What is IBM Guardium?

IBM Guardium is a comprehensive data security and protection platform designed to safeguard sensitive data across a wide range of data environments, including databases, data warehouses, cloud platforms, and big data environments. It provides real-time monitoring, auditing, and protection against unauthorized access, data breaches, and other security threats.
Top 10 Use Cases of IBM Guardium:
- Database Activity Monitoring (DAM): Guardium can monitor and audit database activities, such as queries, logins, and data access, to detect and prevent unauthorized actions.
- Data Discovery and Classification: It can automatically discover sensitive data within databases and classify it based on predefined policies, helping organizations identify data assets that require special protection.
- Vulnerability Assessment: Guardium performs vulnerability assessments to identify security weaknesses and misconfigurations in database environments.
- Data Masking and Encryption: Sensitive data can be masked or encrypted to protect it from unauthorized access even in non-production environments.
- Database Encryption: Guardium provides encryption capabilities to safeguard data at rest within databases.
- User and Privilege Management: Guardium offers user and privilege management features to control access to databases and ensure that only authorized users have appropriate privileges.
- Threat Detection and Prevention: It uses advanced analytics to detect abnormal database activities, potential threats, and suspicious behaviors, providing real-time alerts and automated responses.
- Regulatory Compliance: Guardium helps organizations meet compliance requirements by providing audit trails, reports, and evidence of data protection measures.
- Cloud Data Security: It extends its capabilities to cloud platforms, ensuring that sensitive data is protected even when stored or processed in the cloud.
- Big Data Protection: Guardium can be used to secure big data environments, such as Hadoop clusters, by monitoring and protecting data stored in these platforms.
What are the feature of IBM Guardium?
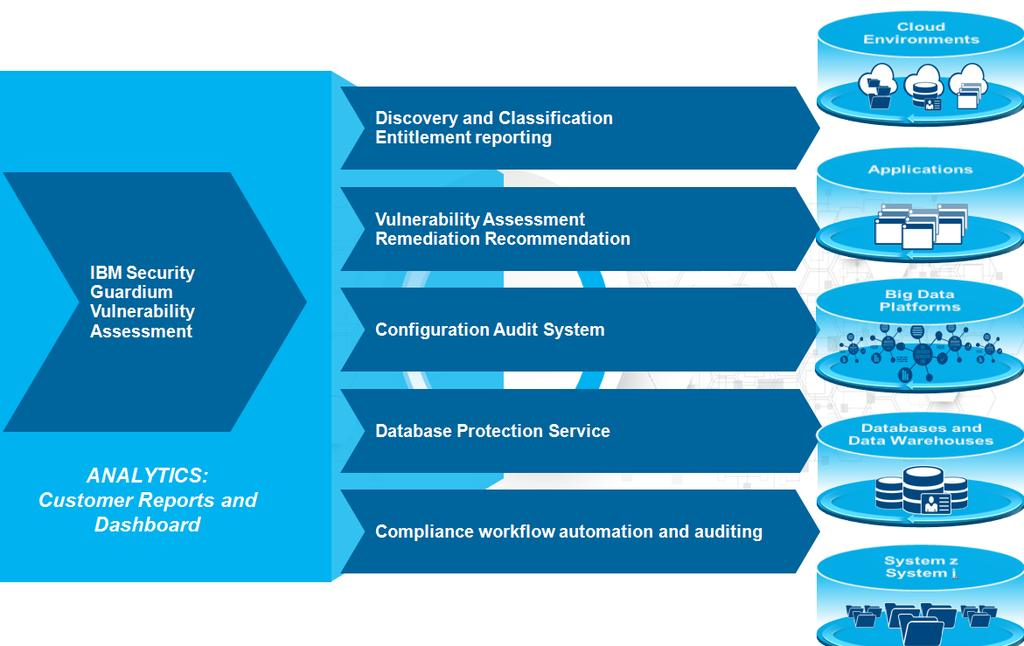
- Real-time monitoring and auditing of data activities.
- Data discovery, classification, and masking.
- Vulnerability assessment and security scanning.
- User and privilege management.
- Encryption of data at rest and in motion.
- Continuous threat detection and prevention.
- Support for various database platforms, cloud environments, and big data systems.
- Compliance reporting and auditing.
- Integration with security information and event management (SIEM) systems.
How IBM Guardium works and Architecture?
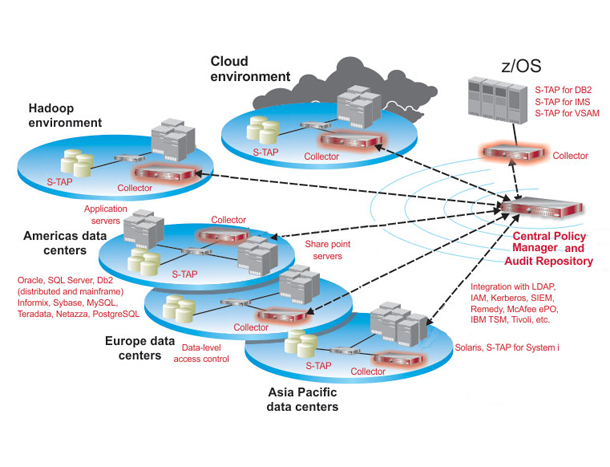
IBM Guardium’s architecture involves agents, collectors, and a centralized management console:
- Agents: Agents are installed on database servers to capture and monitor data activities, such as queries, logins, and data modifications. They send this information to the collector.
- Collectors: Collectors aggregate data from multiple agents and send it to the centralized management server. They also perform data compression and encryption.
- Centralized Management Server: This server manages the Guardium environment. It receives data from collectors, stores it in the central repository, and provides a user interface for configuration, monitoring, and reporting.
- Database Activity Monitoring (DAM): DAM agents monitor and capture data activities, which are then sent to the collector for analysis and storage.
- Vulnerability Assessment: Guardium performs vulnerability assessments by scanning databases and identifying security vulnerabilities and misconfigurations.
How to Install IBM Guardium?
Installing IBM Guardium involves several steps, and the process can vary based on the specific deployment and version. Generally, the installation process includes:
- Preparation: Ensure that you have met the system requirements, have the necessary hardware and software, and have obtained the installation package.
- Installation: Install the Guardium components, including agents, collectors, and the centralized management server, according to the provided instructions.
- Configuration: Configure the Guardium components, including connecting agents to collectors and setting up monitoring policies.
- Integration: Integrate Guardium with existing systems, such as SIEM solutions, to streamline security operations.
- Testing and Validation: Perform testing to ensure that data activities are being captured accurately and that policies are working as expected.
- Ongoing Management: Regularly monitor Guardium’s performance, update configurations, and review security policies.
It’s important to consult the official IBM Guardium documentation for a successful installation and configuration: https://www.ibm.com/support/knowledgecenter/SSEPGG_11.5.0/com.ibm.guardium.doc/welcome.html
Basic Tutorials of IBM Guardium: Getting Started

IBM Guardium is a complex enterprise-grade security solution with various functionalities. While I can provide you with a simplified step-by-step guide to get started with basic concepts of IBM Guardium, keep in mind that the actual implementation might vary based on your environment and specific use cases. Here’s a basic tutorial:
Step 1: Install IBM Guardium
- Prerequisites: Ensure you have the necessary hardware and software requirements as outlined in the IBM Guardium documentation.
- Download Installation Package: Obtain the installation package from IBM’s official website.
- Install Components: Install the necessary Guardium components, such as the Central Manager, collectors, and agents, based on the installation instructions provided by IBM.
Step 2: Configure IBM Guardium
- Access Central Manager: Use a web browser to access the Central Manager’s user interface. This is the primary interface for configuring and managing Guardium.
- Initial Configuration: Follow the provided instructions to configure basic settings like the administrator’s credentials, network settings, and database credentials.
- Connect Collectors: Configure and connect collectors to the Central Manager. Collectors gather data from Guardium agents installed on database servers.
Step 3: Discover and Classify Data
- Discover Sensitive Data: Use Guardium to scan your databases and discover sensitive data. This step helps you understand what types of data you need to protect.
- Data Classification: After discovering data, classify it based on its sensitivity and importance. This classification helps you set up appropriate security policies.
Step 4: Implement Security Policies
- Access Control Policies: Define policies to control who can access sensitive data. Specify rules for different users, roles, and situations.
- Activity Monitoring Policies: Set up policies to monitor and audit user activities within databases. Define rules to capture actions like logins, queries, and modifications.
Step 5: Monitor and Respond to Incidents
- Real-Time Monitoring: Use Guardium to monitor real-time data activities. The system will alert you when suspicious or unauthorized activities are detected.
- Incident Response: When alerts are triggered, investigate the incidents, analyze the cause, and take appropriate actions to mitigate potential threats.
Step 6: Reporting and Compliance
- Generate Reports: Utilize Guardium’s reporting capabilities to generate reports on data access, user activities, policy compliance, and more.
- Compliance Auditing: Guardium helps you meet compliance requirements by providing audit trails and evidence of data protection measures.
Remember that IBM Guardium offers various advanced features, such as data masking, encryption, vulnerability assessment, and integration with SIEM systems. This step-by-step guide covers basic concepts, but implementing IBM Guardium fully requires deeper understanding. Always refer to the official IBM Guardium documentation for detailed instructions and best practices: https://www.ibm.com/support/knowledgecenter/SSEPGG_11.5.0/com.ibm.guardium.doc/welcome.html
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
