What is McAfee MVISION ePO?

MVISION ePO is a comprehensive security management platform that offers:
- Endpoint Security Management: Deploy, manage, and update McAfee endpoint security solutions across your network.
- Endpoint Threat Detection and Response (EDR): Continuously monitor endpoints for suspicious activity and respond to threats proactively.
- Vulnerability Management: Identify and prioritize vulnerabilities across your environment and patch them before attackers exploit them.
- Security Information and Event Management (SIEM): Aggregate and analyze log data from various sources to gain insights into potential security threats and compliance violations.
- Security Orchestration and Automation: Automate routine security tasks and workflows to improve efficiency and effectiveness.
Top 10 use cases of McAfee MVISION ePO?
Top 10 Use Cases of McAfee MVISION ePO:
- Centralized Endpoint Security Management: Efficiently manage all your McAfee endpoint security solutions from a single platform.
- Proactive Threat Detection and Response: Identify and respond to threats quickly with real-time monitoring and EDR capabilities.
- Vulnerability Management and Patching: Protect your infrastructure by prioritizing and patching vulnerabilities before attackers exploit them.
- Improved Security Visibility and Insights: Gain comprehensive visibility into your IT environment and potential security risks with centralized log analysis.
- Simplified Compliance Reporting: Streamline compliance reporting for various regulations like PCI-DSS, HIPAA, and SOX.
- Automated Security Workflows: Automate routine tasks like policy enforcement, vulnerability scanning, and incident response to reduce manual effort.
- Enhanced User Activity Monitoring: Track user activity and identify potential insider threats or unauthorized access attempts.
- Incident Investigation and Forensics: Investigate security incidents with historical log data and forensic analysis tools.
- Operational Optimization: Monitor system performance and application health to identify and address issues proactively.
- Threat Intelligence Integration: Feed external threat intelligence data into MVISION ePO for enhanced threat detection capabilities.
Benefits of using McAfee MVISION ePO:
- Improved Security Posture: Proactively identify and mitigate security threats with comprehensive security management capabilities.
- Reduced Costs and Complexity: Manage all your security needs from a single platform, reducing infrastructure and administrative overhead.
- Enhanced Compliance: Streamline compliance reporting and demonstrate compliance effectively.
- Faster Incident Response: Automate processes and respond to threats quickly and efficiently.
- Improved Operational Efficiency: Gain insights into your IT environment and optimize security operations.
What are the feature of McAfee MVISION ePO?
McAfee MVISION ePO boasts a vast array of features, but to personalize my response and focus on the most relevant aspects, could you tell me what areas of the platform you’re most interested in? I can provide detailed explanations for different categories like:
1. Endpoint Security Management:
- Deployment and configuration: Streamline deployment of McAfee endpoint solutions across desktops, servers, and mobile devices.
- Policy management: Create and enforce consistent security policies to protect your endpoints.
- Patch management: Identify and prioritize vulnerabilities, and automate patching across your network.
- Application control: Manage and whitelist/blacklist applications to prevent unauthorized software execution.
- Device control: Enforce restrictions on removable media usage and external device connections.
2. Endpoint Threat Detection and Response (EDR):
- Real-time threat monitoring: Analyze endpoint behavior and activity for suspicious indicators.
- Advanced threat investigation: Investigate potential threats with forensic tools and detailed event analysis.
- Automated incident response: Trigger automated containment and remediation actions against identified threats.
- Endpoint data loss prevention (DLP): Prevent sensitive data from unauthorized transfer or exfiltration.
3. Vulnerability Management:
- Vulnerability scanning: Discover and assess vulnerabilities in your operating systems, applications, and firmware.
- Vulnerability prioritization: Rank vulnerabilities based on severity and exploitability to guide patching efforts.
- Patch deployment and tracking: Automate patch deployment and track compliance across your endpoints.
- Integration with vulnerability feeds: Stay updated on emerging vulnerabilities and threats.
4. Security Information and Event Management (SIEM):
- Log aggregation and analysis: Collect and analyze logs from various sources across your IT infrastructure.
- Threat detection and correlation: Identify potential security incidents by correlating events from different sources.
- Compliance reporting: Generate reports for various compliance regulations.
- Security dashboards and visualizations: Gain visual insights into your security posture and potential threats.
5. Security Orchestration and Automation (SOAR):
- Automate routine security tasks: Automate tasks like vulnerability scanning, patch deployment, and log analysis.
- Integrate with security tools: Connect MVISION ePO with other security solutions for unified workflows.
- Customize workflow automation: Create custom workflows to automate specific security processes.
Beyond these specific categories, MVISION ePO offers numerous additional features like user activity monitoring, mobile device management, network access control, and cloud security capabilities.
How McAfee MVISION ePO works and Architecture?
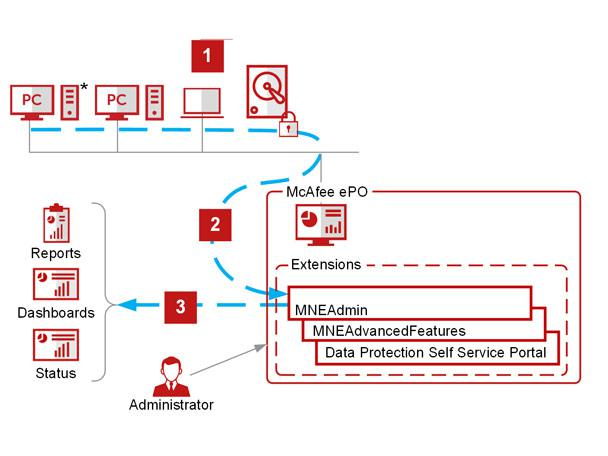
McAfee MVISION ePO functions on a distributed architecture designed for centralized management and scalability. Following is a breakdown of its key components:
1. Management Server:
- Acts as the brain of the operation, hosting the console, databases, and core processing modules.
- Manages tasks like policy distribution, agent communication, data analysis, and reporting.
- Provides a web-based interface for administrators to configure and manage the platform.
2. Agents:
- Installed on endpoints (desktops, servers, mobile devices) and continuously monitor system activity.
- Collect endpoint data like security events, system state, and log data.
- Communicate with the management server for policy updates, commands, and data transfer.
3. Databases:
- Store various types of data like endpoint information, security policies, vulnerabilities, and historical logs.
- Separate databases manage specific data categories for optimized performance and security.
4. Integrators:
- Connect MVISION ePO with other security tools like SIEM, SOAR, and vulnerability scanners.
- Enable automated workflows and exchange of security data for a unified security posture.
5. Cloud Management:
- Optional component allowing you to host the management server and databases in the cloud for increased scalability and flexibility.
Work Flow:
- Agents continuously monitor endpoints and send data to the management server.
- The server analyzes data against security policies and identifies potential threats and vulnerabilities.
- Alerts and reports are generated based on predefined rules and policies.
- Security analysts investigate alerts and take appropriate actions like remediation, patching, or further investigation.
- Dashboards and reports provide insights into security posture, compliance status, and endpoint health.
Benefits of this Architecture:
- Centralized Management: Manage all your security needs from a single platform, simplifying administration and improving efficiency.
- Scalability: Easily add more agents and servers to accommodate larger environments.
- Real-time Visibility: Gain immediate insights into endpoint activity and potential threats.
- Automated Workflows: Automate routine tasks and response actions to save time and resources.
- Integrations: Enhance security by connecting MVISION ePO with other tools for a holistic approach.
- Flexible Deployment: Choose on-premises or cloud deployment based on your needs.
Understanding the architecture behind MVISION ePO empowers you to leverage its functionalities effectively.
How to Install McAfee MVISION ePO it?
Installing McAfee MVISION ePO involves several steps and options depending on your environment and desired deployment method. To guide you efficiently, I need some details:
1. Choose your deployment method:
- On-premises: Traditional installation on your own hardware and infrastructure.
- Cloud: Host the MVISION ePO server and databases in the McAfee cloud for increased scalability and flexibility.
2. Prepare your environment:
- Hardware: Ensure sufficient resources (CPU, RAM, storage) are available for the server and databases.
- Software: Verify compatibility with your operating system and any required pre-installed software.
- Networking: Configure firewall rules and network access for communication between server, agents, and cloud resources (if applicable).
3. Choose your installation type:
- New installation: Fresh installation of MVISION ePO on a new server.
- Upgrade: Upgrade an existing McAfee ePO (5.x) or MVISION ePO server to the latest version.
4. Follow the appropriate installation guide:
- MVISION ePO includes separate guides for on-premises and cloud deployments, new installations, and upgrades.
- Each guide provides detailed instructions for each step of the installation process.
- You’ll configure the server, databases, agents, and security policies.
Note: Before installation, consider consulting with McAfee Support or a qualified IT professional if you need assistance or have specific requirements.
Basic Tutorials of McAfee MVISION ePO: Getting Started

McAfee MVISION ePO, an endpoint protection and policy management platform, offers comprehensive security management capabilities. Here’s are stepwise basic tutorials for McAfee MVISION ePO:
1. Adding Systems to your MVISION ePO environment:
Step 1. Navigate to System Management:
- Open the MVISION ePO console.
- Click on the “Systems” tab in the main navigation bar.
Step 2. Choose Import Method:
- Click on “Import Systems” in the “Systems” menu.
- Choose your preferred method:
- Agent Package: Download and distribute the agent to target systems for automatic registration.
- Manual Entry: Add systems individually by specifying hostname/IP and credentials.
- CSV File: Upload a CSV file containing bulk system information for import.
Step 3. Proceed with chosen method:
- Follow the on-screen instructions for each method:
- Agent Package: Provide distribution instructions and wait for systems to register.
- Manual Entry: Fill in details for each system and press “Import.”
- CSV File: Upload the pre-planned CSV file and map data fields correctly.
Step 4. Verify System Import:
- Expand the relevant group or folder in the “System Tree” panel.
- Right-click a system and select “Show Status” to confirm connection and policy assignment.
- Ensure all systems show “Connected” status for successful communication.
2. Deploying Antivirus Policies:
Step 1. Access Policy Management:
- Click on the “Policies” tab in the main navigation bar.
- Select “Antivirus” from the policy categories.
Step 2. Create a New Policy:
- Click on “New” and provide a descriptive name for your policy.
Step 3. Configure Policy Settings:
- Define scan options like schedule, type (quick, full, custom), and file exclusions.
- Specify actions to take upon malware detection (quarantine, delete, etc.).
- Configure real-time protection behavior and resource usage.
Step 4. Save and Assign the Policy:
- Click “Save” to finalize the policy configuration.
- Go back to the “Systems” tab and select the target group or folder.
- Right-click and choose “Assign Policy.”
Step 5. Select and Apply Policy:
- Choose the newly created antivirus policy from the list.
- Click “Assign” to deploy the policy to the selected systems.
Step 6. Monitor Policy Compliance:
- Navigate back to the “Systems” tab and expand the assigned group/folder.
- Right-click a system and select “Show Status” to view compliance information.
- Verify that systems report “Compliant” status for the assigned antivirus policy.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
