What is Dome9?

Dome9, now known as Check Point CloudGuard Dome9, is a cloud security platform designed to help organizations secure their cloud environments and infrastructure across multiple cloud providers. It offers a range of features and capabilities to enhance cloud security.
Dome9’s comprehensive cloud security capabilities make it a valuable solution for organizations seeking to strengthen their cloud security posture, maintain compliance, and protect their cloud assets from evolving threats and vulnerabilities.
Top 10 use cases of Dome9:
Here are the top 10 use cases of Dome9:
- Cloud Security Posture Management (CSPM): Dome9 provides CSPM capabilities, allowing organizations to assess and remediate security risks and misconfigurations in their cloud environments. This helps ensure that cloud resources are compliant with security best practices and industry standards.
- Network Security Group (NSG) Management: Dome9 helps manage network security groups (firewall rules) in cloud environments, ensuring that only authorized traffic is allowed and helping organizations maintain a strong security posture.
- Identity and Access Management (IAM) Security: It offers IAM security features to control and monitor user access to cloud resources, helping prevent unauthorized access and account compromises.
- Security Policy Enforcement: Dome9 enforces security policies and compliance standards across cloud accounts and resources, reducing the risk of misconfigurations and security breaches.
- Vulnerability Management: Organizations can use Dome9 to identify and remediate vulnerabilities in their cloud infrastructure, helping maintain a secure and patched environment.
- Asset Discovery and Inventory: Dome9 provides visibility into cloud assets, helping organizations maintain an up-to-date inventory of resources and detect any unauthorized or unknown assets.
- Security Events and Alerts: It monitors cloud environments for security events and generates alerts for suspicious activities, enabling rapid incident detection and response.
- Multi-Cloud Security: Dome9 supports multiple cloud providers, allowing organizations to manage security policies and configurations consistently across different cloud platforms.
- Security Automation and Remediation: Dome9 offers automation capabilities to streamline security tasks and remediation processes, reducing manual effort and response times.
- Compliance Reporting: It helps organizations demonstrate compliance with regulatory requirements by providing predefined compliance reports and audit trails of security activities.
- Cloud-Native Security: Dome9 is designed to address the unique security challenges posed by cloud-native technologies, including serverless computing and container orchestration platforms.
- Security Monitoring and Threat Detection: Dome9 continuously monitors cloud environments for suspicious or anomalous activities and provides threat detection capabilities to identify potential security threats.
- Cloud-Native Firewall Management: It allows organizations to manage cloud-native firewall rules and security groups efficiently, ensuring proper network segmentation and security controls.
- Cloud-Native Encryption: Dome9 helps organizations manage encryption keys and certificates for data protection in the cloud.
- Integration with DevOps Pipelines: Dome9 can be integrated into DevOps pipelines to ensure that security is considered throughout the development and deployment processes.
What are the feature of Dome9?
Dome9, now known as Check Point CloudGuard Dome9, is a comprehensive cloud security platform designed to protect cloud environments and infrastructure across multiple cloud providers. Below are some key features of Dome9, along with an overview of how it works and its typical architecture:
Key Features of Dome9:
- Cloud Security Posture Management (CSPM): Dome9 helps organizations assess and remediate security risks and misconfigurations in their cloud environments. It provides recommendations for improving security posture based on best practices and compliance standards.
- Network Security Group (NSG) Management: It offers tools to manage network security groups (firewalls) in cloud environments, ensuring that only authorized traffic is allowed and that the network is properly segmented.
- Identity and Access Management (IAM) Security: Dome9 assists in securing IAM configurations, ensuring that user permissions are properly configured and monitoring for unauthorized access and changes.
- Security Policy Enforcement: Organizations can enforce security policies and compliance standards consistently across their cloud accounts and resources, reducing the risk of misconfigurations and security breaches.
- Vulnerability Management: Dome9 identifies vulnerabilities in cloud infrastructure and provides tools to remediate them. It helps maintain a secure and patched environment.
- Asset Discovery and Inventory: Dome9 provides visibility into cloud assets, helping organizations maintain an up-to-date inventory of resources and detect unauthorized or unknown assets.
- Security Events and Alerts: It monitors cloud environments for security events and generates alerts for suspicious activities, enabling rapid incident detection and response.
- Multi-Cloud Security: Dome9 supports multiple cloud providers, allowing organizations to manage security policies and configurations consistently across different cloud platforms.
- Security Automation and Remediation: Dome9 offers automation capabilities to streamline security tasks and remediation processes, reducing manual effort and response times.
- Compliance Reporting: It helps organizations demonstrate compliance with regulatory requirements by providing predefined compliance reports and audit trails of security activities.
How Dome9 works and Architecture?
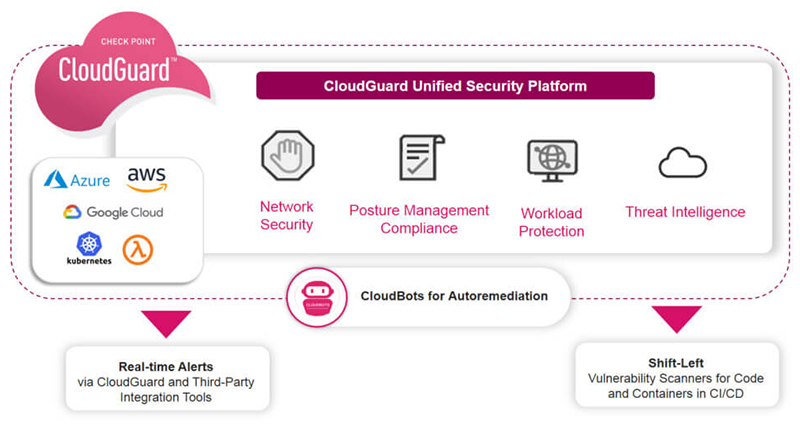
- Agentless Architecture: Dome9 operates without requiring agents to be deployed on cloud instances. Instead, it leverages cloud provider APIs to interact with and secure cloud resources.
- Inventory and Discovery: Dome9 conducts a comprehensive inventory of cloud resources and continuously discovers new assets. It provides visibility into resource configurations and relationships.
- Vulnerability Assessment: Dome9 scans cloud resources for vulnerabilities and misconfigurations. It prioritizes and provides recommendations for remediation.
- Security Posture Management: Organizations can define and enforce security policies across their cloud environments. Dome9 checks for policy compliance and alerts when violations occur.
- Access Control and IAM Monitoring: Dome9 monitors IAM configurations and user access. It identifies excessive privileges, risky configurations, and unauthorized access attempts.
- Network Security Management: Dome9 manages network security groups (NSGs) and firewall rules, ensuring proper segmentation and control over network traffic.
- Threat Detection and Response: Dome9 analyzes security events and anomalies in real-time. It generates alerts and notifications for potential threats, enabling rapid response.
Dome9’s architecture is designed to be cloud-native and agentless, allowing it to seamlessly integrate with cloud environments. While specific configurations may vary based on the cloud provider and organization’s needs, here are the core components of Dome9:
- Dome9 Central Console: This is the web-based interface used by administrators and security teams to configure security policies, view alerts, and manage cloud security.
- Dome9 Compliance Engine: It continuously assesses cloud resources against predefined security policies and compliance standards.
- Dome9 Compliance Library: This library contains predefined policies and compliance standards based on industry best practices and regulatory requirements.
- Dome9 Inventory and Discovery: This component continuously discovers and inventories cloud assets, providing real-time visibility into resource configurations.
- Dome9 Agentless Compliance Scanning: Dome9 scans cloud resources for vulnerabilities, misconfigurations, and adherence to security policies.
- Dome9 Threat Intelligence: It leverages threat intelligence feeds and behavioral analysis to detect security threats and anomalies in real-time.
- Dome9 Secure Access: This feature helps manage and secure access to cloud resources and IAM configurations.
Dome9’s architecture is designed to provide organizations with a holistic view of their cloud security posture and streamline the management of security policies and configurations across cloud providers. It helps organizations maintain strong security, compliance, and threat detection capabilities in their cloud environments.
How to Install Dome9?
To install Dome9, you will need to:
- Create an account on the Dome9 website.
- Install the Dome9 Agent on your cloud servers.
- Connect your cloud accounts to Dome9.
- Configure Dome9 policies.
- Start monitoring and managing your cloud security posture.
More detailed tutorial on how to install Dome9:
- Create an account on the Dome9 website. Go to the Dome9 website and create an account.
- Install the Dome9 Agent on your cloud servers. The Dome9 Agent is a software package that collects data from your cloud servers and sends it to Dome9. You can download the Dome9 Agent from the Dome9 website.
- Connect your cloud accounts to Dome9. You can connect your AWS, Azure, and Google Cloud Platform accounts to Dome9. Once you have connected your cloud accounts, Dome9 will start collecting data from your servers.
- Configure Dome9 policies. Dome9 policies allow you to define the desired security posture for your cloud environment. You can create policies to detect and prevent common cloud security misconfigurations.
- Start monitoring and managing your cloud security posture. Once you have configured Dome9 policies, you can start monitoring and managing your cloud security posture. Dome9 will send you alerts when it detects a misconfiguration or other security issue.
Basic Tutorials of Dome9: Getting Started
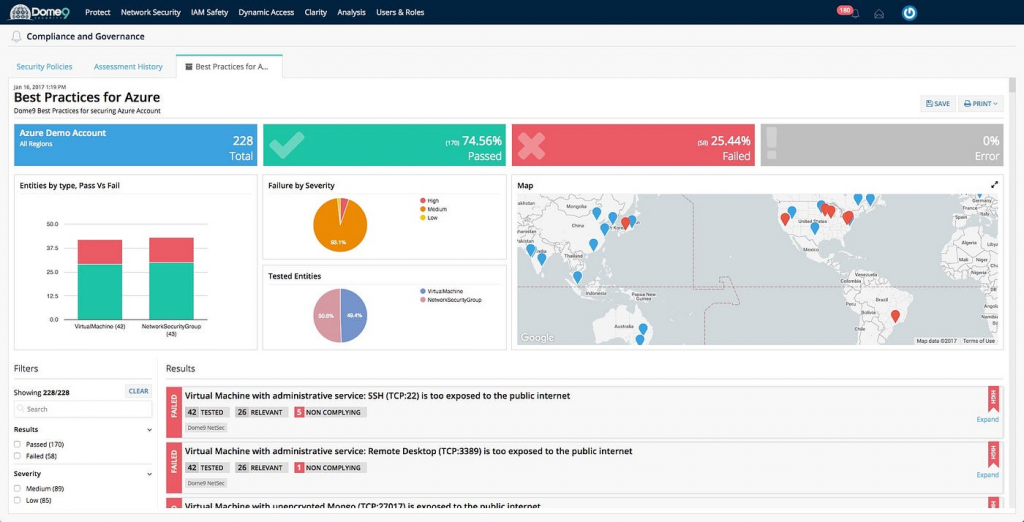
The following are the steps of basic tutorial of Dome9:
1. Create an account on the Dome9 website.
Go to the Check Point website and create an account for CloudGuard Cloud Security.
2. Install the CloudGuard Agent on your cloud servers.
The CloudGuard Agent is a software package that collects data from your cloud servers and sends it to Dome9. You can download the CloudGuard Agent from the Check Point website.
3. Connect your cloud accounts to Dome9.
You can connect your AWS, Azure, and Google Cloud Platform accounts to Dome9. Once you have connected your cloud accounts, Dome9 will start collecting data from your servers.
4. Configure Dome9 policies.
Dome9 policies allow you to define the desired security posture for your cloud environment. You can create policies to detect and prevent common cloud security misconfigurations.
5. Start monitoring and managing your cloud security posture.
Once you have configured Dome9 policies, you can start monitoring and managing your cloud security posture. Dome9 will send you alerts when it detects a misconfiguration or other security issue.
Some additional tips for using Dome9:
- Use the Dome9 Knowledge Base to learn more about Dome9 and how to use it to protect your cloud environment.
- Join the Dome9 community forum to ask questions and get help from other Dome9 users.
- Take advantage of the Dome9 free trial to try out Dome9 before you commit to a paid subscription.
Dome9 is a powerful cloud security posture management (CSPM) tool that can help you improve the security of your cloud environment. By following these basic tutorials, you can get started with Dome9 quickly and easily.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
