What is Sysdig Secure?

Sysdig Secure is a container security platform that provides runtime security and forensics for containers and microservices in cloud-native environments. It helps organizations detect and respond to threats, vulnerabilities, and compliance issues in real-time.
Overall, Sysdig Secure plays a crucial role in securing containerized applications and microservices in dynamic and distributed cloud-native environments. It helps organizations proactively address security threats, vulnerabilities, and compliance requirements, while also providing the necessary tools for incident response and forensic analysis in case of security incidents.
Top 10 use cases of Sysdig Secure:
Here are the top 10 use cases of Sysdig Secure:
- Vulnerability Scanning: Sysdig Secure performs vulnerability scanning on container images to identify known security vulnerabilities in the software libraries and components used in containerized applications.
- Runtime Threat Detection: It continuously monitors containerized applications at runtime, detecting unauthorized or suspicious activities and potential security threats.
- Compliance and Policy Enforcement: Sysdig Secure enforces security and compliance policies by monitoring container configurations, runtime behavior, and deviations from established security baselines.
- Incident Response: In the event of a security incident, Sysdig Secure provides forensic capabilities, allowing organizations to investigate and analyze containerized applications to determine the root cause and extent of the incident.
- File Integrity Monitoring (FIM): It monitors file system changes within containers, ensuring that critical system files and configuration files are not tampered with or modified.
- Network Visibility and Firewalling: Sysdig Secure offers network visibility and firewalling capabilities, allowing organizations to define and enforce network policies for containers to restrict communication or detect suspicious network traffic.
- Zero Trust Security: It follows a zero-trust security model by monitoring all container activities and traffic, regardless of where containers are running, to ensure continuous security enforcement.
- Compliance Reporting: Sysdig Secure generates compliance reports for various industry standards, such as PCI DSS, HIPAA, and GDPR, helping organizations demonstrate compliance to auditors and regulators.
- Custom Security Policies: Organizations can define custom security policies tailored to their specific requirements and risk profiles, allowing for flexibility in security enforcement.
- Integration with CI/CD Pipelines: Sysdig Secure integrates with CI/CD pipelines to automatically scan container images for vulnerabilities and enforce security policies during the build and deployment process.
- Container Runtime Protection: It provides runtime protection for containerized applications, ensuring that containers are not exploited or abused by malicious actors.
- Cloud-Native Security: Sysdig Secure is designed specifically for cloud-native environments, including Kubernetes, ensuring that security measures are aligned with modern container orchestration technologies.
What are the feature of Sysdig Secure?
Sysdig Secure is a container security platform designed to provide runtime security, vulnerability management, compliance, and incident response capabilities for containerized and cloud-native environments. Here are the key features of Sysdig Secure:
- Container Image Scanning: Sysdig Secure scans container images for known vulnerabilities and provides detailed reports on identified security issues.
- Runtime Threat Detection: It continuously monitors containerized applications at runtime, detecting unauthorized activities, suspicious behaviors, and potential threats.
- Compliance Checks: Sysdig Secure enforces compliance policies based on industry standards and custom rules, helping organizations meet regulatory and security requirements.
- Incident Response: In the event of a security incident, Sysdig Secure offers forensic capabilities, allowing organizations to investigate and analyze container activity to identify the root cause and extent of the incident.
- File Integrity Monitoring (FIM): It tracks and alerts on changes to files and configurations within containers, ensuring that critical system files remain secure.
- Network Visibility: Sysdig Secure provides network visibility into container communication, helping organizations detect and respond to suspicious network traffic.
- Container Firewalling: It allows organizations to define network policies to control communication between containers, preventing unauthorized or malicious connections.
- User and Process Activity Monitoring: Sysdig Secure monitors user and process activities within containers, helping organizations detect unauthorized access or suspicious behaviors.
- Zero Trust Security Model: It follows a zero-trust security model, continuously monitoring all container activities and network traffic, regardless of the location of containers.
- Compliance Reporting: Sysdig Secure generates compliance reports for standards such as PCI DSS, HIPAA, and GDPR, simplifying compliance audits.
- Custom Security Policies: Organizations can define custom security policies to align with their specific security requirements and risk profiles.
- Integration with CI/CD Pipelines: Sysdig Secure integrates with CI/CD pipelines to scan container images during the build process, ensuring that only secure images are deployed.
- Kubernetes Security: Sysdig Secure is optimized for Kubernetes environments, providing visibility and security controls specific to container orchestration platforms.
How Sysdig Secure works and Architecture?
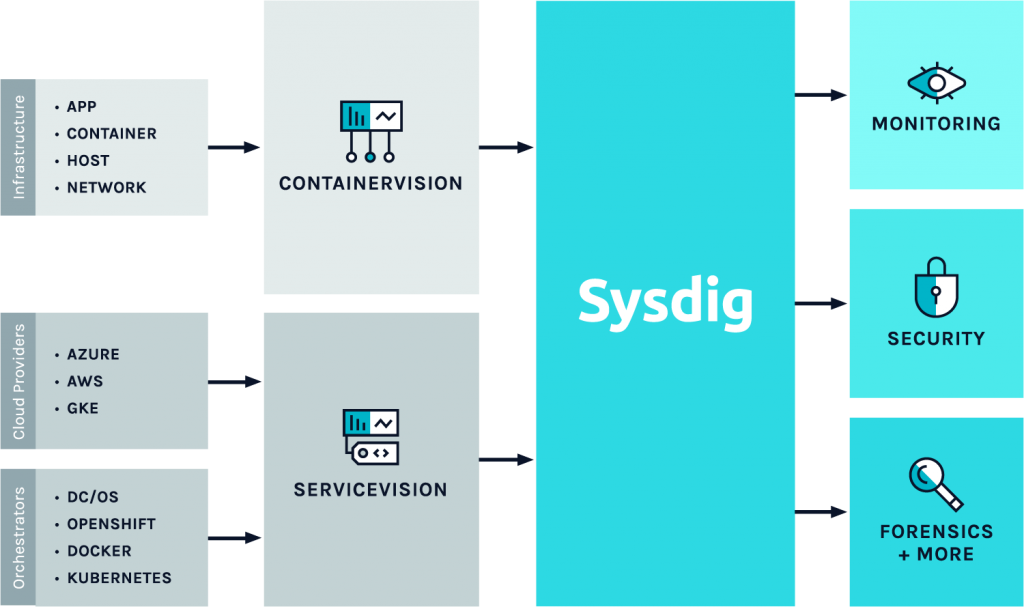
Sysdig Secure operates with an architecture that is optimized for containerized and cloud-native environments. Here’s a simplified overview of how Sysdig Secure works and its typical architecture:
Components:
- Sysdig Agent: The Sysdig Agent is deployed on each host in the environment, where it collects runtime data, including system and application metrics, network activity, and system calls.
- Sysdig Collector: The Sysdig Collector receives data from Sysdig Agents and forwards it to the Sysdig Backend for processing.
- Sysdig Backend: The Sysdig Backend processes and analyzes the collected data, running security checks, compliance assessments, and threat detection algorithms.
- User Interface: Sysdig Secure provides a user-friendly web-based interface for security monitoring, reporting, and incident investigation.
How It Works:
- Data Collection: The Sysdig Agent collects data from containers, hosts, and Kubernetes environments, including system calls, network traffic, and metrics.
- Data Forwarding: The Sysdig Collector forwards collected data to the Sysdig Backend, where it is processed and analyzed.
- Policy Evaluation: Sysdig Secure evaluates security policies, compliance checks, and runtime threats against the collected data in real-time.
- Alerting and Reporting: When a policy violation or security incident is detected, Sysdig Secure generates alerts and reports, providing visibility into security issues.
- Incident Response: In the event of a security incident, Sysdig Secure offers forensic capabilities to investigate and analyze container activity, helping organizations respond effectively.
- Integration: Sysdig Secure integrates with other tools and platforms, including Kubernetes, container registries, CI/CD pipelines, and security information and event management (SIEM) systems.
Overall, Sysdig Secure’s architecture and features are designed to address the unique security challenges presented by containerized and cloud-native environments, providing comprehensive security and compliance solutions for modern applications and microservices.
How to Install Sysdig Secure?
To install Sysdig Secure, you will need to:
- Create a Sysdig account and obtain an access key.
- Install the Sysdig Agent on your hosts and containers.
- Install the Sysdig Monitor and Sysdig Secure components.
- Connect your cloud accounts to Sysdig Secure.
Installing the Sysdig Agent
The Sysdig Agent can be installed on a variety of platforms, including Linux, Windows, macOS, and Kubernetes. To install the Sysdig Agent, you can use the following steps:
- Download the Sysdig Agent package from the Sysdig website.
- Install the Sysdig Agent package on your hosts and containers.
Installing the Sysdig Monitor and Sysdig Secure components
The Sysdig Monitor and Sysdig Secure components can be installed on-premises or in the cloud. To install the Sysdig Monitor and Sysdig Secure components, you can use the following steps:
- Download the Sysdig Monitor and Sysdig Secure packages from the Sysdig website.
- Install the Sysdig Monitor and Sysdig Secure packages on your servers.
Connecting your cloud accounts to Sysdig Secure
Sysdig Secure can be connected to a variety of cloud accounts, including AWS, Azure, and GCP. To connect your cloud accounts to Sysdig Secure, you can use the following steps:
- Log in to the Sysdig Secure web console.
- Click on the Integrations tab.
- Click on the Add Account button and select your cloud provider.
- Follow the on-screen instructions to connect your cloud account to Sysdig Secure.
Once you have installed the Sysdig Agent and Sysdig Secure components, and connected your cloud accounts to Sysdig Secure, you can start using Sysdig Secure to monitor and secure your infrastructure.
Some additional tips for installing Sysdig Secure:
- Make sure that your system meets the minimum requirements for Sysdig Secure. You can find the minimum requirements on the Sysdig website.
- If you are installing Sysdig Secure on a production system, be sure to test Sysdig Secure thoroughly before deploying it.
- If you have any questions or problems installing Sysdig Secure, please contact Sysdig Support for assistance.
Basic Tutorials of Sysdig Secure: Getting Started

The following steps are the basic tutorials of Sysdig Secure:
Creating a new Sysdig Secure policy
- Log in to the Sysdig Secure web console.
- Click on the Policies tab.
- Click on the Create Policy button.
- Enter a name and description for the new policy.
- Select the type of policy you want to create.
- Configure the policy settings.
- Click on the Create Policy button.
Running a Sysdig Secure scan
- Click on the Scans tab.
- Click on the Run Scan button.
- Select the policy you want to run the scan against.
- Click on the Run Scan button.
Viewing Sysdig Secure scan results
- Click on the Scans tab.
- Click on the scan you want to view the results for.
- The scan results will be displayed.
Remediating Sysdig Secure scan failures
- Click on the Scans tab.
- Click on the scan you want to remediate the failures for.
- Click on the Failures tab.
- Click on the Remediate button for the failure you want to remediate.
- Sysdig Secure will attempt to remediate the failure.
Some additional tips for using Sysdig Secure:
- You can use Sysdig Secure to monitor and secure your infrastructure on-premises and in the cloud.
- Sysdig Secure provides a variety of policies that you can use to monitor and secure your infrastructure for security, compliance, and performance.
- Sysdig Secure can be integrated with a variety of cloud providers, including AWS, Azure, and GCP.
- Sysdig Secure provides a variety of tools to help you remediate security vulnerabilities and compliance failures.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
