What is Micro Focus Fortify?

Micro Focus Fortify is a comprehensive application security (AppSec) platform that helps organizations identify and remediate vulnerabilities throughout the software development lifecycle (SDLC). It acts as a powerful security shield, offering a diverse range of tools and services to:
- Prevent vulnerabilities: Catch security flaws early in the development process through static and dynamic analysis.
- Protect applications: Monitor applications in real-time and actively defend against cyberattacks and exploits.
- Manage risk: Prioritize vulnerabilities based on severity and exploitability, optimizing remediation efforts.
- Comply with regulations: Demonstrate adherence to industry security standards and data privacy regulations.
Top 10 use cases of Micro Focus Fortify?
Top 10 Use Cases of Micro Focus Fortify:
- Static Application Security Testing (SAST): Analyzes source code for vulnerabilities like SQL injection, cross-site scripting, and insecure coding practices, preventing them from manifesting later.
- Dynamic Application Security Testing (DAST): Simulates real-world attacks on running applications to uncover hidden vulnerabilities in web applications and APIs.
- Interactive Application Security Testing (IAST): Monitors deployed applications for real-time suspicious activity and attack attempts, providing immediate insight into potential threats.
- Runtime Application Self-Protection (RASP): Embeds security controls directly within applications for real-time threat detection and automatic mitigation, acting as an internal security guard.
- Software Composition Analysis (SCA): Identifies and manages security risks within open-source and third-party software dependencies, ensuring your applications are built on a secure foundation.
- Compliance Management: Simplifies compliance with industry regulations like PCI DSS, HIPAA, and GDPR by providing tools and reports that demonstrate your security posture.
- DevSecOps Integration: Seamlessly integrates with development workflows and CI/CD pipelines to weave security testing throughout the SDLC, promoting continuous security practices.
- Vulnerability Management: Provides centralized tracking and prioritization of vulnerabilities, streamlining remediation efforts and ensuring timely fixes.
- Security Education and Training: Equips developers and security teams with the knowledge and best practices to build secure applications and address security challenges effectively.
- Threat Intelligence: Leverages the latest threat intelligence to stay ahead of evolving cyberattacks and prioritize vulnerabilities based on their relevance to current threats.
Micro Focus Fortify offers a comprehensive and adaptable solution for organizations of all sizes to build and maintain secure applications. If you’re looking to:
- Reduce your attack surface
- Minimize security risks
- Build trusted and reliable applications
- Comply with data privacy regulations
Micro Focus Fortify can be a valuable partner in your AppSec journey.
What are the feature of Micro Focus Fortify?
Micro Focus Fortify boasts a diverse and powerful set of features designed to comprehensively address your application security needs across the SDLC. Here’s a closer look at some key highlights:
Vulnerability Detection and Analysis:
- SAST (Static Application Security Testing): Scans source code for vulnerabilities like SQL injection, cross-site scripting, and insecure coding practices, helping prevent them early on.
- DAST (Dynamic Application Security Testing): Simulates real-world attacks on running applications to uncover hidden vulnerabilities in web apps and APIs.
- IAST (Interactive Application Security Testing): Monitors deployed applications for suspicious activity and attack attempts in real-time, providing immediate insights into potential threats.
- RASP (Runtime Application Self-Protection): Embeds security controls within applications for real-time threat detection and automatic mitigation, acting as an internal security guard.
- SCA (Software Composition Analysis): Identifies and manages security risks within open-source and third-party software dependencies, ensuring secure foundations for your applications.
Vulnerability Management and Prioritization:
- Centralized Vulnerability Tracking: Provides a single pane of glass to track all identified vulnerabilities across your applications.
- Vulnerability Prioritization: Analyzes vulnerabilities based on severity, exploitability, and business impact, helping you focus on the most critical issues first.
- Remediation Guidance: Offers clear and actionable steps for fixing vulnerabilities, with detailed reports and resources to empower developers.
DevSecOps Integration and Automation:
- Seamless Integration with Development Tools: Plugs into popular IDEs, CI/CD pipelines, and DevOps workflows, making security testing an integral part of the development process.
- Automated Scanning and Reporting: Schedules automated scans, generates reports, and tracks progress, streamlining security practices and minimizing manual effort.
Compliance and Reporting:
- Compliance Management: Simplifies adherence to industry regulations like PCI DSS, HIPAA, and GDPR by providing tools and reports that demonstrate your security posture.
- Customizable Dashboards and Reports: Create custom dashboards and reports to visualize security data in a way that suits your specific needs and provides stakeholders with clear insights.
Additional Features:
- Threat Intelligence: Leverages the latest threat intelligence to stay ahead of evolving cyberattacks and prioritize vulnerabilities based on their relevance to current threats.
- Security Education and Training: Equips developers and security teams with the knowledge and best practices to build secure applications and address security challenges effectively.
- Scalability and Flexibility: Adapts to diverse application types and development environments, catering to organizations of all sizes.
Micro Focus Fortify offers a potent combination of features to meet your AppSec needs. Whether you’re a developer, security professional, or business leader, Fortify can empower you to build and maintain secure applications with confidence.
How Micro Focus Fortify works and Architecture?
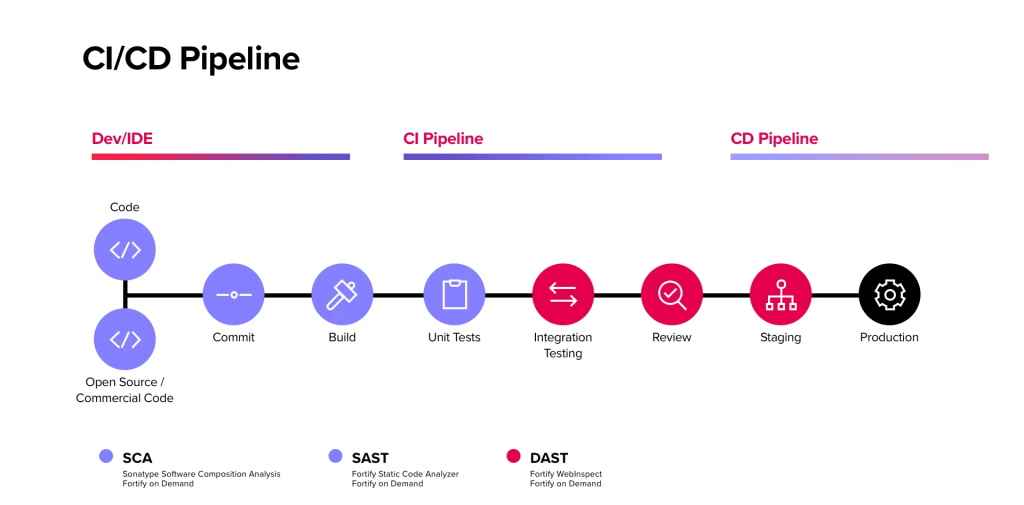
Micro Focus Fortify boasts a complex yet well-designed architecture aimed at providing comprehensive application security across the SDLC. Here’s a breakdown of its key elements and processes:
Components:
- Fortify Platform: The central hub that orchestrates all security analyses, stores data, and manages workflows. It includes:
- Scanners: Engines for different analysis types like SAST, DAST, IAST, and SCA.
- Database: Stores information about applications, vulnerabilities, and analysis results.
- Workflow Engine: Automates tasks like scan scheduling, reporting, and vulnerability tracking.
- User Interface: Provides access to tools, reports, and security insights.
- Integrations: Fortify seamlessly connects with various development tools and platforms like IDEs, CI/CD pipelines, and issue trackers.
- Applications: Organizations upload their software code, web applications, or third-party dependencies for analysis.
- Analysis Tools: Different tools handle specific tasks:
- SAST: Scans source code for vulnerabilities in various programming languages.
- DAST: Simulates attacks against running applications to detect exploitable weaknesses.
- IAST: Monitors application behavior during testing and in deployment to identify suspicious activity.
- RASP: Embeds security controls within applications for real-time threat detection and mitigation.
- SCA: Analyzes dependencies for known vulnerabilities and license compliance issues.
- Vulnerability Management: After analysis, vulnerabilities are identified and classified based on severity and risk. Fortify offers features like:
- Prioritization: Ranking vulnerabilities based on potential impact and exploitability.
- Remediation guidance: Providing developers with clear steps to fix vulnerabilities.
- Tracking and reporting: Monitoring progress towards resolving vulnerabilities.
Architecture Benefits:
- Centralized platform: Streamlines security management and provides a single source of truth for all security data.
- Integrated solution: Seamlessly connects with developer workflows for efficient and continuous security testing.
- Automated processes: Automates scans, reporting, and remediation tasks for faster execution and reduced manual effort.
- Flexibility and scalability: Adapts to various application types and security needs, catering to organizations of all sizes.
- Comprehensive analysis: Combines multiple analysis methods for a holistic view of application security risks.
In essence, Fortify’s architecture empowers organizations to implement a proactive and efficient approach to application security throughout the software lifecycle.
How to Install Micro Focus Fortify it?
Installing Micro Focus Fortify directly isn’t the typical approach, as it’s a cloud-based platform delivered as a service. There are several ways to access and utilize Fortify depending on your specific needs:
1. Free Trial:
- Visit the Veracode official website and click on “Free Trial.”
- This provides you access to a limited range of Fortify features and a trial period to search its capabilities.
- Ideal for beginners or organizations evaluating Fortify for the first time.
2. Subscription Purchase:
- Contact Micro Focus sales or an authorized partner to purchase a subscription plan based on your specific needs.
- Different plans offer varying features, scan limits, and support options.
- This approach is suitable for organizations requiring advanced functionalities and ongoing security assessment.
3. Integration with Veracode Platform:
- If you already use the Veracode platform for other AppSec services, you can integrate Fortify features within the same platform.
- This provides a unified view of all application security assessments and simplifies workflow management.
- You may need to purchase additional Fortify modules or subscriptions depending on the desired features.
4. On-Premise Deployment (Advanced Users):
- In specific cases, Micro Focus offers an on-premise deployment option for organizations with strict security requirements or network limitations.
- This setup requires installing and maintaining Fortify software on your own infrastructure.
- This option is generally recommended for experienced users with dedicated IT resources.
Here are some additional points to consider:
- System Requirements: Ensure your environment meets the minimum system requirements for the chosen access method.
- Integration Configuration: If integrating with other tools, follow the specific instructions provided by Micro Focus.
- User Accounts and Permissions: Create user accounts and assign appropriate permissions within the platform.
- Training and Support: Utilize available training resources and support channels to learn best practices and address any technical challenges.
Remember, the best approach to installing Fortify depends on your specific needs and environment. I recommend exploring the available options and seeking guidance from Micro Focus or its partners to ensure a smooth and successful installation.
Basic Tutorials of Micro Focus Fortify: Getting Started

To craft the most helpful tutorials, let’s explore your preferred area of focus within Micro Focus Fortify:
1. Static Code Analysis (SCA):
- Basic DAST Scan:
- Step 1: Download and install the Fortify Static Code Analyzer (SCA) on your development machine.
- Step 2: Open the SCA and create a new project for your codebase.
- Step 3: Import your source code files (supported languages vary depending on your SCA license).
- Step 4: Run a Quick Scan or choose a specific configuration depending on your needs.
- Step 5: Review the identified vulnerabilities, their severity, and suggested remediation steps.
- Building a Custom Scan Profile:
- Step 1: In the SCA, navigate to “Analysis Profiles” and create a new profile.
- Step 2: Configure the scanning options, including targeted files/folders, rule sets, and severity thresholds.
- Step 3: Save the profile and use it for subsequent scans tailored to your specific needs.
2. Dynamic Application Security Testing (DAST):
- Simulating Real-World Attacks:
- Step 1: Install the Fortify WebInspect Scanner on your machine or deploy it on a server.
- Step 2: Configure your application target (URL, credentials, authentication methods).
- Step 3: Choose a scanning profile or customize settings to focus on specific vulnerabilities.
- Step 4: Run the scan and observe the spidering process as WebInspect crawls your application.
- Step 5: Analyze the identified vulnerabilities, exploit attempts, and recommendations for mitigation.
- Integration with CI/CD Pipeline:
- Step 1: Choose your CI/CD platform (Jenkins, GitLab CI, etc.) and install the Fortify WebInspect plugin.
- Step 2: Configure the plugin to automatically trigger scans at key stages of your pipeline (build, deploy).
- Step 3: Set fail conditions based on critical vulnerability findings to prevent insecure deployments.
- Step 4: Integrate vulnerability reports and remediation progress into your development workflow.
- Step 5: Collaborate and iterate to embed security testing as a core practice within your CI/CD process.
3. Vulnerability Management:
- Prioritizing Vulnerabilities:
- Step 1: Open the Fortify Audit Workbench and navigate to the “Vulnerability Management” section.
- Step 2: Filter vulnerabilities by application, severity, exploitability, and other relevant criteria.
- Step 3: Analyze the CVSS score, exploit details, and potential impact of each vulnerability.
- Step 4: Assign vulnerabilities to development teams and prioritize them based on risk and resource availability.
- Step 5: Track progress towards fixing vulnerabilities with reports and status updates.
- Remediation Workflow:
- Step 1: Select a prioritized vulnerability and review the detailed remediation guidance provided by Fortify.
- Step 2: Collaborate with developers to understand the vulnerable code and identify the root cause.
- Step 3: Implement a secure code fix based on the provided guidance and best practices.
- Step 4: Verify the fix by re-scanning the application or code section to confirm the vulnerability is resolved.
- Step 5: Update the vulnerability status in Fortify Audit Workbench and share documentation for future reference.
Remember, these are just basic tutorials! Feel free to ask any specific questions you have regarding Fortify features, use cases, or configurations. I’m here to guide you through your application security journey with Fortify!
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
