What is Synopsys Software Integrity Platform?

The Synopsys Software Integrity Platform (SIP) is a comprehensive suite of tools and services designed to build security and quality into software throughout the development lifecycle, from coding to deployment. It empowers organizations to deliver secure, reliable, and compliant software by providing:
- Automated security testing: Identifies vulnerabilities and security flaws early in the development process.
- Application security: Protects against cyberattacks and data breaches.
- Software composition analysis (SCA): Manages and mitigates risks introduced by open-source libraries.
- Code quality: Improves code quality and maintainability.
- Compliance management: Helps comply with industry regulations and standards.
Top 10 use cases of Synopsys Software Integrity Platform?
Top 10 Use Cases of Synopsys Software Integrity Platform:
- Shift left security: Integrate security testing throughout the development cycle to address vulnerabilities sooner and at lower cost.
- Reduce security risks: Proactively identify and mitigate potential security flaws before they reach production.
- Improve software quality: Enhance code maintainability, reliability, and performance.
- Comply with regulations: Meet industry standards and regulations like OWASP, NIST, GDPR, and PCI DSS.
- Accelerate development: Automate security and quality checks to streamline the development process.
- Empower developers: Provide developers with tools and insights to write secure and high-quality code.
- Reduce security debt: Address existing vulnerabilities and prevent future issues from accumulating.
- Build trust with customers: Deliver secure software that your customers can rely on.
- Protect sensitive data: Securely handle and store sensitive data to avoid breaches and leaks.
- Strengthen incident response: Improve your ability to detect, respond to, and recover from security incidents.
Additional Benefits of Synopsys Software Integrity Platform:
- Scalability: Supports projects of all sizes and complexities.
- Integration: Integrates with popular development tools and platforms.
- Customizable: Adapts to your specific needs and security requirements.
- Expertise: Backed by Synopsys’s deep security and application security knowledge.
Overall, the Synopsys Software Integrity Platform offers a comprehensive solution for building secure and reliable software from the ground up. Its wide range of capabilities and diverse use cases make it a valuable asset for organizations of all sizes looking to improve their software security posture.
What are the feature of Synopsys Software Integrity Platform?
Here are some of the key features of the Synopsys Software Integrity Platform (SIP):
Static Application Security Testing (SAST):
- Analyzes source code to identify vulnerabilities such as injection flaws, cross-site scripting (XSS), buffer overflows, and more.
- Supports multiple programming languages and frameworks.
- Integrates with development environments for early detection of issues.
Software Composition Analysis (SCA):
- Scans open-source and third-party components for known vulnerabilities and license compliance issues.
- Provides detailed information about component usage and potential risks.
- Helps create policies for managing open-source dependencies.
Interactive Application Security Testing (IAST):
- Combines static analysis and runtime testing to provide more accurate results.
- Detects vulnerabilities in real-time, even in complex applications.
- Identifies attack paths and prioritizes remediation efforts.
Dynamic Application Security Testing (DAST):
- Simulates attacks on running applications to uncover vulnerabilities.
- Tests for common web application attacks such as SQL injection, XSS, and broken authentication.
- Can be integrated into continuous integration/continuous delivery (CI/CD) pipelines.
Fuzz Testing:
- Generates random inputs to try to crash applications and expose hidden vulnerabilities.
- Effective in finding memory corruption issues and unexpected program behavior.
Code Quality:
- Enforces coding standards and best practices to improve code quality and maintainability.
- Detects potential defects and security issues early in the development process.
Compliance Management:
- Helps organizations meet industry regulations and standards such as OWASP, NIST, PCI DSS, and GDPR.
- Provides reporting and auditing capabilities to demonstrate compliance.
Integration and Automation:
- Integrates with popular development tools and platforms, including IDEs, build systems, issue trackers, and CI/CD pipelines.
- Automates security and quality checks to streamline the development process.
Additional Features:
- Vulnerability Management: Tracks and manages vulnerabilities throughout the development lifecycle.
- Threat Modeling: Identifies potential threats and prioritizes mitigation efforts.
- Risk Assessment: Assesses the overall security risk of software applications.
- Reporting and Dashboards: Provides comprehensive reporting and dashboards for visibility into security posture.
The SIP offers a comprehensive set of capabilities to address security and quality concerns throughout the software development lifecycle, making it a valuable tool for organizations striving to deliver secure, reliable, and compliant software.
How Synopsys Software Integrity Platform works and Architecture?
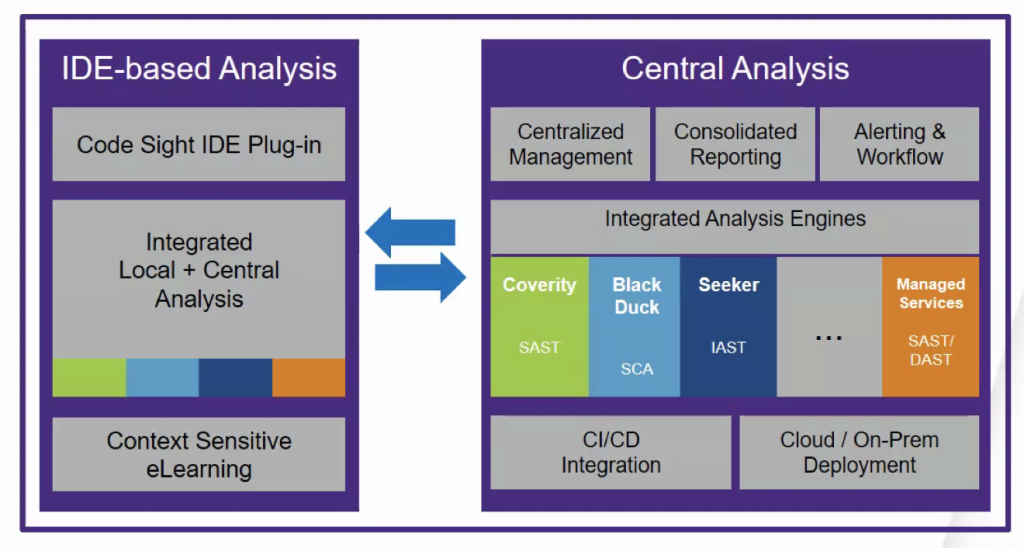
Here’s a breakdown of how Synopsys Software Integrity Platform (SIP) works and its architecture:
Key Components:
- Central Platform: Serves as the foundation, managing data, coordinating activities, and providing a unified interface.
- Testing Tools: Include SAST, SCA, IAST, DAST, fuzz testing, and code quality analyzers.
- Vulnerability Database: Stores information about known vulnerabilities, enabling detection and prioritization of risks.
- Reporting and Analytics: Generate reports, dashboards, and metrics for visibility into security posture and progress.
- Integration APIs: Facilitate connections with development tools, issue trackers, and CI/CD pipelines.
Workflow:
- Code and Component Analysis:
- Developers write code and incorporate open-source components.
- SCA scans components for vulnerabilities and license compliance issues.
- SAST analyzes source code for vulnerabilities.
- Code quality tools enforce coding standards and detect defects.
- Interactive Testing and Fuzzing:
- IAST monitors application behavior during testing and runtime for real-time vulnerability detection.
- DAST simulates attacks on running applications to uncover vulnerabilities.
- Fuzz testing probes for unexpected behavior and memory corruption issues.
- Vulnerability Management:
- Identified vulnerabilities are tracked, prioritized, and assigned for remediation.
- Developers fix vulnerabilities and rescan code to ensure fixes are effective.
- Compliance and Reporting:
- SIP generates reports to demonstrate compliance with industry standards and regulations.
- Dashboards provide visibility into security posture, progress, and risk levels.
Architecture:
- Modular: Composed of independent, interchangeable components, allowing customization to specific needs.
- Scalable: Accommodates projects of varying sizes and complexities.
- Cloud-Based or On-Premises: Deployable in a cloud environment for easy access or on-premises for greater control.
- API-Driven: Enables integration with existing tools and workflows.
Key Advantages:
- Shift Left Security: Integrates security testing early in the development cycle for cost-effective remediation.
- Comprehensive Coverage: Addresses various security aspects through complementary testing techniques.
- Automation and Integration: Streamlines security processes within development workflows.
- Visibility and Compliance: Provides insights for informed decision-making and demonstrates compliance.
Overall, SIP’s architecture facilitates a comprehensive and integrated approach to software security, enabling organizations to build secure and compliant software with efficiency and visibility.
How to Install Synopsys Software Integrity Platform it?
Installing the Synopsys Software Integrity Platform (SIP) involves several steps, varying based on your deployment model and chosen tools:
1. Choose Your Deployment Option:
- Cloud-Based: Synopsys hosts and maintains the platform, accessed through a web browser. This model offers ease of use, scalability, and automatic updates.
- On-Premises: Install and manage the platform within your own infrastructure for greater control and customization.
2. Contact Synopsys:
- Regardless of deployment choice, reach out to Synopsys to discuss your requirements and obtain necessary installation instructions, licenses, and access credentials.
3. Cloud-Based Deployment:
- Synopsys will provision your account and provide login details.
- No further installation is needed; access the platform through the web interface.
4. On-Premises Deployment:
- Environment Requirements: Ensure your servers meet hardware and software specifications provided by Synopsys.
- Installation Process: Follow detailed instructions from Synopsys, typically involving:
- Downloading installation packages
- Configuring network settings
- Setting up databases
- Installing and configuring individual tools
- Integration: Configure integrations with your development tools, issue trackers, and CI/CD pipelines.
5. Access and Configuration:
- Once installed, access the SIP web interface using provided credentials.
- Configure users, projects, settings, and integrations to align with your workflows and security requirements.
Tips:
- Installation complexity varies depending on chosen tools and deployment model.
- Synopsys experts can assist with installation and configuration.
- Cloud-based deployment is often simpler and faster to set up.
- On-premises deployment offers greater control and customization.
Basic Tutorials of Synopsys Software Integrity Platform: Getting Started

Now, Let’s have a look at some Basic Tutorials of Synopsys Software Integrity Platform so, I’m providing a general outline of basic steps:
1. Accessing the Platform:
- Cloud-Based: Log in to the web interface using the URL and credentials provided by Synopsys.
- On-Premises: Access the platform using the internal URL and credentials set during installation.
2. Creating a Project:
- Initiate a new project to organize your security testing efforts.
- Provide a descriptive project name and associate it with relevant applications or codebases.
3. Integrating Development Tools:
- Connect SIP with your development environment (IDEs, build systems), issue trackers, and CI/CD pipelines for seamless integration of security testing into your workflows.
- Follow specific instructions for each tool and platform.
4. Performing Static Analysis (SAST):
- Upload source code or connect to your repositories.
- Initiate SAST scans to identify potential vulnerabilities within the code itself.
- Review scan results, prioritize critical issues, and assign them for remediation.
5. Conducting Software Composition Analysis (SCA):
- Scan your codebase to identify open-source and third-party components.
- Check for known vulnerabilities and license compliance issues within these components.
- Address any risks discovered through updates, replacements, or mitigation strategies.
6. Running Interactive Application Security Testing (IAST):
- Configure IAST agents within your testing or runtime environments.
- Execute tests or use applications as usual while IAST monitors for vulnerabilities in real-time.
- Review identified issues and prioritize remediation.
7. Executing Dynamic Application Security Testing (DAST):
- Launch simulated attacks against running applications to uncover vulnerabilities that might be missed by static analysis.
- Address any discovered vulnerabilities.
8. Managing Vulnerabilities:
- Track identified vulnerabilities, prioritize them based on severity and risk, and assign them to developers for remediation.
- Re-scan code after fixes to ensure vulnerabilities have been effectively addressed.
9. Generating Reports and Dashboards:
- Utilize SIP’s reporting capabilities to create comprehensive reports on security posture, compliance status, and progress over time.
- Use dashboards to visualize key metrics and track trends.
10. Customizing and Maintaining:
- Tailor SIP’s settings, workflows, and integrations to match your specific needs and security requirements.
- Keep the platform and its tools updated with the latest security intelligence and features.
Say goodbye to the hassles of bike ownership! MotoShare.in offers affordable rentals, whether you need a scooter for errands, a bike for a road trip, or a reliable ride to explore new cities.

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
