- Edited
You can limit, or completely disable, public access from the internet to your Kubernetes cluster endpoint.
Amazon Amazon EKS creates an endpoint for the managed Kubernetes API server that you use to communicate with your cluster (using Kubernetes management tools such as kubectl). By default, this API server endpoint is public to the internet, and access to the API server is secured using a combination of AWS Identity and Access Management (IAM) and native Kubernetes Role Based Access Control (RBAC).
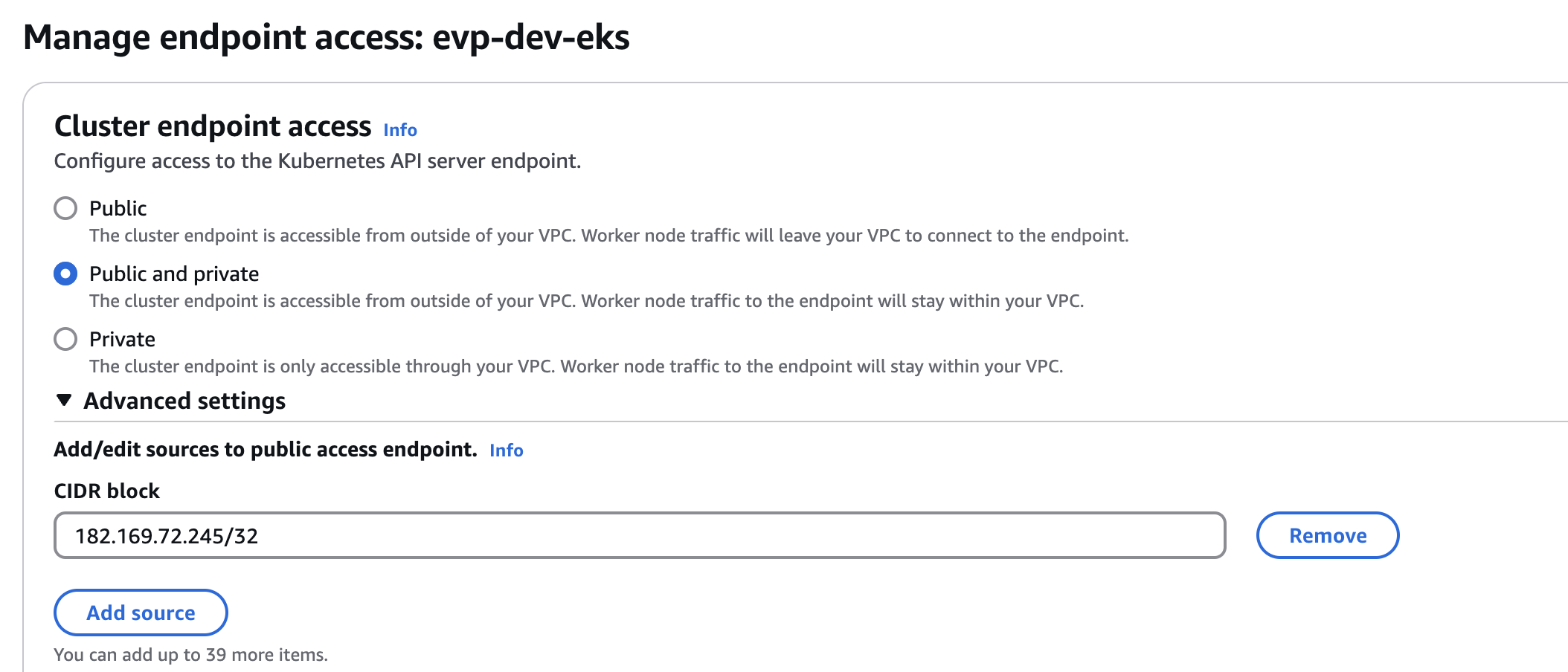
You can, optionally, limit the CIDR blocks that can access the public endpoint. If you limit access to specific CIDR blocks, then it is recommended that you also enable the private endpoint, or ensure that the CIDR blocks that you specify include the addresses that worker nodes and Fargate pods (if you use them) access the public endpoint from.
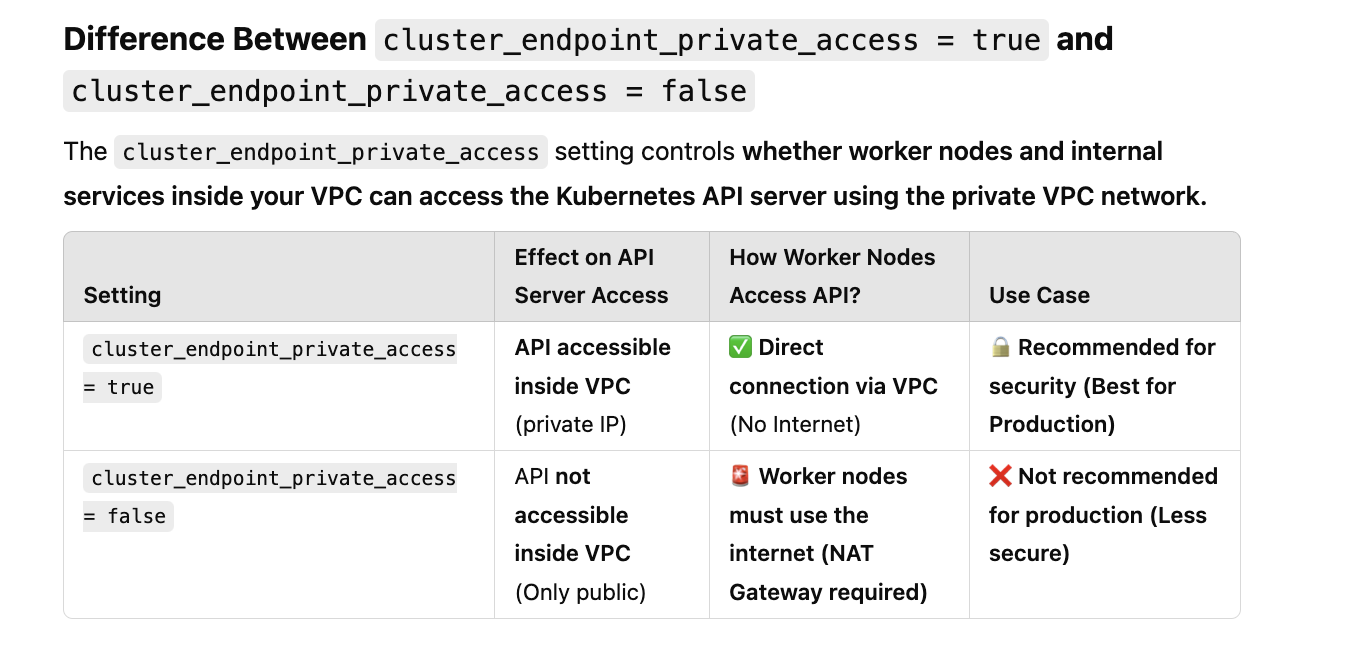
You can enable private access to the Kubernetes API server so that all communication between your worker nodes and the API server stays within your VPC. You can limit the IP addresses that can access your API server from the internet, or completely disable internet access to the API server.
Let’s break it down in simpler terms with practical examples so you fully understand EKS API access modes.
 Understanding EKS API Endpoints
Understanding EKS API Endpoints
Every EKS cluster has an API server endpoint that allows:
- kubectl and other Kubernetes tools to communicate with the cluster.
- Worker nodes to communicate with the control plane.
EKS supports three access modes:
- Public
- Public and Private
- Private
 Public API Endpoint (
Public API Endpoint ( Least Secure)
Least Secure)
 What It Means
What It Means
- The EKS API endpoint is accessible from the internet.
- Worker nodes in your VPC must connect to the API over the internet.
- You can restrict access to specific IPs (
cluster_endpoint_public_access_cidrs).
 Downsides
Downsides
- Security risk: If someone gets access to your cluster credentials, they can reach the API from anywhere (unless restricted by IP).
- Worker nodes must access API over the internet, which is less secure and increases latency.
 Example Scenario
Example Scenario
Imagine you work remotely and want to manage your EKS cluster from home.
Terraform Example:
cluster_endpoint_public_access = true
cluster_endpoint_public_access_cidrs = ["182.169.72.245/32"] This allows only your laptop's IP (
This allows only your laptop's IP (182.169.72.245/32) to access the cluster.
 Public and Private API Endpoint (
Public and Private API Endpoint ( Recommended)
Recommended)
 What It Means
What It Means
- The EKS API endpoint is accessible from the internet (for administrators).
- Worker nodes stay inside the VPC to communicate with the API server (does NOT use the internet).
- You can still restrict public access to specific IPs.
 Why It’s Recommended
Why It’s Recommended
- Admin access from outside AWS is possible.
- Worker nodes remain private (no need for internet access).
- Best balance of security and usability.
 Example Scenario
Example Scenario
Imagine:
- Your admin team works remotely and needs
kubectlaccess. - Your worker nodes should stay private and not access the API over the internet.
Terraform Example:
cluster_endpoint_public_access = true
cluster_endpoint_public_access_cidrs = ["182.169.72.245/32"] Admins can access EKS API from
Admins can access EKS API from 182.169.72.245, but worker nodes will use private networking.
 Private API Endpoint (
Private API Endpoint ( Most Secure)
Most Secure)
 What It Means
What It Means
- The EKS API endpoint is NOT accessible from the internet (only inside AWS).
- Worker nodes stay inside the VPC to communicate with the API server.
- kubectl will NOT work from outside AWS unless using a VPN, Bastion Host, or Direct Connect.
 Best for High Security
Best for High Security
- If you don’t need remote access to EKS, use this mode.
- All API traffic stays private inside AWS.
 Example Scenario
Example Scenario
Imagine:
- Your entire team works inside AWS (e.g., using AWS Workspaces or a private VPN).
- You want maximum security and do not need
kubectlfrom outside.
Terraform Example:
cluster_endpoint_public_access = false
cluster_endpoint_public_access_cidrs = [] This ensures only services inside the VPC can communicate with EKS.
This ensures only services inside the VPC can communicate with EKS.
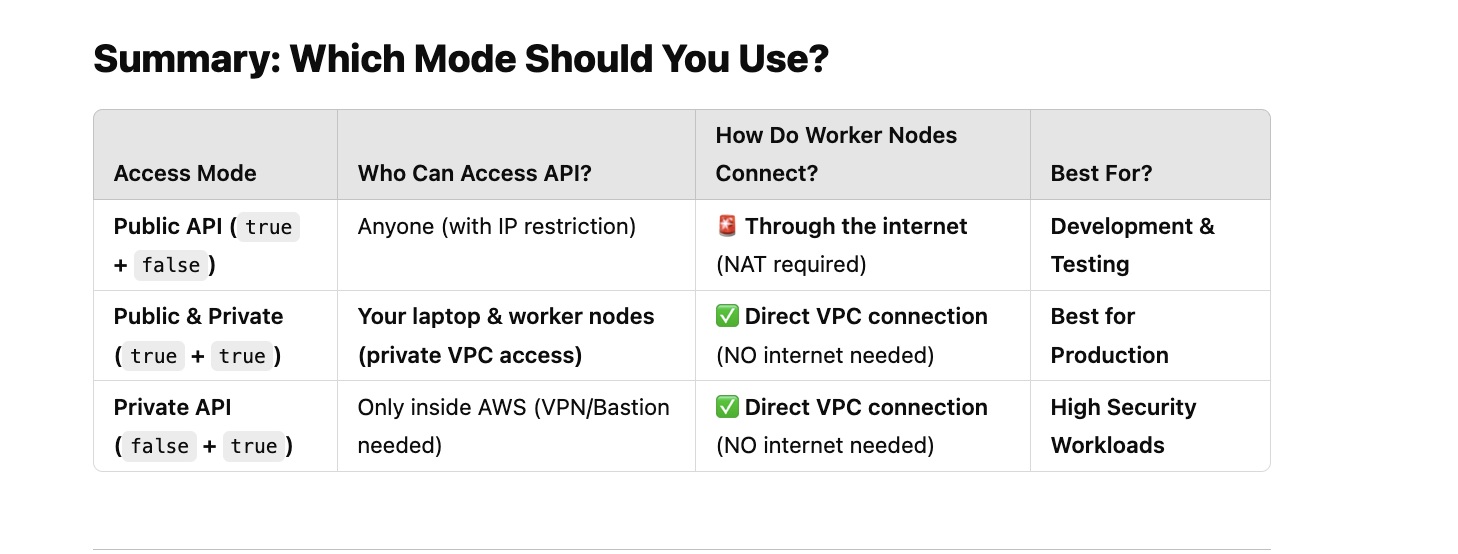
 Summary: Choosing the Right Access Mode
Summary: Choosing the Right Access Mode
| Access Mode | Who Can Access EKS API? | How Do Worker Nodes Connect? | Recommended For? |
|----------------------|--------------------------------|------------------------------|-----------------------|
| Public ( Not Secure) | Anyone on the internet (can restrict by IP) | Nodes go through the internet | Temporary setups, non-production |
Not Secure) | Anyone on the internet (can restrict by IP) | Nodes go through the internet | Temporary setups, non-production |
| Public & Private ( Recommended) | Admins via internet (with IP restriction) | Nodes stay inside the VPC | Secure, flexible access for admins & workloads |
Recommended) | Admins via internet (with IP restriction) | Nodes stay inside the VPC | Secure, flexible access for admins & workloads |
| Private ( Most Secure) | Only inside AWS (VPN, Bastion, etc.) | Nodes stay inside the VPC | High-security workloads, no internet exposure |
Most Secure) | Only inside AWS (VPN, Bastion, etc.) | Nodes stay inside the VPC | High-security workloads, no internet exposure |
 How Can You Access a Private EKS API?
How Can You Access a Private EKS API?
If you choose Private mode (cluster_endpoint_public_access = false), you can still manage the cluster using:
- Bastion Host (EC2 instance inside the VPC)
- SSH into the EC2 instance and run
kubectlfrom there.
- SSH into the EC2 instance and run
- AWS Systems Manager (SSM)
- Use
aws ssm start-sessionto access an EC2 in the VPC without needing SSH.
- Use
- VPN / AWS Direct Connect
- Connect to AWS privately and access EKS as if inside the VPC.
 Final Answer
Final Answer
- Public: You can access from your laptop, but worker nodes will communicate via the internet.
- Public & Private (Recommended): Your laptop can access, and worker nodes will stay private.
- Private: Only accessible inside AWS (VPN, Bastion, SSM).