If you want to control traffic flow at the IP address or port level (OSI layer 3 or 4), then you might consider using Kubernetes NetworkPolicies for particular applications in your cluster. NetworkPolicies are an application-centric construct which allow you to specify how a pod is allowed to communicate with various network “entities” (we use the word “entity” here to avoid overloading the more common terms such as “endpoints” and “services”, which have specific Kubernetes connotations) over the network. NetworkPolicies apply to a connection with a pod on one or both ends, and are not relevant to other connections.
The entities that a Pod can communicate with are identified through a combination of the following 3 identifiers:
- Other pods that are allowed (exception: a pod cannot block access to itself)
- Namespaces that are allowed
- IP blocks (exception: traffic to and from the node where a Pod is running is always allowed, regardless of the IP address of the Pod or the node)
When defining a pod- or namespace- based NetworkPolicy, you use a selector to specify what traffic is allowed to and from the Pod(s) that match the selector.
Meanwhile, when IP based NetworkPolicies are created, we define policies based on IP blocks (CIDR ranges).
Sample Code – https://github.com/devopsschool-sample-programs/kubernetes-network-policy-recipes
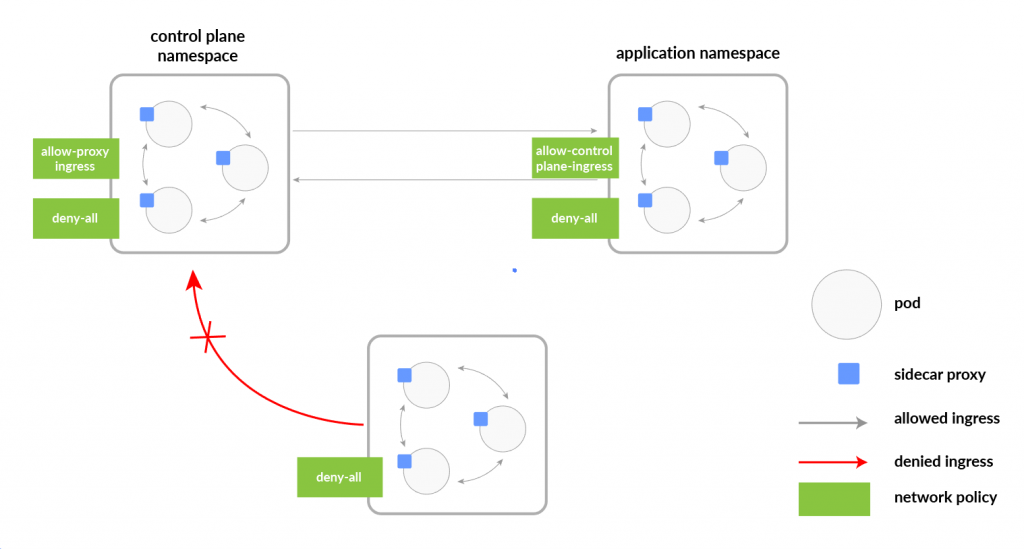
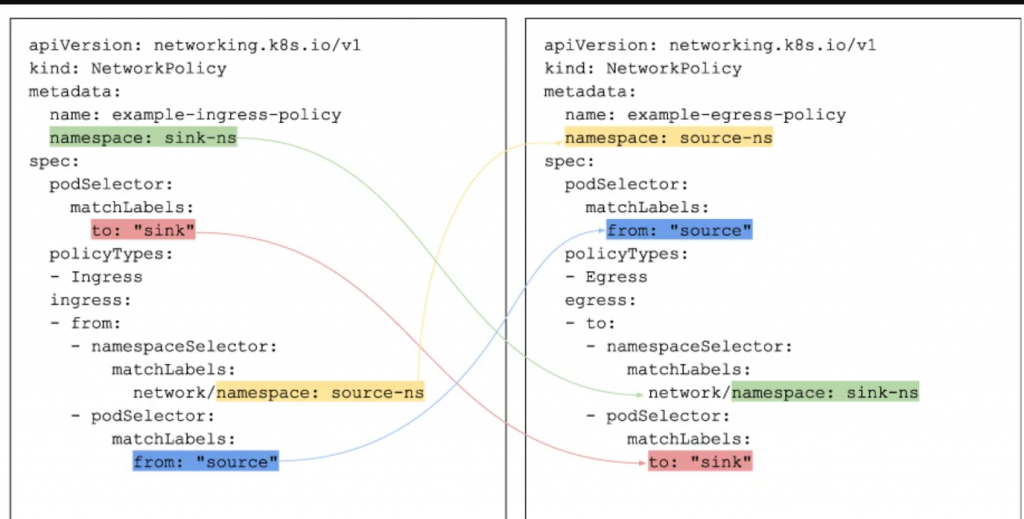
Example Use Cases
Below is a brief list of common use cases for Network Policies. You can find more use case examples with sample manifests at the kubernetes-networkpolicy-tutorial on GitHub.
- DENY all traffic to an application
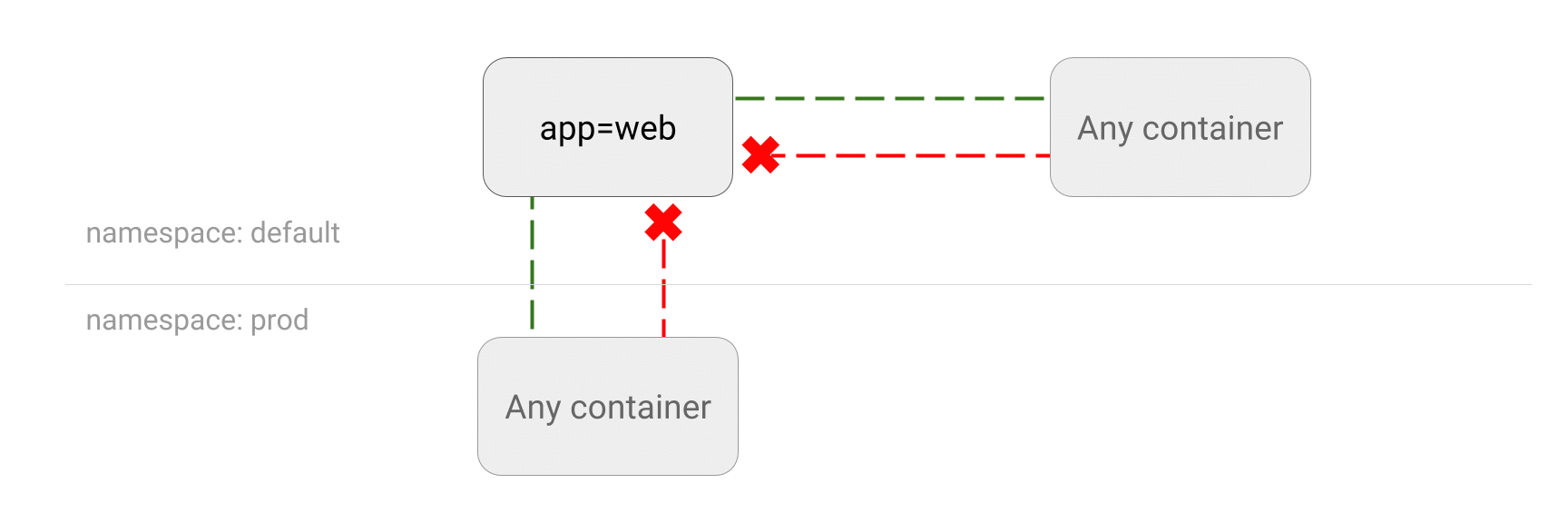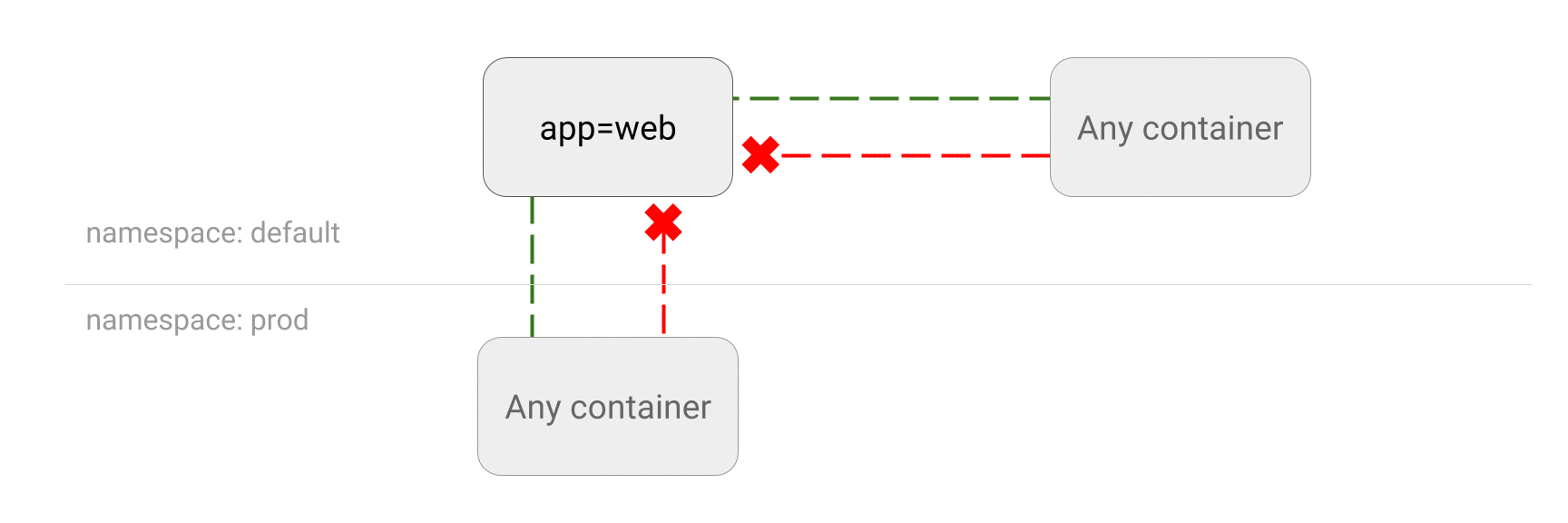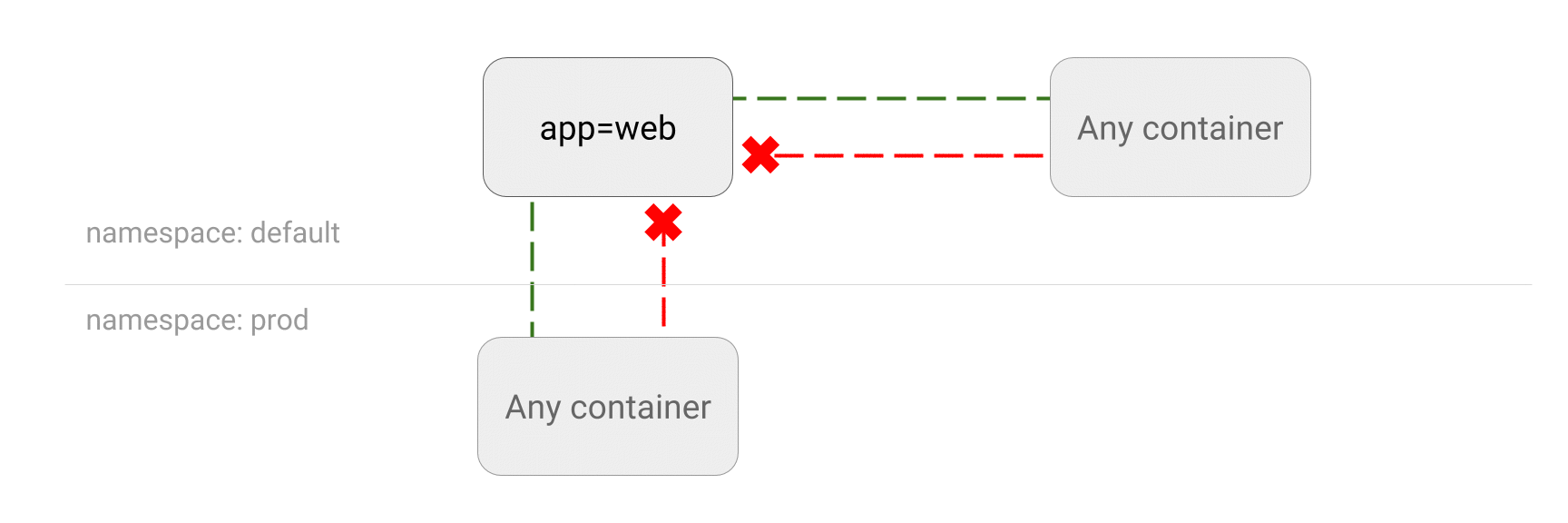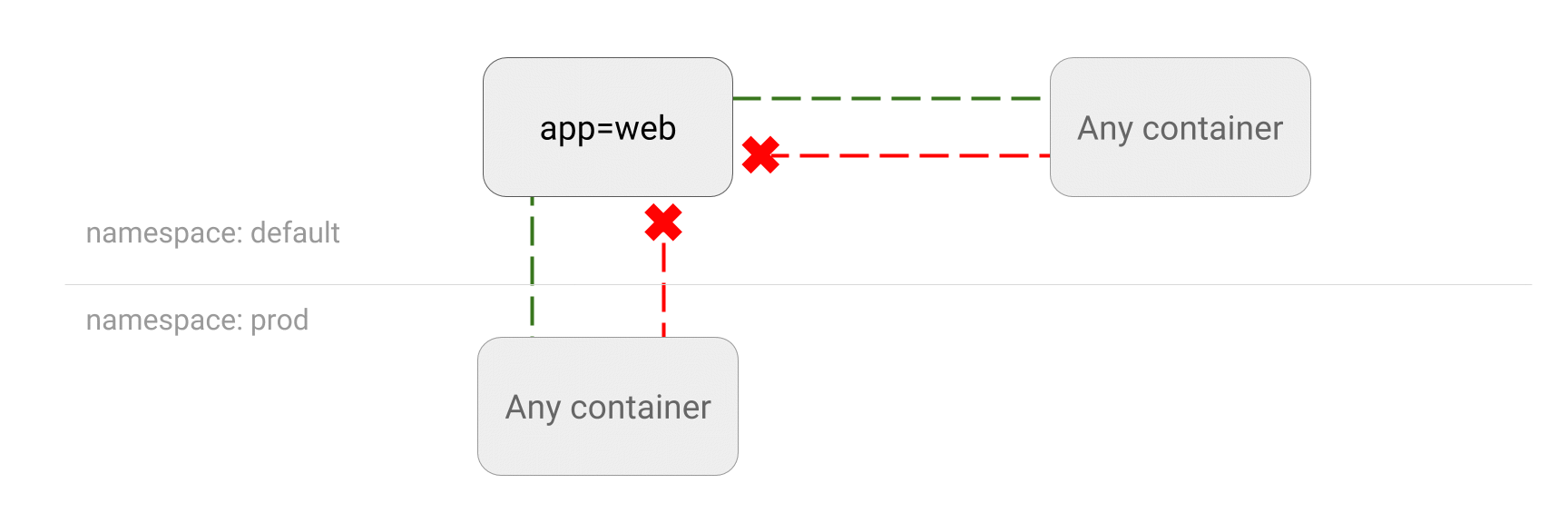
- LIMIT traffic to an application
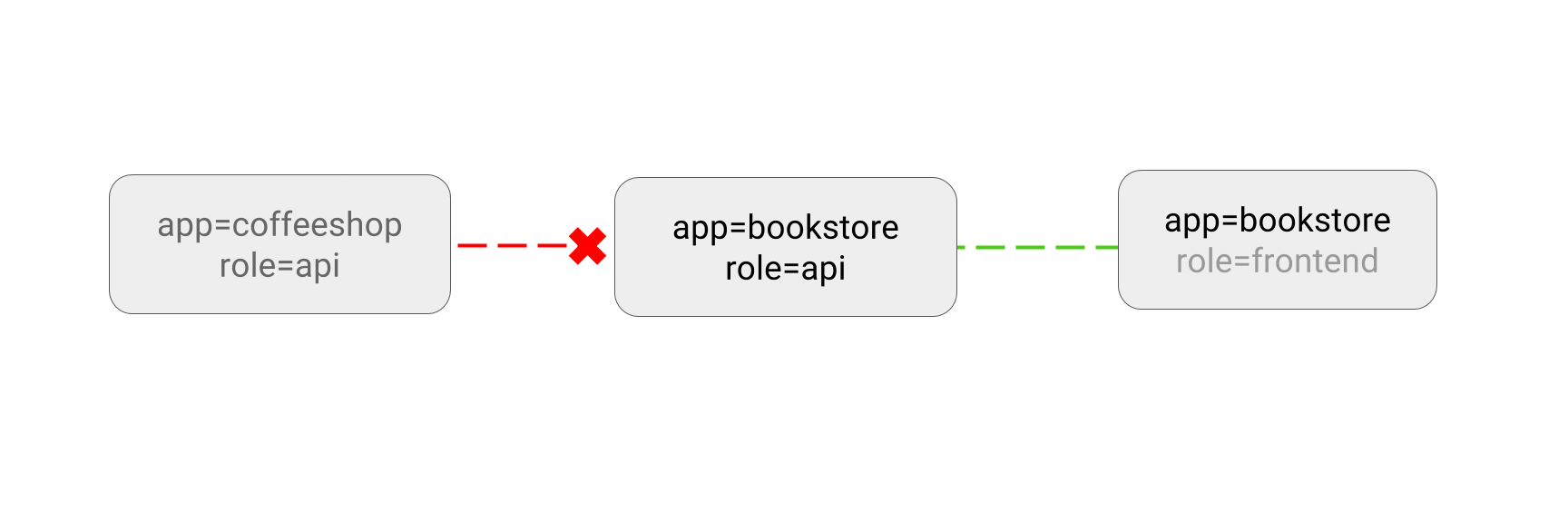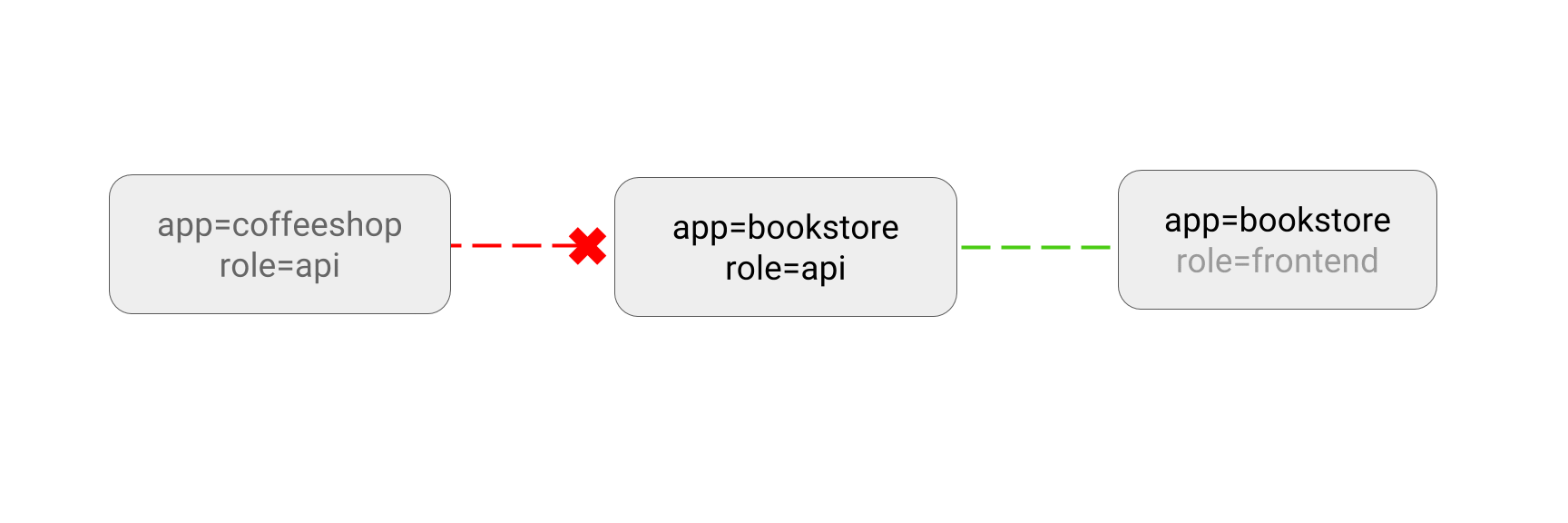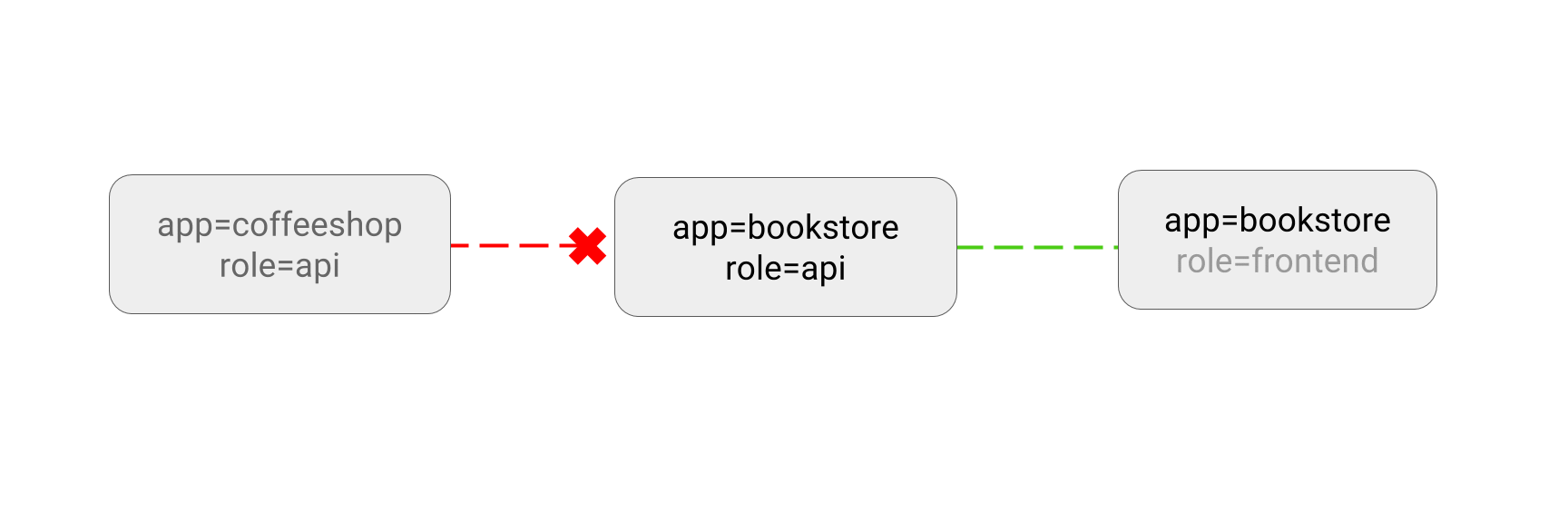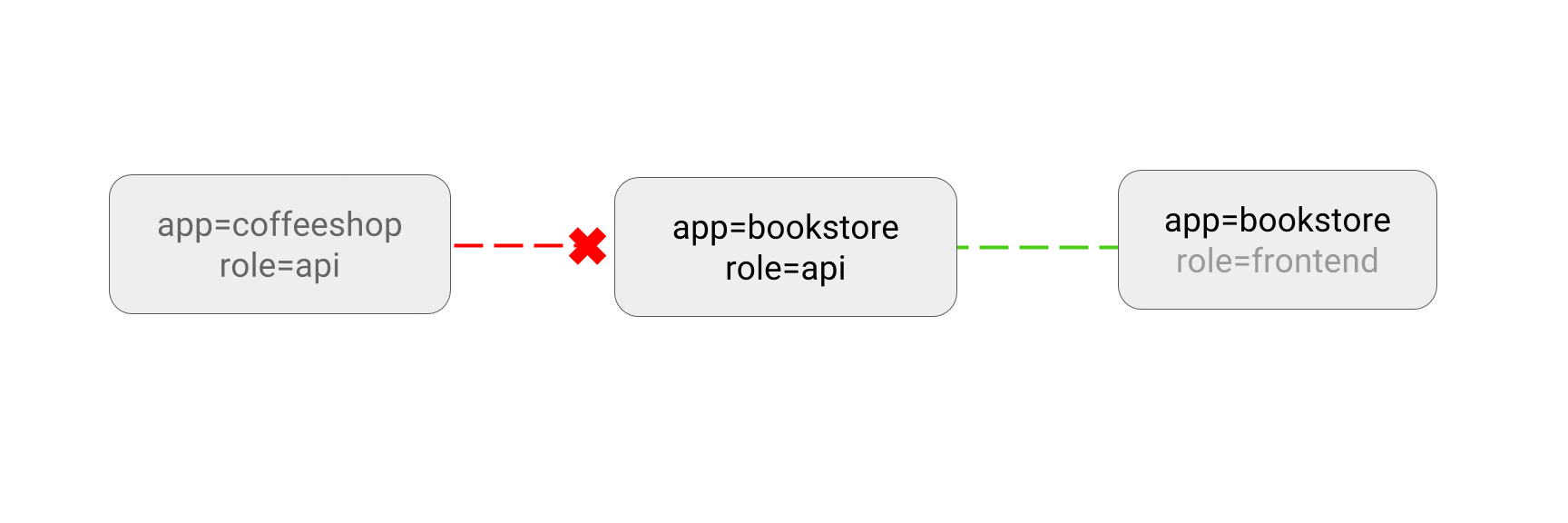
- DENY all non-whitelisted traffic in a namespace
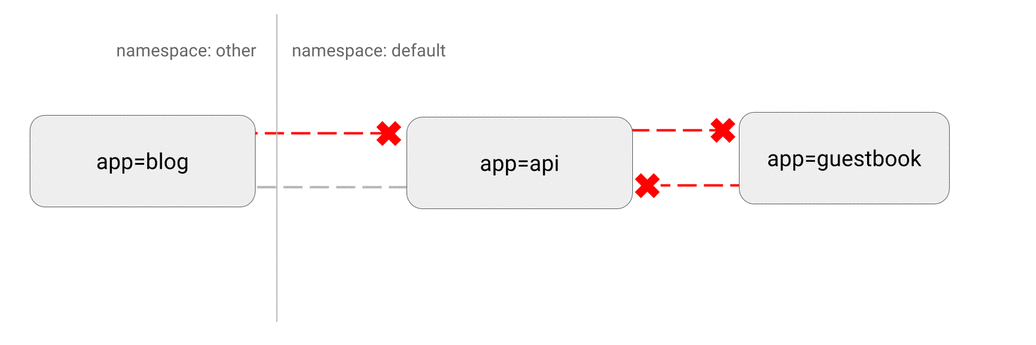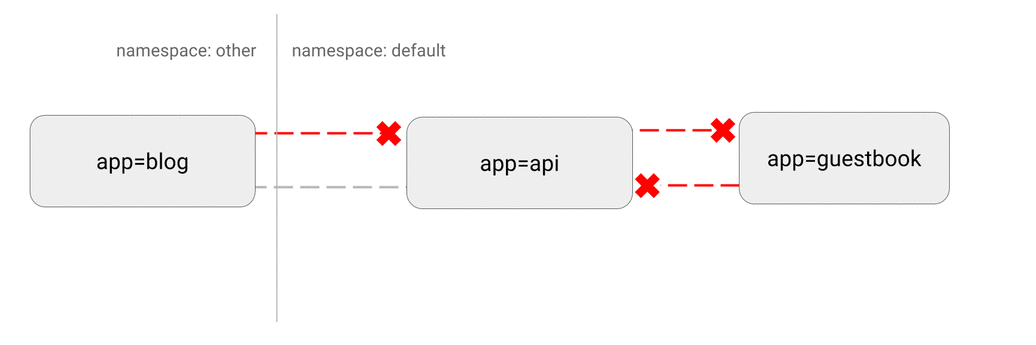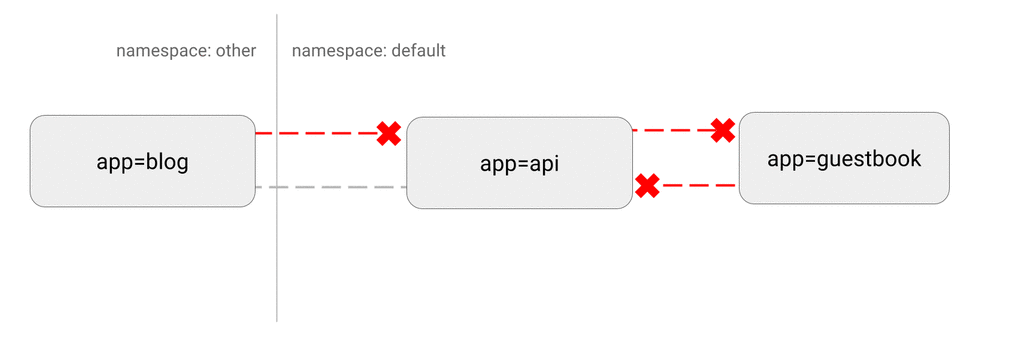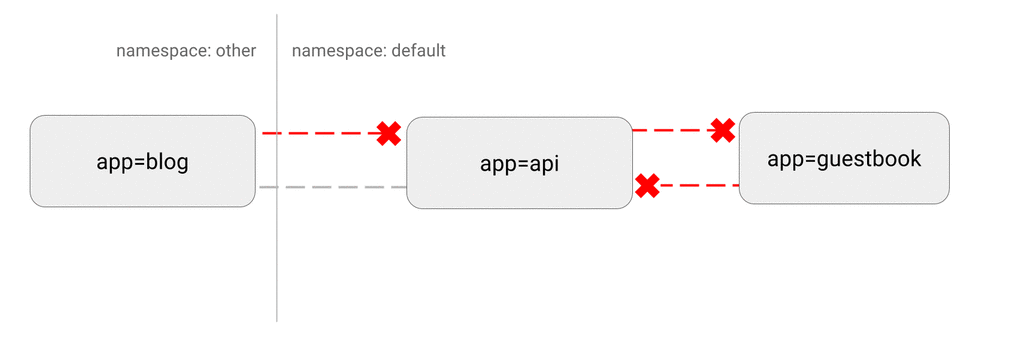
- DENY all traffic from other namespaces
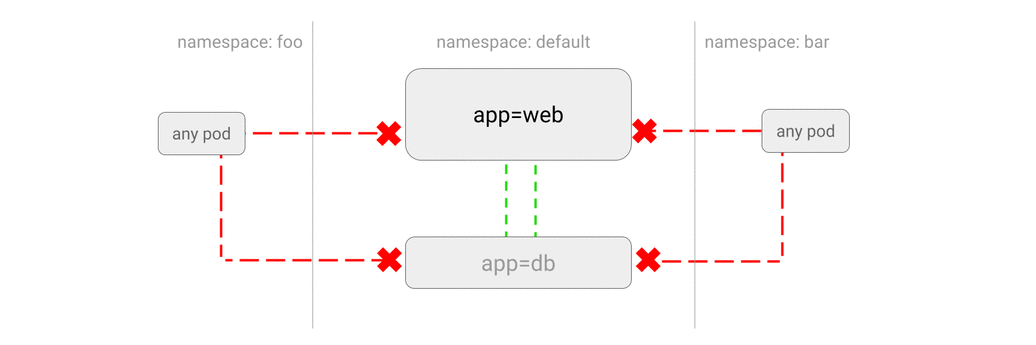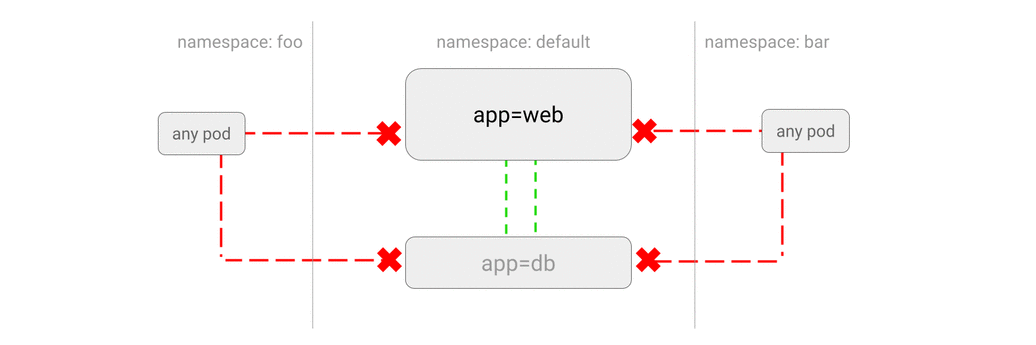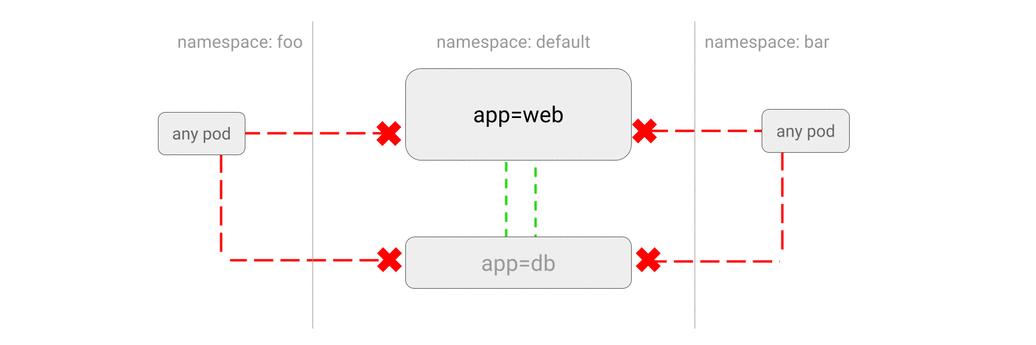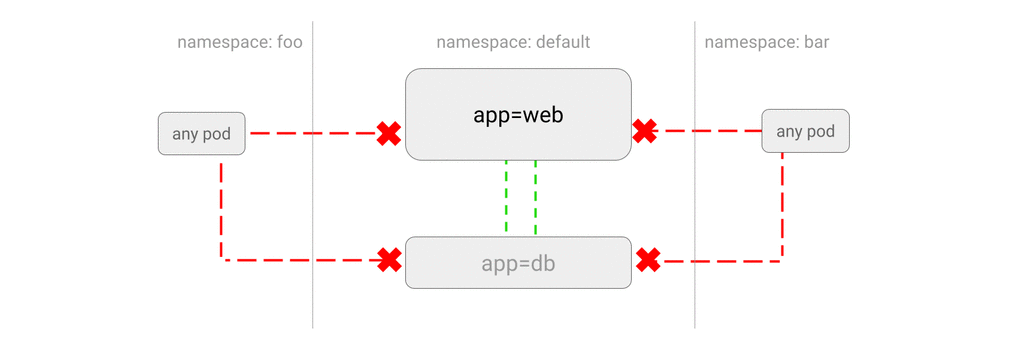
- ALLOW traffic from other namespaces
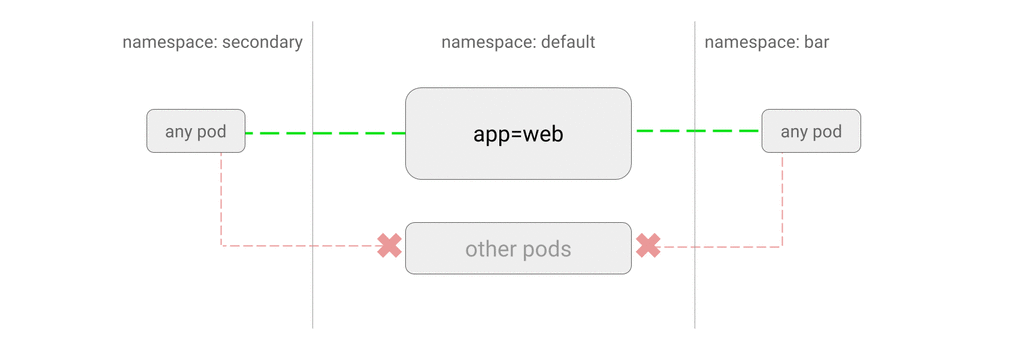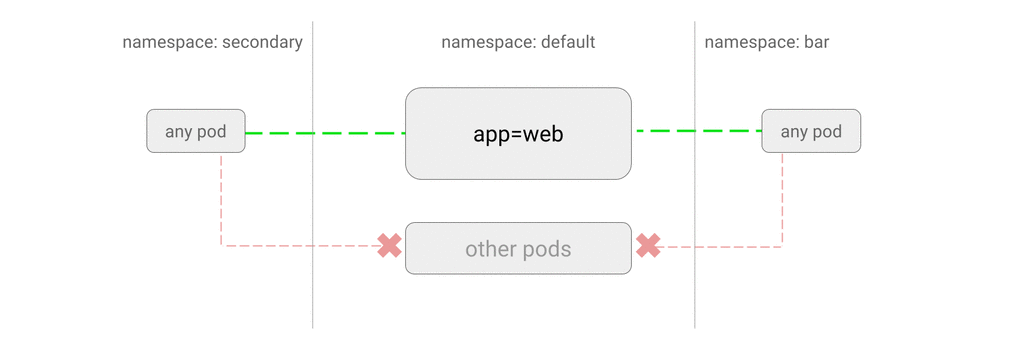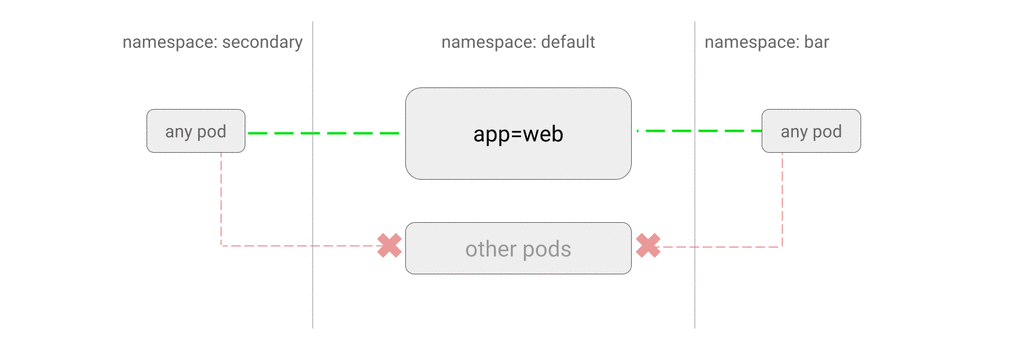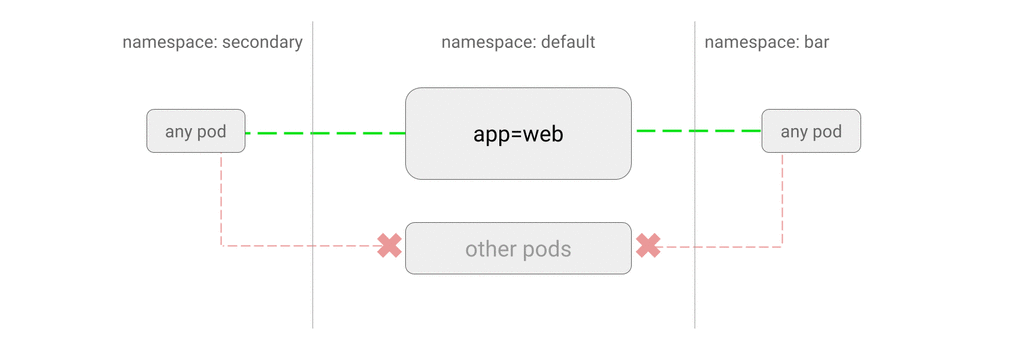
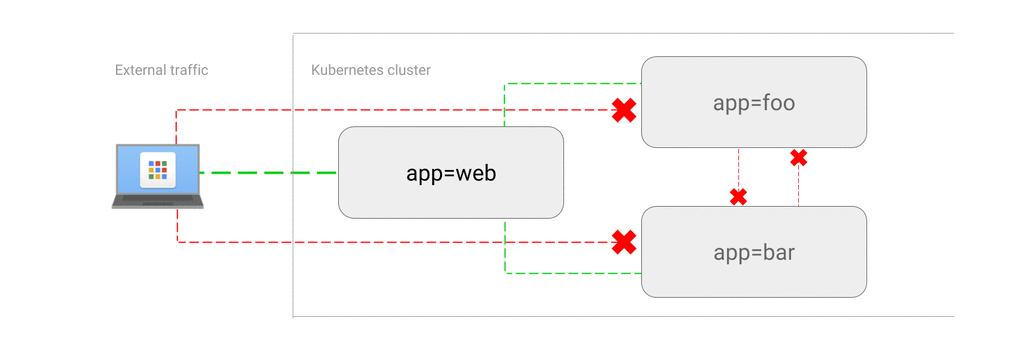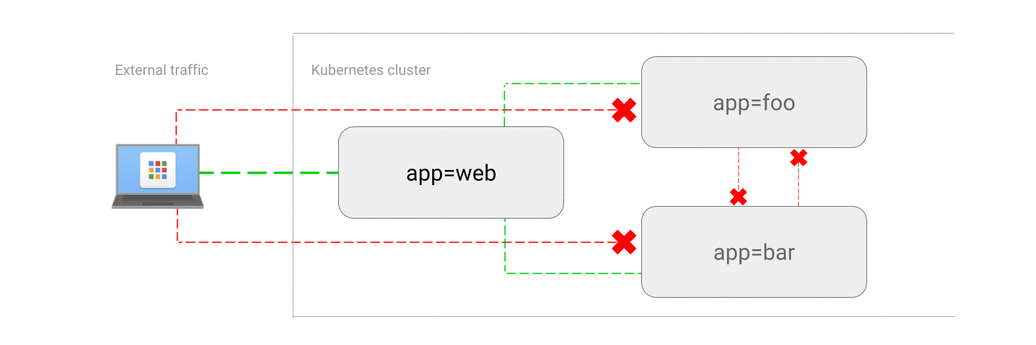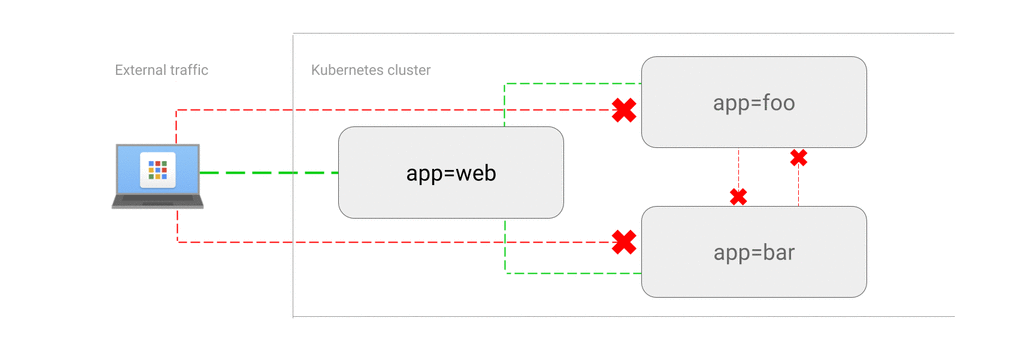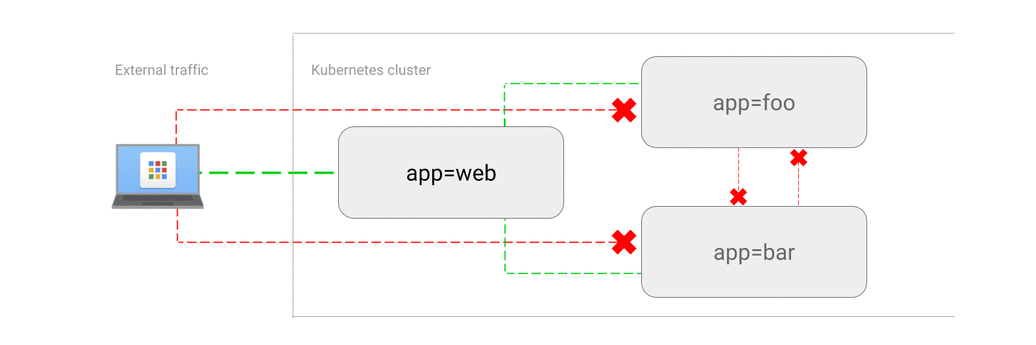
- ALLOW traffic from external clients
| # allows backend pods to have incoming traffic from frontend pods and to cassandra namespace | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: backend | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| run: backend | |
| policyTypes: | |
| - Ingress | |
| - Egress | |
| ingress: | |
| - from: | |
| - podSelector: | |
| matchLabels: | |
| run: frontend | |
| egress: | |
| - to: | |
| - namespaceSelector: | |
| matchLabels: | |
| ns: cassandra |
| # allows backend pods to have incoming traffic from frontend pods | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: backend | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| run: backend | |
| policyTypes: | |
| - Ingress | |
| ingress: | |
| - from: | |
| - podSelector: | |
| matchLabels: | |
| run: frontend |
| # deny all incoming and outgoing traffic from all pods in namespace cassandra | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: cassandra-deny | |
| namespace: cassandra | |
| spec: | |
| podSelector: {} | |
| policyTypes: | |
| - Ingress | |
| - Egress |
| # allows cassandra pods having incoming connection from backend namespace | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: cassandra | |
| namespace: cassandra | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| run: cassandra | |
| policyTypes: | |
| - Ingress | |
| ingress: | |
| - from: | |
| - namespaceSelector: | |
| matchLabels: | |
| ns: default |
| # deny all incoming and outgoing traffic from all pods in namespace default | |
| # but allow DNS traffic. This way you can do for example: kubectl exec frontend -- curl backend | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: deny | |
| namespace: default | |
| spec: | |
| podSelector: {} | |
| policyTypes: | |
| - Egress | |
| - Ingress | |
| egress: | |
| - ports: | |
| - port: 53 | |
| protocol: TCP | |
| - port: 53 | |
| protocol: UDP |
| # deny all incoming and outgoing traffic from all pods in namespace default | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: deny | |
| namespace: default | |
| spec: | |
| podSelector: {} | |
| policyTypes: | |
| - Egress | |
| - Ingress |
| allows frontend pods to communicate with backend pods | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: frontend | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| run: frontend | |
| policyTypes: | |
| - Egress | |
| egress: | |
| - to: | |
| - podSelector: | |
| matchLabels: | |
| run: backend |
| # allows frontend pods to communicate with backend pods | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: frontend | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| run: frontend | |
| policyTypes: | |
| - Egress | |
| egress: | |
| - to: | |
| - podSelector: | |
| matchLabels: | |
| run: backend |
| # all outgoing traffic if: | |
| # (destination namespace label=id=ns1 AND port=80) OR (destination pod label=id=backend in default namespace) | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: example | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| id: frontend | |
| policyTypes: | |
| - Egress | |
| egress: | |
| - to: | |
| - namespaceSelector: | |
| matchLabels: | |
| id: ns1 | |
| ports: | |
| - protocol: TCP | |
| port: 80 | |
| - to: | |
| - podSelector: | |
| matchLabels: | |
| id: backend | |
| --- | |
| # the following two NPs combined/merged are the same as the top one | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: example2a | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| id: frontend | |
| policyTypes: | |
| - Egress | |
| egress: | |
| - to: | |
| - namespaceSelector: | |
| matchLabels: | |
| id: ns1 | |
| ports: | |
| - protocol: TCP | |
| port: 80 | |
| --- | |
| apiVersion: networking.k8s.io/v1 | |
| kind: NetworkPolicy | |
| metadata: | |
| name: example2b | |
| namespace: default | |
| spec: | |
| podSelector: | |
| matchLabels: | |
| id: frontend | |
| policyTypes: | |
| - Egress | |
| egress: | |
| - to: | |
| - podSelector: | |
| matchLabels: | |
| id: backend |
I’m a DevOps/SRE/DevSecOps/Cloud Expert passionate about sharing knowledge and experiences. I am working at Cotocus. I blog tech insights at DevOps School, travel stories at Holiday Landmark, stock market tips at Stocks Mantra, health and fitness guidance at My Medic Plus, product reviews at I reviewed , and SEO strategies at Wizbrand.
Do you want to learn Quantum Computing?
Please find my social handles as below;
Rajesh Kumar Personal Website
Rajesh Kumar at YOUTUBE
Rajesh Kumar at INSTAGRAM
Rajesh Kumar at X
Rajesh Kumar at FACEBOOK
Rajesh Kumar at LINKEDIN
Rajesh Kumar at PINTEREST
Rajesh Kumar at QUORA
Rajesh Kumar at WIZBRAND

