What is IBM QRadar?

IBM QRadar is a robust security information and event management (SIEM) solution designed to help organizations detect, investigate, and respond to security threats and incidents. QRadar collects and analyzes data from various sources within an organization’s IT environment to provide comprehensive security intelligence.
IBM QRadar is a powerful SIEM solution used by organizations to enhance their cybersecurity posture, protect sensitive data, and respond effectively to security incidents. Its versatility and extensive feature set make it valuable for security teams across various industries and use cases.
Top 10 use cases of IBM QRadar:
Here are the top 10 use cases of IBM QRadar:
- Threat Detection and Monitoring: QRadar continuously monitors network traffic, system logs, and other data sources to detect suspicious activities and security threats in real-time.
- Incident Response: QRadar provides incident response capabilities, allowing security teams to quickly investigate and respond to security incidents, including breaches, malware outbreaks, and data exfiltration.
- Security Event Correlation: QRadar correlates security events from multiple sources to identify complex attack patterns and prioritize alerts based on the severity and potential impact of the threat.
- User and Entity Behavior Analytics (UEBA): QRadar employs UEBA to analyze user and entity behavior to detect insider threats, compromised accounts, and abnormal activities that may indicate a security breach.
- Log Management and Retention: QRadar collects and centralizes log data from various sources, providing organizations with a comprehensive log management solution for compliance, auditing, and forensic analysis.
- Vulnerability Management Integration: By integrating with vulnerability assessment tools, QRadar can prioritize security vulnerabilities based on their potential impact and exploitability, allowing organizations to focus on critical issues.
- Cloud Security Monitoring: QRadar extends its capabilities to cloud environments, allowing organizations to monitor security events and activities in cloud services, such as AWS and Azure.
- Threat Intelligence Integration: QRadar can ingest threat intelligence feeds and indicators of compromise (IoCs) to enhance its ability to detect and respond to known threats and emerging attack vectors.
- Compliance and Reporting: QRadar provides reporting and dashboards to assist organizations in meeting compliance requirements by demonstrating adherence to security policies and regulations.
- Insider Threat Detection: QRadar helps organizations identify and respond to insider threats, whether they are due to malicious intent, negligence, or compromised accounts.
- Network Flow Analysis: By analyzing network flows and packet data, QRadar can provide visibility into network traffic patterns and identify anomalies that may indicate malicious activities.
- Integration with Security Orchestration and Automation: QRadar can integrate with security orchestration, automation, and response (SOAR) platforms to automate incident response workflows and reduce manual intervention.
What are the feature of IBM QRadar?
IBM QRadar is a comprehensive security information and event management (SIEM) solution that provides a wide range of features and capabilities to help organizations detect and respond to security threats and incidents. Here are the key features of IBM QRadar, along with an overview of how it works and its architecture:
Key Features of IBM QRadar:
- Log and Event Data Collection: QRadar collects and centralizes log and event data from various sources, including network devices, servers, applications, and cloud services.
- Real-Time Threat Detection: QRadar analyzes incoming data in real-time, using predefined rules and behavioral analysis to detect security threats and anomalies.
- Security Event Correlation: QRadar correlates security events and log data from multiple sources to identify complex attack patterns and prioritize security incidents.
- User and Entity Behavior Analytics (UEBA): QRadar employs UEBA to monitor user and entity behavior, helping detect insider threats and compromised accounts.
- Incident Investigation and Forensics: Security analysts can use QRadar to investigate security incidents, conduct forensic analysis, and reconstruct incident timelines.
- Vulnerability Assessment Integration: QRadar integrates with vulnerability assessment tools to prioritize security vulnerabilities based on potential impact and exploitability.
- Threat Intelligence Integration: QRadar can ingest threat intelligence feeds and IoCs to enhance threat detection and response.
- Customizable Dashboards and Reporting: QRadar offers customizable dashboards and reporting capabilities to provide insights into security events and compliance status.
- Compliance Management: QRadar helps organizations meet compliance requirements by providing reporting and auditing capabilities.
- Security Orchestration and Automation: QRadar can integrate with security orchestration and automation platforms (SOAR) to automate incident response workflows.
How IBM QRadar works and Architecture?
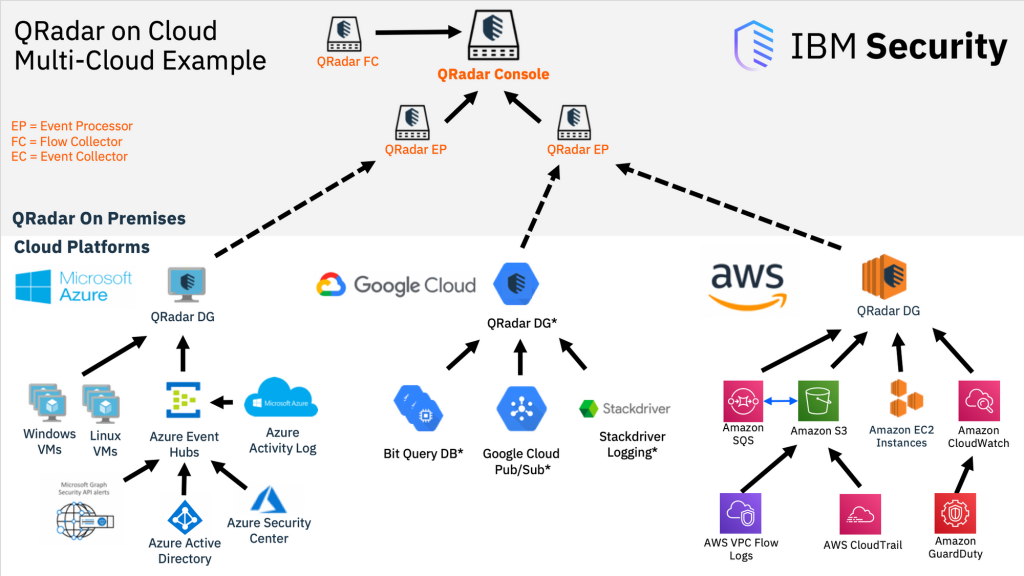
IBM QRadar operates as a SIEM platform that collects, analyzes, and correlates security data to detect and respond to security incidents:
- Data Collection: QRadar collects data from various sources, including logs, events, network flows, and user activities. It supports integration with a wide range of devices and applications.
- Data Normalization: The collected data is normalized to a common format, making it easier to analyze and correlate information from different sources.
- Real-Time Analysis: QRadar’s real-time analysis engine processes incoming data in real-time, applying predefined rules and behavioral analysis to detect security threats.
- Correlation: The correlation engine correlates security events and data to identify patterns and anomalies indicative of security incidents. It assigns risk scores to events to prioritize alerts.
- Alerting and Notification: When QRadar identifies a potential security threat, it generates alerts and notifications for security analysts to investigate.
- Incident Investigation: Security analysts use QRadar’s investigation tools to analyze alerts, investigate incidents, and determine the scope and impact of security events.
- Response and Mitigation: QRadar provides incident response capabilities, enabling security teams to take action to mitigate threats, such as isolating compromised systems or blocking malicious traffic.
QRadar’s architecture is designed for scalability, high availability, and distributed deployment. It consists of the following key components:
- Console: The console is the user interface that security analysts use to interact with QRadar, access dashboards, and investigate security incidents.
- Event Processors: Event processors collect and process event and log data in real-time. They perform initial event correlation and risk scoring.
- Data Nodes: Data nodes store normalized and indexed data for historical analysis and reporting. They support distributed data collection and storage.
- Flow Processors: Flow processors collect, process, and analyze network flow data to detect anomalies and potential threats.
- QRadar SIEM Appliances: QRadar SIEM appliances are available in different sizes and configurations to meet the needs of organizations of various sizes. They can be deployed as managed appliances or virtualized.
- QRadar App Host: The app host supports custom applications and integrations with third-party security tools.
- QRadar Event Collector: Event collectors are responsible for collecting data from various log sources and forwarding it to the event processors.
- QRadar Data Store: The data store stores normalized and indexed data for historical analysis, reporting, and forensic investigations.
QRadar’s distributed architecture allows organizations to scale their SIEM deployment to accommodate their data volume and performance requirements while ensuring high availability and fault tolerance. It plays a critical role in helping organizations detect and respond to security threats effectively.
How to Install IBM QRadar?
To install IBM QRadar, you can follow these steps:
- Prepare the hardware and software prerequisites. This includes installing and configuring a Red Hat Enterprise Linux (RHEL) server, a database server, and a supported version of Java.
- Download the QRadar installation media. You can download the QRadar installation media from the IBM Passport Advantage website.
- Install QRadar. To install QRadar, you can use either the graphical installer or the command-line installer.
- Configure QRadar. After QRadar is installed, you need to configure it. This includes setting up the database connection, configuring the network settings, and creating user accounts.
- Deploy QRadar. To deploy QRadar, you need to start the QRadar services.
A high-level overview of the QRadar installation process:
- Prepare the hardware and software prerequisites:
- Install and configure a supported version of RHEL.
- Install and configure a supported database server.
- Install a favored version of Java.
- Download the QRadar installation media:
- Go to the IBM Passport Advantage website.
- Log in to your account.
- Search for IBM QRadar.
- Download the QRadar installation media.
- Install QRadar:
- Mount the QRadar installation media.
- Run the QRadar installer.
- Configure QRadar:
- Set up the database connection.
- Configure the network settings.
- Create user accounts.
- Deploy QRadar:
- Start the QRadar services.
Once QRadar is installed and deployed, you can start using it to monitor and analyze security events.
Some additional tips for installing QRadar:
- Make sure that you have all of the required prerequisites installed and configured before you start the QRadar installation process.
- Follow the instructions in the IBM QRadar Installation Guide carefully.
- If you are having trouble installing or configuring QRadar, contact IBM support for assistance.
Basic Tutorials of IBM QRadar: Getting Started
The following steps are the Basic Tutorials of IBM QRadar:
Tutorial 1: Logging in to the QRadar Console
- Open a web browser and navigate to the URL of the QRadar Console.
- Enter your username and password.
- Click Login.
Tutorial 2: Viewing and managing offenses
- In the QRadar Console, click Offenses.
- To view a list of all offenses, click All Offenses.
- To view a specific offense, click the name of the offense.
- To manage an offense, such as closing it or assigning it to an analyst, click the Manage button.
Tutorial 3: Creating a new rule
- In the QRadar Console, click Rules.
- Click Create Rule.
- Enter a name and description for the rule.
- Select the type of rule you want to create.
- Configure the rule parameters.
- Click Create.
Tutorial 4: Searching for events
- In the QRadar Console, click Search.
- Enter the search criteria you want to use.
- Click Search.
- To view the results of the search, click the Results tab.
Tutorial 5: Generating reports
- In the QRadar Console, click Reports.
- Select the report you want to generate.
- Configure the report parameters.
- Click Generate.
These are just a few basic tutorials for QRadar.
Some additional tips for using QRadar:
- Use rules to automate the detection and prioritization of security events.
- Use searches to investigate specific security incidents.
- Use reports to track security trends and identify areas for improvement.
- Use the QRadar Console to monitor the security of your network in real time.
By following these tips, you can help to protect your organization from cyberattacks.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
