
1. What is threat modeling?
Answer: Threat modeling is a process of identifying potential threats and vulnerabilities in a system or application.
2. Why is threat modeling important?
Answer: Threat modeling helps to identify potential security risks and vulnerabilities before they can be exploited by attackers.
3. What are the different types of threat modeling?
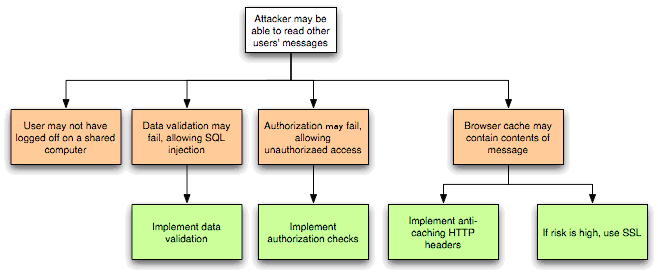
Answer: The different types of threat modeling include data flow diagrams, attack trees, and misuse cases.
4. What is a data flow diagram?
Answer: A data flow diagram is a visual representation of how data flows through a system or application.
5. What is an attack tree?
Answer: An attack tree is a hierarchical diagram that shows the different ways an attacker can exploit a system or application.
6. What is a misuse case?
Answer: A misuse case is a scenario that describes how an attacker might misuse a system or application.
7. What are the different phases of threat modeling?
Answer: The different phases of threat modeling include identification, assessment, mitigation, and validation.
8. What is the identification phase?
Answer: The identification phase involves identifying potential threats and vulnerabilities in a system or application.
9. What is the assessment phase?
Answer: The assessment phase involves evaluating the potential impact of identified threats and vulnerabilities.
10. What is the mitigation phase?
Answer: The mitigation phase involves implementing measures to reduce the risk of identified threats and vulnerabilities.
11. What is the validation phase?
Answer: The validation phase involves testing the effectiveness of implemented mitigation measures.
12. What is the difference between a threat and a vulnerability?
Answer: A threat is a potential danger to a system or application, while a vulnerability is a weakness that can be exploited by an attacker.
13. What is the difference between a risk and a threat?
Answer: A risk is the likelihood of a threat being realized, while a threat is a potential danger to a system or application.
14. What is the difference between a threat actor and an attacker?
Answer: A threat actor is anyone who has the potential to cause harm to a system or application, while an attacker is someone who actually carries out an attack.
15. What is the difference between a security control and a security countermeasure?
Answer: A security control is a measure that is put in place to prevent or mitigate security risks, while a security countermeasure is a measure that is put in place to detect or respond to security incidents.
16. What is the difference between a vulnerability assessment and a penetration test?
Answer: A vulnerability assessment is a process of identifying potential vulnerabilities in a system or application, while a penetration test is a process of attempting to exploit identified vulnerabilities to determine their impact.
17. What is the difference between a threat model and a risk assessment?
Answer: A threat model is a process of identifying potential threats and vulnerabilities in a system or application, while a risk assessment is a process of evaluating the likelihood and impact of identified threats and vulnerabilities.
18. What is the difference between a security policy and a security standard?
Answer: A security policy is a set of guidelines that define how security should be implemented in an organization, while a security standard is a set of technical requirements that must be met to comply with the security policy.
19. What is the difference between confidentiality, integrity, and availability?
Answer: Confidentiality refers to the protection of sensitive information, integrity refers to the accuracy and completeness of information, and availability refers to the accessibility of information.
20. What is the CIA triad?
Answer: The CIA triad refers to confidentiality, integrity, and availability, which are the three main objectives of information security.
21. What is a threat model template?
Answer: A threat model template is a pre-defined structure that can be used to guide the process of creating a threat model.
22. What is a threat library?
Answer: A threat library is a collection of known threats and vulnerabilities that can be used to inform the threat modeling process.
23. What is a threat actor profile?
Answer: A threat actor profile is a description of the characteristics and motivations of potential attackers.
24. What is a threat agent?
Answer: A threat agent is a specific entity that carries out an attack, such as a hacker or a virus.
25. What is a threat vector?
Answer: A threat vector is the means by which an attacker can exploit a vulnerability, such as a network connection or a software vulnerability.
26. What is a threat surface?
Answer: A threat surface is the area of a system or application that is vulnerable to attack.
27. What is a threat model diagram?
Answer: A threat model diagram is a visual representation of the threats and vulnerabilities identified during the threat modeling process.
28. What is a threat model report?
Answer: A threat model report is a document that summarizes the findings of the threat modeling process and provides recommendations for mitigating identified risks.
29. What is a threat model review?
Answer: A threat model review is a process of evaluating the effectiveness of a threat model and identifying any areas that need improvement.
30. What is a threat model workshop?
Answer: A threat model workshop is a collaborative process of creating a threat model with input from multiple stakeholders.
31. What is a threat modeling tool?
Answer: A threat modeling tool is a software application that can be used to automate the threat modeling process.
32. What is a threat modeling methodology?
Answer: A threat modeling methodology is a structured approach to the threat modeling process that provides guidance on how to identify and mitigate potential security risks.
33. What is a threat modeling framework?
Answer: A threat modeling framework is a set of guidelines and best practices for conducting the threat modeling process.
34. What is a threat modeling process?
Answer: A threat modeling process is a systematic approach to identifying and mitigating potential security risks in a system or application.
35. What is a threat modeling team?
Answer: A threat modeling team is a group of individuals who are responsible for conducting the threat modeling process.
36. What is a threat modeling project plan?
Answer: A threat modeling project plan is a document that outlines the scope, objectives, and timeline for a threat modeling project.
37. What is a threat modeling risk register?
Answer: A threat modeling risk register is a document that lists all identified threats and vulnerabilities, along with their likelihood and impact.
38. What is a threat modeling use case?
Answer: A threat modeling use case is a scenario that describes how a system or application might be used by an attacker to carry out an attack.
39. What is a threat modeling checklist?
Answer: A threat modeling checklist is a list of items that should be considered during the threat modeling process, such as data flows, access controls, and authentication mechanisms.
40. What is a threat modeling questionnaire?
Answer: A threat modeling questionnaire is a set of questions that can be used to guide the threat modeling process and ensure that all relevant information is considered.
41. What is a threat modeling training program?
Answer: A threat modeling training program is a set of courses or workshops that are designed to teach individuals how to conduct the threat modeling process.
42. What is a threat modeling certification?
Answer: A threat modeling certification is a credential that demonstrates an individual’s proficiency in conducting the threat modeling process.
43. What is a threat modeling community?
Answer: A threat modeling community is a group of individuals who share knowledge and best practices related to the threat modeling process.
44. What is a threat modeling conference?
Answer: A threat modeling conference is an event where individuals can learn about the latest trends and best practices related to the threat modeling process.
45. What is a threat modeling blog?
Answer: A threat modeling blog is a website that provides information and insights related to the threat modeling process.
46. What is a threat modeling podcast?
Answer: A threat modeling podcast is an audio program that provides information and insights related to the threat modeling process.
47. What is a threat modeling webinar?
Answer: A threat modeling webinar is an online seminar that provides information and insights related to the threat modeling process.
48. What is a threat modeling white paper?
Answer: A threat modeling white paper is a document that provides in-depth information and analysis related to the threat modeling process.
49. What is a threat modeling case study?
Answer: A threat modeling case study is a real-world example of how the threat modeling process was used to identify and mitigate potential security risks.
50. What is a threat modeling best practice?
Answer: A threat modeling best practice is a guideline or recommendation that has been proven to be effective in the threat modeling process.
Related video:

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

