What is HashiCorp Sentinel?

HashiCorp Sentinel is a policy as code (PaC) framework that is a part of the HashiCorp ecosystem. It is designed to automate and enforce policies across the software development and infrastructure deployment lifecycle. Sentinel enables organizations to codify their policies and integrate them into their infrastructure and application workflows.
HashiCorp Sentinel works by defining policies as code, which are written using the Sentinel policy language. These policies are then evaluated during the execution of workflows, such as infrastructure provisioning or application deployment, to ensure compliance with the defined rules. Sentinel integrates with various HashiCorp tools like Terraform, Vault, and Nomad, as well as other third-party solutions, making it a powerful tool for policy enforcement and governance in modern cloud and infrastructure environments.
Top 10 use cases of HashiCorp Sentinel:
Here are the top 10 use cases of HashiCorp Sentinel:
- Infrastructure as Code (IaC) Policy Enforcement: Sentinel can enforce policies on Infrastructure as Code (IaC) files to ensure that infrastructure deployments adhere to security, compliance, and operational requirements.
- Terraform Policy Enforcement: Sentinel is often used with HashiCorp Terraform to define and enforce policies that control the creation, modification, or deletion of cloud resources and infrastructure.
- Cloud Resource Governance: Sentinel helps organizations govern the usage of cloud resources by enforcing policies on cloud services and configurations, ensuring cost management and security.
- Compliance and Security: Sentinel enables automated compliance checks by ensuring that infrastructure and application deployments comply with industry standards, regulatory requirements, and organizational security policies.
- Change Control and Approval Workflows: Organizations can use Sentinel to implement change control policies, requiring approval for specific changes to infrastructure or application configurations.
- Cost Optimization: Sentinel can enforce policies to manage and optimize cloud resource costs, such as tagging resources for cost allocation or controlling resource types and sizes.
- Resource Tagging: Organizations can define and enforce resource tagging policies to ensure consistent labeling of resources for tracking and management purposes.
- Secret Management: Sentinel can be used to enforce policies around secret management, ensuring secure handling of sensitive data, such as credentials and API keys.
- Access Control: Sentinel can enforce access control policies, restricting access to certain resources or actions based on role-based access control (RBAC) rules.
- Custom Policies: Sentinel allows organizations to define custom policies tailored to their specific requirements, making it flexible for addressing unique use cases and compliance needs.
- Application Deployment Policies: Sentinel can be used to define and enforce policies on application deployment workflows, ensuring consistency and adherence to best practices.
- Multi-Cloud Governance: Organizations with multi-cloud environments can use Sentinel to manage policies consistently across different cloud providers.
What are the feature of HashiCorp Sentinel?
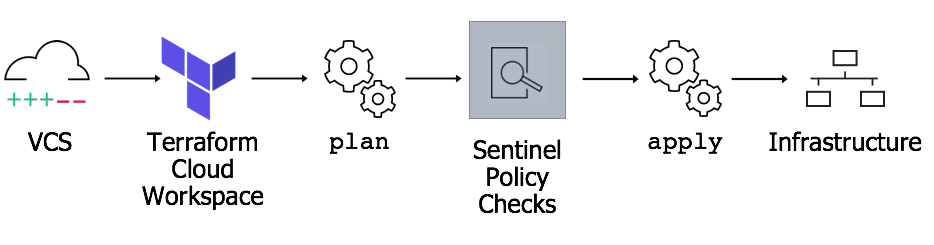
HashiCorp Sentinel is a policy as code (PaC) framework that provides a set of features and capabilities for defining, enforcing, and managing policies across various HashiCorp tools and infrastructure workflows. Here are the key features of HashiCorp Sentinel:
- Policy Language: Sentinel offers a domain-specific language (DSL) for writing policies as code, allowing users to define policies in a human-readable and expressive manner.
- Policy as Code: Policies are defined as code, enabling version control, collaboration, and automation of policy enforcement.
- Integration: Sentinel seamlessly integrates with various HashiCorp tools, including Terraform, Vault, Consul, Nomad, and Boundary, allowing users to enforce policies throughout the software development and deployment lifecycle.
- Policy Libraries: Sentinel supports the use of reusable policy modules, making it easy to share and apply common policies across different environments and projects.
- Dynamic Policy Data: Policies can access dynamic data sources, enabling context-aware policy decisions based on real-time information.
- Rule-Based Evaluation: Policies are evaluated based on rules and conditions defined by users, providing fine-grained control over policy enforcement.
- Policy Testing: Sentinel includes testing and simulation capabilities to validate policies before applying them to production workflows.
- Compliance Reporting: Sentinel generates compliance reports, helping organizations demonstrate adherence to policies, standards, and regulations.
- Change Control: Policies can be configured to require approval for specific changes, ensuring that critical changes are reviewed and authorized.
- Customization: Users can define custom policies to address specific organizational requirements, security controls, and compliance needs.
How HashiCorp Sentinel works and Architecture?
Here’s an overview of how HashiCorp Sentinel works and its architecture:
1. Policy Authoring:
- Users define policies in the Sentinel policy language.
- Policies are written as code and stored in version control systems for management and collaboration.
2. Policy Repository:
- Policies are stored in a central policy repository, which can be hosted on a version control platform like Git.
3. Integration with HashiCorp Tools:
- HashiCorp Sentinel integrates with HashiCorp tools such as Terraform, Vault, Consul, Nomad, and Boundary.
4. Workflow Execution:
- During infrastructure provisioning, application deployment, or other workflows, the HashiCorp tool invokes Sentinel to evaluate policies.
- Sentinel checks whether the defined policies allow or deny the requested actions.
5. Policy Evaluation:
- Sentinel evaluates policies based on defined rules, conditions, and context-specific data.
- Policies can access dynamic data sources to make real-time decisions.
6. Approval Workflow:
- If configured, Sentinel enforces approval workflows for specific actions, requiring manual or automated approval before proceeding.
7. Compliance Reporting:
- Sentinel generates compliance reports, highlighting policy violations and adherence to organizational policies and standards.
8. Policy Testing:
- Sentinel includes testing and simulation capabilities for policy validation and troubleshooting.
9. Feedback Loop:
- Sentinel provides feedback to users and administrators regarding policy evaluations and violations.
10. Continuous Improvement:
– Users can iterate on policies, refine them, and adapt to changing requirements, ensuring ongoing policy compliance and security.
Overall, HashiCorp Sentinel serves as a critical component in the HashiCorp ecosystem, enabling organizations to enforce policies consistently, enhance security, and ensure compliance throughout the infrastructure and application deployment lifecycle. Its flexible architecture allows it to adapt to various use cases and integrate seamlessly with HashiCorp tools and workflows.
How to Install HashiCorp Sentinel?
To install HashiCorp Sentinel, you can use the following steps:
- Download the Sentinel CLI from the HashiCorp website.
- Unzip the Sentinel CLI package.
- Add the Sentinel CLI to your PATH environment variable.
- Verify that Sentinel is installed by running the following command:
sentinel --versionThis should output the version of Sentinel that is installed.
Some additional tips for installing Sentinel:
- Make sure that your system meets the minimum requirements for Sentinel. You can find the minimum requirements on the HashiCorp website.
- If you are installing Sentinel on a production system, be sure to test Sentinel thoroughly before deploying it.
- If you have any questions or problems installing Sentinel, please contact HashiCorp Support for assistance.
Example of installing Sentinel on Ubuntu 22.04:
- Download the Sentinel CLI from the HashiCorp website:
wget https://releases.hashicorp.com/sentinel/0.11.0/sentinel_0.11.0_linux_amd64.zip- Unzip the Sentinel CLI package:
unzip sentinel_0.11.0_linux_amd64.zip- Add the Sentinel CLI to your PATH environment variable:
export PATH=$PATH:$(pwd)/sentinel- Verify that Sentinel is installed:
sentinel --versionThis should output the version of Sentinel that is installed.
Once Sentinel is installed, you can start using it to manage and enforce policy for your applications.
Basic Tutorials of HashiCorp Sentinel: Getting Started

Let’s have a look at a basic tutorial of HashiCorp Sentinel:
Creating a new Sentinel policy:
- Create a new file with a
.sentinelextension. This is the Sentinel policy file. - Add a
nameand arulessection to the policy file. - In the
rulessection, add one or more rules. Each rule should have aname, adescription, and aconditionsection. - The
conditionsection is where you specify the conditions that must be met for the rule to be satisfied. You can use expressions and variables in the condition section. - If the condition section is satisfied, the rule will take the specified actions. You can specify actions such as returning an error, sending a notification, or modifying a resource.
Example of a simple Sentinel policy:
name: "My Policy"
rules:
- name: "Rule 1"
description: "This rule checks if the user is authenticated."
condition:
- user.authenticated: true
- name: "Rule 2"
description: "This rule checks if the user is authorized to access the
resource."
condition:
- user.authorized: true
This policy will check if the user is authenticated and authorized to access the resource. If either of these conditions is not met, the policy will return an error.
Running the Sentinel policy:
To run the Sentinel policy, you can use the sentinel evaluate command.
sentinel evaluate my_policy.sentinel
This will evaluate the policy and return an error if the policy is not satisfied.
You can also run the Sentinel policy as part of a workflow. For example, you could use Sentinel to check the policy before deploying a new version of an application.
Verifying the results:
To verify the results of the policy evaluation, you can check the output of the sentinel evaluate command.
If the policy is satisfied, the command will output a message such as:
“Policy ‘My Policy’ is satisfied.”
If the policy is not satisfied, the command will output an error message.
Writing more complex Sentinel policies:
Sentinel policies can be as simple or as complex as you need them to be. You can use Sentinel policies to manage and enforce all aspects of your applications, including security, compliance, and performance.
To write more complex Sentinel policies, you can use the following resources:
- Rules: You can use rules to check for specific conditions and to take actions if those conditions are met.
- Expressions: You can use expressions to evaluate complex conditions.
- Variables: You can use variables to store values that can be used throughout a policy.
- Policy sets: You can use policy sets to group multiple policies together. This can be useful for managing complex policies.
HashiCorp Sentinel is a powerful tool that can be used to manage and enforce policy for your applications. By following these basic tutorials, you can learn how to start using Sentinel to secure, comply with, and optimize your applications.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
