What is Ping?

Ping Identity is a company that specializes in identity and access management (IAM) solutions. They provide products and services to help organizations manage and secure user identities, access to applications, and data.
Ping Identity’s IAM solutions are designed to address the complex challenges of managing and securing user identities and access in modern IT environments, including cloud, mobile, and on-premises systems. They help organizations improve security, streamline user management, and enhance the user experience.
Top 10 use cases of Ping:
Here are the top 10 use cases for Ping Identity:
- Single Sign-On (SSO): Ping Identity enables SSO for users, allowing them to access multiple applications with a single set of credentials. This simplifies the login process and enhances user productivity.
- Multi-Factor Authentication (MFA): Organizations can implement MFA using Ping Identity to add an extra layer of security. Users are required to provide multiple authentication factors (e.g., password, OTP, biometrics) for access.
- Federated Identity: Ping Identity supports identity federation, allowing users to use their existing credentials from trusted identity providers to access applications. This is particularly useful for partner or customer portals.
- User Provisioning and De-Provisioning: Ping Identity automates the process of creating and managing user accounts in various applications, ensuring that users have the right access permissions throughout their lifecycle.
- API Security: Ping Identity provides API security solutions, protecting APIs and ensuring that only authorized users and applications can access them. This is crucial for securing microservices and APIs.
- Identity and Access Governance: Organizations can use Ping Identity to enforce access policies and governance controls, ensuring that users have appropriate access to resources and data.
- Customer Identity and Access Management (CIAM): Ping Identity helps businesses manage customer identities and provide secure access to digital services, enhancing user experiences while maintaining security.
- Adaptive Authentication: Ping Identity uses contextual information to assess the risk of login attempts and adjust authentication requirements accordingly. This helps prevent unauthorized access.
- Passwordless Authentication: Organizations can implement passwordless authentication methods, such as biometrics or hardware tokens, to improve security and user convenience.
- Identity Analytics: Ping Identity offers identity analytics and behavioral analysis to detect and respond to suspicious activities, helping organizations identify potential security threats.
- Identity-as-a-Service (IDaaS): Ping Identity provides cloud-based identity services, making it easier for organizations to adopt IAM solutions without significant infrastructure investments.
- Zero Trust Security: Ping Identity aligns with the Zero Trust security model by continuously verifying user identities and device trust before granting access to resources.
- Compliance and Audit: Ping Identity helps organizations maintain compliance with regulatory requirements by providing auditing and reporting capabilities to track user access and authentication events.
- Secure Browsing: Ping Identity can be used to secure web applications and protect against browser-based attacks like phishing.
- Mobile Application Security: Ping Identity enhances security for mobile applications by providing secure authentication and access controls for mobile users.
What are the feature of Ping?
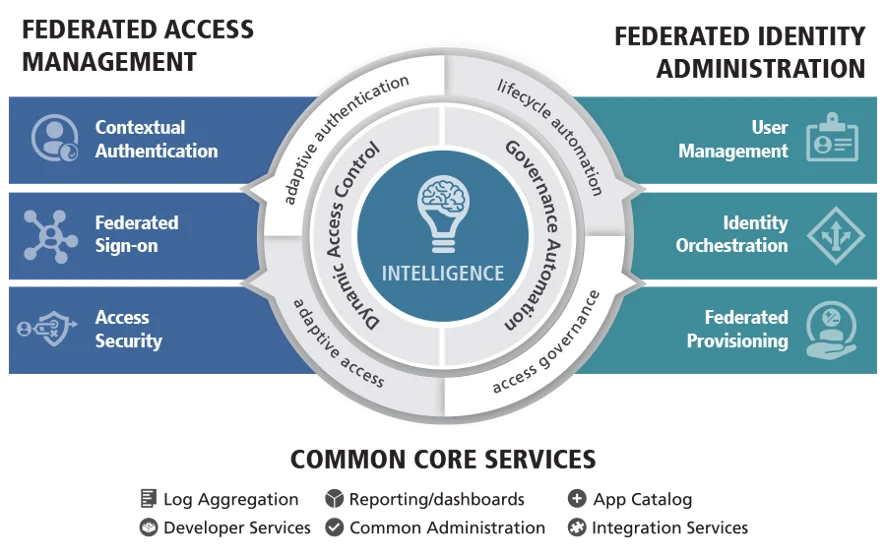
Ping Identity provides a comprehensive set of features within its identity and access management (IAM) solutions to help organizations manage and secure user identities and access to applications and resources. Here are some of the key features of Ping Identity, along with an overview of how it works and its architecture:
Key Features of Ping Identity:
- Single Sign-On (SSO): Ping Identity enables SSO, allowing users to access multiple applications with a single set of credentials, enhancing user productivity and reducing password fatigue.
- Multi-Factor Authentication (MFA): Organizations can implement MFA using Ping Identity to require users to provide multiple authentication factors, such as passwords, OTPs, or biometrics, for access.
- Federated Identity: Ping Identity supports identity federation, allowing users to use their existing credentials from trusted identity providers (e.g., SAML, OAuth) to access applications and resources.
- User Provisioning and De-Provisioning: Ping Identity automates user provisioning and de-provisioning processes, ensuring that user accounts are created, updated, and deactivated according to predefined policies.
- API Security: Ping Identity provides API security solutions to protect APIs and ensure that only authorized users and applications can access them, crucial for securing modern microservices and APIs.
- Identity and Access Governance: Organizations can enforce access policies and governance controls, ensuring that users have appropriate access to resources and data based on their roles and responsibilities.
- Customer Identity and Access Management (CIAM): Ping Identity helps businesses manage customer identities and provide secure access to digital services, improving customer experiences while maintaining security.
- Adaptive Authentication: Ping Identity uses contextual information, such as user behavior and device trust, to assess the risk of login attempts and adjust authentication requirements accordingly.
- Passwordless Authentication: Organizations can implement passwordless authentication methods, such as biometrics or hardware tokens, to enhance security and user convenience.
- Identity Analytics: Ping Identity offers identity analytics and behavioral analysis to detect and respond to suspicious activities, helping organizations identify and mitigate potential security threats.
How Ping works and Architecture?
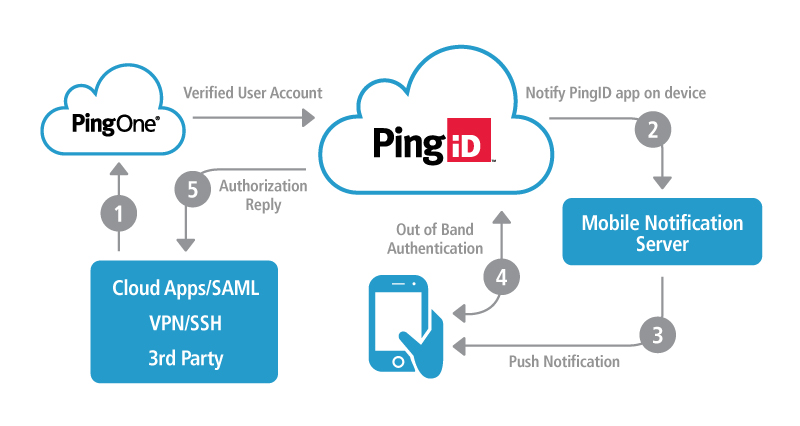
- User Authentication: When a user attempts to access an application or resource, Ping Identity handles the authentication process. Users provide their credentials (e.g., username and password) and additional authentication factors, if required.
- Identity Verification: Ping Identity verifies user identities using various authentication methods, including password-based, MFA, or federated identity.
- Access Control: Ping Identity enforces access policies that define what resources and data each user is allowed to access based on their identity, roles, and contextual information.
- Single Sign-On (SSO): Once authenticated, users can access multiple applications seamlessly without the need to re-enter their credentials, thanks to SSO capabilities.
- User Provisioning and Lifecycle Management: Ping Identity automates user provisioning and de-provisioning processes, ensuring that users have the right access throughout their lifecycle.
- API Security: For APIs and microservices, Ping Identity provides security controls, such as OAuth and token-based authentication, to protect access to these services.
- Adaptive Authentication: Ping Identity assesses the risk of login attempts based on contextual information and may require additional authentication factors for high-risk access attempts.
Ping Identity’s architecture is designed for scalability and flexibility:
- Ping Identity Server: This is the core component that manages user authentication, access policies, and identity federation. It acts as the authentication authority for users.
- PingFederate: This component handles identity federation, allowing users to use their existing credentials from trusted identity providers to access applications.
- PingAccess: PingAccess is responsible for enforcing access policies and controlling resource access based on user identities and policies. It supports SSO and API security.
- PingDirectory: This directory service stores user identities and attributes. It can be integrated with other directories and databases.
- PingOne: This cloud-based solution offers identity and access management as a service (IDaaS) and is suitable for organizations seeking cloud-based IAM solutions.
- PingIntelligence: PingIntelligence provides identity analytics and threat detection to monitor user behavior and detect suspicious activities.
- API Gateway: Ping Identity can integrate with API gateways to secure API endpoints and manage API access.
- Mobile SDKs: Ping Identity provides mobile software development kits (SDKs) to help developers integrate secure authentication and authorization into mobile applications.
Ping Identity’s architecture allows organizations to implement a flexible and scalable IAM solution that meets their specific security and access control requirements. It helps organizations improve security, streamline user management, and enhance the user experience across various use cases and deployment scenarios.
How to Install Ping?
To install Ping on a Linux system, you can use the following steps:
- Update the system repositories:
sudo apt update- Install the
iputils-pingpackage:
sudo apt install iputils-ping- Check the installation by running the below command:
ping -c 1 google.comIf the command is successful, you will see output similar to the following:
PING google.com (142.250.183.35) 56(84) bytes of data.
64 bytes from lhr18s17-in-f14.1e100.net (142.250.183.35): icmp_seq=1 ttl=110
time=1.578 ms
64 bytes from lhr18s17-in-f14.1e100.net (142.250.183.35): icmp_seq=2 ttl=110
time=1.394 ms
64 bytes from lhr18s17-in-f14.1e100.net (142.250.183.35): icmp_seq=3 ttl=110
time=1.403 ms
--- google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2002ms
rtt min/avg/max/mdev = 1.394/1.425/1.578/0.077 msThis indicates that Ping was successfully installed and is working correctly.
Once Ping is installed, you can use it to test the connectivity between your system and another host. To do this, simply run the ping command followed by the IP address or hostname of the host you want to test. For example, to ping Google, you would run the following command:
ping google.comIf the command is successful, you will see output similar to the example above. If the command fails, you will see an error message indicating that the host could not be reached.
Ping is a useful tool for troubleshooting network connectivity issues. It can also be used to test the performance of a network connection by measuring the round-trip time (RTT) of packets.
Basic Tutorials of Ping: Getting Started

The following steps are the Basic Tutorials of Ping:
Step 1: Open a command prompt window.
- In Windows, press
Windows+Rto open the Run dialog box. Typecmdand pressEnter. - In macOS, open Spotlight Search by pressing
Command+Space. TypeTerminaland pressEnter. - In Linux, click
Ctrl+Alt+Tto open a terminal window.
Step 2: Type the following command and press Enter:
ping [destination IP address or hostname]
For example, to ping Google, you would type the following command:
ping google.com
Step 3: The ping command will send four Echo Request messages to the destination host and wait for a response.
If the destination host is reachable, the ping command will display a summary of the results, including the number of packets sent, the number of packets received, and the round-trip time (RTT) for each packet.
Step 4: If the destination host is not reachable, the ping command will display a “Request timed out” error message.
Example output:
Pinging google.com [142.250.181.196] with 32 bytes of data:
Reply from 142.250.181.196: bytes=32 time=11ms TTL=55
Reply from 142.250.181.196: bytes=32 time=11ms TTL=55
Reply from 142.250.181.196: bytes=32 time=11ms TTL=55
Reply from 142.250.181.196: bytes=32 time=11ms TTL=55
Ping statistics for 142.250.181.196:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 11ms, Maximum = 11ms, Average = 11ms
Troubleshooting ping problems:
If you are having problems pinging a device, there are a few things you can try:
- Make sure that the device is turned on and connected to the network.
- Verify that the IP address or hostname of the device is correct.
- Try pinging another device on the network to see if the problem is specific to the device you are trying to ping.
- Try disabling any firewalls or antivirus software that may be running on the device you are trying to ping.
- If you are still having problems, contact your network administrator for assistance.
Additional tips:
- You can use the
-noption to specify the number of Echo Request messages to send. - You can use the
-toption to ping the destination host continuously until the ping command is stopped. - You can use the
-loption to specify the size of the Echo Request messages in bytes. - You can use the
-ioption to specify the interval in milliseconds between sending Echo Request messages.
For more information on the ping command, you can type ping /? in a command prompt window and press Enter.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
