What is Kali Linux?

Kali Linux is an open-source project that is constantly developed and maintained by a passionate community of cybersecurity experts and enthusiasts. It is developed and maintained by Offensive Security, a leading organization in the field of cybersecurity training and certification. Kali Linux is based on Debian and comes preloaded with a wide range of security tools and utilities, making it a popular choice among cybersecurity professionals and enthusiasts.
Unauthorized or malicious use of these tools can have legal consequences. Users should always obtain proper authorization and adhere to ethical standards when using Kali Linux or any other cybersecurity tools.
Top 10 use cases of Kali Linux
Here are the top 10 use cases for Kali Linux:
- Penetration Testing: Kali Linux is primarily used for penetration testing and ethical hacking. Security professionals and ethical hackers use it to assess the vulnerabilities and weaknesses of systems, networks, and applications to improve their security.
- Vulnerability Assessment: Kali includes tools for scanning and identifying vulnerabilities in target systems. Security experts can use these tools to discover and mitigate security flaws in their networks.
- Wireless Network Assessment: Kali Linux provides tools for auditing and securing wireless networks. Professionals can use it to assess the security of Wi-Fi networks, test for weaknesses, and recommend improvements.
- Forensics and Incident Response: Kali Linux offers a suite of digital forensics tools for investigating and analyzing security incidents, data breaches, and cybercrime. It helps experts collect evidence and analyze system artifacts.
- Malware Analysis: Security researchers and analysts use Kali Linux to dissect and analyze malicious software. It includes tools for reverse engineering, sandboxing, and examining malware samples.
- Web Application Testing: Kali Linux contains numerous tools for testing and securing web applications. Professionals can perform vulnerability assessments, SQL injection tests, and cross-site scripting (XSS) checks, among other things.
- Password Cracking and Recovery: Ethical hackers use Kali Linux to test the strength of passwords by attempting to crack them. It includes tools for password recovery and hash analysis.
- Security Awareness and Training: Kali Linux is also used for cybersecurity education and training. Many cybersecurity courses and certifications, such as Certified Ethical Hacker (CEH) and Offensive Security Certified Professional (OSCP), use Kali Linux as a platform for hands-on training.
- Network Monitoring and Analysis: Security professionals can use Kali Linux to monitor network traffic, analyze packet captures, and detect anomalies or suspicious activity on the network.
- Custom Tool Development: Kali Linux is highly customizable, allowing users to create and integrate their own security tools and scripts. This flexibility is valuable for tailoring the environment to specific testing or assessment needs.
It’s important to note that Kali Linux is intended for legal and ethical purposes, such as cybersecurity research, penetration testing, and education.
What are the feature of Kali Linux?
Kali Linux is a specialized Linux distribution with a focus on cybersecurity and penetration testing. It provides a wide range of features and tools designed to support various security-related tasks. Here are some of the key features of Kali Linux:
- Vast Collection of Tools: Kali Linux includes over 600 pre-installed penetration testing tools, making it one of the most comprehensive and versatile Linux distributions for cybersecurity professionals.
- Customizable: Kali Linux is highly customizable, allowing users to add or remove tools and packages to tailor the distribution to their specific needs.
- Debian-Based: It is based on the Debian Linux distribution, providing a stable and well-established foundation.
- Rolling Release: Kali Linux follows a rolling release model, which means that updates and new features are continuously integrated into the distribution. Users don’t need to reinstall the entire OS to stay up-to-date.
- Access to Exploits: Kali Linux provides access to a vast database of known vulnerabilities and exploits, which can be used responsibly for security testing and research.
- Live Boot Option: Kali Linux can be run as a live distribution from a USB drive or DVD, allowing users to use it on any system without installing it.
- Full Disk Encryption: It offers the option to encrypt the entire disk during installation, ensuring the security of sensitive data and tools.
- Multiple Desktop Environments: Users can choose between different desktop environments, including GNOME, KDE, Xfce, and more, to suit their preferences.
- Community and Professional Support: Kali Linux has a dedicated community of users and professional support from Offensive Security, the organization behind Kali Linux. This support includes training and certifications.
- Security and Privacy Features: Kali Linux includes various security and privacy features, such as a hardened kernel, anonymous browsing tools, and secure networking utilities.
How Kali Linux works and Architecture?
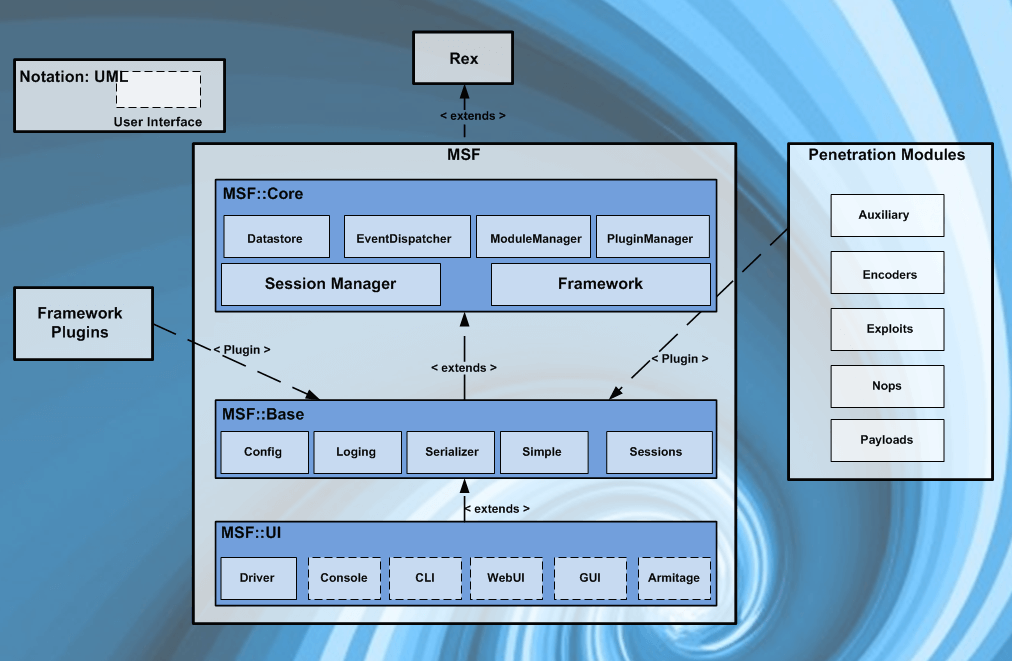
Kali Linux’s architecture is similar to that of other Linux distributions, as it is based on Debian. Here’s a simplified overview of how Kali Linux works:
- Package Management: Kali Linux uses the Debian package management system, allowing users to install, update, and manage software packages easily using package managers like
aptanddpkg. - Kernel: Kali Linux uses a customized Linux kernel with added security features and support for various hardware and networking devices.
- Tools and Utilities: The primary focus of Kali Linux is its vast collection of security tools and utilities. These tools are organized into categories such as Information Gathering, Vulnerability Analysis, Web Application Analysis, and more.
- User Interface: Kali Linux offers a choice of desktop environments, enabling users to interact with the OS and tools using a graphical user interface (GUI).
- Live Mode: Users can boot Kali Linux in live mode from a removable medium (USB drive or DVD) without installing it on the system. This is useful for quick security assessments.
- Persistence: Kali Linux can be configured for persistent storage on a USB drive, allowing users to save their work and tool configurations across sessions.
- Security Measures: Kali Linux incorporates various security measures, including full disk encryption during installation, ensuring the privacy and security of sensitive data.
Overall, Kali Linux is a versatile and powerful Linux distribution specifically tailored for cybersecurity professionals, penetration testers, and ethical hackers, providing the necessary tools and features to perform security assessments and research.
How to Install Kali Linux?
To install Kali Linux, you will require to:
- Download the Kali Linux ISO image from the Kali Linux website.
- Create a bootable USB drive or DVD from the ISO image.
- Boot a computer from the bootable DVD or USB drive.
- Follow the on-screen instructions to install Kali Linux.
To create a bootable USB drive:
- Download and install Rufus, a free and open-source USB creation tool.
- Launch Rufus and select the Kali Linux ISO image.
- Select the USB drive that you want to make bootable.
- Click the “Start” button and wait for Rufus to finish creating the bootable USB drive.
To boot your computer from the bootable USB drive or DVD:
- Insert the bootable USB drive or DVD into your computer.
- Again, start your computer and press the key that opens the boot menu (this key varies depending on your computer manufacturer).
- Choose the bootable USB drive or DVD from the boot menu.
To install Kali Linux:
- Follow the on-screen instructions to install Kali Linux.
- Choose the appropriate installation type for your needs.
- Create a user account and set a password.
- Wait for the installation to complete.
Once the installation is complete, you will be able to log in to Kali Linux and start using it.
Some additional tips for installing Kali Linux:
- Make sure that your computer meets the minimum system requirements for Kali Linux.
- Back up all of your important data before installing Kali Linux.
- If you are dual-booting Kali Linux with another operating system, make sure that you create a separate partition for Kali Linux.
- Be careful when installing Kali Linux on a laptop, as the installation process may disable some of the laptop’s features, such as the Wi-Fi card.
Once you have installed Kali Linux, you can start learning how to use it for penetration testing and security research. There are many resources available online to help you get started, such as the official Kali Linux documentation and tutorials.
Basic Tutorials of Kali Linux: Getting Started

Some step-by-step basic tutorials of Kali Linux:
1. Getting started with the terminal:
The terminal is the primary interface for interacting with Kali Linux. To open a terminal window, press Ctrl+T.
2. Basic Linux commands:
There are many basic Linux commands that you should learn, such as cd, ls, pwd, and mkdir. You can learn more about Linux commands by typing man <command name> in the terminal.
3. Exploring the Kali Linux tools:
Kali Linux comes with a wide range of tools for penetration testing and security research. You can explore the Kali Linux tools by typing apt list --installed in the terminal.
4. How to use the Metasploit Framework:
The Metasploit Framework is a powerful tool for exploiting vulnerabilities and gaining access to target systems. You can learn more about the Metasploit Framework by typing msfconsole in the terminal and then typing help.
5. How to use Nmap:
Nmap is a network scanner that can be used to discover hosts and services on a network. You can learn more about Nmap by typing nmap --help in the terminal.
6. How to use Wireshark:
Wireshark is a network traffic analyzer that can be used to capture and analyze network traffic. You can learn more about Wireshark by typing wireshark in the terminal.
Step-by-step tutorial for using the Metasploit Framework to exploit a vulnerability in a target system:
- Start the Metasploit console by typing
msfconsolein the terminal. - Search for an exploit for the vulnerability that you want to exploit by typing
search <vulnerability name>. - Load the exploit by typing
use <exploit name>. - Set the options for the exploit by typing
set <option name> <option value>. - Run the exploit by typing
run.
Step-by-step tutorial for using Nmap to scan a network for open ports and services:
- Start Nmap by typing
nmap <network address>in the terminal. - To scan a specific port, type
nmap -p <port number> <network address>. - To scan for specific services, type
nmap -sV <network address>.
Step-by-step tutorial for using Wireshark to capture and analyze network traffic:
- Start Wireshark by typing
wiresharkin the terminal. - Select the network interface that you want to capture traffic on from the list of interfaces.
- Click the “Start” button to start capturing traffic.
- To stop capturing traffic, click the “Stop” button.
- To analyze the captured traffic, double-click on a packet in the list of packets.
These are just a few basic tutorials of Kali Linux. There are many other tutorials and resources available online to help you learn more about Kali Linux and how to use it for penetration testing and security research.
Some additional tips for using Kali Linux:
- Be careful when using Kali Linux, as it contains many tools that can be used to exploit vulnerabilities and gain unauthorized access to systems.
- Only use Kali Linux on networks that you are authorized to access.
- Be sure to keep Kali Linux up to date with the latest security patches.
- If you are new to Linux, it is a good idea to learn about basic Linux commands and concepts before using Kali Linux.
Kali Linux is a powerful tool that can be used for a variety of purposes. By following these basic tutorials and tips, you can start learning how to use Kali Linux for penetration testing and security research.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
