What MySQL integration collects and sends?
NewRelic MySQL integration collects and sends inventory and metrics from your MySQL database to our platform, where you can see the health of your database server and analyze metric data so that you can easily find the source of any problems.
Compatibility and requirements
- MySQL version 5.6 or higher.
- Install the infrastructure agent
- Install infrastructure on-host integrations
Our MySQL integration uses the New Relic Infrastructure agent to collect and send performance metrics from your MySQL database to our platform. You can see your database server’s health and analyze metric data so that you can easily find the source of any problems
Install and Configure Mysql Server in Centos
- CENTOS – How to Install MySQL on CentOS 7
- UBUNTU with Xampp – Alternate – You may use XAMPP as well. How to install and Configure XAMPP on Ubuntu?
- MySql with XAMPP – How to Install & configure Xampp with mysql in Linux?
- Ubuntu – How To Install MySQL server and client on Ubuntu?
What is “infrastructure on-host integrations”?
New Relic’s on-host integrations are a type of infrastructure integration that collect data from core services running on your hosts, such as MySQL, Apache, or Redis, among others.
To collect data from on-host services, all you need are two things: the infrastructure agent, and the on-host integrations. All on-host integrations require that our infrastructure agent is installed on the host. Besides collecting system’s data, the agent acts as a forwarder for integrations’s data, and can forward logs.
Centos / RHEL – Install infrastructure on-host integrations for mysql in linux?
$ sudo yum -q makecache -y --disablerepo='*' --enablerepo='newrelic-infra'
$ sudo yum install nri-mysql
$ sudo systemctl restart newrelic-infra
# From the command line, create a user newrelic@localhost with a specific password by running:
$ sudo mysql -e "CREATE USER 'newrelic'@'localhost' IDENTIFIED BY $YOUR_PASSWORD WITH MAX_USER_CONNECTIONS 5;"
# Grant replication privileges to newrelic@localhost, with a maximum of 5 connections, by running:
$ sudo mysql -e "GRANT REPLICATION CLIENT ON *.* TO 'newrelic'@'localhost' WITH MAX_USER_CONNECTIONS 5;"
# Grant privileges to newrelic@localhost, with a maximum of 5 connections, by running:
$ sudo mysql -e "GRANT SELECT ON *.* TO 'newrelic'@'localhost' WITH MAX_USER_CONNECTIONS 5;"
# Change the directory to the integration's folder.
$ cd /etc/newrelic-infra/integrations.d
$ sudo cp mysql-config.yml.sample mysql-config.yml
# Edit the configuration file mysql-config.yml as explained in the next section.
$ vi mysql-config.yml
$ Restart the infrastructure agent.
Ubuntu – Install infrastructure on-host integrations for mysql in linux?
$ sudo apt-get install nri-mysql -y
$ sudo systemctl restart newrelic-infra
# From the command line, create a user newrelic@localhost with a specific password by running:
$ sudo mysql -e "CREATE USER 'newrelic'@'localhost' IDENTIFIED BY $YOUR_PASSWORD WITH MAX_USER_CONNECTIONS 5;"
# Grant replication privileges to newrelic@localhost, with a maximum of 5 connections, by running:
$ sudo mysql -e "GRANT REPLICATION CLIENT ON *.* TO 'newrelic'@'localhost' WITH MAX_USER_CONNECTIONS 5;"
# Grant privileges to newrelic@localhost, with a maximum of 5 connections, by running:
$ sudo mysql -e "GRANT SELECT ON *.* TO 'newrelic'@'localhost' WITH MAX_USER_CONNECTIONS 5;"
# Change the directory to the integration's folder.
$ cd /etc/newrelic-infra/integrations.d
$ sudo cp mysql-config.yml.sample mysql-config.yml
# Edit the configuration file mysql-config.yml as explained in the next section.
$ vi mysql-config.yml
$ Restart the infrastructure agent.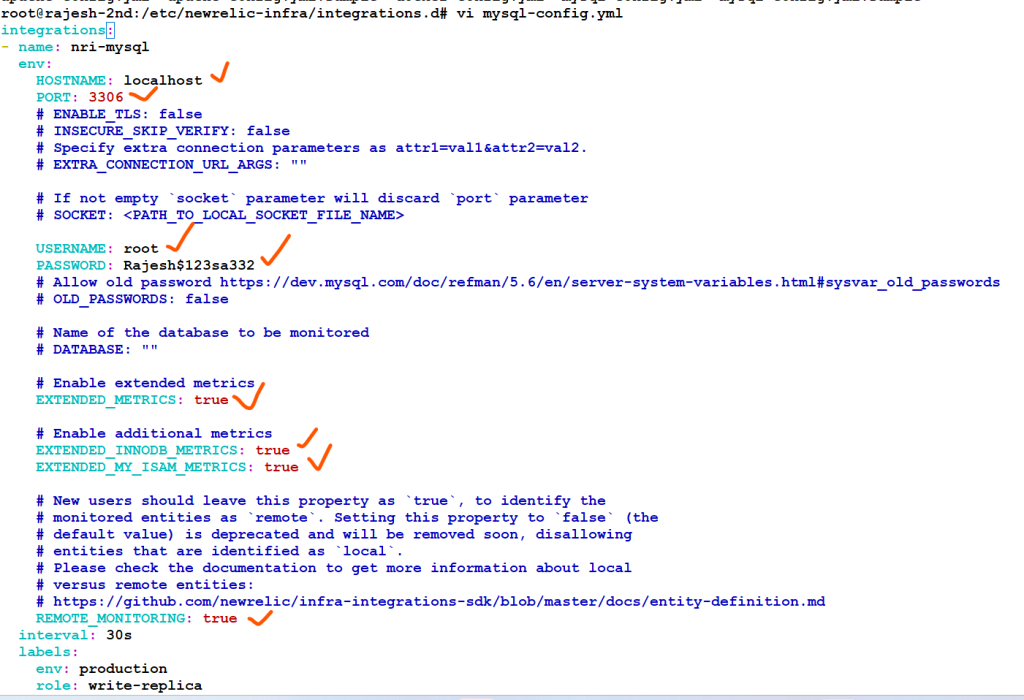
Reference
- https://docs.newrelic.com/docs/integrations/host-integrations/installation/install-infrastructure-host-integrations/
- https://docs.newrelic.com/docs/integrations/host-integrations/host-integrations-list/mysql-monitoring-integration/
| This configuration collects metrics every 30 seconds and inventory every 60 seconds: | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production | |
| - name: nri-mysql | |
| env: | |
| INVENTORY: true | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| REMOTE_MONITORING: true | |
| interval: 60s | |
| labels: | |
| environment: production | |
| inventory_source: config/mysql |
| Use to connect to MySQL with TLS. You can add TLS_INSECURE_SKIP_VERIFY : true to disable the server name verification: | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| USE_TLS: true | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production |
| Use to connect to MySQL with TLS. You can add TLS_INSECURE_SKIP_VERIFY : true to disable the server name verification: | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| USE_TLS: true | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production |
| Use to connect to MySQL using a socket file. This is an alternative to a TCP Hostname/Port connection: | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| SOCKET: /var/run/mysql/mysql.sock | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production |
| Use this to collect your metrics including extended, slave, innodb and my-isam metrics: | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| EXTENDED_METRICS: true | |
| EXTENDED_INNODB_METRICS: true | |
| EXTENDED_MY_ISAM_METRICS: true | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production |
| Use this if you need to collect metrics from two different MySQL servers using the the same integration. | |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: mysql_host1 | |
| PORT: 3306 | |
| USERNAME: mysql1_user | |
| PASSWORD: mysql1_password | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production | |
| - name: nri-mysql | |
| env: | |
| METRICS: true | |
| HOSTNAME: mysql_host2 | |
| PORT: 3306 | |
| USERNAME: mysql2_user | |
| PASSWORD: mysql2_password | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| USERNAME: mysql_user | |
| PASSWORD: mysql_password | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| environment: production | |
| inventory_source: config/mysql |
| integrations: | |
| - name: nri-mysql | |
| env: | |
| HOSTNAME: localhost | |
| PORT: 3306 | |
| # ENABLE_TLS: false | |
| # INSECURE_SKIP_VERIFY: false | |
| # Specify extra connection parameters as attr1=val1&attr2=val2. | |
| # EXTRA_CONNECTION_URL_ARGS: "" | |
| # If not empty `socket` parameter will discard `port` parameter | |
| #SOCKET: <PATH_TO_LOCAL_SOCKET_FILE_NAME> | |
| USERNAME: newrelic | |
| PASSWORD: RAJU%234 | |
| # Allow old password https://dev.mysql.com/doc/refman/5.6/en/server-system-variables.html#sysvar_old_passwords | |
| # OLD_PASSWORDS: false | |
| # Name of the database to be monitored | |
| # DATABASE: "" | |
| # Enable extended metrics | |
| # EXTENDED_METRICS: false | |
| # Enable additional metrics | |
| # EXTENDED_INNODB_METRICS: false | |
| # EXTENDED_MY_ISAM_METRICS: false | |
| # New users should leave this property as `true`, to identify the | |
| # monitored entities as `remote`. Setting this property to `false` (the | |
| # default value) is deprecated and will be removed soon, disallowing | |
| # entities that are identified as `local`. | |
| # entities that are identified as `local`. | |
| # Please check the documentation to get more information about local | |
| # versus remote entities: | |
| # https://github.com/newrelic/infra-integrations-sdk/blob/master/docs/entity-definition.md | |
| REMOTE_MONITORING: true | |
| interval: 30s | |
| labels: | |
| env: production | |
| role: write-replica | |
| inventory_source: config/mysql |
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Do you want to learn Quantum Computing?
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

