What is Microsoft Threat Modeling Tool?
The Microsoft Threat Modeling Tool (TM2) is a free, downloadable application specifically designed to help developers, architects, and security professionals identify and mitigate potential security threats in their software systems. It’s considered a core element of the Microsoft Security Development Lifecycle (SDL) and empowers users to address security concerns early in the design phase, when they’re easier and cheaper to fix.
Top 10 use cases of Microsoft Threat Modeling Tool?
Here are the top 10 use cases of the Microsoft Threat Modeling Tool:
- Visualize system design and data flows: TM2 uses a standardized notation for drawing diagrams that make complex software architectures clear and understandable. This visualization helps in identifying potential vulnerabilities and attack vectors.
- Identify common threats: TM2 provides guidance and templates for considering various threat categories like spoofing, data tampering, elevation of privilege, and denial-of-service attacks. This prompts users to think about security from a comprehensive perspective.
- Assess likelihood and impact of threats: The tool helps users prioritize threats by estimating their likelihood and potential impact on the system and data. This allows them to focus mitigation efforts on the most critical issues.
- Generate mitigation recommendations: TM2 suggests potential countermeasures for identified threats, based on best practices and security principles. This provides a starting point for implementing security controls within the software.
- Facilitate collaboration and communication: The tool promotes teamwork by allowing multiple users to work on the same threat model and share their insights. This helps developers, architects, and security professionals collaborate effectively on securing the system.
- Document security decisions: TM2 automatically generates reports that document the identified threats, potential mitigations, and rationale behind decisions. This serves as a valuable record for future reference and audits.
- Integrate with development workflows: TM2 can be easily integrated with existing development tools and methodologies, minimizing disruption to existing processes. This encourages security to be considered throughout the software development lifecycle.
- Educate developers on security: The tool provides guided assistance and learning resources, making it easy for non-security experts to understand basic threat modeling concepts and apply them to their projects.
- Complement comprehensive threat modeling: TM2 can be used as a quick and lightweight approach for early design analysis, while more in-depth threat modeling can be conducted later in the development cycle for complex systems.
- Improve development efficiency: By identifying and addressing security concerns early, TM2 helps prevent future costly rework and vulnerabilities. This leads to more secure and reliable software with reduced development time and resources.
Overall, the Microsoft Threat Modeling Tool is a valuable asset for any organization concerned about the security of their software. Its easy-to-use interface, helpful guidance, and practical features make it a powerful tool for identifying and mitigating threats, ultimately leading to more secure and robust software systems.
What are the feature of Microsoft Threat Modeling Tool?
Here are the key features of the Microsoft Threat Modeling Tool (TM2):
1. Visual Modeling:
- Data Flow Diagrams (DFDs): Create visual representations of system components, data flows, and trust boundaries using a standardized notation.
- Threat Trees: Break down complex threats into smaller, more manageable sub-threats to analyze attack paths and potential consequences.
- Visualize mitigations: Link mitigation actions to specific threats on the model to visualize security controls and their effectiveness.
2. Threat Analysis:
- STRIDE Methodology: Systematically identify threats based on six categories: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege.
- Threat Libraries: Utilize built-in libraries of common threats and mitigations for reference and guidance.
- Threat Highlighting: Visually highlight threats on the model to focus attention on areas of concern.
3. Mitigation Management:
- Suggested Mitigations: Receive recommendations for potential mitigations based on identified threats and best practices.
- Custom Mitigations: Add and manage custom mitigation actions to tailor security controls to specific needs.
- Threat-Mitigation Mapping: Track the relationship between threats and mitigations to ensure comprehensive coverage.
4. Collaboration and Communication:
- Multi-user Support: Allow multiple users to work on the same model simultaneously for enhanced collaboration.
- Comments and Notes: Add comments and notes to model elements for documentation and discussion.
- Threat Report Generation: Export detailed reports in HTML format to share threat analysis results with stakeholders.
5. Integration and Usability:
- Integration with Microsoft SDL: Seamlessly integrates with the Microsoft Security Development Lifecycle (SDL) for a holistic approach to security.
- Visual Studio Integration: Open and save threat models directly within Visual Studio for a seamless development experience.
- User-Friendly Interface: Features a user-friendly interface with drag-and-drop functionality and intuitive navigation.
- Contextual Help: Provides guidance and tutorials within the tool to assist users with understanding threat modeling concepts.
6. Additional Features:
- Threat Modeling Templates: Access predefined templates for common system architectures to accelerate model creation.
- Data Flow Validation: Validate data flow diagrams to ensure consistency and accuracy.
- Threat Tracking and Prioritization: Track threat status and prioritize mitigation efforts based on risk assessments.
- Search Functionality: Quickly find specific elements within complex models for efficient analysis.
How Microsoft Threat Modeling Tool works and Architecture?
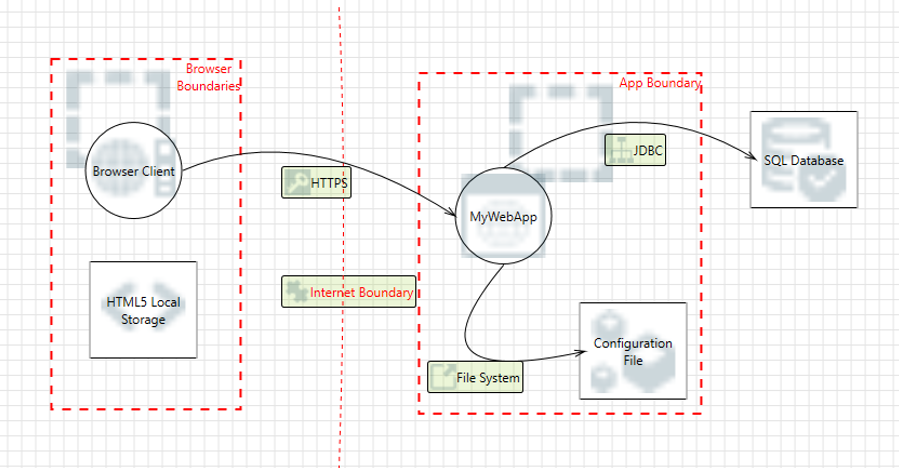
The Microsoft Threat Modeling Tool (TM2) works through a layered approach that combines user input, pre-defined patterns, and automated analysis to help identify and mitigate potential security threats in software systems.
Here’s a breakdown of how TM2 works:
1. User Input:
- Users first draw a Data Flow Diagram (DFD) using the tool’s visual editor. This DFD represents the system’s components, data flows, and trust boundaries.
- Users then identify assets to be protected and define the system’s security objectives.
- Additional details can be added to each element, such as descriptions, properties, and vulnerabilities.
2. Threat Analysis:
- TM2 utilizes the STRIDE methodology, which stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. This framework assists users in systematically considering different types of threats that could target the system.
- Based on the DFD and STRIDE methodology, TM2 automatically generates a list of potential threats for each element in the diagram.
- Users can then refine and prioritize these threats based on their likelihood and impact on the system and its assets.
3. Mitigation Recommendations:
- TM2 provides suggested mitigation strategies for identified threats, drawing from built-in libraries and best practices.
- Users can choose and refine these mitigations, or add their own custom countermeasures to address specific vulnerabilities.
- The tool helps link mitigations to corresponding threats, ensuring comprehensive coverage.
4. Collaboration and Reporting:
- TM2 allows multiple users to work on the same threat model simultaneously, facilitating collaboration and discussions between developers, architects, and security professionals.
- Users can add comments and notes to specific elements for documentation and communication.
- TM2 generates detailed reports in HTML format that summarize the threat analysis, identified threats, potential mitigations, and rationale behind decisions. These reports can be shared with auditors and stakeholders.
TM2’s Architecture:
TM2 consists of several components:
- Client application: The user interface where users create and edit threat models.
- Engine: Analyzes the data flow diagram and generates potential threats based on the STRIDE methodology.
- Libraries: Contain pre-defined threat and mitigation patterns.
- Persistence layer: Stores threat models and related data.
- Reporting module: Generates HTML reports.
Overall, TM2’s architecture is designed to be flexible and extensible, allowing developers to customize the tool and add their own libraries and patterns.
How to Install Microsoft Threat Modeling Tool it?
Here are the steps to install the Microsoft Threat Modeling Tool (TM2):
1. Download the Tool:
- Visit the official download page.
- Click the “Download” button to save the installer file (
ThreatModelingTool2016.msi) to your computer.
2. Check Prerequisites:
- Ensure you have .NET Framework 4.5 or later installed on your system. If not, download and install it from Microsoft’s website.
3. Run the Installer:
- Double-click the downloaded
ThreatModelingTool2016.msifile to start the installation wizard. - Use the on-screen instructions to complete the installation process.
4. Launch the Tool:
- Once installation is complete, you can find the tool in your Start Menu or by searching for “Threat Modeling Tool”.
- Launch the tool to start creating and analyzing threat models.
Important Notes:
- Administrator Privileges: You might need administrator privileges to install the tool.
- Updates: Check for updates periodically from the Microsoft Download Center to ensure you have the latest version with bug fixes and new features.
- Visual Studio Integration: If you’re using Visual Studio, you can also install the Threat Modeling Tool for Visual Studio extension for a more integrated experience.
Basic Tutorials of Microsoft Threat Modeling Tool: Getting Started
Here’s a step-by-step basic tutorial on using the Microsoft Threat Modeling Tool (TM2), incorporating images for visual guidance:
1. Create a New Threat Model:
- Launch TM2 and click “File” > “New”.
- Choose a template (e.g., “Simple Web Application”) or start with a blank diagram.
- Give your model a descriptive name and save it.
2. Draw the Data Flow Diagram (DFD):
- Pull and drop elements from the toolbox onto the canvas:
- Processes (rectangles): Represent actions or functions.
- Data stores (open rectangles): Contain data.
- External entities (person icons): Interact with the system.
- Data flows (arrows): Show data movement between elements.
- Trust boundaries (dotted lines): Separate areas of different trust levels.
3. Identify Assets and Security Objectives:
- Right-click on elements to add details:
- Description: Explain the element’s purpose.
- Assets: List valuable information or resources to protect.
- Security objectives: Define protection goals for assets.
4. Generate Threats:
- Click the “Analyze” tab.
- Select a STRIDE category (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege).
- TM2 will automatically generate potential threats based on the DFD and STRIDE.
5. Review and Refine Threats:
- Review the generated threats for relevance and accuracy.
- Add any missing threats you identify.
- Prioritize threats based on likelihood and impact.
6. Identify Mitigations:
- TM2 suggests potential mitigations for each threat.
- Review and select appropriate mitigations.
- Add custom mitigations if needed.
7. Generate a Report:
- Click “File” > “Generate Report” to create an HTML report summarizing the threat model, threats, mitigations, and rationale.
8. Share and Collaborate:
- Share the threat model and report with stakeholders for review and discussion.
- TM2 supports multi-user collaboration for effective teamwork.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
