
The following are the most popular container security tools:
- Aqua Security is a comprehensive container security platform that provides a wide range of features, including vulnerability scanning, image registry security, runtime protection, and compliance checks.
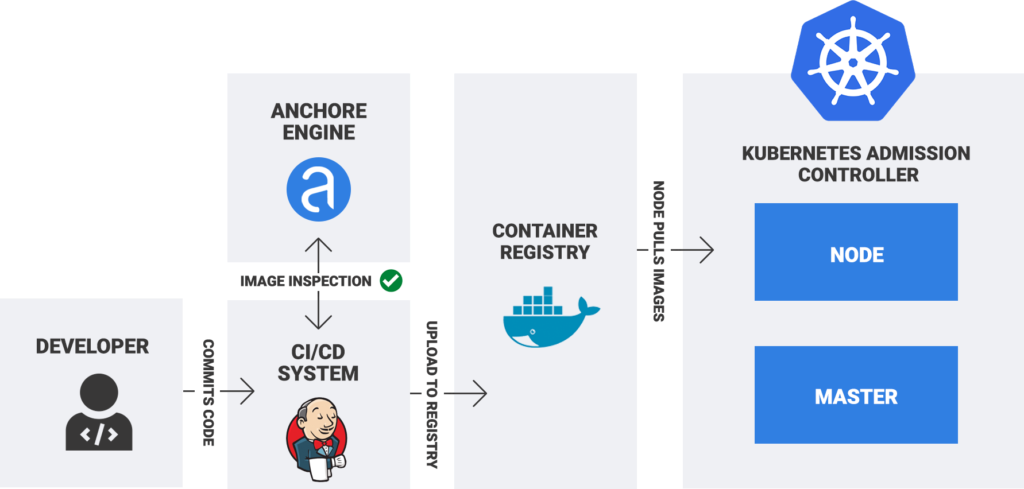
- Anchore Engine is an open-source container image scanning tool that can be used to identify vulnerabilities, misconfigurations, and other security risks.
- Cyral is a cloud-native security platform that helps organizations secure their containerized applications from development to production.
- NeuVector is a container security platform that provides a unified view of all container assets, including images, containers, and hosts.
- Snyk Container Security is a cloud-based tool that helps organizations find and fix vulnerabilities in their container images.
- Sysdig Secure is a container security platform that provides visibility and control over containerized applications.

- Twistlock is a container security platform that helps organizations prevent, detect, and respond to container security threats.
- Qualys Cloud Container Security is a cloud-based tool that helps organizations scan container images for vulnerabilities and misconfigurations.
- Red Hat Advanced Cluster Security for Kubernetes is a Kubernetes security solution that provides a comprehensive set of features for securing containerized applications.

These are just a few of the many container security tools available. The awesome tool for your organization will depend on your specific goals and requirements.
Some factors to consider when choosing a container security tool:
- The features offered by the tool.
- The size and complexity of your container environment.
- Your budget.
- Your technical expertise.
- Your compliance requirements.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

