What is Bitglass?

Bitglass is a cloud security platform that provides comprehensive security solutions for businesses using cloud applications, data, and devices. It offers a sort of features and functionalities, including:
- Cloud Access Security Broker (CASB): Secures access to cloud applications and protects against data leakage.
- Secure Web Gateway (SWG): Filters web traffic to block malware and phishing attacks.
- Zero Trust Network Access (ZTNA): Provides secure access to internal resources from any device or location.
- Data Loss Prevention (DLP): Prevents sensitive data from unauthorized access or exfiltration.
- Advanced Threat Protection (ATP): Detects and protects against targeted attacks and zero-day threats.
- Endpoint Protection Platform (EPP): Protects devices from malware, ransomware, and other threats.
Bitglass takes a unified approach to cloud security, consolidating various security tools into a single platform for simplified management and increased visibility. This helps businesses improve their security posture, reduce risk, and comply with data privacy regulations.
Top 10 use cases of Bitglass?
Top 10 Use Cases of Bitglass:
- Securing access to cloud applications: Bitglass helps manage user access to cloud applications, ensuring only authorized users can access sensitive data.
- Protecting against data breaches: Bitglass DLP prevents unauthorized data sharing and exfiltration, reducing the risk of data breaches.
- Enabling secure remote work: Bitglass ZTNA provides secure access to internal resources for remote employees, regardless of their location or device.
- Blocking malware and phishing attacks: Bitglass SWG filters web traffic to block malicious websites and protect users from phishing attacks.
- Enhancing endpoint security: Bitglass EPP strengthens endpoint security by protecting devices from malware, ransomware, and other threats.
- Meeting compliance requirements: Bitglass helps businesses comply with data privacy regulations like GDPR and HIPAA.
- Simplifying security management: Bitglass consolidates various security tools into a single platform, simplifying management and reducing costs.
- Improving user experience: Bitglass provides a seamless and secure user experience for accessing cloud applications and resources.
- Gaining visibility into cloud activity: Bitglass provides comprehensive logs and reports to give businesses insights into user activity and potential security threats.
- Responding to security incidents: Bitglass helps businesses quickly identify and respond to security incidents, minimizing the impact on their operations.
These are just a few of the many use cases for Bitglass. The platform can be tailored to meet the specific needs of any business, regardless of its size or industry.
What are the feature of Bitglass?
Bitglass boasts a comprehensive suite of features, catering to various cloud security needs. Here’s a breakdown of its key capabilities:
Cloud Access Security Broker (CASB):
- Visibility and Control: Gain in-depth insights into cloud app usage, user activity, and data flows. Implement granular access controls to regulate user permissions and secure sensitive data.
- Data Loss Prevention (DLP): Prevent unauthorized data exfiltration with content inspection, encryption, and watermarking across cloud apps and devices.
- Threat Protection: Defend against advanced threats like malware, phishing, and insider threats through continuous monitoring and real-time threat detection.
- Compliance Management: Simplify compliance with regulations like GDPR, HIPAA, and PCI DSS by automating compliance assessments and reporting.
Secure Web Gateway (SWG):
- Web Filtering: Block access to malicious websites and block unwanted content like gambling, violence, or social media to ensure safe and productive browsing.
- Advanced Threat Protection: Block malware, phishing attacks, and ransomware before they reach endpoints, safeguarding devices and data.
- Secure Remote Access: Enable secure access to internal resources for remote employees regardless of their location or device.
- URL Rewriting and Encryption: Enhance security and user experience by rewriting unsafe URLs and encrypting web traffic between users and websites.
Zero Trust Network Access (ZTNA):
- Least Privilege Access: Grant users access to specific applications and resources based on their role and need-to-know basis, minimizing attack surface.
- Continuous Authentication: Continuously verify user identities and device posture to enforce real-time access control and prevent unauthorized access.
- Session Recording and Replay: Record user sessions for auditing and forensics purposes to enhance security investigations and incident response.
- Device Security: Enforce device security policies, including endpoint encryption and malware protection, to secure access from unmanaged devices.
Data Loss Prevention (DLP):
- Content Inspection: Identify and classify sensitive data across cloud apps, emails, and files using advanced content inspection techniques.
- Data Encryption: Encrypt sensitive data at rest and in transit to ensure confidentiality even in case of breaches.
- Data Leakage Prevention: Block unauthorized data exfiltration through email, cloud apps, and device channels.
- Data Discovery and Classification: Automatically discover and classify sensitive data across all data stores to simplify DLP implementation.
Endpoint Protection Platform (EPP):
- Anti-Malware and Antivirus: Protect devices from malware, ransomware, and other threats through signature-based and behavior-based detection.
- Endpoint Patch Management: Automate endpoint patching to ensure timely vulnerability mitigation and prevent exploit attempts.
- Device Control and Encryption: Secure devices by enforcing device usage policies, including data encryption and peripheral control.
- Endpoint Visibility and Reporting: Gain insights into endpoint activity and security posture through detailed reports and logs.
Additional Features:
- Advanced Analytics and Reporting: Gain insights into user behavior, app usage, and security threats through comprehensive analytics and reporting tools.
- API Integration: Integrate Bitglass with existing security tools and workflows for seamless coordination and threat detection.
- Incident Response: Streamline incident response with automated workflows, forensics tools, and threat containment capabilities.
- User Education and Training: Provide users with security awareness training and education to promote safer cloud usage.
This is just a glimpse of Bitglass’s extensive feature set. The platform’s flexibility and modularity allow businesses to tailor their security posture based on their specific needs and threats.
How Bitglass works and Architecture?
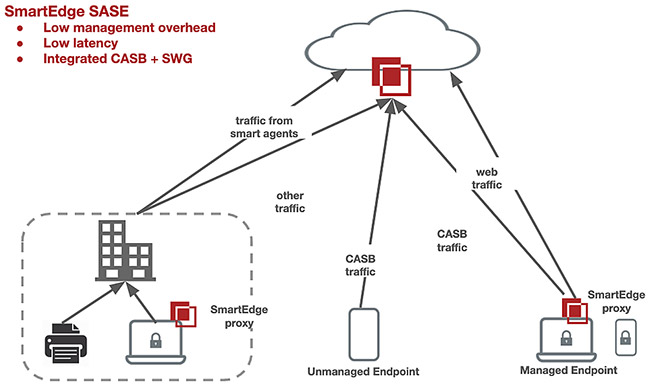
Bitglass operates through a unique Polyscale Architecture, designed for scalability, high performance, and resilience. Following is a breakdown of how it works:
1. Global Network of Data Centers:
- Bitglass boasts a geographically distributed network of data centers strategically located around the world. This ensures low latency and optimal performance for users regardless of their location.
- Each data center houses all core components of the platform, including databases, Elasticsearch nodes, DLP scanning engines, and malware engines.
2. Reverse Proxy and Data Inspection:
- When a user accesses a cloud application, the request is routed through a Bitglass reverse proxy.
- This proxy intercepts the traffic and performs various security checks:
- DLP: Scans data for sensitive information and applies configured policies.
- Threat Detection: Analyzes traffic for malware, phishing attacks, and other threats.
- Access Control: Enforces granular access controls based on user roles, policies, and context.
- If the inspection passes, the request is forwarded to the cloud application, and the response is returned to the user through the reverse proxy.
3. Data Security and Encryption:
- Bitglass offers various data security features, including:
- Data Encryption: Sensitive data is encrypted at rest and in transit using robust encryption algorithms.
- Tokenization: Sensitive data can be replaced with non-reversible tokens to further minimize risk.
- Data Loss Prevention (DLP): Prevents unauthorized data sharing and exfiltration through various techniques.
4. Scalability and Resilience:
- Bitglass’s Polyscale Architecture is designed for automatic scaling and high availability.
- Data centers can dynamically scale up or down based on resource demands, ensuring optimal performance and resource utilization.
- If a data center experiences an outage, traffic is automatically redirected to other healthy data centers, minimizing downtime and service disruptions.
5. Centralized Management and Reporting:
- Bitglass provides a centralized management console to configure security policies, monitor user activity, and generate reports.
- This centralized view allows organizations to manage their entire cloud security posture from a single location.
Benefits of Bitglass Architecture:
- Global Accessibility: Users around the world experience low latency and fast performance.
- Enhanced Security: Comprehensive data security features protect against various threats.
- Scalability and Reliability: Automatic scaling and resilience ensure high availability and optimal performance.
- Centralized Management: Simplified management and reporting for efficient security administration.
I hope this explanation provides a clear understanding of how Bitglass works and the benefits of its unique architecture.
How to Install Bitglass it?
Installing Bitglass isn’t a one-size-fits-all process, as it depends on your chosen deployment method and specific configuration needs. To provide accurate instructions, I need some additional information:
1. Deployment Method:
- Cloud-based: This is the most common approach, where you configure Bitglass through its web interface and no on-premise installation is needed.
- Hybrid: You can combine cloud-based services with on-premise components for additional control and customization.
- API Integration: You can integrate Bitglass with existing security tools and workflows via its API.
2. Desired Features and Configuration:
- Will you be using CASB, SWG, ZTNA, DLP, EPP, or a combination of features?
- Do you need to integrate with specific cloud applications or directories?
- Are there any custom configurations or policies you need to implement?
3. Technical Expertise:
- Are you comfortable with basic IT management tasks, or do you require support from Bitglass or an IT provider?
Remember, installing Bitglass can involve technical details and security configurations. Providing precise details about your situation will ensure I tailor the instructions and resources to your specific needs.
Basic Tutorials of Bitglass: Getting Started

While offering step-by-step instructions for Bitglass requires specific details about your desired configuration, I will guide you through the general onboarding process and provide resources for further learning based on your choices. Here’s an overview:
1. Account Setup:
- Sign up for a Bitglass trial or purchase a subscription.
- Access the Bitglass Administration Console with your credentials.
- Complete the initial setup wizard, providing general information and configuring basic settings.
2. Deployment Selection:
- Choose your deployment method: cloud-based, hybrid, or API integration.
- Review the official documentation and installation guides based on your chosen method.
3. Feature Configuration:
- Select the desired features you want to enable: CASB, SWG, ZTNA, DLP, EPP, or combinations.
- Configure specific settings for each feature based on your needs and security policies.
- Integrate with relevant cloud applications, directories, and other security tools (if applicable).
4. User Management:
- Create user accounts and assign roles with appropriate access permissions.
- Configure authentication methods and security policies for user access.
- Implement user education and training programs to promote secure cloud usage.
5. Monitoring and Reporting:
- Monitor user activity and application usage through comprehensive dashboards and reports.
- Analyze security events and identify potential threats to take corrective actions.
- Leverage reporting tools to gain insights into your cloud security posture and compliance adherence.
Note:
- The provided steps are a general outline. Specific instructions will vary depending on your chosen features, configurations, and deployment method.
- Utilize the extensive resources provided by Bitglass to tailor your setup and address specific needs.
- Don’t hesitate to reach out to Bitglass customer support for personalized assistance and expert guidance.

👤 About the Author
Rahul is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps. Driven by a love for innovation and continuous improvement, Rahul enjoys helping engineers and organizations embrace automation, reliability, and intelligent IT operations. Connect with Rahul and stay up-to-date with the latest in tech!
🌐 Connect with Rahul
-
Website: MotoShare.in
-
Facebook: facebook.com/DevOpsSchool
-
X (Twitter): x.com/DevOpsSchools
-
LinkedIn: linkedin.com/company/devopsschool
-
YouTube: youtube.com/@TheDevOpsSchool
-
Instagram: instagram.com/devopsschool
-
Quora: devopsschool.quora.com
-
Email: contact@devopsschool.com

