What is F5 Networks?

F5 Networks is a leading provider of multi-cloud application services, security, and automation solutions. They empower organizations to deliver their applications faster, more securely, and with greater control, across any cloud environment. Whether you’re in the enterprise, service provider, or government sector, F5 has solutions to help you thrive in the digital age.
Top 10 use cases of F5 Networks?
Top 10 Use Cases of F5 Networks:
- Application Delivery and Load Balancing: F5’s core competency lies in load balancing traffic across multiple servers, ensuring optimal performance and availability for your applications. They offer a wide range of load balancers, from hardware appliances to software-defined solutions, to meet your specific needs.
- Application Security: F5 provides comprehensive security solutions to protect your applications from a variety of threats, including DDoS attacks, web application attacks, and bot fraud. Their Web Application Firewall (WAF) is a leader in the industry, and their security solutions integrate seamlessly with their application delivery offerings.
- API Management: With the increasing use of APIs, F5 helps you secure, manage, and govern your APIs effectively. Their API Gateway provides a central point for managing API traffic, enforcing security policies, and collecting valuable analytics.
- Multi-Cloud Management: As organizations embrace hybrid and multi-cloud environments, F5 provides solutions to manage and orchestrate your applications across multiple clouds. Their Cloud Services platform offers a unified view of your applications, regardless of where they are deployed.
- Network Functions Virtualization (NFV): F5 helps service providers virtualize their network functions, such as firewalls and load balancers, to improve agility and efficiency. Their service delivery platform provides a foundation for building and deploying virtual network functions.
- Bot Management: With the rise of malicious bots, F5 helps you identify and block bad bots from impacting your applications and infrastructure. Their bot management solutions use advanced machine learning to distinguish between good and bad bots.
- DNS Security: F5 provides solutions to protect your Domain Name System (DNS) infrastructure from attacks. Their DNS security solutions can help mitigate DDoS attacks, prevent DNS hijacking, and protect your valuable domain names.
- Application Acceleration: F5 offers solutions to accelerate the performance of your applications, regardless of where they are deployed. Their acceleration solutions can improve application response times, reduce latency, and improve user experience.
- Threat Intelligence: F5 provides access to real-time threat intelligence to help you stay ahead of cyberattacks. Their threat intelligence service provides insights into the latest threats and vulnerabilities, so you can take proactive steps to protect your applications.
- Analytics and Automation: F5 offers a variety of analytics and automation solutions to help you gain insights into your network and application performance. Their analytics solutions can help you identify and troubleshoot problems, while their automation solutions can help you automate repetitive tasks.
These are just a few of the many use cases for F5 Networks’ solutions. They offer a wide range of products and services to help organizations of all sizes deliver their applications faster, more securely, and with greater control.
What are the feature of F5 Networks?
F5 Networks boasts a diverse feature set across its product portfolio, addressing various application delivery, security, and multi-cloud management needs. Here’s a breakdown of some key areas and features:
Application Delivery and Load Balancing:
- High-performance load balancing: Efficiently distribute traffic across multiple servers for optimal application performance and availability.
- Layer 4-7 load balancing: Support various protocols and application-aware routing for intelligent traffic management.
- Global Server Load Balancing (GSLB): Deliver a consistent user experience globally with geographically distributed applications.
- Web Application Acceleration: Optimize application performance by caching static content and compressing dynamic content.
Application Security:
- Web Application Firewall (WAF): Protect applications from diverse web attacks like SQL injection, cross-site scripting, and bot attacks.
- Bot Management: Identify and block malicious bots targeting your applications and infrastructure.
- Advanced Threat Protection: Defend against sophisticated attacks like zero-day vulnerabilities and application-layer denial-of-service (DoS).
- API Security: Secure your APIs with authentication, authorization, and rate limiting capabilities.
Multi-Cloud Management:
- Cloud Services Platform: Manage and orchestrate applications across multiple clouds with a unified view and control plane.
- Hybrid Cloud Networking: Connect applications across on-premises and cloud environments seamlessly.
- Multi-Tenant Cloud Services: Deliver cloud services securely and efficiently to multiple tenants.
Additional Features:
- DNS Security: Protect your Domain Name System (DNS) infrastructure from attacks.
- Network Functions Virtualization (NFV): Build and deploy virtual network functions for greater agility and efficiency.
- Analytics and Automation: Gain insights into network and application performance and automate repetitive tasks.
- Threat Intelligence: Access real-time threat intelligence to stay ahead of cyberattacks.
- Openness and Integration: Integrate with diverse tools and platforms for enhanced flexibility.
How F5 Networks works and Architecture?
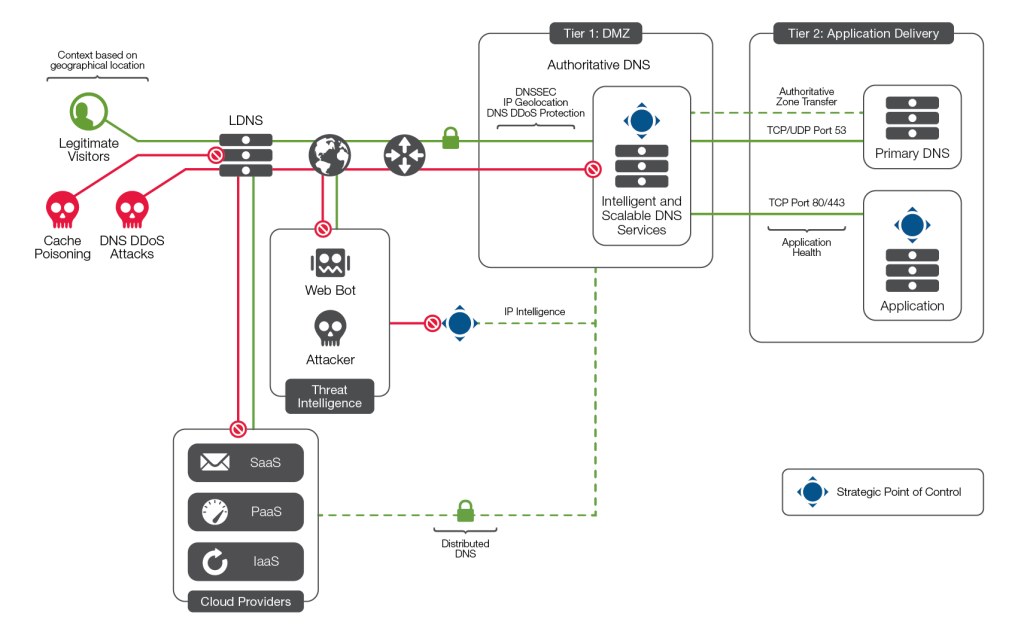
F5 Networks delivers secure and agile applications through a well-integrated architecture comprising hardware, software, and cloud-based services. Here’s a breakdown of the key components and how they work together:
Hardware:
- High-performance appliances: These physical devices deliver core application delivery and security functionalities.
- Virtual appliances: Software versions of the appliances, offering deployment flexibility in virtualized environments.
Software:
- BIG-IP platform: The core software suite providing various modules for:
- Load balancing: Distributes traffic efficiently across servers for optimal performance.
- Application security: Protects applications from web attacks, bots, and advanced threats.
- API management: Secures, manages, and governs APIs effectively.
- DNS security: Safeguards Domain Name System infrastructure from attacks.
- Application acceleration: Optimizes application performance through caching and compression.
- TMS Traffic Management System (optional): Offers advanced traffic management capabilities for complex network environments.
Cloud Services:
- Cloud Edition BIG-IP: Cloud-based version of the BIG-IP platform for managed service delivery.
- Cloud Services platform: Orchestrates and manages applications across multiple clouds.
- Threat intelligence services: Delivers real-time insights into emerging threats and vulnerabilities.
Architecture Principles:
- Modular design: Enables flexible customization and scalability by combining hardware, software, and cloud services as needed.
- API-driven automation: Facilitates integration with automation tools and workflows for enhanced efficiency.
- Multi-cloud support: Works seamlessly across on-premises, cloud, and hybrid environments.
- Security-first approach: Integrates security features at every layer for comprehensive protection.
How it Works:
- Traffic enters the network and reaches F5 devices.
- BIG-IP platform uses load balancing algorithms to distribute traffic across servers.
- Application security modules inspect traffic for malicious activity and block threats.
- Additional modules provide specific functionalities like API management or DNS security.
- Cloud Services platform orchestrates and manages applications across diverse cloud environments.
- Monitoring and analytics tools provide insights into network and application performance and security.
Benefits of F5 Architecture:
- Agility and scalability: Adapts to changing needs and scales effectively.
- Security: Comprehensive protection for applications and infrastructure.
- Automation: Streamlines operations and reduces manual tasks.
- Flexibility: Supports diverse deployment options and integrations.
- Visibility and control: Provides centralized management and insights into applications and network health.
Remember, specific configurations and details might vary depending on your chosen products and environment.
How to Install F5 Networks it?
Installing F5 Networks solutions involves several steps and considerations, depending on your chosen product, deployment method, and network environment. Here’s a general overview to guide you:
1. Identify your needs and chosen product:
- What are you trying to achieve (e.g., application delivery, security, multi-cloud management)?
- Which F5 Networks product best suits your requirements (e.g., BIG-IP appliance, virtual appliance, Cloud Edition BIG-IP)?
2. Choose your deployment method:
- On-premises hardware: Physical appliance installation.
- Virtual environment: Deployment on your virtualization platform (e.g., VMware, KVM).
- Cloud deployment: Managed through F5 cloud services (e.g., Cloud Edition BIG-IP).
3. Gather necessary information and resources:
- Product documentation: Specific installation guides and manuals for your chosen product.
- Software downloads: Obtain the appropriate BIG-IP image or package from F5 Networks.
- Hardware requirements: Ensure you have compatible hardware specifications for physical deployments.
- Network configuration details: Understand your existing network topology and IP addressing scheme.
4. Follow the installation guide:
- Each F5 Networks product comes with detailed installation instructions specific to its model and deployment method.
- These guides typically cover:
- Hardware installation (if applicable)
- Software configuration
- Initial network setup
- Security configuration
- Verification and testing
5. Additional considerations:
- Licensing: Ensure you have the necessary licenses for your chosen product and features.
- Configuration customization: Tailor the settings to your specific network environment and policies.
- Post-installation tasks: Update firmware, integrate with management tools, and monitor performance.
Important notes:
- Due to the diverse product range and potential complexity, I cannot provide specific installation instructions without knowing your chosen product and deployment method.
- Consider seeking professional assistance for complex deployments or if you lack technical expertise.
Note:
- F5 Networks acquired NGINX, Inc. in 2019. Some products previously under NGINX are now part of the F5 portfolio. Ensure you consult the correct resources and instructions specific to your chosen product, whether an original F5 offering or an acquired NGINX solution.
- The specific installation process for Cloud Edition BIG-IP, a cloud-based service, differs from on-premises or virtual appliance deployments. Follow the guidance provided by F5 for cloud deployments.
Basic Tutorials of F5 Networks: Getting Started

F5 Networks is known for providing solutions related to application delivery and security, including load balancing, application firewall, and other networking services. Below are step-by-step basic tutorials to help you get started with F5 Networks’ BIG-IP platform.
Prerequisites:
- Access to F5 BIG-IP:
- Have access to an F5 BIG-IP device, either physical or virtual.
2. BIG-IP Licensing:
- Ensure that your BIG-IP device is properly licensed.
Step 1: Initial Configuration of BIG-IP Device
- Access the BIG-IP Configuration Utility:
- Open a web browser and enter the management IP address of the BIG-IP device.
- Sign in with the default or configured credentials.
2. Change Admin Password:
- Change the default admin password for security:
- Navigate to
System > Admin > Admin Accounts. - Click on
adminand update the password.
- Navigate to
3. License Activation:
- Activate the license on the BIG-IP device:
- Navigate to
System > License. - Click on
Activate Licenseand follow the prompts.
- Navigate to
Step 2: Basic Network Configuration
- Configure VLANs:
- Create VLANs to segment traffic:
- Navigate to
Local Traffic > VLANs. - Click on
Createto add a new VLAN.
- Navigate to
2. Create Self IP Addresses:
- Configure Self IP addresses for VLANs:
- Navigate to
Local Traffic > Self IP. - Click on
Createto add a new Self IP.
- Navigate to
Step 3: Create a Simple Virtual Server
- Configure a Pool:
- Create a pool of servers:
- Navigate to
Local Traffic > Pools. - Click on
Createto add a new pool.
- Navigate to
2. Create a Virtual Server:
- Configure a virtual server:
- Navigate to
Local Traffic > Virtual Servers. - Click on
Createto add a new virtual server.
- Navigate to
Step 4: Configure iRules
- Create an iRule:
- Write a simple iRule to customize traffic behavior:
- Navigate to
Local Traffic > iRules. - Click on
Createto add a new iRule.
- Navigate to
2. Attach iRule to a Virtual Server:
- Attach the created iRule to a virtual server:
- Navigate to
Local Traffic > Virtual Servers. - Edit the virtual server and associate the iRule.
- Navigate to
Step 5: Configure Access Control Lists (ACLs)
- Create ACLs:
- Implement Access Control Lists to control traffic:
- Navigate to
Local Traffic > iRules. - Click on
Createto add a new ACL.
- Navigate to
2. Associate ACLs with Policies:
- Associate ACLs with policies for enforcement:
- Navigate to
Security > Application Security > Application Security Policies. - Edit a policy and associate the ACL.
- Navigate to
These tutorials provide a basic introduction to configuring F5 BIG-IP, covering initial setup, network configuration, virtual server creation, iRules, and ACLs.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
