What is IBM Security Identity and Access Manager?

IBM Security Identity and Access Manager (ISAM) is a comprehensive identity and access management (IAM) solution designed to help organizations secure user identities, control access to resources, and ensure compliance with security policies and regulations. ISAM provides a wide range of features and capabilities to address various IAM needs. Another critical aspect of IAM is the selection of robust SSO providers. A well-chosen SSO provider can significantly enhance security and streamline user access across different applications. For an in-depth comparison of SSO providers you must consider, it’s essential to look at their features, pros, cons, and pricing.
IBM Security Identity and Access Manager is a versatile IAM solution that can be tailored to the specific needs of organizations in various industries. It helps organizations improve security, streamline access controls, and ensure compliance with regulatory requirements.
Top 10 use cases of IBM Security Identity and Access Manager:
Here are the top 10 use cases of IBM Security Identity and Access Manager:
- Single Sign-On (SSO): Implement SSO to allow users to access multiple applications and services with a single set of credentials, enhancing user experience and reducing password fatigue.
- Identity Federation: Federate identities from external identity providers (IdPs) using industry-standard protocols like SAML and OAuth, enabling secure SSO and collaboration with partners and external organizations.
- Web Access Management (WAM): Control user access to web applications and resources through centralized access policies, ensuring secure and compliant access.
- Multi-Factor Authentication (MFA): Enhance security by requiring users to provide multiple authentication factors, such as something they know, something they have, or something they are, during login.
- User Self-Service: Empower users to perform self-service tasks such as password resets, account unlocks, and profile updates, reducing the workload on IT support.
- Access Request and Approval: Implement workflows for access request and approval, ensuring that users obtain the necessary access rights based on predefined policies.
- Privileged Access Management (PAM): Manage and secure privileged accounts, enforcing controls and auditing privileged user activities to prevent unauthorized access.
- Identity Governance and Administration (IGA): Automate identity lifecycle management, including user provisioning, de-provisioning, and access certification, to ensure compliance with security policies and regulatory requirements.
- Adaptive Access Control: Utilize risk-based access controls to assess user behavior and context, granting or denying access based on risk factors and policy conditions.
- API Security: Secure APIs and microservices by enforcing authentication, authorization, and access policies to protect sensitive data and resources.
- Cloud Identity Management: Extend identity and access management capabilities to cloud-based applications and services to maintain consistent security policies across hybrid environments.
- IoT Device Identity Management: Manage and secure identities for Internet of Things (IoT) devices, ensuring that only authorized devices can access resources and services.
What are the feature of IBM Security Identity and Access Manager?
IBM Security Identity and Access Manager (ISAM) is a robust identity and access management (IAM) solution that provides a wide range of features and capabilities to help organizations secure their digital identities and control access to resources. Here are the key features of ISAM, along with an overview of how it works and its architecture:
Key Features of IBM Security Identity and Access Manager:
- Single Sign-On (SSO): Enable users to access multiple applications and services with a single set of credentials, improving user experience and reducing password-related issues.
- Identity Federation: Federate identities from external identity providers (IdPs) using protocols like SAML and OAuth, allowing for secure SSO and collaboration with partners and external organizations.
- Web Access Management (WAM): Control user access to web applications and resources through centralized access policies, ensuring secure and compliant access.
- Multi-Factor Authentication (MFA): Strengthen security by requiring users to provide multiple authentication factors during login, such as something they know, something they have, or something they are.
- User Self-Service: Empower users to perform self-service tasks, including password resets, account unlocks, and profile updates, reducing the burden on IT support.
- Access Request and Approval: Implement workflows for access request and approval, ensuring that users obtain the necessary access rights based on predefined policies.
- Privileged Access Management (PAM): Manage and secure privileged accounts, enforce controls, and audit privileged user activities to prevent unauthorized access.
- Identity Governance and Administration (IGA): Automate identity lifecycle management, including user provisioning, de-provisioning, and access certification, to ensure compliance with security policies and regulatory requirements.
- Adaptive Access Control: Utilize risk-based access controls to assess user behavior and context, granting or denying access based on risk factors and policy conditions.
- API Security: Secure APIs and microservices by enforcing authentication, authorization, and access policies to protect sensitive data and resources.
How IBM Security Identity and Access Manager works and Architecture?
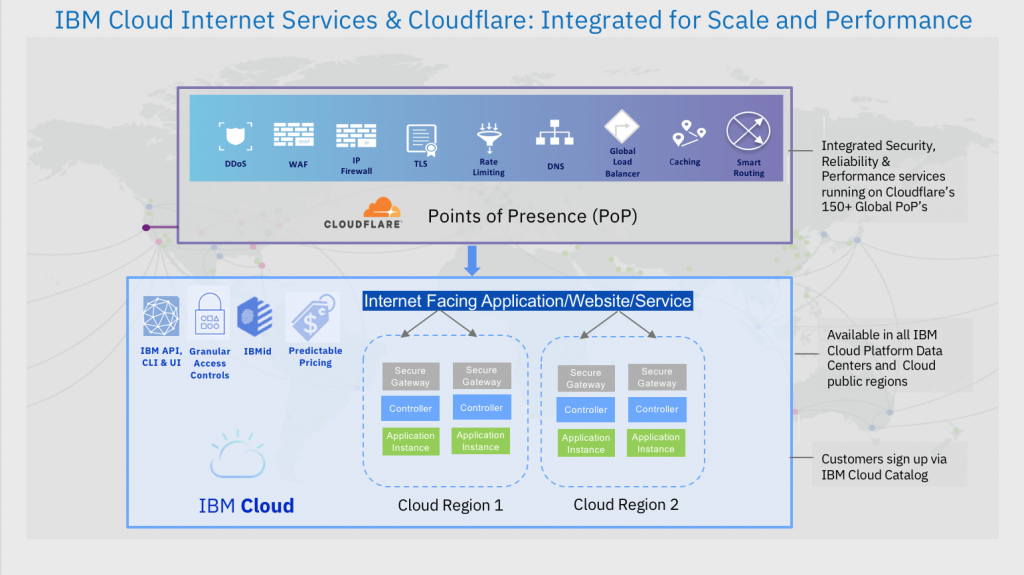
IBM Security Identity and Access Manager operates as a comprehensive IAM solution, providing security and access control for organizations. It’s an overview of how it works:
- Authentication: Users access the ISAM platform and initiate the authentication process by providing their credentials (username and password) or through other authentication methods, including MFA.
- Authorization and Access Control: ISAM evaluates user access requests against access policies and authorization rules to determine whether access should be granted or denied. This includes enforcing SSO and federation.
- User Self-Service: Users can perform self-service tasks, such as password resets or access requests, through ISAM’s self-service portal, reducing IT support overhead.
- Access Management: ISAM provides access management features for web applications, enforcing access controls and ensuring secure access to resources.
- Session Management: ISAM can manage user sessions, including SSO sessions, to monitor and control user activities during their session.
- API Security: ISAM can secure APIs and microservices by enforcing authentication and authorization policies, protecting sensitive data and resources.
ISAM’s architecture is designed for scalability, flexibility, and security. It typically comprises the following components:
- Web Gateway: The web gateway acts as the front-end component responsible for handling user requests, authentication, and access control.
- Reverse Proxy: The reverse proxy component helps secure and control access to web applications and resources.
- Policy Server: The policy server enforces access policies, authentication, and authorization rules based on user requests and policy definitions.
- Federation Server: The federation server handles identity federation, allowing for secure SSO with external identity providers.
- Authentication Mechanisms: ISAM supports various authentication mechanisms, including username/password, MFA, and integration with third-party authentication providers.
- Directory Services Integration: ISAM can integrate with directory services like LDAP and Active Directory to manage user identities.
- API Gateway: For API security, ISAM can include an API gateway component to enforce API authentication and authorization.
- Management Console: The management console provides a user-friendly interface for administrators to configure and manage ISAM components, policies, and user access.
ISAM’s architecture can be tailored to meet the specific requirements and deployment scenarios of organizations, making it suitable for a wide range of IAM needs in various industries. It helps organizations improve security, streamline access management, and ensure compliance with security policies and regulatory requirements.
How to Install IBM Security Identity and Access Manager?
To install IBM Security Identity and Access Manager (ISIM), you will need to:
- Prepare the prerequisite software. This includes installing and configuring a database server, directory server, and WebSphere Application Server.
- Install ISIM. You can download the ISIM installation media from the IBM Passport Advantage website.
- Configure ISIM. This involves creating a database schema, configuring the directory server, and configuring WebSphere Application Server.
- Deploy ISIM. This involves deploying the ISIM web application to WebSphere Application Server and starting the ISIM services.
Let’s have a look t a high-level overview of the ISIM installation process:
- Prepare the prerequisite software:
- Install and configure a supported database server.
- Install and configure a supported directory server.
- Install and configure a favored version of WebSphere Application Server.
- Install ISIM:
- Download the ISIM installation media from the IBM Passport Advantage website.
- Mount the ISIM installation media.
- Run the ISIM installer.
- Configure ISIM:
- Create a database schema for ISIM.
- Configure the directory server to work with ISIM.
- Configure WebSphere Application Server to deploy the ISIM web application.
- Deploy ISIM:
- Deploy the ISIM web application to WebSphere Application Server.
- Start the ISIM services.
Once ISIM is installed and deployed, you can start using it to manage user identities and access permissions.
Some additional tips for installing ISIM:
- Make sure that you have all of the required prerequisites installed and configured before you start the ISIM installation process.
- Follow the instructions in the IBM Security Identity and Access Manager Installation Guide carefully.
- If you are having trouble installing or configuring ISIM, contact IBM support for assistance.
Basic Tutorials of IBM Security Identity and Access Manager: Getting Started

The following steps are the Basic Tutorials of IBM Security Identity and Access Manager (ISIM):
Tutorial 1: Logging in to the ISIM console
- Open a web browser and navigate to the URL of the ISIM console.
- Enter your username and password.
- Click Login.
Tutorial 2: Creating a new user
- In the ISIM console, click Users and Groups.
- Click Create User.
- Enter the required information, such as the user’s name, email address, and password.
- Click Create.
Tutorial 3: Adding a user to a group
- In the ISIM console, click Users and Groups.
- Click the name of the group you want to add the user to.
- Click the Add Users button.
- Choose the user you want to add to the group and click Add.
- Click OK.
Tutorial 4: Creating a new role
- In the ISIM console, click Roles and Policies.
- Click Create Role.
- Type your name and description for the role.
- Click the Permissions tab.
- Select the permissions you want to grant to the role and click Add.
- Click OK.
Tutorial 5: Assigning a role to a user
- In the ISIM console, click Users and Groups.
- Click the name of the user you want to assign the role to.
- Click the Roles tab.
- Choose the role you want to assign to the user and press Add.
- Click OK.
These are just a few basic tutorials for ISIM.
Some additional tips for using ISIM:
- Use strong passwords for your ISIM accounts.
- Enable multi-factor authentication for your ISIM accounts.
- Use ISIM to manage all of your user identities and access permissions, including passwords, roles, and groups.
- Use ISIM policies to control who can access resources and what actions they can perform.
- Implement a regular password rotation schedule for all users.
By following these tips, you can help to protect your organization from unauthorized access to resources.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
