What is Identity?
Identity, in the context of information technology and security, refers to the unique characteristics, attributes, or credentials that are used to identify and verify individuals, devices, or entities accessing digital systems, applications, and resources. Identity management involves the process of establishing, verifying, and maintaining digital identities to control access to data and services securely.
Identity management is a critical component of cybersecurity and plays a fundamental role in protecting digital assets and data while enabling secure and convenient access for users across various use cases and industries.
Top 10 use cases of Identity:
Here are the top 10 use cases of identity management:
- User Authentication: Verifying the identity of users who log in to applications or systems, typically through the use of usernames and passwords, biometrics, or multi-factor authentication (MFA).
- Access Control: Managing and enforcing access policies to ensure that users have appropriate permissions to access specific resources and data, preventing unauthorized access.
- Single Sign-On (SSO): Allowing users to access multiple applications and services with a single set of credentials, reducing the need for multiple logins and enhancing user productivity.
- Multi-Factor Authentication (MFA): Adding an extra layer of security by requiring users to provide multiple forms of verification (e.g., something they know, something they have, something they are) during login.
- Identity Federation: Enabling users to use their existing credentials from one trusted identity provider to access resources and services from other organizations, simplifying user access across multiple domains.
- User Provisioning and De-Provisioning: Automating the process of creating, modifying, and deactivating user accounts and access rights throughout the user’s lifecycle.
- Customer Identity and Access Management (CIAM): Managing customer identities and providing secure access to digital services, improving user experiences while maintaining security.
- Identity Governance and Compliance: Enforcing security policies, access controls, and auditing to ensure that user access is in compliance with regulatory requirements and organizational policies.
- API Security: Securing application programming interfaces (APIs) and controlling access to APIs to protect data and services, particularly in microservices and modern application architectures.
- Behavioral Analysis and Threat Detection: Analyzing user behavior and access patterns to detect suspicious activities and potential security threats, enhancing security posture.
- Identity Analytics: Using data analytics to gain insights into user behavior, access patterns, and compliance, helping organizations make informed decisions about access management and security.
- Password Management: Implementing password policies, including password complexity requirements, password reset processes, and self-service password reset options.
- Identity as a Service (IDaaS): Leveraging cloud-based identity management solutions to provide identity and access management capabilities without the need for on-premises infrastructure.
- Guest Access Control: Managing access for external users, partners, vendors, and guests, ensuring they meet security and compliance requirements before granting access.
- Zero Trust Security: Implementing the Zero Trust security model, which assumes that no entity, whether inside or outside the network, should be trusted by default. Identity plays a central role in verifying trustworthiness.
What are the feature of Identity?
Identity management solutions, often referred to as Identity and Access Management (IAM), offer a range of features and capabilities to manage and secure user identities and access to digital resources. These features help organizations control who can access what, under what circumstances, and with what level of privilege. Here are some key features of identity management and an overview of how identity management works and its typical architecture:
Key Features of Identity Management:
- User Authentication: Verify the identity of users through various authentication methods, including passwords, biometrics, smart cards, or multi-factor authentication (MFA).
- Single Sign-On (SSO): Allow users to log in once and access multiple applications without the need to re-enter credentials for each one.
- User Provisioning and De-Provisioning: Automate the process of creating, modifying, and disabling user accounts and access permissions based on predefined policies.
- Access Control: Define and enforce access policies to ensure users have appropriate permissions to access specific resources, systems, or applications.
- Identity Federation: Enable users to use their credentials from trusted identity providers to access resources in multiple domains without the need for separate accounts.
- Multi-Factor Authentication (MFA): Require users to provide multiple forms of authentication, such as a password and a one-time code, to enhance security.
- Password Management: Implement password policies, including complexity requirements, self-service password reset, and password expiration rules.
- Role-Based Access Control (RBAC): Assign users to roles and grant access permissions based on their roles and responsibilities within the organization.
- Identity Governance: Enforce compliance with access policies, regulatory requirements, and auditing by monitoring and managing access rights.
- Behavioral Analysis and Threat Detection: Analyze user behavior and access patterns to detect and respond to suspicious activities and potential security threats.
- Identity Analytics: Use data analytics to gain insights into user behavior, access patterns, and compliance, helping organizations make informed decisions about access management and security.
How Identity works and Architecture?
- User Registration: Users create or are assigned digital identities within the identity management system. This typically involves providing personal information and setting up authentication credentials.
- Authentication: When users attempt to access a resource, they are prompted to authenticate themselves. This process involves verifying their identity using one or more authentication factors.
- Authorization: Once authenticated, users’ access requests are checked against access control policies to determine if they have the necessary permissions to access the resource.
- Access Control: Access control mechanisms enforce policies based on user attributes, roles, and resource attributes. Users are either granted access or denied access based on these policies.
- Audit and Compliance: Identity management systems log access events, authentication attempts, and user actions for auditing purposes. Compliance requirements are met through these logs.
- Provisioning and De-Provisioning: User accounts and access rights are managed throughout their lifecycle. Accounts are created, modified, or deactivated as needed, often through automated processes.
- SSO and Federation: Single Sign-On allows users to authenticate once and access multiple applications. Identity federation enables users to access resources in external domains using their home organization’s credentials.
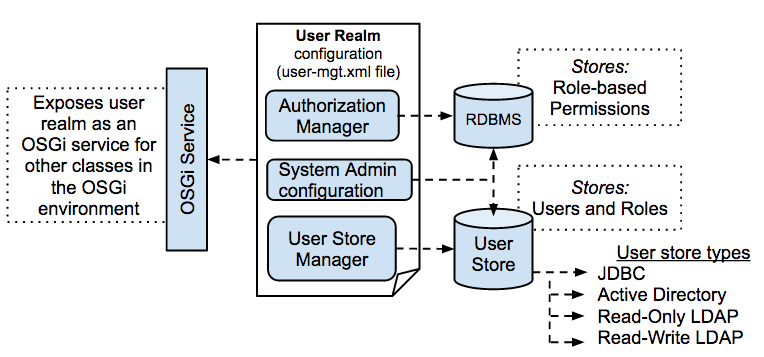
Identity management systems typically consist of the following components:
- User Store: A repository where user identity data is stored. This may include directories, databases, or cloud-based repositories.
- Authentication Service: Responsible for verifying user identities through authentication methods like passwords, tokens, biometrics, or MFA.
- Authorization and Access Control: Determines what resources users can access and with what permissions. This includes role-based access control (RBAC) and access policies.
- Identity Federation: Provides the capability to federate identities with external identity providers and ensure secure access across domains.
- User Provisioning and De-Provisioning: Automates user account creation, modification, and deletion based on defined policies.
- SSO and Federation Services: Enables single sign-on and identity federation across various applications and services.
- Audit and Compliance Management: Logs and monitors user activities and access events for auditing and compliance reporting.
- APIs and Integrations: Provides interfaces and connectors to integrate with applications, directories, and other systems.
- Identity Analytics and Threat Detection: Analyzes user behavior and access patterns to detect anomalies and security threats.
- User Self-Service Portals: Allows users to manage their own identities, passwords, and access preferences.
Identity management architecture can be implemented on-premises, in the cloud, or in hybrid configurations, depending on an organization’s needs and preferences. It is a critical component of modern cybersecurity, ensuring that only authorized users gain access to digital resources while protecting sensitive data and maintaining regulatory compliance.
How to Install Identity?
There are two main ways to install identity:
- Use an identity management solution. Identity management solutions provide a comprehensive set of tools and features for managing user identities and access permissions. Some popular identity management solutions include:
- Active Directory
- Okta
- Azure Active Directory
- Ping Identity
- Implement identity management yourself. This is a more complex option, but it gives you more control over your identity management system. To implement identity management yourself, you will need to set up a database to store user information, develop a web application or API to allow users to manage their accounts, and implement security measures to protect user data.
Some general steps for installing identity yourself:
- Set up a database. You can use any database to store user information, but some popular choices include MySQL, PostgreSQL, and MongoDB.
- Develop a web application or API. This will allow users to manage their accounts, such as creating new accounts, changing passwords, and resetting forgotten passwords.
- Implement security measures. This includes measures to protect user data from unauthorized access, such as encryption and password hashing.
- Configure your applications to use your identity management system. This will involve configuring your applications to authenticate users against your identity management system and to authorize users to access resources.
Once you have installed identity, you will need to manage user accounts and permissions. This includes adding new users, deleting users, and assigning users to groups and roles.
It is important to note that identity management is a complex topic and there is no one-size-fits-all solution. The best approach for you will depend on your specific needs and requirements.
If you are unsure how to install identity, or if you need help managing your identity management system, you should consult with an expert.
Basic Tutorials of Identity: Getting Started

The following are the steps of Basic Tutorials of Identity:
Step 1: Understand the different types of identity.
There are many different types of identity, including:
- Personal identity: This includes your name, date of birth, address, and other information that is unique to you.
- Digital identity: This is your identity in the digital world, such as your email address, social media accounts, and online banking accounts.
- Professional identity: This is your identity in the workplace, such as your job title, company name, and education.
- Social identity: This is your identity in relation to other people and groups, such as your family, friends, and community.
Step 2: Identify your unique identity.
What makes you unique? What are your values, beliefs, and interests? What are your skills and talents? What are your goals and aspirations?
Once you have a good understanding of your unique identity, you can start to build a strong sense of self-worth and confidence.
Step 3: Protect your identity.
It is important to protect your identity from unauthorized access and use. This includes keeping your personal information safe, using strong passwords, and being careful about what information you share online.
You should also be aware of the different types of identity theft and how to protect yourself from them.
Step 4: Manage your identity.
Your identity is not static. It changes over time as you grow and learn. It is important to manage your identity and make sure that it is accurate and up-to-date.
This includes updating your personal information as needed, such as when you change your address or phone number. You should also review your social media accounts and other online accounts regularly to make sure that the information displayed is accurate and that you are comfortable with it being shared online.
Step 5: Use your identity to make a difference.
Your identity is a powerful tool. You can use it to make a difference in the world by advocating for causes you care about, volunteering your time and talents, and helping others.
You can also use your identity to build relationships with others and to create a positive impact on your community.
Additional tips:
- Be mindful of how you present yourself online and in person.
- Be authentic and true to yourself.
- Be respectful of others and their identities.
- Be open to learning and growing.
Your identity is a unique and valuable gift. By understanding and managing your identity, you can live a more fulfilling and meaningful life.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
