What is Demisto?

Demisto is a security orchestration, automation, and response (SOAR) platform designed to streamline and automate security incident management and response processes. It helps security teams efficiently manage and respond to security incidents by integrating with various security tools and automating workflows.
Demisto’s capabilities are designed to enhance the efficiency and effectiveness of security operations teams by reducing response times, automating repetitive tasks, and providing a centralized platform for incident management and collaboration.
Top 10 use cases of Demisto:
Here are the top 10 use cases of Demisto:
- Incident Triage and Enrichment: Demisto collects and correlates information from multiple sources to provide context on security incidents, helping analysts quickly assess the severity and impact of an incident.
- Incident Workflow Automation: It automates incident response workflows, enabling the automatic execution of predefined actions in response to security alerts or incidents.
- Alert Management: Demisto centralizes security alerts from various sources, deduplicates them, and prioritizes them based on predefined criteria, reducing alert fatigue.
- Threat Intelligence Integration: Demisto integrates with threat intelligence feeds and platforms to enrich incident data with threat context, indicators of compromise (IOCs), and known attack patterns.
- Playbook Creation: Security teams can create custom playbooks to define step-by-step response procedures for specific types of incidents or threats.
- Orchestration of Security Tools: Demisto orchestrates the actions of security tools and technologies, such as firewalls, SIEM systems, and endpoint detection and response (EDR) solutions, to respond to incidents.
- User and Entity Behavior Analytics (UEBA) Integration: Demisto integrates with UEBA solutions to analyze user and entity behaviors and correlate them with security alerts to detect insider threats and anomalous activities.
- Forensics and Investigation: Security analysts can use Demisto to perform digital forensics, investigate incidents, and gather evidence for further analysis.
- Incident Reporting and Documentation: Demisto provides incident reporting and documentation features, helping teams create detailed incident reports for compliance and post-incident analysis.
- Compliance and Reporting: Demisto helps organizations maintain compliance by automating compliance checks, audits, and reporting tasks.
- Incident Tracking and Management: It tracks the lifecycle of incidents, from initial detection and analysis to containment, eradication, and recovery.
- Integration with SIEM and Log Management: Demisto can integrate with SIEM solutions and log management platforms to ingest and analyze log data for incident detection and response.
What are the feature of Demisto?
Demisto is a comprehensive security orchestration, automation, and response (SOAR) platform with a range of features and capabilities to help organizations streamline and automate their security incident management and response processes. Here are the key features of Demisto:
- Incident Triage and Enrichment: Demisto collects and aggregates alerts and incidents from various sources, enriching them with contextual information from internal and external sources.
- Playbook Automation: Demisto allows the creation of customizable playbooks that define step-by-step workflows for incident response and automate actions across different security tools and systems.
- Incident Workflow Management: It provides tools for tracking, managing, and prioritizing incidents, ensuring that security teams are focused on the most critical issues.
- Threat Intelligence Integration: Demisto integrates with threat intelligence feeds to automatically correlate and enrich incident data with relevant threat intelligence information.
- Alert Management: The platform centralizes alerts from multiple security tools, deduplicates them, and assigns priorities, reducing alert fatigue and enhancing response efficiency.
- Automated Response: Demisto automates incident response actions, enabling the execution of predefined tasks and workflows in response to security incidents.
- Custom Integrations: Users can create custom integrations with security tools and systems using Demisto’s integration framework, ensuring compatibility with their existing technology stack.
- Machine Learning and AI: Demisto incorporates machine learning and artificial intelligence to help identify and respond to threats more effectively.
- User and Entity Behavior Analytics (UEBA) Integration: It integrates with UEBA solutions to monitor and detect anomalous user and entity behaviors.
- Forensics and Investigation: Demisto provides tools for digital forensics and evidence gathering during incident investigations.
- Incident Reporting: The platform offers incident reporting and documentation capabilities to create detailed incident reports for compliance and analysis.
- Compliance Automation: Demisto can automate compliance checks, audits, and reporting tasks to ensure adherence to regulatory requirements.
How Demisto works and Architecture?
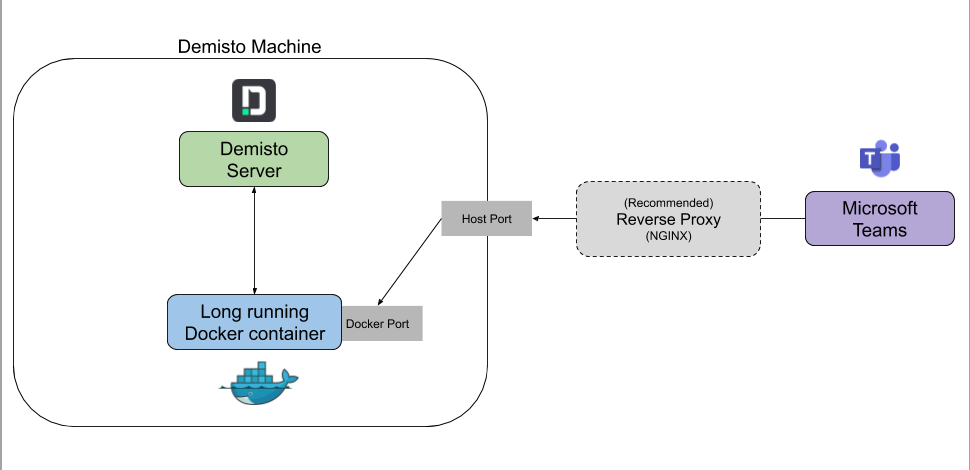
Demisto’s architecture and workflow can be summarized as follows:
1. Data Ingestion: Demisto ingests data from various sources, including security tools, SIEM systems, threat intelligence feeds, and user inputs.
2. Incident Triage: Demisto centralizes and triages incoming alerts and incidents, applying predefined rules and logic to prioritize them.
3. Context Enrichment: The platform enriches incidents with additional context, such as threat intelligence, asset information, and historical data.
4. Playbook Execution: Demisto executes playbooks, which are predefined workflows that guide incident response activities, including automated actions and human-driven tasks.
5. Orchestration: Demisto orchestrates actions across security tools and systems, triggering responses such as containment, mitigation, and evidence collection.
6. Collaboration: Demisto enables collaboration among security team members and external stakeholders by providing a centralized incident management platform.
7. Reporting and Documentation: The platform supports incident reporting and documentation for compliance and post-incident analysis.
8. Continuous Improvement: Demisto allows organizations to continuously refine and optimize their incident response processes through automation and feedback.
Demisto’s architecture is designed to be flexible and scalable, allowing organizations to integrate with their existing security stack and adapt to evolving threats and technologies. It offers a unified interface for managing security incidents and responding to them efficiently.
How to Install Demisto?
To install Sysdig Secure, you will need to:
- Create a Sysdig account and obtain an access key.
- Install the Sysdig Agent on your hosts and containers.
- Install the Sysdig Monitor and Sysdig Secure components.
- Connect your cloud accounts to Sysdig Secure.
Installing the Sysdig Agent
The Sysdig Agent can be installed on a variety of platforms, including Linux, Windows, macOS, and Kubernetes. To install the Sysdig Agent, you can use the following steps:
- Download the Sysdig Agent package from the Sysdig website.
- Install the Sysdig Agent package on your hosts and containers.
Installing the Sysdig Monitor and Sysdig Secure components
The Sysdig Monitor and Sysdig Secure components can be installed on-premises or in the cloud. To install the Sysdig Monitor and Sysdig Secure components, you can use the following steps:
- Download the Sysdig Monitor and Sysdig Secure packages from the Sysdig website.
- Install the Sysdig Monitor and Sysdig Secure packages on your servers.
Connecting your cloud accounts to Sysdig Secure
Sysdig Secure can be connected to a variety of cloud accounts, including AWS, Azure, and GCP. To connect your cloud accounts to Sysdig Secure, you can use the following steps:
- Log in to the Sysdig Secure web console.
- Click on the Integrations tab.
- Click on the Add Account button and select your cloud provider.
- Follow the on-screen instructions to connect your cloud account to Sysdig Secure.
Once you have installed the Sysdig Agent and Sysdig Secure components, and connected your cloud accounts to Sysdig Secure, you can start using Sysdig Secure to monitor and secure your infrastructure.
Some additional tips for installing Sysdig Secure:
- Make sure that your system meets the minimum requirements for Sysdig Secure. You can find the minimum requirements on the Sysdig website.
- If you are installing Sysdig Secure on a production system, be sure to test Sysdig Secure thoroughly before deploying it.
- If you have any questions or problems installing Sysdig Secure, please contact Sysdig Support for assistance.
Basic Tutorials of Demisto: Getting Started

The following steps are the basic tutorials of Demisto:
Creating a new Demisto playbook:
- Log in to the Cortex XSOAR web console.
- Click on the Playbooks tab.
- Click on the Create Playbook button.
- Enter a name and description for the new playbook.
- Select the type of playbook you want to create.
- Configure the playbook steps.
- Click on the Create Playbook button.
Running a Demisto playbook:
- Click on the Playbooks tab.
- Click on the playbook you want to run.
- Click on the Run Playbook button.
Viewing Demisto playbook results:
- Click on the Playbooks tab.
- Click on the playbook you want to view the results for.
- The playbook results will be displayed.
Example of a simple Demisto playbook:
name: "My Playbook"
description: "This playbook prints a message to the console."
steps:
- name: "Print Message"
command: "echo 'Hello, world!'"
type: "local"
To run this playbook, you would follow these steps:
- Log in to the Cortex XSOAR web console.
- Click on the Playbooks tab.
- Click on the My Playbook playbook.
- Click on the Run Playbook button.
The playbook will then print the message “Hello, world!” to the console.
You can also use Demisto playbooks to automate more complex security tasks, such as investigating security incidents or responding to threats. For example, you could create a playbook to automatically quarantine a compromised host or to remediate a security vulnerability.
Some additional tips for using Demisto:
- Demisto provides a variety of integrations with security tools and platforms. This allows you to automate workflows across your security stack.
- Demisto provides a library of pre-built playbooks that you can use to automate common security tasks. This can save you time and help you to improve your security posture.
- Demisto is a powerful tool that can help you to automate your security operations. However, it is important to note that Demisto is not a replacement for security expertise. You should always carefully review and test any playbooks that you create or use.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

