What is Phantom?

Phantom is a security orchestration, automation, and response (SOAR) platform designed to streamline and automate security operations and incident response processes. It enables security teams to connect and orchestrate their existing security tools, automate repetitive tasks, and respond to incidents more efficiently.
Phantom’s capabilities can significantly improve the efficiency and effectiveness of security operations teams by automating repetitive tasks, accelerating incident response times, and providing a unified platform for incident management and collaboration.
Top 10 use cases of Phantom:
Here are the top 10 use cases of Phantom:
- Incident Triage and Enrichment: Phantom collects and aggregates security alerts and incidents from various sources, enriching them with contextual information from internal and external sources.
- Playbook Automation: Users can create custom playbooks to define and automate step-by-step incident response workflows, integrating with security tools and systems.
- Incident Workflow Management: Phantom provides a centralized platform for tracking, managing, and prioritizing security incidents, ensuring that critical issues receive immediate attention.
- Alert Management: The platform centralizes and deduplicates alerts from multiple security tools, helping security teams reduce alert fatigue and prioritize their response efforts.
- Orchestration of Security Tools: Phantom orchestrates actions and responses across a wide range of security tools and technologies, enabling coordinated incident response.
- Threat Intelligence Integration: Phantom integrates with threat intelligence feeds to automatically correlate and enrich incident data with relevant threat context.
- Automated Response: It automates incident response actions, allowing organizations to execute predefined tasks and workflows in response to security incidents.
- Custom Integrations: Users can create custom integrations with security tools, systems, and APIs, ensuring compatibility with their existing technology stack.
- Machine Learning and AI: Phantom leverages machine learning and artificial intelligence to help identify and respond to threats more effectively.
- User and Entity Behavior Analytics (UEBA) Integration: The platform integrates with UEBA solutions to monitor and detect anomalous user and entity behaviors.
- Forensics and Investigation: Phantom provides tools for digital forensics and evidence gathering during incident investigations.
- Incident Reporting: The platform offers incident reporting and documentation capabilities to create detailed incident reports for compliance and analysis.
What are the feature of Phantom?
Phantom is a robust security orchestration, automation, and response (SOAR) platform designed to help security teams streamline and automate their incident response and security operations. It provides a wide range of features and capabilities to enhance incident response efficiency and effectiveness. Here are the key features of Phantom:
- Playbooks: Phantom allows users to create custom playbooks, which are sets of predefined actions and workflows for automating incident response processes. Playbooks can be tailored to specific security use cases and threats.
- Integration Hub: Phantom offers a vast library of pre-built integrations with various security tools, enabling seamless orchestration of actions across a wide range of technologies.
- Incident Management: The platform provides a centralized incident management interface for tracking, prioritizing, and managing security incidents and alerts from multiple sources.
- Alert Ingestion: Phantom can ingest alerts and incidents from various security tools and sources, reducing the time and effort required to consolidate and analyze incoming security data.
- Event Correlation: Phantom correlates and enriches incident data with additional context from threat intelligence feeds, asset databases, and external sources to provide a comprehensive view of each incident.
- Automated Workflows: Security teams can automate repetitive tasks, such as alert triage, investigation, and response actions, to accelerate incident resolution.
- Human-in-the-Loop Automation: Phantom supports human decision points within automated workflows, allowing security analysts to make critical decisions when necessary.
- Case Management: It offers case management capabilities to group related incidents, track investigation progress, and maintain detailed incident records.
- Threat Intelligence Integration: Phantom integrates with threat intelligence sources and platforms to enrich incident data with relevant threat context, indicators of compromise (IOCs), and known attack patterns.
- Incident Reporting: The platform provides incident reporting and documentation features to create detailed reports for compliance, analysis, and post-incident review.
- Machine Learning and AI: Phantom incorporates machine learning and artificial intelligence capabilities to enhance threat detection and automate decision-making within workflows.
- Customization: Users can create custom scripts, actions, and integrations to tailor Phantom to their specific security environment and requirements.
How Phantom works and Architecture?
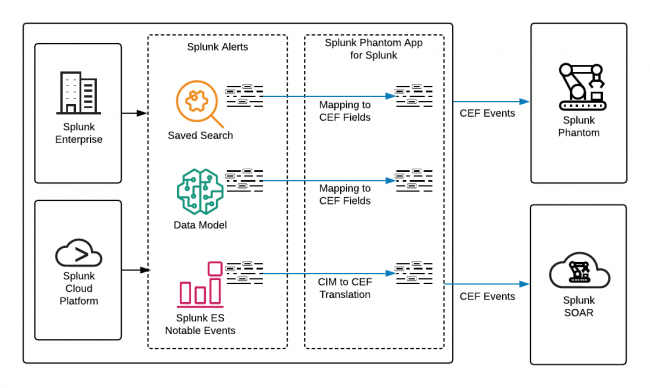
Phantom’s architecture and workflow can be summarized as follows:
Components:
- Phantom Core: This is the central component of the platform that manages playbooks, integrations, and incident data.
- Phantom Apps: These are pre-built integrations with various security tools, allowing users to connect and orchestrate actions across those tools.
- Playbooks: Playbooks define the workflows and actions to be taken in response to security incidents. They can be generated and customized by users.
Workflow:
- Alert Ingestion: Phantom ingests alerts and incidents from various security tools and sources, creating incidents in its incident management interface.
- Playbook Execution: Playbooks are executed in response to incidents, orchestrating actions across connected security tools and technologies.
- Automation: Automated tasks within playbooks help triage, investigate, and respond to incidents, reducing manual effort.
- Human Decision Points: Playbooks can include human decision points, where security analysts can make critical decisions or provide additional input.
- Reporting and Documentation: Phantom offers reporting and documentation features to create detailed incident reports and maintain a historical record of incidents.
- Integration: Phantom integrates seamlessly with security tools, threat intelligence feeds, and external data sources to enrich and automate incident response.
Phantom’s architecture and features are designed to enhance incident response capabilities by automating repetitive tasks, improving the coordination of actions across security tools, and providing a unified platform for incident management and collaboration.
How to Install Phantom?
There are two ways to install Phantom: as a browser extension or as a desktop app.
To install Phantom as a browser extension:
- Go to the Phantom website and click on the “Download” button.
- Select the extension for your browser and click on the “Install” button.
- Follow the on-screen instructions to install the extension.
To install Phantom as a desktop app:
- Go to the Phantom website and click on the “Download” button.
- Select the desktop app for your operating system and click on the “Download” button.
- Follow the on-screen instructions to install the desktop app.
Once Phantom is installed, you can create a new account or connect to an existing account.
To verify that Phantom is installed correctly:
- For the browser extension, open your browser and click on the extension icon. You should see the Phantom logo.
- For the desktop app, open the app and click on the “Connect Wallet” button. You should be able to select your Phantom wallet from the list of wallets.
How to open the Phantom extension:
- Press on the extension icon in your browser toolbar.
- Click on the “Open Phantom” button in the extension popup.
How to open the Phantom desktop app:
- Double-click on the Phantom app icon on your desktop.
Basic Tutorials of Phantom: Getting Started
The following steps are the Basic Tutorials of Phantom:
Getting started
- Install Phantom. You can install Phantom as a browser extension or as a desktop app.
- Create a Phantom wallet. If you don’t already have a Phantom wallet, you can create one by clicking on the “Create Wallet” button.
- Fund your wallet. Once you have created a Phantom wallet, you can fund it by sending Solana (SOL) to your wallet address. You can find your wallet address by clicking on the “Receive” button.
Sending and receiving SOL
- To send SOL, click on the “Send” button and enter the recipient’s wallet address and the amount of SOL you want to send.
- To receive SOL, click on the “Receive” button and give the sender your wallet address.
Interacting with Solana dApps
- To interact with a Solana dApp, go to the website of the dApp and click on the “Connect Wallet” button.
- Select your Phantom wallet from the list of wallets.
- Once your wallet is connected, you can start interacting with the dApp.
Additional tips
- Use a strong password for your Phantom wallet and enable 2FA for added security.
- Keep your Phantom software up to date.
- Be careful when interacting with Solana dApps, and only interact with dApps that you trust.
Example use case: Sending SOL to a friend
- Open Phantom and connect your wallet.
- Click on the “Send” button.
- Enter your friend’s wallet address and the amount of SOL you want to send.
- Click on the “Send” button again to confirm the transaction.
Example use case: Interacting with a Solana dApp to mint an NFT
- Go to the website of the Solana dApp that you want to use to mint an NFT.
- Click on the “Connect Wallet” button.
- Select your Phantom wallet from the list of wallets.
- Once your wallet is connected, follow the instructions on the dApp’s website to mint an NFT.
Phantom is a powerful tool for interacting with the Solana blockchain. By following the steps in this tutorial, you can learn how to use Phantom to send and receive SOL, interact with Solana dApps, and more.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
