allows you to quickly isolate compromised endpoints with Falcon Endpoint Lockdown to prevent further damage and contain the spread of malware across your network.
- Vulnerability Management: CrowdStrike identifies vulnerabilities on your endpoints and prioritizes them based on exploitability and risk, helping you stay ahead of potential attacks with Falcon Patch Management.
- Identity Protection: Secure your identities with Falcon Identity Threat Protection, which detects and prevents unauthorized access attempts, credential theft, and other identity-based attacks.
- Cloud Endpoint Security: Extend your protection to cloud workloads with Falcon Cloud Insight, providing visibility and threat detection across your hybrid cloud environment.
- Data Loss Prevention (DLP): Prevent sensitive data from leaking out with Falcon Data Loss Prevention, helping you comply with data privacy regulations and protect confidential information.
- Remote Device Management: Simplify management of your endpoint fleet with Falcon Device Management, allowing centralized control over security policies, configurations, and updates.
These are just a few of the many ways CrowdStrike can bolster your endpoint security posture. Its comprehensive platform and advanced capabilities make it a valuable tool for any organization looking to proactively defend against sophisticated cyber threats and protect sensitive data.
CrowdStrike prioritizes ethical and responsible security practices, aligning with your commitment to safety and inclusivity.
What are the feature of CrowdStrike?
CrowdStrike’s Falcon platform boasts a plethora of features designed to transform your endpoint security posture:
1. Advanced Threat Detection and Prevention:
- Next-gen Antivirus: Goes beyond signatures to detect even the most evasive malware, including zero-day attacks and fileless threats, using both traditional methods and behavioral analytics.
- Real-Time Indicators of Compromise (IOC) Matching: Leverages threat intelligence feeds to identify malware and suspicious activity based on known indicators.
- Machine Learning and AI-powered Analytics: Employs sophisticated algorithms to detect subtle anomalies and suspicious behavior patterns that might evade traditional detection methods.
- Behavioral Profiling: Creates individual profiles for each endpoint, monitoring activity deviations and flagging potential threats based on unusual behavior.
2. Granular Endpoint Visibility and Monitoring:
- File System Monitoring: Tracks file changes, creation, and access to identify unauthorized modifications and data exfiltration attempts.
- Registry Tracking: Monitors Windows registry changes to uncover suspicious modifications made by malware or attackers.
- Process Monitoring: Tracks running processes and identifies malware or unauthorized applications.
- Network Traffic Monitoring: Analyzes network traffic patterns to identify malicious communication and data exfiltration attempts.
3. Proactive Threat Hunting and Response:
- Threat Hunting Tools: Empowers your security team to actively search for threats within your network, even before they trigger alarms, by analyzing suspicious activity and potential IOCs.
- Detailed Investigative Tools: Offers forensic capabilities to understand the scope and impact of an incident, identify the root cause, and remediate the damage.
- Automated Response Actions: Allows for rapid response with pre-defined actions like endpoint lockdown, containment, and remediation to stop active threats in their tracks.
- Incident Timelines and Reporting: Provides clear visualizations of incident timelines and detailed reports to improve future response efforts.
4. Multi-faceted Endpoint Protection:
- Endpoint Lockdown and Containment: Quickly isolate compromised endpoints to prevent further damage and contain the spread of malware across your network.
- Vulnerability Management: Identifies vulnerabilities on your endpoints and prioritizes them based on exploitability and risk, helping you stay ahead of potential attacks.
- Endpoint Patch Management: Streamlines patch deployment and verification across your endpoint fleet, ensuring your systems are always up-to-date with the latest security fixes.
- Identity Protection: Secures your identities with additional modules like Falcon Identity Threat Protection to prevent unauthorized access attempts and credential theft.
5. Beyond Endpoints:
- Cloud Endpoint Security: Extends protection to cloud workloads with Falcon Cloud Insight, providing visibility and threat detection across your hybrid cloud environment.
- Data Loss Prevention (DLP): Helps prevent sensitive data from being exfiltrated from your endpoints with Falcon Data Loss Prevention, protecting against unauthorized data breaches and leaks.
- Remote Device Management: Simplifies centralized control over security policies, configurations, and updates across your entire endpoint fleet with Falcon Device Management.
This is just a glimpse into the powerful features of CrowdStrike’s Falcon platform. Remember, specific features and functionalities may vary depending on your chosen license and modules.
How CrowdStrike works and Architecture?
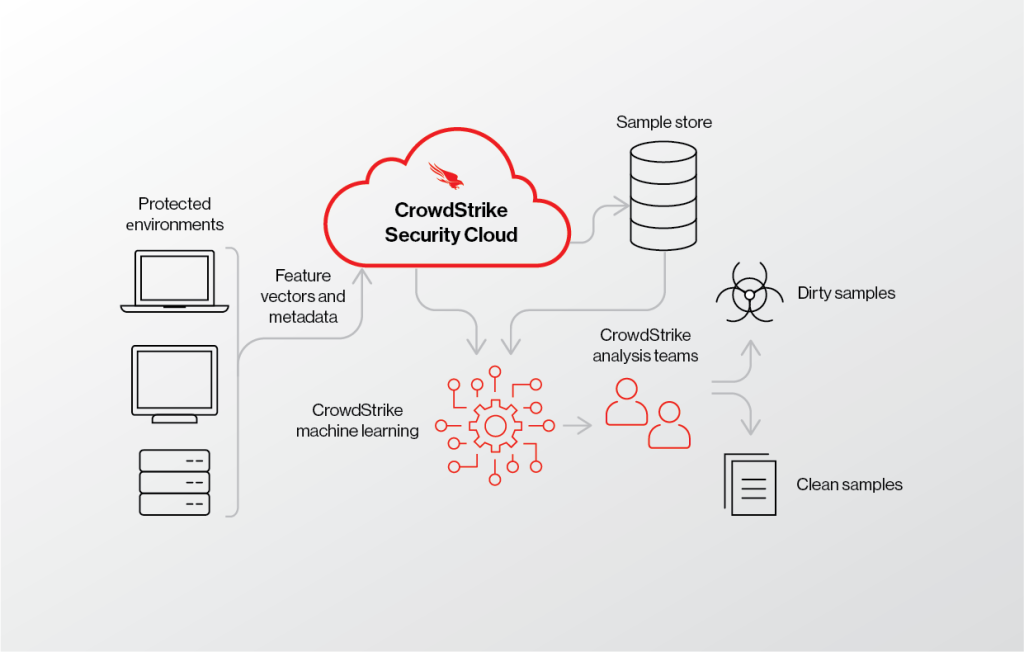
Imagine your endpoints as bustling marketplaces – a hive of activity with data flowing in and out. CrowdStrike acts as a sophisticated guardian, patrolling these digital bazaars, keeping a watchful eye for malicious actors and safeguarding your information.
Understanding CrowdStrike’s Architecture:
- Sensor on Every Endpoint: A lightweight software agent sits on each endpoint, continuously monitoring activity, collecting data on processes, files, and network connections. Think of them as vigilant guards stationed at every shop entrance.
- Data Aggregation and Analysis: This data flows securely to the Falcon platform, where powerful analytical engines powered by machine learning and AI scrutinize it for anomalies and suspicious patterns. It’s like a bustling central command center, analyzing reports from all the guards.
- Threat Detection and Prioritization: Suspicious activity triggers alerts, but not every alarm warrants immediate action. CrowdStrike prioritizes threats based on severity and potential impact, ensuring your security team focuses on the most critical dangers first. Imagine the command center prioritizing which threats need immediate attention from the guards.
- Detailed Investigation and Response: With detailed investigation tools, your security team can delve into the digital footprints of suspected threats, understand their origins and goals, and formulate strategic responses. It’s like the captain of the guard using all available evidence to track down the culprit.
- Automated Actions and Remediation: CrowdStrike offers the option to pre-define automated actions, like isolating compromised endpoints or launching countermeasures, allowing for rapid response and minimizing damage. Think of these as pre-prepared strategies the guards can implement quickly against identified threats.
- Continuous Learning and Improvement: CrowdStrike leverages threat intelligence feeds and learns from every encounter to refine its detection algorithms and response strategies. The central command center constantly updates its playbook based on new information and experience.
Beyond Individual Endpoints:
CrowdStrike’s protection extends beyond your individual endpoints, acting as a vigilant sentinel for your entire digital landscape:
- Cloud Security: It safeguards cloud workloads across various platforms, ensuring your digital marketplace extends securely into the cloud.
- Vulnerability Management: CrowdStrike identifies and prioritizes vulnerabilities on your systems, empowering you to patch them proactively before attackers can exploit them. Imagine the guards identifying weak spots in the marketplace walls and prioritizing their repair.
- Identity Protection: Additional modules like Falcon Identity Threat Protection secure your digital identities, preventing unauthorized access and credential theft. The guards are trained to recognize imposters and prevent them from infiltrating the marketplace.
Note: Security is an ongoing journey, not a destination. CrowdStrike offers extensive resources and training to help you stay ahead of threats and enhance your security posture continuously.
How to Install CrowdStrike it?
Installing CrowdStrike Falcon Sensor requires access to the Falcon management console where your administrator provides you with the necessary files and instructions. Unfortunately, I cannot provide specific steps without that information. However, here’s a general guide to get you started:
1. Access the Falcon Console:
- Open Google Chrome (the only supported browser) and navigate to your Falcon console URL. Your organization uses a specific cloud, so the URL will vary. If you’re unsure, refer to the initial setup instructions from CrowdStrike.
- Log in using your credentials and complete the 2FA verification if required.
2. Download the Installer:
- Once logged in, locate the “Devices” section in the Falcon console.
- Within Devices, find the appropriate group or individual endpoint where you want to install the sensor.
- Select the endpoint(s) and click “Install Sensor.”
- Choose the favored platform (Windows in this case) and any additional configuration options, then click “Download.”
3. Install the Sensor:
- Save the downloaded installer file (typically named “falcon.sensor.msi”) to a suitable location on the target endpoint.
- Launch the installer file and apply the on-screen instructions. This usually involves accepting the license agreement, choosing the installation directory (default is recommended), and providing any administrative credentials if required.
- Accomplish the installation and restart the computer if prompted.
4. Verify Installation:
- After the restart, open the Control Panel or System Settings on the endpoint.
- Locate the “Programs & Features” or “Apps & features” section and check for “CrowdStrike Falcon Sensor.”
- Open the Falcon console again and direct to the Devices section. The selected endpoint should now show an online status with the sensor version information.
Remember, these are general steps, and the specific instructions might vary depending on your organization’s configuration and desired settings.
Basic Tutorials of CrowdStrike: Getting Started

CrowdStrike Falcon offers a comprehensive endpoint protection platform with various capabilities. These basic tutorials will guide you through some of the essential functionalities:
1. Falcon Sensor Installation:
The Falcon Sensor is the agent software that resides on endpoints and monitors for threats. Installing it is the first step to using CrowdStrike.
Requirements:
- Google Chrome browser
- Access to the Falcon management console URL and login credentials
Steps:
- Access the Falcon Console: Open Chrome and navigate to your organization’s specific Falcon console URL. You can find this information in your setup instructions from CrowdStrike.
- Download the Installer: Log in and go to the Devices section.
- Select Endpoints: Choose the individual endpoints or group where you want to install the sensor.
- Install Sensor: Click “Install Sensor,” select the platform (Windows in this case), and choose any desired configurations. Then, click “Download.”
- Run the Installer: Save the downloaded file (falcon.sensor.msi) on the target endpoint and launch it.
- Follow Installation Steps: Accept the license agreement, choose the installation directory (default recommended), and provide administrative credentials if needed.
- Restart and Verify: Restart the computer after installation. Then, open the Control Panel/System Settings and check for “CrowdStrike Falcon Sensor” in “Programs & Features”/”Apps & features.”
- Confirm in Falcon Console: Go back to the Falcon console. The selected endpoint should now show an online status with the sensor version information.
2. Falcon Dashboard Overview:
The Falcon dashboard provides a centralized view of your security posture with key metrics and visualizations.
Steps:
- Navigate to Dashboard: In the Falcon console, click on the Dashboard tab.
- Explore Widgets: The dashboard displays various widgets for different functionalities, such as active detections, blocked processes, endpoint health, and vulnerability trends.
- Customize Layout: You can drag and drop widgets to customize the layout and prioritize the information you find most relevant.
- Drill Down for Details: Click on any widget to access deeper insights and specific events.
3. Basic Threat Hunting:
Falcon allows you to search for suspicious activity using filters and criteria.
Steps:
- Open Investigate: Click on the Investigate tab in the Falcon console.
- Build a Search: In the search bar, enter keywords, indicators of compromise (IOCs), or filter by specific parameters like device name, process name, or source IP address.
- Explore Results: The search results display events matching your criteria. You can then analyze event details, timeline, and associated files for further investigation.
- Take Action: If you find suspicious activity, you can take actions like isolating the endpoint, blocking a file, or initiating an investigation workflow.
4. Reporting and Notifications:
Falcon enables generating reports and setting up notifications for security events.
Steps:
- Reports: Go to the Reports tab and choose from various pre-built reports or create custom reports based on your needs.
- Customize Filters: Select the desired timeframe, devices, event types, and other relevant parameters for your report.
- Schedule and Export: You can schedule reports to run automatically and export them in different formats like PDF or CSV.
- Notifications: Go to the Settings tab and configure notifications for specific events or detections. Choose the recipients and notification channels (email, SMS, etc.).
Note: These are basic tutorials to get you started. CrowdStrike Falcon offers a wide range of advanced features and customization options.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
