Server Version Banner should be removed.
I’d say this is one of the first things to think about, because you don’t want to reveal your web server version. By exposing the version, you are assisting the hacker in expediting the reconnaissance process.
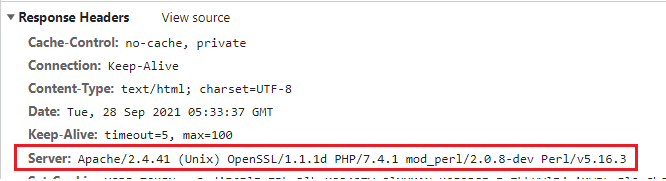
The Apache Version and OS Type will be exposed by default, as illustrated below.
- Go to the $Web Server/conf directory.
- Using the vi editor, modify httpd.conf.
- Save the httpd.conf file after adding the following directive.
ServerTokens "Prod"
ServerSignature "Off"Code language: JavaScript (javascript)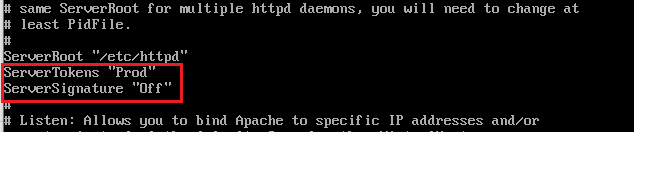
- Apache should be restarted
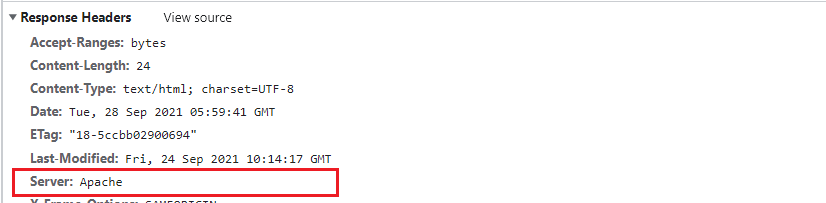
The version information in the page generated by Apache will be removed by ServerSignature.
Header will be changed to production only by ServerTokens, i.e., Apache.
As you can see in the screenshot below, the version and operating system information has vanished.
Disable the directory browser’s display.
Disable directory listing in a browser to prevent visitors from seeing all of the files and folders under the root or subdirectory.
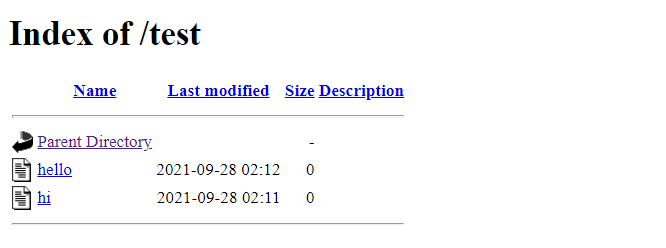
Let’s see how it looks with the default settings.
- Go to the $Web Server/htdocs directory.
- Make a folder with a few files inside it.
# mkdir test
# cd test
# touch hi
# touch helloCode language: PHP (php)Now, go to http://localhost/test and try to connect to Apache.
- Go to the $Web Server/conf directory.
- Using vi, open httpd.conf.
- Change the Options directive to None or –Indexes after you’ve added the Directory.
<Directory /opt/lampp/htdocs/test>
Options -Indexes
</Directory>Code language: HTML, XML (xml)or
<Directory /opt/lampp/htdocs/test>
Options None
</Directory>Code language: HTML, XML (xml)Note: If your environment contains multiple Directory directives, you should consider implementing the same thing for all of them.
- Restart Apache
- Now, go to http://localhost/test and try to connect to Apache.
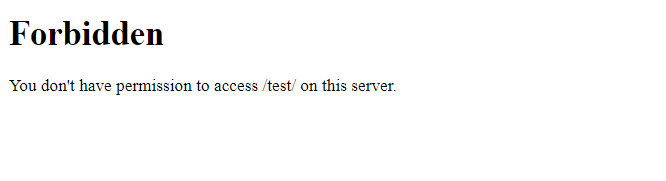
Instead of displaying the test folder listing, it displays a forbidden error.
Use a non-privileged account to run Apache.
Nobody or daemon is the default user account for a default installation. It’s a good idea to provide Apache its own non-privileged user.
The goal is to protect other services running in case of any security hole.
- Create an apache user and group.
# groupadd apache
# useradd –G apache apacheCode language: PHP (php)- Change the ownership of the apache installation directory to a newly created non-privileged user.
# chown –R apache:apache /opt/lamppCode language: PHP (php)- Go to the $Web Server/conf directory.
- Using vi, open httpd.conf
- Change the User & Group Directive to non-privileged account apache by searching for it.
User apache
Group apache- Save the httpd.conf configuration file.
- Restart Apache
- grep for running http processes and make sure they’re all running with the apache user.
# ps –ef |grep httpCode language: PHP (php)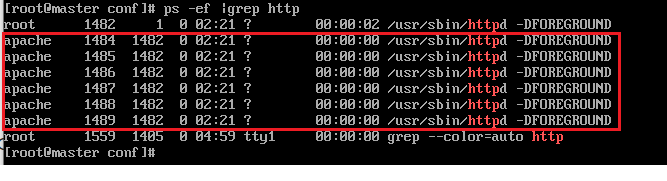
- One process should be running as root, as you can see. This is due to the fact that Apache listens on port 80 and must be run as root.
Permissions on binary and configuration directories should be protected.
The binary and configuration permissions are set to 755 by default, which implies that any user on the server may see the settings. You can deny access to the conf and bin folders to another user.
- Go to the $Web Server/conf directory.
- Bin and conf folder permissions should be changed.
chmod –R 750 bin conf
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Do you want to learn Quantum Computing?
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

