What is Netsparker?

Netsparker is a web application security scanner and vulnerability assessment tool developed by Netsparker Ltd. It is designed to help organizations identify and remediate security vulnerabilities in their web applications and websites. Netsparker automates the process of scanning and testing web applications for a wide range of security issues, including but not limited to:
- SQL Injection: Identifying vulnerabilities that allow attackers to manipulate a web application’s database.
- Cross-Site Scripting (XSS): Detecting vulnerabilities that can lead to the execution of malicious scripts in a user’s browser.
- Cross-Site Request Forgery (CSRF): Identifying weaknesses that can allow an attacker to trick a user into performing actions without their consent.
- Security Misconfigurations: Detecting misconfigured settings that may expose sensitive information or create security weaknesses.
- Out-of-Date Software: Identifying web application components or libraries that are outdated and may have known vulnerabilities.
- Authentication and Authorization Issues: Scanning for weaknesses in user authentication and authorization mechanisms.
- Sensitive Data Exposure: Detecting instances where sensitive data may be exposed to unauthorized users.
- Server-Side Request Forgery (SSRF): Identifying vulnerabilities that allow attackers to make unauthorized requests to internal or external resources.
- Path Traversal: Detecting vulnerabilities that may allow attackers to access files and directories outside of the intended scope.
- XML External Entity (XXE) Injection: Identifying weaknesses that can lead to the disclosure of internal files or denial of service attacks.
Netsparker provides automated scanning capabilities that simulate real-world attacks against web applications to identify vulnerabilities and potential security risks. It also offers reporting features that provide detailed information about the identified vulnerabilities, their severity, and recommendations for remediation. This information is valuable for security teams and developers to prioritize and address security issues effectively.
Top 10 use cases of Netsparker:
Here are the top 10 use cases of Netsparker:
- Web Application Vulnerability Scanning: Netsparker scans web applications to identify a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), and security misconfigurations.
- Automated Security Testing: Netsparker automates the process of security testing, making it easier for organizations to assess the security of their web applications without extensive manual effort.
- Continuous Security Monitoring: Netsparker can be set up for continuous monitoring, regularly scanning web applications to detect new vulnerabilities that may have emerged since the last scan.
- Compliance Assessment: Organizations can use Netsparker to assess the compliance of their web applications with security standards and regulatory requirements, such as OWASP Top Ten and PCI DSS.
- False Positive Reduction: Netsparker uses advanced scanning techniques to minimize false positives, ensuring that the identified vulnerabilities are accurate and actionable.
- Web Application Inventory: Netsparker helps organizations maintain an inventory of their web applications, ensuring that all applications are scanned and assessed for vulnerabilities.
- Reporting and Remediation: Netsparker generates detailed reports that include descriptions of vulnerabilities, severity ratings, and recommendations for remediation. This information is valuable for security teams and developers.
- Integration with Development Pipelines: Netsparker can be integrated into development pipelines and continuous integration/continuous deployment (CI/CD) processes to automate security testing throughout the software development lifecycle.
- API Security Testing: Netsparker can be used to test the security of APIs (Application Programming Interfaces) to identify vulnerabilities and weaknesses that could be exploited by attackers.
- Web Application Firewall (WAF) Testing: Organizations can use Netsparker to evaluate the effectiveness of their Web Application Firewalls by simulating attacks and assessing how well the WAF protects against them.
Netsparker is a valuable tool for organizations that develop or use web applications, as it helps them identify and address vulnerabilities before they can be exploited by malicious actors. It streamlines the security testing process and provides actionable insights for improving web application security.
What are the feature of Netsparker?
Here are the key features of Netsparker, along with an overview of how it works and its architecture:
Key Features of Netsparker:
- Automated Scanning: Netsparker automates the scanning and assessment of web applications to identify a wide range of vulnerabilities, including SQL injection, cross-site scripting (XSS), and more.
- Comprehensive Coverage: It offers comprehensive coverage of web applications, including single-page applications, RESTful APIs, and complex web forms.
- Accurate Vulnerability Identification: Netsparker employs advanced scanning techniques to minimize false positives and deliver accurate results, reducing the need for manual verification.
- Continuous Monitoring: Netsparker supports continuous scanning and monitoring, allowing organizations to stay vigilant against emerging vulnerabilities.
- Compliance Scanning: It provides compliance scanning capabilities, helping organizations assess their web applications’ compliance with various security standards and regulations, such as OWASP Top Ten and PCI DSS.
- Reporting and Remediation: Netsparker generates detailed reports that include vulnerability descriptions, severity ratings, and recommendations for remediation, streamlining the vulnerability management process.
- Integration with CI/CD Pipelines: Netsparker can be integrated into development pipelines and CI/CD processes, enabling automated security testing during the software development lifecycle.
- Web Application Firewall (WAF) Testing: Organizations can use Netsparker to evaluate the effectiveness of their Web Application Firewalls by simulating attacks and assessing how well the WAF protects against them.
- API Security Testing: Netsparker is capable of testing the security of APIs (Application Programming Interfaces) to identify vulnerabilities and weaknesses.
- Integration Capabilities: It can be integrated with other security tools and platforms, such as SIEM systems and issue tracking systems, for a more holistic security approach.
How Netsparker works and Architecture?
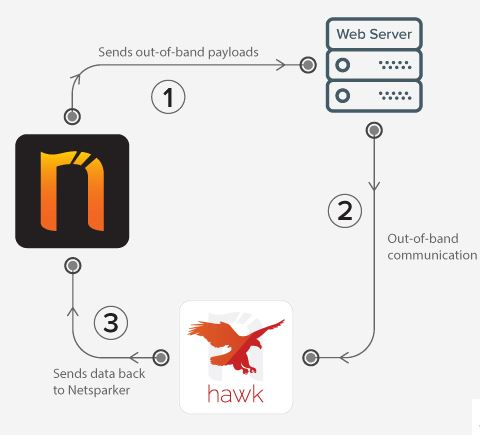
Netsparker follows a straightforward process to scan and assess web applications:
- Target Selection: Users specify the target web application or website that needs to be scanned.
- Scan Configuration: Users configure the scan settings, including authentication credentials (if needed), scan depth, and scope.
- Scanning: Netsparker performs an automated scan of the web application, simulating various attack scenarios and analyzing the application’s responses.
- Vulnerability Identification: During the scan, Netsparker identifies vulnerabilities and security weaknesses by analyzing the application’s behavior and responses.
- Data Analysis: Netsparker’s scanning engine analyzes the data collected during the scan to generate a detailed report of identified vulnerabilities.
- Reporting: Netsparker generates comprehensive reports that provide information about each identified vulnerability, its severity, impact, and recommendations for remediation.
Netsparker Architecture:
Netsparker’s architecture may vary depending on the deployment option chosen (on-premises or cloud-based). However, here are some common components:
- Scanner Engine: The scanner engine performs the actual scanning and vulnerability identification. It simulates attacks and analyzes the application’s responses.
- Scanning Server: In a distributed setup, scanning servers coordinate and manage scan tasks, ensuring efficient scanning of multiple targets.
- Web Interface: Netsparker provides a web-based interface for users to configure scans, view results, and generate reports.
- Vulnerability Database: Netsparker maintains a database of known vulnerabilities and attack patterns to aid in the scanning process.
- Integration Points: Netsparker can be integrated with other security tools, development environments, and workflow systems to streamline security processes.
Netsparker’s architecture is designed for flexibility, scalability, and ease of use, making it suitable for organizations of varying sizes and security needs. It helps organizations proactively identify and address web application vulnerabilities to strengthen their overall security posture.
How to Install Netsparker?
To install Netsparker, you will need to download the installation package from the Netsparker website. The package you download will be specific to your operating system and processor.
Once you have downloaded the installation package, follow the steps below to install Netsparker:
On Windows:
- Double-click on the Netsparker installation package to open the InstallShield Wizard.
- Apply the live-screen instructions to complete the installation.
On macOS:
- Open a Terminal window.
- Navigate to the directory where you downloaded the installation package.
- Run the following command to install Netsparker:
sudo sh netsparker-<version>-<platform>.pkgReplace <version> with the version of Netsparker you are installing, and replace <platform> with your operating system platform.
On Linux:
- Open a terminal window.
- Navigate to the directory where you downloaded the installation package.
- Run the following command to install Netsparker:
sudo sh netsparker-<version>-<platform>.runReplace <version> with the version of Netsparker you are installing, and replace <platform> with your operating system platform.
Once Netsparker is installed, you will need to create an account and activate your license. You can do this by opening Netsparker in a web browser and following the on-screen instructions.
Additional notes:
- If you are installing Netsparker on a remote server, you will need to enable SSH port forwarding on the client machine.
- If you are installing Netsparker on a Linux server, you will need to install the following packages:
sudo yum install -y epel-release
sudo yum install -y openssl-devel python-devel sqlite-devel- If you are installing Netsparker on a macOS server, you will need to install the following packages:
brew install openssl
brew install python3
brew install sqlite3Once Netsparker is installed and activated, you can start scanning your web applications for vulnerabilities.
Basic Tutorials of Netsparker: Getting Started

The following are the stepwise basic tutorial of Netsparker:
1. Create an account and activate your license.
Once you have created an account and activated your license, you can start using Netsparker to scan your web applications for vulnerabilities.
2. Add your web applications to Netsparker.
You can add your web applications manually or by importing a list of web applications from a file.
3. Create a scan policy.
A scan policy specifies the types of scans to perform, the frequency of scans, and the web applications to scan.
4. Run a scan.
Once you have created a scan policy, you can run a scan to identify vulnerabilities in your web applications. Netsparker offers a variety of scan types, including:
- Quick Scan: Performs a basic scan of your web applications for the most common vulnerabilities.
- Comprehensive Scan: Performs a more in-depth scan of your web applications for a wider range of vulnerabilities.
- Custom Scan: Allows you to select the specific types of vulnerabilities to scan for.
5. Review the scan results.
Once a scan has completed, you can review the results in the Netsparker web interface. The scan results will show you which web applications have vulnerabilities and what the vulnerabilities are.
6. Remediate vulnerabilities.
Once you have identified vulnerabilities, you need to take steps to remediate them. This may involve patching software, updating firmware, or implementing security controls.
Simple example of how to use Netsparker to identify and remediate vulnerabilities:
- Create a scan policy that scans all of your web applications for vulnerabilities.
- Run the scan policy.
- Review the scan results.
- Identify any vulnerabilities that need to be remediated.
- Prioritize the remediation of vulnerabilities based on their severity and risk.
- Take steps to remediate the vulnerabilities.
- Run the scan policy again to verify that the vulnerabilities have been remediated.
You can repeat this process on a regular basis to ensure that your web applications are protected from known vulnerabilities.
Additional tips for using Netsparker:
- Use Netsparker to scan your web applications both before and after they are deployed to production.
- Use Netsparker to scan your web applications on a regular basis to identify new vulnerabilities.
- Use Netsparker’s reporting features to track your vulnerability management progress and identify trends.
- Use Netsparker to integrate with other security tools, such as SIEM systems and ticketing systems.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
