What is Thales eSecurity?

Thales eSecurity, now known as Thales CipherTrust, is a division of Thales Group that specializes in providing cybersecurity solutions for protecting sensitive data, digital identities, and critical systems. Thales eSecurity offers a wide range of products and services designed to help organizations secure their data and maintain compliance with various industry regulations.
These use cases reflect Thales eSecurity’s commitment to providing comprehensive cybersecurity solutions that address the evolving challenges of data protection, privacy, and compliance in today’s digital landscape. Their products and services are used across various industries, including finance, healthcare, government, and critical infrastructure, to safeguard sensitive information and critical systems.
Top 10 use cases of Thales eSecurity:
Here are the top 10 use cases for Thales eSecurity’s solutions:
- Data Encryption: Thales eSecurity provides encryption solutions to protect data at rest, in transit, and in use, ensuring that sensitive information remains confidential and secure.
- Key Management: Managing cryptographic keys is critical for data security. Thales eSecurity offers key management solutions to generate, store, and protect encryption keys.
- Tokenization: Tokenization replaces sensitive data with non-sensitive tokens, reducing the risk of data breaches. Thales eSecurity’s tokenization solutions help organizations secure payment card data and other sensitive information.
- Cloud Security: As organizations migrate to the cloud, Thales eSecurity helps secure data and workloads in cloud environments, ensuring data privacy and compliance.
- Hardware Security Modules (HSMs): Thales eSecurity’s HSMs are used to protect cryptographic keys and perform secure cryptographic operations. They are commonly used in financial institutions, payment systems, and critical infrastructure.
- Digital Identity and Access Management: Thales eSecurity offers solutions for managing digital identities and controlling access to systems and data, helping organizations ensure that only authorized users have access.
- Compliance and Regulatory Compliance: Thales eSecurity assists organizations in achieving compliance with industry regulations such as GDPR, HIPAA, and PCI DSS by implementing security controls and encryption.
- Secure Remote Access: With the rise in remote work, Thales eSecurity helps organizations secure remote access to networks and resources, ensuring data protection even outside the corporate perimeter.
- Secure IoT (Internet of Things): As IoT devices become more prevalent, Thales eSecurity offers security solutions to protect data and identities associated with IoT devices.
- Secure Payment Processing: Thales eSecurity’s solutions are widely used in the financial industry to secure payment transactions, including point-of-sale (POS) systems and online payments.
What are the feature of Thales eSecurity?
Thales eSecurity, now known as Thales CipherTrust, offers a range of features and capabilities designed to help organizations protect sensitive data, digital identities, and critical systems. While the specific features may vary depending on the product or solution within the Thales eSecurity portfolio, here are some common features and functionalities associated with their offerings:
- Data Encryption: Thales eSecurity provides robust encryption algorithms to protect data at rest, in transit, and in use, ensuring confidentiality and integrity.
- Key Management: Thales eSecurity offers key management solutions that include the secure generation, storage, and lifecycle management of cryptographic keys.
- Tokenization: Tokenization solutions replace sensitive data with non-sensitive tokens, reducing the risk of data breaches while retaining functionality.
- Hardware Security Modules (HSMs): Thales eSecurity’s HSMs are tamper-resistant hardware devices that protect cryptographic keys and perform secure cryptographic operations.
- Digital Identity and Access Management: Thales eSecurity solutions help organizations manage digital identities and control access to systems and data, ensuring only authorized users gain access.
- Cloud Security: Thales eSecurity provides solutions for securing data and workloads in cloud environments, supporting multi-cloud and hybrid cloud deployments.
- Secure Remote Access: Thales eSecurity solutions enable secure remote access to networks and resources, safeguarding data even when accessed outside the corporate network.
- Compliance and Regulatory Compliance: Thales eSecurity assists organizations in achieving compliance with industry regulations and standards like GDPR, HIPAA, PCI DSS, and more by implementing necessary security controls.
- IoT Security: Thales eSecurity solutions address the security challenges associated with the Internet of Things (IoT) by securing data and identities associated with IoT devices.
- Secure Payment Processing: Thales eSecurity’s solutions are widely used in the financial industry to secure payment transactions, including point-of-sale (POS) systems and online payments.
How Thales eSecurity works and Architecture?
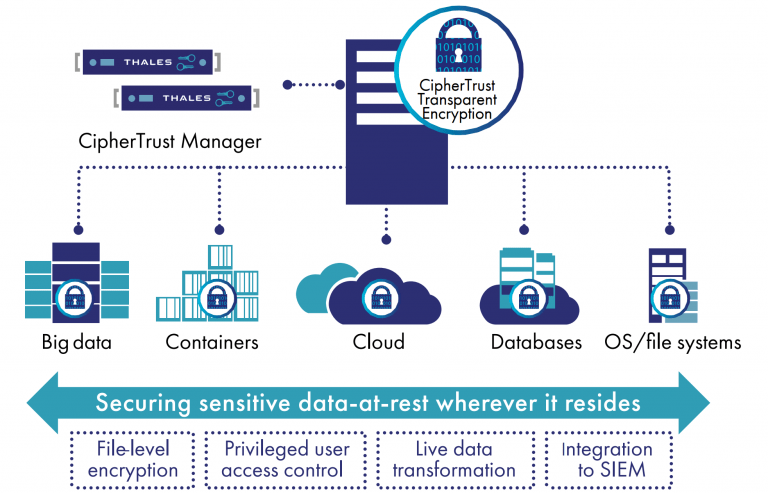
Thales eSecurity’s architecture and how it works can vary depending on the specific product or solution being used, but here’s a general overview of how their solutions typically operate:
- Encryption and Key Management: Thales eSecurity solutions encrypt data and manage cryptographic keys. Encryption ensures data confidentiality, and key management ensures the secure storage, distribution, and rotation of encryption keys.
- Tokenization: Tokenization solutions replace sensitive data with tokens, which are then stored and processed separately from the original data. This reduces the risk of data exposure in the event of a breach.
- HSMs: Hardware Security Modules (HSMs) are physical devices that protect cryptographic keys and perform secure cryptographic operations. They can be integrated into an organization’s infrastructure to ensure the security of cryptographic operations.
- Access Control and Identity Management: Thales eSecurity solutions help organizations manage user identities, authenticate users, and enforce access controls to protect critical systems and data.
- Cloud Integration: Thales eSecurity products integrate with various cloud service providers, allowing organizations to extend their security controls into cloud environments.
- Compliance and Reporting: Thales eSecurity solutions often include reporting and auditing features to demonstrate compliance with security policies and regulatory requirements.
- Secure Communication: Thales eSecurity supports secure communication protocols such as SSL/TLS to protect data transmitted over networks.
- Monitoring and Alerts: Thales eSecurity solutions monitor for suspicious activity, generate alerts, and provide insights into potential security threats.
Overall, Thales eSecurity’s architecture and solutions are designed to provide organizations with the tools and capabilities needed to protect their data, manage cryptographic assets, and ensure compliance with security standards. Specific implementations can vary depending on an organization’s needs and the Thales eSecurity products in use.
How to Install Thales eSecurity?
To install Thales eSecurity software, you will need to download the installer package from the Thales eSecurity website. The specific steps involved in the installation process will vary depending on the software product you are installing, but the general steps are as follows:
- Download the installer package. You can download the installer package from the Thales eSecurity website. Go to the product page for the software you want to install and click the “Download” button.
- Run the installer package. Once you have downloaded the installer package, double-click on it to start the installation process.
- Follow the on-screen instructions. The installer will guide you through the installation process. You will need to select a location to install the software and agree to the license terms.
- Finish the installation. Once the installation is complete, you will be able to launch the software.
Some additional things to keep in mind when installing Thales eSecurity software:
- Make sure that your system meets the minimum requirements for the software you are installing. You can find the minimum requirements on the product page for the software on the Thales eSecurity website.
- If you are installing a software product that requires a hardware security module (HSM), make sure that the HSM is properly installed and configured before you start the installation process.
- If you are installing a software product that will be used in a production environment, be sure to test the software thoroughly before you deploy it.
Here are some specific instructions for installing some popular Thales eSecurity products:
- nShield Connect
To install nShield Connect, download the nShield Connect installer package from the Thales eSecurity website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
- SafeNet ProtectToolkit-M
To install SafeNet ProtectToolkit-M, download the ProtectToolkit-M installer package from the Thales eSecurity website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
- RSA Certificate Manager
To install RSA Certificate Manager, download the RSA Certificate Manager installer package from the Thales eSecurity website. Once you have downloaded the installer package, double-click on it to start the installation process. Follow the on-screen instructions to fulfill the installation.
Basic Tutorials of Thales eSecurity: Getting Started

The following steps are the basic tutorials of Thales eSecurity:
Thales eSecurity SafeNet Protect
Step 1: Install and configure SafeNet Protect
- Download the SafeNet Protect installation package from the Thales eSecurity website.
- Run the installation package and apply the on-screen instructions to fulfill the installation.
- Once the installation is complete, open the SafeNet Protect Console.
- Create a new vault by clicking the Create Vault button and following the on-screen instructions.
Step 2: Import your encryption keys into SafeNet Protect
- You can import your encryption keys from a variety of sources, such as HSMs, file servers, and cloud storage.
- To import your encryption keys, click the Import Keys button in the SafeNet Protect Console and follow the on-screen instructions.
Step 3: Encrypt and decrypt data with SafeNet Protect
- To encrypt data, click the Encrypt button in the SafeNet Protect Console and select the file or folder that you want to encrypt.
- To decrypt data, click the Decrypt button in the SafeNet Protect Console and select the file or folder that you want to decrypt.
Step 4: Manage your encryption keys with SafeNet Protect
- SafeNet Protect provides a variety of features to help you manage your encryption keys, such as key rotation and key escrow.
- To manage your encryption keys, click the Manage Keys button in the SafeNet Protect Console.
Thales eSecurity SafeNet Token
Step 1: Enroll for a SafeNet Token
- You can enroll for a SafeNet Token through your organization’s IT department.
Step 2: Activate your SafeNet Token
- Once you have received your SafeNet Token, you will need to activate it before you can use it.
- To activate your SafeNet Token, follow the instructions that are provided with your token.
Step 3: Use your SafeNet Token for authentication
- Once your SafeNet Token is activated, you can use it to authenticate to your organization’s applications and systems.
- To use your SafeNet Token for authentication, follow the instructions that are provided by your organization’s IT department.
Step 4: Manage your SafeNet Token
- You can manage your SafeNet Token using the SafeNet Token Manager application.
- The SafeNet Token Manager application allows you to change your PIN, reset your token, and back up your token data.
Thales eSecurity SafeNet Key Manager
Step 1: Install and configure SafeNet Key Manager
- Download the SafeNet Key Manager installation package from the Thales eSecurity website.
- Run the installation package and implement the on-screen instructions to accomplish the installation.
- Once the installation is complete, open the SafeNet Key Manager Console.
- Create a new cluster by clicking the Create Cluster button and following the on-screen instructions.
Step 2: Import your encryption keys into SafeNet Key Manager
- You can import your encryption keys from a variety of sources, such as HSMs, file servers, and cloud storage.
- To import your encryption keys, click the Import Keys button in the SafeNet Key Manager Console and follow the on-screen instructions.
Step 3: Manage your encryption keys with SafeNet Key Manager
- SafeNet Key Manager provides a variety of features to help you manage your encryption keys, such as key rotation, key escrow, and audit logging.
- To manage your encryption keys, click the Manage Keys button in the SafeNet Key Manager Console.
Email- contact@devopsschool.com

 Starting: 1st of Every Month
Starting: 1st of Every Month  +91 8409492687
+91 8409492687  Contact@DevOpsSchool.com
Contact@DevOpsSchool.com
