What is FireEye?

FireEye is a cybersecurity company that provides a range of solutions and services to help organizations detect, prevent, respond to, and mitigate advanced cyber threats and attacks. FireEye is known for its expertise in threat intelligence, malware analysis, and cybersecurity technologies.
FireEye’s cybersecurity solutions and services are designed to provide a holistic approach to cybersecurity, addressing various aspects of threat detection, prevention, and response. These use cases demonstrate how FireEye helps organizations protect their digital assets and sensitive data from a wide range of cyber threats.
Top 10 use cases of FireEye:
Here are the top 10 use cases of FireEye:
- Advanced Threat Detection: FireEye’s solutions are designed to detect and alert on advanced threats, including APTs (Advanced Persistent Threats), zero-day exploits, and malware that traditional security tools may miss.
- Malware Analysis and Sandboxing: FireEye offers malware analysis tools and sandboxes that allow organizations to safely execute and analyze suspicious files and attachments to identify malicious behavior.
- Threat Intelligence: FireEye provides access to threat intelligence feeds and reports, helping organizations stay informed about the latest cyber threats, vulnerabilities, and tactics used by threat actors.
- Incident Response: FireEye offers incident response services and technologies that help organizations investigate and respond to cybersecurity incidents, including data breaches and intrusions.
- Email Security: FireEye’s email security solutions protect organizations from email-based threats, including phishing attacks, spam, and malicious attachments, by analyzing and blocking malicious content.
- Endpoint Security: FireEye provides endpoint security solutions that monitor and protect individual devices (endpoints) from malware and other threats, enhancing overall device security.
- Network Security: FireEye’s network security solutions help organizations secure their network infrastructure by detecting and blocking malicious traffic and suspicious network activity.
- Threat Intelligence Sharing: FireEye supports the sharing of threat intelligence among organizations and industries to improve collective cybersecurity defense and incident response efforts.
- Security Awareness Training: FireEye offers security awareness training programs to educate employees and raise security awareness throughout an organization, reducing the risk of social engineering attacks.
- Cloud Security: With the increasing adoption of cloud services, FireEye provides cloud security solutions that protect cloud-based environments and applications from cyber threats.
- IoT Security: As the Internet of Things (IoT) continues to grow, FireEye offers IoT security solutions to protect connected devices and networks from cyber threats targeting IoT ecosystems.
- Threat Hunting: FireEye’s expertise and tools can be used for proactive threat hunting, where security teams actively search for hidden threats and vulnerabilities within an organization’s network and endpoints.
- Threat and Vulnerability Management: FireEye solutions can help organizations manage and prioritize threats and vulnerabilities effectively to enhance their cybersecurity posture.
- Regulatory Compliance: FireEye technologies and services assist organizations in achieving and maintaining compliance with various regulatory requirements related to data security and privacy.
- Insider Threat Detection: FireEye’s solutions can help organizations detect and mitigate insider threats by monitoring user activity and identifying suspicious behavior.
What are the feature of FireEye?
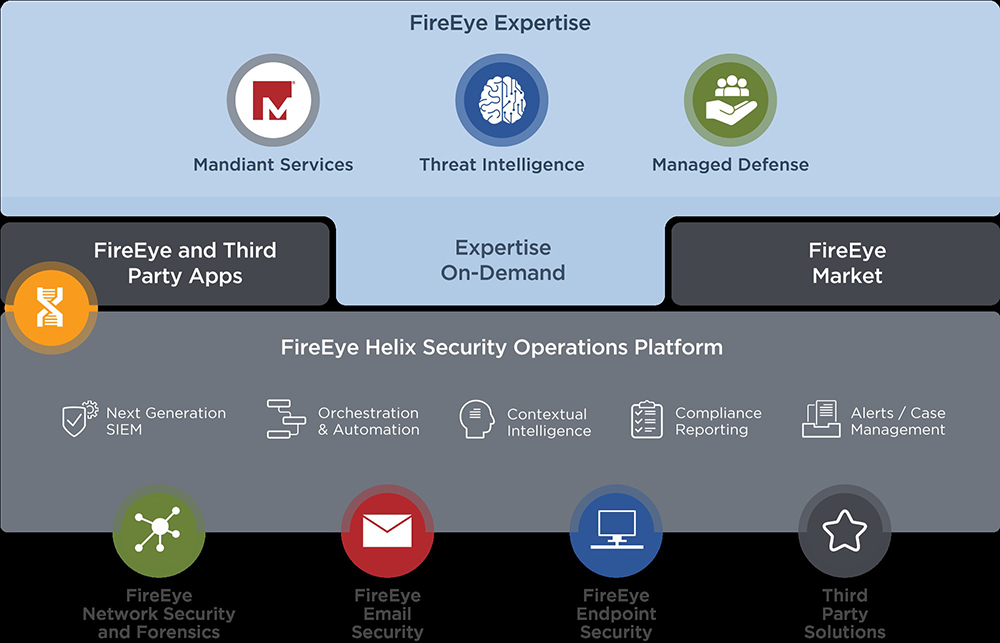
FireEye is a cybersecurity company that offers a range of products and services to help organizations protect against and respond to cyber threats. While the specific features and capabilities of FireEye’s products may vary, here are some common features and an overview of how FireEye works:
Key Features of FireEye:
- Advanced Threat Detection: FireEye’s solutions are designed to detect advanced threats, including APTs (Advanced Persistent Threats), zero-day exploits, and targeted attacks, using a combination of signature-based and behavioral analysis techniques.
- Dynamic Threat Intelligence: FireEye provides dynamic threat intelligence feeds that offer real-time information about emerging threats, vulnerabilities, and indicators of compromise (IOCs).
- Malware Analysis: FireEye offers sandboxing and malware analysis tools that allow organizations to safely execute and analyze suspicious files and email attachments to identify malicious behavior.
- Endpoint Security: FireEye provides endpoint security solutions that protect individual devices (endpoints) from malware and other threats, using features like anti-virus, host-based intrusion prevention, and behavioral analysis.
- Network Security: FireEye’s network security solutions monitor network traffic and detect and block malicious activity, including network-based attacks and command-and-control communication.
- Email Security: FireEye’s email security solutions protect organizations from email-based threats such as phishing attacks, spam, and malicious attachments.
- Threat Intelligence Sharing: FireEye supports the sharing of threat intelligence among organizations to improve collective cybersecurity defense and incident response efforts.
- Incident Response Services: FireEye offers incident response services to help organizations investigate and respond to cybersecurity incidents, including data breaches and intrusions.
- Security Awareness Training: FireEye provides security awareness training programs to educate employees and raise security awareness throughout an organization, reducing the risk of social engineering attacks.
- Cloud Security: FireEye offers cloud security solutions that protect cloud-based environments and applications from cyber threats.
- Threat Analytics: FireEye’s analytics tools help organizations analyze and correlate threat data to identify patterns and trends, allowing for more effective threat detection and response.
How FireEye works and Architecture?
FireEye’s products and services work together to provide a comprehensive cybersecurity defense:
- Data Collection: FireEye collects data from various sources, including network traffic, email, endpoints, and cloud environments.
- Analysis and Detection: The collected data is analyzed using a combination of signature-based and behavioral analysis techniques to detect known and unknown threats.
- Alerting and Reporting: When a threat is detected, FireEye generates alerts and provides reports to inform security teams about the nature of the threat and its potential impact.
- Threat Intelligence: FireEye’s dynamic threat intelligence feeds are continuously updated to provide organizations with real-time information about emerging threats and vulnerabilities.
- Malware Analysis: Suspicious files and attachments are sent to FireEye’s sandboxing and malware analysis tools for deeper inspection.
- Incident Response: If a cybersecurity incident is confirmed, organizations can engage FireEye’s incident response services to investigate the incident and mitigate the threat.
FireEye Architecture:
FireEye’s architecture typically consists of a combination of physical and virtual appliances deployed throughout an organization’s network. These appliances perform tasks such as network traffic analysis, email scanning, and endpoint protection. The collected data is sent to central analysis engines for further processing and correlation.
FireEye’s architecture is designed to provide visibility and protection across various attack vectors, including networks, email, and endpoints. The company’s products are designed to work together to provide a holistic and integrated approach to cybersecurity.
It’s important to note that the specific architecture and capabilities of FireEye’s products may vary depending on the specific solutions and versions deployed by an organization. FireEye’s offerings continue to evolve to address emerging cyber threats and challenges.
How to Install FireEye?
To install FireEye, you will need the following:
- A Windows or Linux server with the following system requirements:
- CPU: 8 cores
- Memory: 16 GB
- Storage: 500 GB-1 TB
- A FireEye license
- A FireEye installation package
Steps to install FireEye on Windows:
- Download the FireEye installation package from the FireEye website.
- Double-click the installation package to start the installation process.
- Follow the on-screen instructions to fulfill the installation process.
- Once the installation is complete, you will need to configure the FireEye agent.
Steps to install FireEye on Linux:
- Download the FireEye installation package from the FireEye website.
- Extract the installation package to a directory on your server.
- Open a terminal window and navigate to the directory where you extracted the installation package.
- Run the following command to start the FireEye agent installation process:
sudo ./agent_install.sh- Apply the on-screen instructions to complete the installation process.
Once the installation is complete, you will need to configure the FireEye agent.
Steps to configure the FireEye agent:
- Open the FireEye Management Console.
- Navigate to the Agents page.
- Click the Add Agent button.
- Select the type of agent that you want to install and click the Next button.
- Enter the required information for the agent and click the Finish button.
The FireEye agent will now be installed and configured on your server.
Additional tips for installing FireEye:
- Make sure that your server has the required system requirements.
- If you are installing FireEye in a production environment, it is recommended to follow the FireEye hardening guide to secure your installation.
- You can also find a variety of tutorials and other resources on the FireEye website.
FireEye is a powerful security solution that can help you to protect your organization from a wide range of threats. By following the steps above, you can learn how to install and configure FireEye to improve your security posture.
Basic Tutorials of FireEye: Getting Started

The following steps are the basic tutorial on how to use FireEye to improve your security posture:
- Getting Started
- Create a FireEye account.
- Log in to the FireEye Management Console.
- Review the Getting Started documentation.
- Deploying Sensors
- Deploy FireEye sensors to your network.
- FireEye sensors can be deployed on physical servers, virtual machines, and cloud-based servers.
- Configuring Sensors
- Configure the FireEye sensors to collect the data that you need to protect your organization.
- You can configure the FireEye sensors to collect a variety of data, including network traffic, file activity, and system events.
- Monitoring Events
- Monitor the events that are collected by the FireEye sensors.
- FireEye provides a variety of tools to help you monitor events, including dashboards, reports, and alerts.
- Investigating Incidents
- Investigate incidents that are detected by the FireEye sensors.
- FireEye provides a variety of tools to help you investigate incidents, such as threat intelligence, analytics, and collaboration tools.
- Responding to Incidents
- Respond to incidents that are investigated by the FireEye sensors.
- FireEye provides a variety of tools to help you respond to incidents, such as automated playbooks and case management tools.
- Reporting
- Generate reports to track your security posture and to identify trends in your security data.
- FireEye provides a variety of reports, including incident reports, threat intelligence reports, and compliance reports.
Some additional tips for using FireEye:
- Use the FireEye community to get help and support from other FireEye users.
- Take advantage of FireEye’s training resources to learn more about the platform and how to use it effectively.
- Contact FireEye support if you have any questions or problems.
FireEye is a powerful security platform that can help you to improve your security posture by helping you to identify, assess, and mitigate threats to your organization. By following the steps above, you can learn how to use FireEye to deploy sensors, configure sensors, monitor events, investigate incidents, respond to incidents, and generate reports.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
