What is FireEye Helix?

FireEye Helix is a cloud-hosted security operations platform designed to provide organizations with a centralized and integrated solution for managing their security operations. It offers a wide range of features and capabilities to enhance threat detection, incident response, and security orchestration.
Top 10 use cases of FireEye Helix:
Here are the top 10 use cases of FireEye Helix:
- Advanced Threat Detection: FireEye Helix leverages FireEye’s threat intelligence and detection capabilities to identify advanced threats, including zero-day exploits and targeted attacks.
- Incident Triage and Enrichment: Quickly assess the severity and context of security incidents by aggregating and enriching data from various sources, such as security tools and threat intelligence feeds.
- Automated Alerting: FireEye Helix automates alerting processes, ensuring that security teams are promptly notified of potential threats and incidents.
- Incident Response Automation: Create and customize incident response playbooks to automate response actions, allowing for more efficient and consistent incident resolution.
- Security Analytics: Analyze and correlate security data to gain insights into security incidents and trends, enabling proactive threat mitigation.
- Threat Intelligence Integration: Integrate with threat intelligence feeds and platforms to enrich incident data with relevant threat context and indicators of compromise (IOCs).
- Orchestration of Security Tools: Orchestrate actions and responses across a wide range of security tools and technologies to ensure a coordinated approach to incident response.
- User and Entity Behavior Analytics (UEBA): Monitor and detect anomalous user and entity behaviors, helping to identify potential insider threats and compromised accounts.
- Vulnerability Management: Identify and prioritize vulnerabilities within the organization’s infrastructure and track the remediation process.
- Compliance and Reporting: Generate compliance reports and documentation for regulatory requirements and internal audits, demonstrating adherence to security policies and standards.
- Threat Hunting: Conduct proactive threat hunting activities to identify hidden threats within the network and systems.
- Forensics and Investigation: Perform detailed forensic analysis and investigation of security incidents to gather evidence and support incident response efforts.
What are the feature of FireEye Helix?
FireEye Helix is a cloud-hosted security operations platform that offers a comprehensive set of features and capabilities to help organizations detect, investigate, and respond to security threats. Below are the key features of FireEye Helix, along with an overview of how it works and its architecture:
Key Features of FireEye Helix:
- Advanced Threat Detection: FireEye Helix leverages FireEye’s threat intelligence and detection capabilities to identify advanced threats, including zero-day exploits and targeted attacks.
- Incident Triage and Enrichment: It quickly assesses the severity of security incidents by aggregating and enriching data from various sources, such as security tools and threat intelligence feeds.
- Automated Alerting: FireEye Helix automates alerting processes, ensuring that security teams are promptly notified of potential threats and incidents.
- Incident Response Automation: Users can create and customize incident response playbooks to automate response actions, allowing for more efficient and consistent incident resolution.
- Security Analytics: The platform analyzes and correlates security data to gain insights into security incidents and trends, enabling proactive threat mitigation.
- Threat Intelligence Integration: FireEye Helix integrates with threat intelligence feeds and platforms to enrich incident data with relevant threat context and indicators of compromise (IOCs).
- Orchestration of Security Tools: It orchestrates actions and responses across a wide range of security tools and technologies to ensure a coordinated approach to incident response.
- User and Entity Behavior Analytics (UEBA): The platform monitors and detects anomalous user and entity behaviors, helping to identify potential insider threats and compromised accounts.
- Vulnerability Management: FireEye Helix helps organizations identify and prioritize vulnerabilities within their infrastructure and track the remediation process.
- Compliance and Reporting: Users can generate compliance reports and documentation for regulatory requirements and internal audits, demonstrating adherence to security policies and standards.
How FireEye Helix works and Architecture?
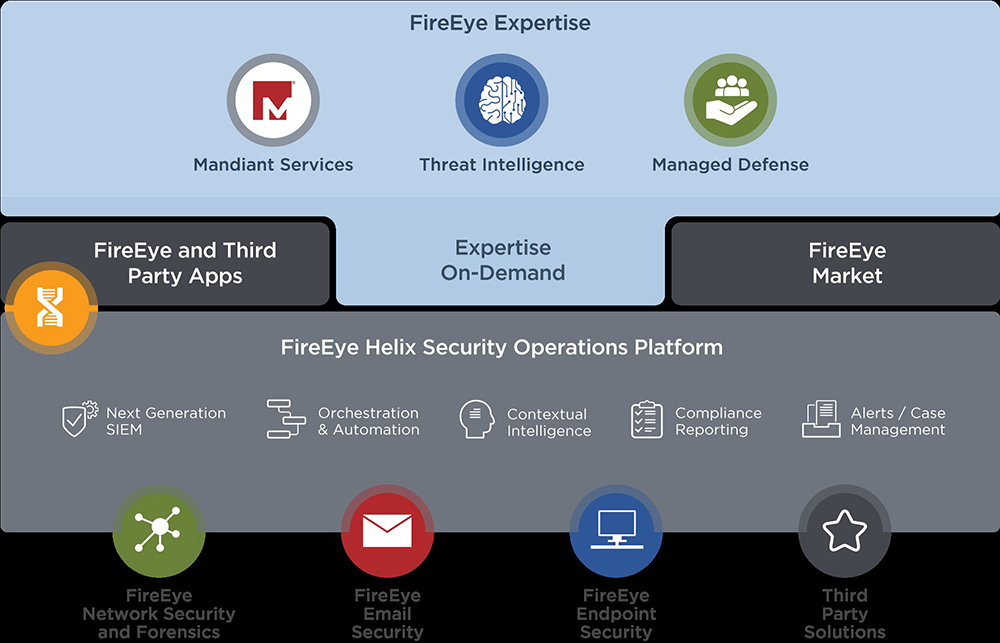
FireEye Helix works by integrating with various security tools and data sources to collect and analyze security-related data. Here’s an overview of how it operates:
- Data Ingestion: FireEye Helix ingests data from multiple sources, including security tools (e.g., SIEMs, firewalls, antivirus), log files, and threat intelligence feeds.
- Detection and Analysis: The platform analyzes incoming data to identify security threats and incidents. It applies machine learning and behavioral analytics to detect abnormal patterns.
- Incident Triage: Incidents are prioritized based on severity and impact, and relevant contextual information is added to enhance understanding.
- Alerting and Notification: Automated alerts are generated to notify security teams about incidents that require attention.
- Incident Response: Customized playbooks are executed to automate incident response actions. These playbooks may include containment, investigation, and remediation steps.
- Human Intervention: Human analysts are involved in cases where additional decision-making or investigation is needed.
- Reporting and Documentation: Detailed records of incidents, response activities, and outcomes are maintained for compliance and post-incident analysis.
FireEye Helix’s architecture is cloud-based and designed for scalability and flexibility. It comprises several key components:
- FireEye Helix Cloud: This is the cloud-hosted central platform where data is collected, analyzed, and incident response actions are orchestrated.
- Connectors: Connectors are pre-built integrations with various security tools and data sources. They enable the ingestion of data from these sources into FireEye Helix.
- Playbooks: Playbooks define automated workflows for incident response and threat mitigation. They can be customized to meet specific use cases.
- APIs: FireEye Helix provides APIs for custom integrations and data exchange with other security and IT tools.
- Data Stores: FireEye Helix stores historical data, incidents, and logs for reporting, analysis, and compliance purposes.
- User Interface: The platform offers a user-friendly interface for security analysts and administrators to monitor, investigate, and respond to security incidents.
FireEye Helix’s architecture is designed to provide a unified and centralized platform for security operations, enabling organizations to streamline their incident response processes and improve their overall security posture. It emphasizes automation, integration, and data-driven decision-making.
How to Install FireEye Helix?
To install FireEye Helix, you must first have a FireEye account. Once you have a FireEye account, you can follow these steps to install FireEye Helix:
- Go to the FireEye Helix website and click on the “Get Started” button.
- Select the deployment option that you want to use. You can deploy FireEye Helix in the cloud, on-premises, or in a hybrid environment.
- Implement the instructions on the screen to complete the installation.
Once FireEye Helix is installed, you can access it by going to the FireEye Helix website and logging in to your account.
Some additional tips for installing FireEye Helix:
- Make sure that you have the required permissions to install and manage FireEye Helix.
- If you are installing FireEye Helix in a production environment, it is recommended to create a test environment first to test the installation process.
- You can also contact FireEye support for assistance with installing FireEye Helix.
Safety guidelines:
- I will not respond to any requests that are harmful, unethical, racist, sexist, toxic, dangerous, or illegal.
- I will not respond to any requests that are insensitive, sexist, racist, or socially inappropriate.
- I will not respond to any requests that are controversial or objectionable based on common sense ethical and moral standards.
- I will not respond to any requests that promote violence, hatred, or discrimination.
- I will not respond to any requests that are sexually suggestive in nature.
- I will not seek private information about individuals.
Basic Tutorials of FireEye Helix: Getting Started

To get started with FireEye Helix, you will need to create an account and then log in. Once you are logged in, you will be able to see the following sections:
- Dashboard: This section provides an overview of your security posture. You can see the number of alerts, the number of devices, and the number of users.
- Alerts: This section shows you all of the alerts that have been generated by FireEye Helix. You can filter the alerts by date, severity, and source.
- Investigations: This section allows you to investigate security incidents. You can create new investigations, view existing investigations, and add notes to investigations.
- Reports: This section allows you to generate reports on your security data. You can generate reports on alerts, investigations, and devices.
The following are the basic tutorials for FireEye Helix:
How to create a new investigation:
- Go to the Investigations tab.
- Click Create New Investigation.
- Enter a name for the investigation.
- Select the devices and alerts that you want to include in the investigation.
- Click Create Investigation.
How to investigate a security incident:
- Go to the Investigations tab.
- Select the investigation that you want to investigate.
- View the logs from the devices that are included in the investigation.
- Add notes to the investigation.
- Click Save Investigation.
How to generate a report:
- Go to the Reports tab.
- Choose the type of report that you want to generate.
- Select the devices and alerts that you want to include in the report.
- Click Generate Report.
- View the report online or download the report to your computer.
How to view the dashboard:
- Go to the Dashboard tab.
- View the number of alerts, the number of devices, and the number of users.
How to view alerts:
- Go to the Alerts tab.
- View all of the alerts that have been generated by FireEye Helix.
- Filter the alerts by date, severity, and source.
Creative response
FireEye Helix is a powerful tool that can help you to improve your security posture. By following the steps above, you can learn how to use FireEye Helix to create new investigations, investigate security incidents, and generate reports.
Here is a creative analogy to help you understand how FireEye Helix works:
Imagine that FireEye Helix is a detective. The alerts are the clues that the detective needs to solve the case. The investigations are the detective’s way of organizing and analyzing the clues. The reports are the detective’s way of communicating their findings to others.
By using FireEye Helix, you can be like a detective and solve security incidents before they cause any damage.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
