What is HashiCorp Vault?

HashiCorp Vault is a popular open-source tool and enterprise-grade solution for managing secrets, encryption, and access control in modern IT environments. It helps organizations securely store, manage, and distribute sensitive data and access credentials.
HashiCorp Vault provides a robust and flexible platform for secret management and data protection in modern, dynamic IT environments. It is particularly valuable for organizations looking to enhance security, automate secret rotation, and enforce access control in a scalable manner across various infrastructure platforms, including on-premises data centers and cloud environments.
Top 10 use cases of HashiCorp Vault:
Here are the top 10 use cases for HashiCorp Vault:
- Secret Management: Securely store and manage sensitive information such as API keys, passwords, tokens, and certificates, ensuring they are protected from unauthorized access and breaches.
- Dynamic Secrets: Generate short-lived, dynamic access credentials for databases, cloud services, and other resources on-demand, reducing the exposure of long-lived secrets.
- Data Encryption: Encrypt and decrypt data using cryptographic services provided by Vault, ensuring data confidentiality and integrity for both data at rest and data in transit.
- Access Control: Define fine-grained access policies to control who can access secrets and under what conditions, helping organizations enforce the principle of least privilege.
- Authentication Backend: Integrate with various authentication backends, including LDAP, OIDC, and AWS IAM, to ensure secure and authenticated access to Vault.
- Tokenization and Data Masking: Protect sensitive data by tokenizing it or applying data masking techniques, allowing organizations to safely handle customer and payment card data.
- Secure Service-to-Service Communication: Facilitate secure communication between microservices and applications by providing cryptographic keys and certificates.
- Certificate Authority: Act as a certificate authority (CA) to issue and manage SSL/TLS certificates for applications, servers, and services, ensuring secure communication.
- Secret Rotation: Automate the rotation of secrets and access credentials, minimizing the risk of exposure due to long-lived secrets.
- Compliance and Audit: Maintain comprehensive audit logs and compliance reports to track access to secrets, helping organizations meet regulatory requirements and security standards.
- Dynamic Infrastructure: Integrate with infrastructure-as-code (IaC) tools like Terraform to dynamically provision and manage secrets for cloud resources and infrastructure.
- Secure CI/CD Pipelines: Integrate Vault into CI/CD pipelines to securely manage secrets and access credentials used during application deployment and testing.
What are the feature of HashiCorp Vault?
HashiCorp Vault is a powerful and flexible secrets management and data protection tool designed for modern IT environments. It offers a range of features for securing and managing secrets, encryption, and access control. Here are some of the key features of HashiCorp Vault, along with an overview of how it works and its typical architecture:
Key Features of HashiCorp Vault:
- Secrets Management: Vault provides a secure way to manage and store secrets such as API keys, passwords, tokens, and encryption keys.
- Dynamic Secrets: It can generate short-lived, dynamic secrets on-demand for various resources like databases, cloud services, and SSH, reducing the risk associated with long-lived credentials.
- Data Encryption: Vault offers encryption services for data at rest (transit) and data in transit, ensuring the confidentiality and integrity of sensitive information.
- Access Control Policies: Fine-grained access control is enabled through policies that define who can access what secrets and under what conditions, following the principle of least privilege.
- Authentication Backends: It supports various authentication backends, including LDAP, OIDC, AWS IAM, and more, ensuring secure and authenticated access to Vault.
- Tokenization and Data Masking: Vault can tokenize or mask sensitive data to protect it from exposure, facilitating the secure handling of customer data and payment card information.
- Dynamic Infrastructure: Integration with infrastructure-as-code (IaC) tools like Terraform allows for the dynamic provisioning and management of secrets for cloud resources and infrastructure.
- Certificate Authority (CA): Vault can act as a CA, issuing and managing SSL/TLS certificates for applications, servers, and services, ensuring secure communication.
- Secret Rotation: Automation of secret rotation helps organizations regularly change secrets, minimizing the risk of exposure.
- Audit and Compliance Logging: Comprehensive audit logging and compliance reports enable organizations to track access to secrets, meeting regulatory requirements and security standards.
How HashiCorp Vault works and Architecture?
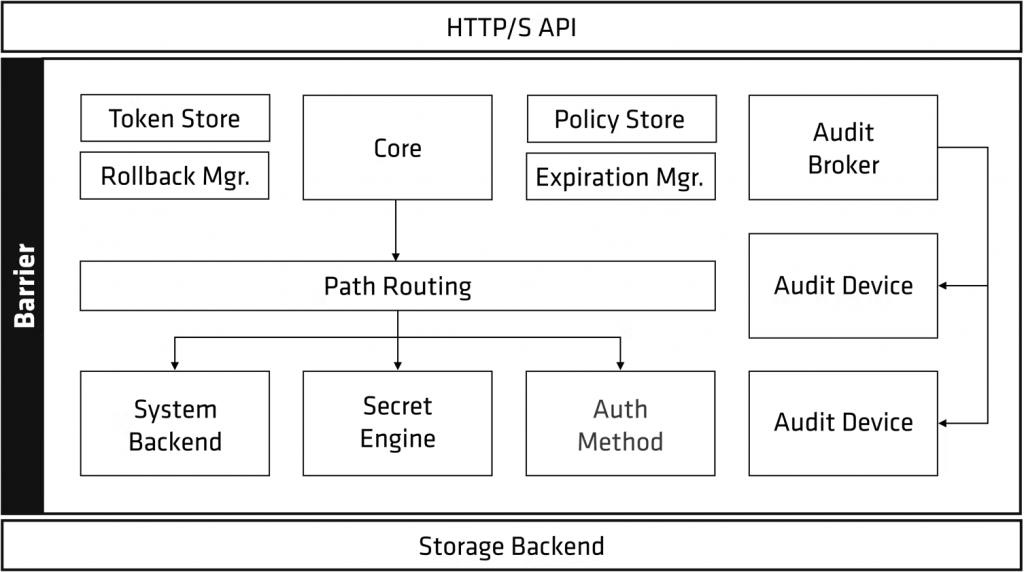
- Initialization: Vault is initialized, and the initial root token is generated during the setup process. This root token has full control over Vault but should be securely stored.
- Mount Secret Engines: Organizations configure secret engines to manage specific types of secrets, such as databases, AWS, or SSH. These secret engines are “mounted” within Vault.
- Authentication: Users and applications authenticate to Vault using various methods, including tokens, usernames/passwords, or external identity providers.
- Authorization and Policies: Vault checks the authenticated entity against access control policies to determine what secrets they are allowed to access.
- Secret Retrieval and Generation: Authorized users and applications can retrieve secrets, generate dynamic secrets, or interact with other Vault features based on their permissions.
- Data Encryption: Vault provides encryption services for data at rest (storage backend) and data in transit (communication with clients and other systems).
- Dynamic Secrets: Vault dynamically generates and manages short-lived secrets for various resources, reducing exposure risks.
- Audit Logging: All actions taken in Vault are logged for auditing purposes, and organizations can configure auditing backends to store these logs.
Vault’s architecture is typically composed of the following components:
- Storage Backend: This component is responsible for storing Vault’s data, including secrets and configuration. Common storage backends include Consul, etcd, or cloud-based storage solutions.
- Core Vault: The core of Vault contains authentication, authorization, and secret engine components. It processes authentication requests, enforces access control policies, and manages secret engines.
- Authentication Backends: Vault supports various authentication methods, including tokens, usernames/passwords, and external identity providers, allowing users and applications to authenticate.
- Secret Engines: These components manage specific types of secrets, such as databases, AWS, and more. Secret engines are mounted within Vault and are responsible for generating and managing secrets.
- Access Control Policies: Vault relies on access control policies to determine what secrets users and applications can access. Policies are defined and enforced through Vault’s policy management.
- API/UI: Vault provides a RESTful API and a user interface for interacting with the system, allowing users and applications to access and manage secrets programmatically or through the UI.
- Audit Backends: Organizations can configure audit backends to capture Vault’s audit logs, enabling compliance and security monitoring.
HashiCorp Vault’s architecture is designed for scalability, security, and flexibility, making it a valuable tool for organizations looking to enhance secrets management and data protection across various infrastructure platforms, including cloud and on-premises environments.
How to Install HashiCorp Vault?
To install HashiCorp Vault, you can follow these steps:
- Download the Vault binary for your operating system from the HashiCorp website.
- Extract the Vault binary to a desired location.
- Add the Vault binary to your PATH environment variable.
- Initialize Vault by running the following command:
“
vault init
“
This will create a new Vault cluster and generate a new root token.
- Store the root token in a secure location.
- Unseal Vault by running the following command:
“
vault unseal
“
You will need to enter the root token to unseal Vault.
Once you have initialized and unsealed Vault, you can start using it to store and manage your secrets.
Some additional tips for installing Vault:
- Make sure that your operating system meets the Vault system requirements.
- Close all other applications before installing Vault.
- If you are having trouble installing Vault, contact HashiCorp support for assistance.
Basic Tutorials of HashiCorp Vault: Getting Started

The following steps are the basic Tutorials of HashiCorp Vault:
1. Initializing Vault
To initialize Vault, run the following command:
vault init
This will create a new Vault cluster and generate a new root token. Store the root token in a secure location.
2. Unsealing Vault
To unseal Vault, run the following command:
vault unseal
You will need to enter the root token to unseal Vault.
3. Creating a Secret
To create a secret, run the following command:
vault write secret/<secret-path> key=<secret-value>
Replace <secret-path> with the path to the secret and <secret-value> with the value of the secret.
4. Reading a Secret
To read a secret, run the following command:
vault read secret/<secret-path>
Replace <secret-path> with the path to the secret.
5. Deleting a Secret
To delete a secret, run the following command:
vault delete secret/<secret-path>
Replace <secret-path> with the path to the secret.
6. Configuring Vault
Vault can be configured using the Vault configuration file. The default configuration file is located at /etc/vault.d/vault.hcl.
7. Using Vault with Applications
Vault can be used with applications to store and manage secrets. To use Vault with an application, you will need to configure the application to use the Vault API.
Some additional tips for using Vault:
- Vault supports a variety of secret engines. You can use secret engines to store different types of secrets, such as database passwords, API keys, and certificates.
- Vault supports policies. Policies can be used to control who has access to which secrets.
- Vault supports audit logging. Audit logging can be used to track who has accessed which secrets and when they accessed them.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
