What is Rapid7?

Rapid7 is a cybersecurity company that provides a wide range of security solutions and services to help organizations identify, prioritize, and mitigate security vulnerabilities and threats. The company offers a variety of products and services, with a focus on vulnerability management, incident detection and response, and security analytics.
Top 10 use cases of Rapid7?
Here are the top 10 use cases of Rapid7:
- Vulnerability Management: Rapid7’s solutions, such as InsightVM (formerly Nexpose), help organizations discover and assess vulnerabilities in their networks, systems, and applications. They provide insights into the risk associated with each vulnerability.
- Threat Detection and Response: Rapid7’s InsightIDR is a cloud-based SIEM (Security Information and Event Management) solution that enables organizations to detect and respond to security threats in real-time. It combines log analysis, user behavior analytics, and endpoint detection and response (EDR) capabilities.
- Incident Response: Rapid7 offers incident response services and solutions to help organizations plan for and respond to security incidents effectively. This includes playbooks, guidance, and automation capabilities.
- Penetration Testing: Rapid7 provides penetration testing services, including both manual and automated assessments, to identify security weaknesses and vulnerabilities in an organization’s infrastructure and applications.
- Cloud Security: With the increasing use of cloud services, Rapid7 offers solutions to assess and secure cloud environments, including AWS, Azure, and Google Cloud Platform.
- User and Entity Behavior Analytics (UEBA): InsightIDR uses UEBA to monitor user and entity behavior, helping organizations detect insider threats, compromised accounts, and suspicious activities.
- Endpoint Detection and Response (EDR): Rapid7’s EDR solutions provide visibility into endpoints (workstations, servers, etc.) and the ability to detect and respond to threats on those endpoints.
- Security Orchestration and Automation (SOAR): Rapid7’s SOAR platform, InsightConnect, allows organizations to automate security processes, streamline incident response, and integrate various security tools and services.
- Application Security: Rapid7 offers solutions to assess the security of web applications and APIs, helping organizations identify vulnerabilities like OWASP Top Ten issues.
- Compliance and Risk Management: Rapid7 helps organizations address compliance requirements by assessing their security posture against various regulatory standards, such as GDPR, HIPAA, and PCI DSS.
These are some of the primary use cases for Rapid7’s solutions and services. Rapid7 aims to provide a comprehensive cybersecurity platform that assists organizations in managing their security vulnerabilities, responding to incidents, and improving their overall security posture.
What are the feature of Rapid7?
Rapid7 is a cybersecurity company that offers a range of security solutions and services, including vulnerability management, threat detection and response, and security analytics. While the specific features and capabilities of Rapid7’s products may vary depending on the offering, here are some common features and a general overview of how Rapid7 works:
Key Features of Rapid7 Products:
- Vulnerability Assessment: Rapid7’s vulnerability management solutions, like InsightVM (formerly Nexpose), provide automated scans to identify vulnerabilities in networks, systems, and applications. They offer comprehensive coverage of assets and vulnerabilities.
- Threat Detection: Rapid7’s solutions, including InsightIDR, use advanced analytics and machine learning to detect and respond to security threats in real-time. They monitor network traffic, log data, and user behavior to identify suspicious activities and potential breaches.
- Incident Response: Rapid7 offers incident response services and solutions to help organizations prepare for, detect, and respond to security incidents effectively. This includes playbooks, automation, and workflow management.
- Penetration Testing: Rapid7 provides penetration testing services to assess an organization’s security posture by simulating real-world attacks and identifying vulnerabilities and weaknesses.
- Cloud Security: Rapid7 solutions help organizations assess and secure cloud environments, including AWS, Azure, and Google Cloud Platform. They provide visibility into cloud assets and potential security risks.
- User and Entity Behavior Analytics (UEBA): InsightIDR employs UEBA to monitor user and entity behavior, enabling organizations to detect insider threats and unusual activities.
- Endpoint Detection and Response (EDR): Rapid7’s EDR solutions offer endpoint visibility, threat detection, and response capabilities. They help organizations protect endpoints from advanced threats.
- Security Orchestration and Automation (SOAR): InsightConnect is Rapid7’s SOAR platform, which allows organizations to automate security workflows, integrate security tools, and streamline incident response.
- Application Security: Rapid7’s solutions assess web applications and APIs for security vulnerabilities, such as those outlined in the OWASP Top Ten.
- Compliance and Risk Management: Rapid7 helps organizations evaluate their security posture against regulatory standards and compliance requirements. It provides reporting and risk assessment capabilities.
How Rapid7 works and Architecture?
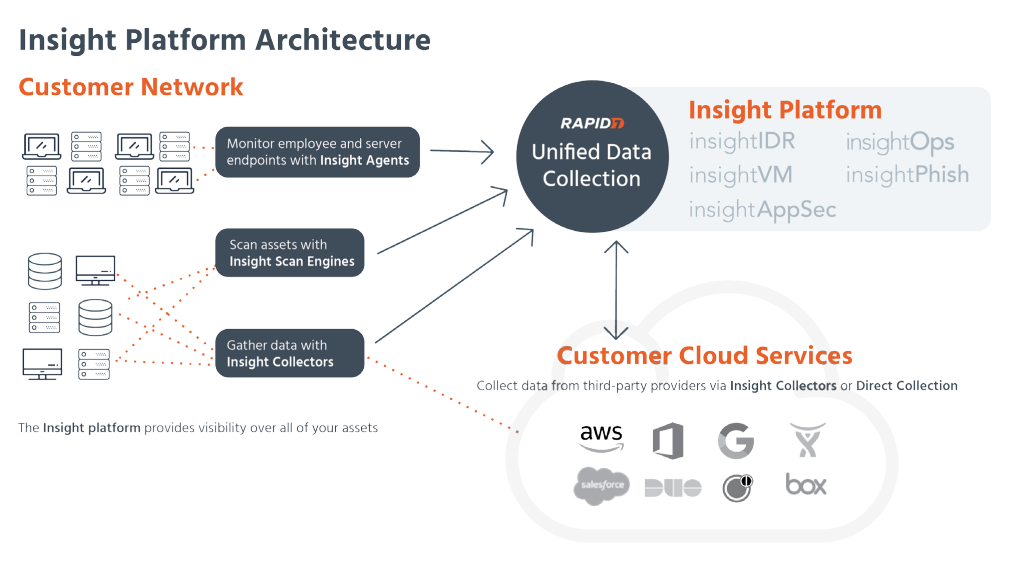
Rapid7’s products and services work together to provide a comprehensive cybersecurity solution. Here’s a simplified overview of how Rapid7 works:
- Deployment: Organizations subscribe to Rapid7’s cloud-based services or deploy on-premises solutions, depending on their needs and preferences.
- Asset Discovery: Rapid7 solutions begin by discovering all assets within an organization’s environment, including devices, servers, applications, and cloud resources.
- Scanning and Monitoring: Automated scans are conducted on the assets to identify vulnerabilities, misconfigurations, and threats. Continuous monitoring and data collection provide ongoing visibility.
- Data Analysis and Threat Detection: Rapid7’s analytics engines analyze the data collected from scans, logs, and network traffic to detect security threats and vulnerabilities. Machine learning and behavior analytics are used to identify anomalies.
- Incident Response: When a security incident is detected, Rapid7’s incident response solutions and services come into play, enabling organizations to investigate, respond to, and mitigate the incident.
Rapid7 Architecture:
Rapid7 offers both cloud-based and on-premises solutions, allowing organizations to choose the deployment option that best suits their requirements. Key components of the architecture may include:
- Cloud-Based Platform: Rapid7’s cloud platform hosts the central services, including vulnerability assessment, threat detection, and analytics.
- On-Premises Scanners: For vulnerability assessment, organizations can deploy on-premises scanners to conduct scans and collect data.
- Endpoint Agents: In the case of endpoint detection and response, lightweight agents may be deployed on endpoints to collect data and facilitate real-time monitoring and response.
- Data Storage and Analysis: Rapid7’s platform stores and analyzes the data collected from scans, logs, and network traffic. Advanced analytics engines are used for threat detection and risk assessment.
- Integration Points: Rapid7 solutions are designed to integrate with other security tools, SIEM platforms, and third-party services to create a comprehensive security ecosystem.
Rapid7’s architecture is flexible, scalable, and designed to adapt to the evolving needs of organizations, making it suitable for businesses of various sizes and industries.
How to Install Rapid7?
There are two ways to install Rapid7: using the graphical installer or using the command line.
To install Rapid7 using the graphical installer:
- Download the Rapid7 installer from the Rapid7 website.
- Double-click the installer icon to start the installation process.
- Follow the prompts to install Rapid7.
- Once the installation is complete, you can launch Rapid7 by clicking the Rapid7 icon on your desktop.
To install Rapid7 using the command line:
- Open a command prompt window.
- Navigate to the directory where you downloaded the Rapid7 installer.
- Run the following command:
msiexec /i Rapid7Installer.msi- Implement the on-screen instructions to fulfill the installation.
Note: If you are installing Rapid7 on a Windows server, you may need to run the installer as an administrator.
Once Rapid7 is installed, you will need to activate your license. To do this, follow these steps:
- Launch Rapid7.
- Click the Help menu and select Activate License.
- Enter your product key in the provided field.
- Click Activate.
Once your license is activated, you can start using Rapid7 to scan your network for vulnerabilities and manage your security posture.
Some additional tips for installing Rapid7:
- Make confirm that your system meets at least installation requirements.
- Uninstall any previously installed copies of Rapid7 before installing the latest version.
- If you are installing Rapid7 on a Windows server, you may need to run the installer as an administrator.
- If you are installing Rapid7 on a Linux system, you may need to install additional dependencies.
- If you are having trouble installing Rapid7, please consult the Rapid7 documentation or contact Rapid7 support for assistance.
Basic Tutorials of Rapid7: Getting Started

The following are the stepwise Basic Tutorials of Rapid7
1. Create a site.
A site is a logical grouping of assets that you want to scan. To create a site:
- Click the Sites tab.
- Click the Create Site button.
- Enter a name for your site and click Create.
2. Add assets to your site.
To add assets to your site:
- Click the Assets tab.
- Click the Add Assets button.
- Enter the IP addresses, hostnames, or DNS names of the assets that you want to add.
- Click Add.
3. Create a scan template.
A scan template defines the types of scans that you want to run on your assets. To create a scan template:
- Click the Scan Templates tab.
- Click the Create Scan Template button.
- Enter a name for your scan template and select the types of scans that you want to run.
- Click Create.
4. Run a scan.
To run a scan:
- Click the Scans tab.
- Click the Create Scan button.
- Select the site and scan template that you want to use.
- Click Create Scan to start the scan.
5. Review your scan results.
Once a scan is complete, you can review the results by clicking the Scans tab and clicking the name of the scan. The scan results will show you all of the vulnerabilities that were found on your assets.
6. Remediate vulnerabilities.
Once you have reviewed your scan results, you can start remediating the vulnerabilities that were found. To do this, you will need to follow the remediation instructions that are provided in the scan results.
Here are some additional tips for using Rapid7:
- You can use Rapid7 to schedule scans to run on a regular basis.
- You can create dynamic asset groups to filter your scan results.
- You can use Rapid7 to generate reports on your scan results.
- You can integrate Rapid7 with other security tools, such as SIEMs and ticketing systems.
Some additional basic tutorials for using Rapid7:
- How to create and manage dynamic asset groups: Dynamic asset groups allow you to filter your scan results based on criteria such as asset type, operating system, and vulnerability severity. To create a dynamic asset group, click the Assets tab and click the Create Dynamic Asset Group button.
- How to generate scan reports: Rapid7 offers a variety of scan reports that you can generate. To generate a scan report, click the Scans tab and click the name of the scan that you want to generate a report for. Then, click the Generate Report button and select the type of report that you want to generate.
- How to integrate Rapid7 with other security tools: Rapid7 can be integrated with a variety of other security tools, such as SIEMs and ticketing systems. To integrate Rapid7 with another security tool, consult the documentation for both Rapid7 and the other tool.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
