1.How important has security been in your DevOps journey?
Ans. Interviewers ask this intentionally broad question to lead job candidates into a discussion about DevOps security and to assess the importance of security in their previous DevOps work. There is no right or wrong answer, but be sure to discuss your role in the pipeline’s security goals. Best practises in code design, code evaluation and testing for known vulnerabilities, and intrusion scanning in the production environment are all examples of this. This question, along with your response, sets the tone for further, more specific inquiries.
2. How do you find and fix security flaws or vulnerabilities?
Ans. This DevSecOps interview question is designed to assess a candidate’s hands-on security experience. Respond in a way that reaffirms your fundamental understanding of security in DevOps processes and goes into greater depth about your adherence to sound security practices throughout the workflow, including how you developed those practices through team discussions and reporting. The fact that you’ve been directly involved in software development security is far more important than how you test and fix flaws.
3. What DevSecOps tools have you used?
Ans. This question assesses the candidate’s practical experience, particularly with security tools used by the prospective employer, such as those for vulnerability checks, testing, systems and change management, and intrusion detection and prevention. It is not necessary for a candidate to be an expert in every tool, but it is beneficial to be familiar with the tools used by the employer to speed up training. If the employer specifies certain tools in the job requirements, learn more about them before the interview.
4. What was the most serious security issue you had to deal with, and how did you deal with it?
Ans. Here’s the meat of the matter: Anecdotal question about a candidate’s direct involvement in a legitimate security issue. It makes no difference whether the problem is a simple buffer overflow or a malicious hack. Instead, talk about your experience in a DevOps environment with a security issue, and tell the interviewer about your specific role in the discovery and resolution of that issue. Include the steps you took to follow up, the lessons you learned, and how you adjusted processes to avoid a repeat of the problem.
5. What is the relationship between developers and operations teams when it comes to security?
Ans. Rather than security knowledge, this DevSecOps interview question focuses on a candidate’s communication and collaboration skills, which are critical in a DevOps environment. Discuss instances where you assisted in the collaborative sharing of information between teams or team members to improve security across the DevOps pipeline.
6. How do you manage segregation of duties with small Security and Development teams?
This is an excellent and frequently asked question. This is where DevOps’ value is realized if done correctly. Consider the following two possibilities:
Ans. 1. Use existing source code management platforms like GitHub to require manual code review and approval before merging new code into the main branch. As part of the code merge Pull Request, you could make this a mandatory gate, along with the requirement that the code pass all of the build checks. I’ve seen 1 to 2 mandatory approvers (another peer or manager on the dev team) used, but the size of your dev team will determine this. When a developer makes changes to infrastructure configuration, you can use Infrastructure as Code (IaC) to automate the process.
2. For pull-based deployments, use a GitOps model, which eliminates the need for human intervention. It also removes the need for any developers or operations personnel to access or make changes in production because everything is done through the pipeline. One person checks the change, separate approvers review it, and then the change is deployed in production by a machine. The only stipulation is that your organization must be mature in terms of DevOps and embrace IaC, containers, and Kubernetes. We can assist you in getting there.
7. What are your thoughts on using static code analysis (your own code) and automated software composition analysis (3rd party scans) in the deployment pipeline?
Ans. This is a big question that might be answered better offline. In general, in the last few years, this field has exploded. SAST, SCA, DAST, and other open-source tools abound, and some Dev & cloud platform vendors provide native capabilities as well. Commercial vendors are also present. In general, these tools are one-of-a-kind and should be included in your pipeline. Which ones to use, where to use them, and how to use them are all dependent on your pipeline setup, app types, programming languages they must support, and so on. However, it’s critical that you choose the right tool and use it correctly.
I’ve noticed two common issues:
1. False positives: Open-source tools, particularly SAST tools, have false positives that must be addressed. Some SAST tools could be fine-tuned, but that would take a lot of time and effort. You could use them to identify bugs early on, but be prepared to sort through the results and eliminate false positives. I don’t recommend using SAST tools as the source of truth and failing the build until all issues have been resolved and the tools are in a usable state. If at all possible, IAST should be used for a more accurate result.
2. False negatives: False negatives are a problem with open-source tools and newly created tools by Dev and cloud platforms. Developers often use these tools in the mistaken belief that they are protected, but this creates a false sense of security. While I do not advocate limiting the tools that developers use, I do advocate for good commercial tools for security reasons.
SCA tools are much more user-friendly. They should be used, and they should be used early in the deployment process. When developers are researching open-source components, some tools now have browser plugins that can identify and flag vulnerable code libraries. Most SCA tools also integrate with IDEs for early detection and code repository integration prior to the build phase. Make the most of it. Commercial SCA vendors are also working on a slew of new and exciting features.
8. Would you recommend starting DevSecOps now, or waiting until we reach a certain level of maturity, if your organization is still in the early stages of DevOps?
Ans. Even if DevOps is in its infancy, you should start DevSecOps concurrently to ensure that security is aligned with your DevOps efforts from the start. If your teams are well-aligned, you can use each other’s strengths and resources to become powerful force multipliers and scale together. You might be surprised to learn that security and DevOps have a lot in common. We’re currently working on a DevSecOps transformation project, and both the security and DevOps leadership teams are in the early stages of developing a programme. We’ve been assisting them with the development of this programme from the ground up, and having both DevOps and Security leadership on the steering committee and closely aligned is a big part of their success.
9. Which should I put first: development or operations?
Ans. This is highly dependent on the organisation and its culture. Ops is frequently the source of DevOps initiatives. However, if security and operations are closely aligned early on, it can be a powerful force multiplier. For example, observability and consistency, which are important to Ops, are also important to security. It may be easier to use real data to have conversations with Dev if you can achieve some security observability by partnering with Ops (such as seeing real-world attacks against the app or identifying gaps in cloud environments as a result of dev team misconfigurations).
There are other options. We’ve worked with app teams that are eager to learn about and improve security (assuming there are no historical frictions and the conversations are conducted correctly) and are actively seeking advice on how to do so. When this happens, it may indicate that things are moving in the right direction and that developers are concerned about code quality, including security.
10. What is DevOps and DevSecOps?
Ans: DevOps, also known as DevSecOps, is a software development philosophy with the primary goal of reducing mean-time-to-change (MTTC) and mean-time-to-recovery (MTTR) for moving new features or bug fixes into production as quickly as possible.
11. When it comes to DevOps and DevSecOps, what’s the difference?
Ans. The main difference is that DevOps requires Developers and IT/OPs staff members to collaborate as a single team with shared sprint goals, whereas DevSecOps requires Developers, IT/OPs, and Security staff to collaborate as a single team with shared sprint goals. Another significant difference is the use of security-related tools at various stages of the SDLC to automate security testing.
12. How do you get started with DevOps projects?
Ans. To get started with DevOps or DevSecOps initiatives in your organization, you’ll need to go through various steps such as assessment, gap analysis, maturity model, project implementation roadmap, and so on.
13. What metrics would you use to assess the success of DevOps adoption across the organization?
Ans: The primary metric for determining DevOps success is to look at the following:
A.Mean-Time-to-Change (MTTC)
B. Recovery Mean Time (MTTR)
C. Release frequency
14. Could you provide an example of a DevOps maturity model?
Ans: The following are some of the stages that an organization might consider moving through in order to achieve success with a DevOps or DevSecOps rollout:
A. Ad-Hoc: Complete ad-hoc tasks on-demand, such as build automation and environment provisioning automation.
B. Organized or Planned: Create a DevOps project roadmap; as part of this, select development methodologies, teams, tools, and frameworks to be used, as well as required team training and mentoring.
C. Align & Assess: Create a proof-of-concept for one or two teams that covers key DevOps implementation aspects. Learn from your mistakes and make changes to the plan so that it can be used for a large-scale rollout across multiple teams within the company.
D. Institutionalization: DevOps/DevSecOps implementation should be rolled out across the organization’s various teams.
E. Continuous Improvement: Apply what you’ve learned and keep improving your DevOps processes.
15. Many people talk about forming a DevOps team to implement DevOps in their company. What are your feelings about this relationship?
Ans: It is not possible to form a separate DevOps team. This is due to the fact that DevOps is a software development philosophy that requires developers and IT/OPs staff to collaborate as a single team with shared Sprint (Agile SCRUM) goals. As a result, the product team is restructured to follow the DevOps or DevSecOps philosophy. The following diagram depicts the various aspects of product teams being transformed to work according to the DevOps philosophy.
16. What are some of the DevOps Architect’s responsibilities?
Ans: A DevOps Architect’s responsibilities may include the following:
A. Create a pipeline for continuous delivery.
B. Create a strategy for implementing DevOps across multiple teams.
C. Be in charge of the DevOps implementation.
D. Outline the technologies that will be used to implement DevOps. These technologies could be related to various aspects of automation, such as build, deployment, and environment provisioning, among others.
17. Is it possible to achieve DevOps without establishing continuous delivery systems and processes?
Ans. Yes, that is correct. Ad-hoc automation of build, deployment, and environment provisioning processes could be used to achieve DevOps with the primary goal of lowering MTTC and MTTR.
18. DevOps is frequently linked to Docker technology, right? What are your feelings about this relationship?
Ans: DevOps does not necessitate the use of Docker technology to achieve its primary goal. The fact that cloud-native apps with Docker as the underlying technology can be used for automated environment provisioning and deployment across multiple environments, including cloud services, makes it a very useful technology for DevOps adoption.
19. What are some of the technologies that are used in DevOps?
Ans: Some of the technologies that could be used for DevOps implementation are as follows:
A. Automated provisioning of environments using configuration management tools such as Chef, Puppet, and Ansible.
B. Tools for continuous integration, such as Jenkins
C. Code repositories like Github
D. Container technologies like Docker and Kubernetes, among others
E. Artifacts repository software like Nexus Repository Manager, JFrog Artifactory, and others.
20. Explain the various stages of the continuous software delivery model.
Ans: Some of the stages of the continuous delivery model are as follows:
A. Developers check in code, which causes WebHooks to be activated, triggering CI Builds.
B. App compilation and deployment artefact creation
C. Uploading deployment artefacts to artifactories
D. Provisioning of a test environment and
E. Deployment of app artefacts across multiple test environments
F. Production deployment of app artefacts
21. How would you go about architecting a Docker-based continuous delivery solution?
Ans: The following are some key points to consider when architecting a Docker-based continuous delivery solution:
A. Arrange the apps for dockerization or containerization. This may necessitate thinking about microservices architecture.
B. Consideration of Docker for provisioning development and test environments
C. Setting up a Docker container registry on-premises or in the cloud (for example, AWS ECR)
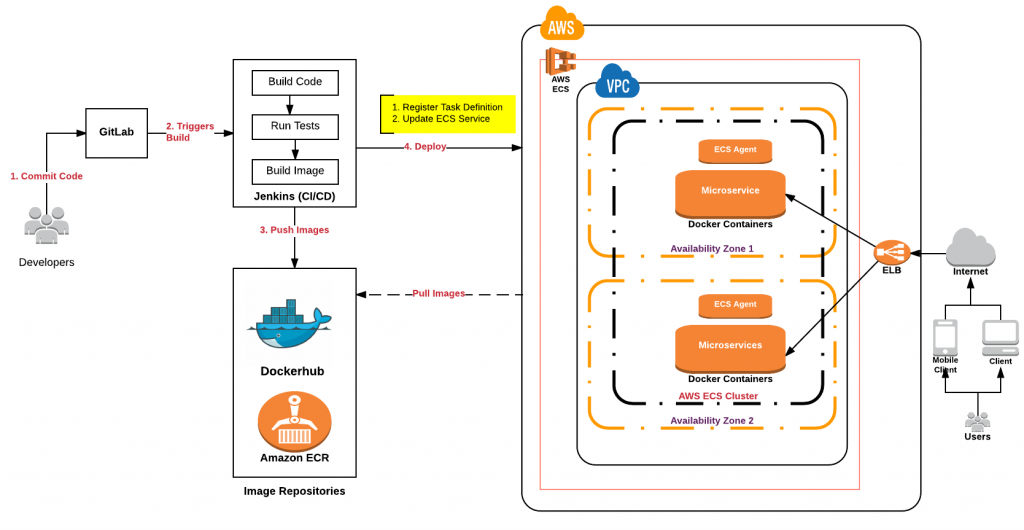
22. Could you design an AWS cloud-based continuous delivery solution for software updates?
Ans: On one of my Github pages, Continuous Delivery of Microservices on AWS, I have a detailed write-up on continuous delivery on AWS ECS and AWS EC2. The continuous delivery reference architecture for AWS is depicted in the diagram below.
23. What is the difference between Agile software development and DevOps or DevSecOps software development?
Ans. The inclusion of IT/OPs and Security staff members in Agile teams, resulting in sprint goals that include stories for both IT/OPs and security staff members, is the primary difference between traditional Agile and DevOps/DevSecOps teams. What’s more, the definition of DONE shifts. The definition of DONE in Agile SCRUM development is creating demonstrable software/artifacts at the end of the sprint. The definition of DONE in an Agile SCRUM team following the DevOps/DevSecOps philosophy shifts to creating demonstrable software/artifacts in a production-like environment at the end of the sprint.
24. Describe the various stages of DevSecOps and the tools that could be used at each stage.
Ans: Security tools could be used for security-related automation in the continuous delivery cycle at the following stages of the SDLC:
A. Scanning of source code: CheckMarx, Gitrob
B. Scans and tests: Evident.IO, GauntLT, and Contrast
C. Artifacts: Sonatype, Nessus, and Tanium
D. Deploy: Beaker, INSPEC
E. Monitoring: Splunk, Evident.io, FireEye, and Metasploit
You learned about some of the questions and answers in this post that you can use to prepare for the DevOps Architect Interview. DevOps and DevSecOps concepts, continuous delivery concepts and reference architecture, related tools and frameworks, and DevOps reference implementation are all important areas to concentrate on.

