What is LogRhythm?

LogRhythm is a cybersecurity information and event management (SIEM) platform that offers a wide range of features and capabilities for monitoring, detecting, and responding to security threats and incidents.
LogRhythm’s comprehensive set of features makes it a valuable SIEM solution for organizations looking to strengthen their cybersecurity defenses, detect and respond to threats effectively, and maintain compliance with regulatory requirements.
Top 10 use cases of LogRhythm:
Here are the top 10 use cases of LogRhythm:
- Threat Detection and Alerting: LogRhythm continuously monitors network and system activity in real-time, analyzing logs and events to detect suspicious or malicious behavior. It generates alerts and notifications when potential threats are identified.
- Incident Investigation: Security teams can use LogRhythm to investigate security incidents by analyzing historical log and event data. This helps in identifying the root cause of incidents and understanding their impact.
- Security Event Correlation: LogRhythm’s correlation engine connects data from various sources to identify complex attack patterns and advanced threats. It helps in detecting threats that may evade individual security controls.
- Compliance Management: LogRhythm assists organizations in meeting regulatory compliance requirements by providing predefined compliance reports and automating compliance monitoring.
- User and Entity Behavior Analytics (UEBA): LogRhythm can analyze user and entity behavior to detect anomalies and potentially malicious activities. This is crucial for identifying insider threats and compromised accounts.
- Vulnerability Management: LogRhythm integrates with vulnerability assessment tools to prioritize and remediate vulnerabilities based on their potential impact on the organization’s security posture.
- Advanced Analytics: LogRhythm offers advanced analytics capabilities, including machine learning and behavioral analytics, to detect threats and anomalies that may evade traditional detection methods.
- Incident Response Orchestration: It supports incident response orchestration by providing workflow automation tools that streamline the response process and ensure timely actions are taken.
- Log Management and Analysis: LogRhythm serves as a centralized log management platform, collecting, storing, and analyzing logs and events from a wide range of sources, including network devices, servers, and applications.
- Cloud Security Monitoring: Organizations can use LogRhythm to extend their security monitoring to cloud environments by integrating with cloud platforms and services to analyze log and event data.
- Insider Threat Detection: LogRhythm assists in identifying insider threats by monitoring user activity and behavior to detect unusual or suspicious actions.
- IoT Security: As the Internet of Things (IoT) continues to grow, LogRhythm can be used to monitor and secure IoT devices and networks by analyzing their activity and behavior.
- Endpoint Detection and Response (EDR) Integration: LogRhythm can integrate with EDR solutions to enhance endpoint security by correlating endpoint data with network and system events.
- Network Traffic Analysis: LogRhythm provides network traffic analysis capabilities to monitor and analyze network activity, identify unauthorized access, and detect anomalies.
- Forensic Analysis: LogRhythm supports forensic analysis by providing tools for examining security incidents in detail, helping organizations understand how an attack occurred and what data may have been compromised.
What are the feature of LogRhythm?
LogRhythm is a robust security information and event management (SIEM) platform that offers a wide range of features and capabilities to help organizations monitor, detect, investigate, and respond to security threats and incidents. Here are some key features of LogRhythm, along with an overview of how it works and its typical architecture:
Key Features of LogRhythm:
- Log and Event Data Collection: LogRhythm can collect and normalize log and event data from various sources, including network devices, servers, endpoints, applications, and cloud services.
- Real-Time Data Analysis: It provides real-time analysis of incoming logs and events, using predefined and custom rules to detect suspicious or malicious activities.
- Event Correlation and Anomaly Detection: LogRhythm’s correlation engine correlates data from multiple sources to identify complex attack patterns and prioritize security incidents based on their potential impact. It also employs anomaly detection to identify unusual behavior.
- Alerting and Notifications: The platform generates alerts and notifications when potential security threats or policy violations are detected, allowing security teams to respond promptly.
- Incident Investigation: LogRhythm offers tools for incident investigation, enabling security analysts to explore and analyze historical log and event data to understand the scope and impact of security incidents.
- User and Entity Behavior Analytics (UEBA): It can profile user and entity behavior to detect deviations from normal patterns, helping organizations identify insider threats or compromised accounts.
- Vulnerability Management Integration: LogRhythm integrates with vulnerability assessment tools to prioritize and remediate vulnerabilities based on their risk level and potential impact.
- Compliance Management: The platform assists organizations in meeting regulatory compliance requirements by providing predefined compliance reports and automating compliance monitoring.
- Security Orchestration and Automation: LogRhythm supports security orchestration and automation by enabling the creation of custom workflows and automated response actions.
- Custom Dashboards and Reports: Users can create custom dashboards and reports to visualize and present security data in a way that meets their specific needs.
How LogRhythm works and Architecture?
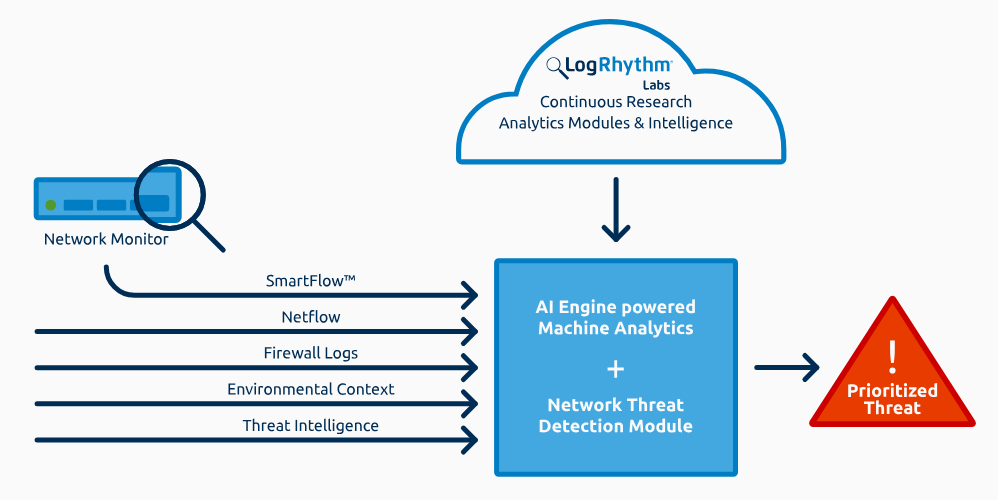
- Data Collection: LogRhythm collects log and event data from various sources, such as network devices, servers, endpoints, applications, and cloud services. This data is sent to LogRhythm’s data processing components.
- Data Normalization: The collected data is normalized to ensure it is in a consistent format and can be analyzed effectively. This step involves converting data from various sources into a common structure.
- Real-Time Analysis: LogRhythm analyzes incoming data in real-time using predefined and custom rules to detect security threats and anomalies.
- Correlation and Anomaly Detection: The correlation engine correlates data from multiple sources to identify patterns and prioritize incidents. It also employs anomaly detection techniques to detect unusual behavior.
- Alerting and Notifications: When a potential security incident is detected, LogRhythm generates alerts and notifications for security analysts to investigate. Notifications can be sent through various channels, such as email or SMS.
- Incident Investigation: Security analysts use LogRhythm’s tools to investigate incidents, analyze historical data, and determine the root cause of security events.
LogRhythm Architecture:
LogRhythm’s architecture typically consists of the following components:
- Data Collectors: Data collectors, also known as agents, are responsible for collecting log and event data from various sources, including network devices, servers, and applications.
- Data Processing: Data processing components normalize and parse the collected data. They analyze the data in real-time, correlate events, and detect anomalies.
- Correlation Engine: The correlation engine is responsible for identifying complex attack patterns and advanced threats by correlating data from different sources.
- Alerting and Notification: LogRhythm generates alerts and notifications when security threats or policy violations are detected. It can notify security teams through various channels.
- User Interface: LogRhythm provides a user-friendly interface for security analysts to investigate incidents, create custom dashboards, and generate reports.
- Data Storage: LogRhythm stores normalized data and indexed data for historical analysis, reporting, and compliance purposes.
- Reference Data: LogRhythm uses reference data, such as threat intelligence feeds and vulnerability information, to enrich and contextualize security events.
- External Integrations: LogRhythm can integrate with external systems, such as ticketing systems, other SIEM solutions, and threat intelligence feeds, to enhance its capabilities.
LogRhythm’s architecture is designed for scalability and high availability, allowing organizations to handle large volumes of data and ensure continuous monitoring and detection of security threats. It provides a comprehensive platform for security operations and incident response.
How to Install LogRhythm?
To install LogRhythm, you will need the following:
- A LogRhythm Platform Manager or XM server
- A LogRhythm database server
- A LogRhythm license
- A network connection
- A web browser
To install LogRhythm:
- Download the LogRhythm installation package from the LogRhythm website.
- Extract the LogRhythm installation package to a directory on your server.
- Open a terminal window and navigate to the directory where you extracted the LogRhythm installation package.
- Run the following command to start the LogRhythm installation process:
./install.sh- Follow the on-screen instructions to complete the installation process.
Once the installation process is complete, you will need to configure LogRhythm.
Some additional tips for installing LogRhythm:
- Make sure that your network has the required bandwidth and latency to support LogRhythm.
- If you are installing LogRhythm in a production environment, it is recommended to follow the LogRhythm hardening guide to secure your installation.
- You can also find a variety of tutorials and other resources on the LogRhythm website.
LogRhythm is a powerful security information and event management (SIEM) platform that can help you to improve your security posture by helping you to collect, analyze, and respond to security threats. By following the steps above, you can learn how to install LogRhythm and start using it to improve your security posture.
Basic Tutorials of LogRhythm: Getting Started

The following is the basic tutorial on how to use LogRhythm to improve your security posture:
1. Getting Started
- Install LogRhythm. Follow the instructions on the LogRhythm website to install LogRhythm on your servers.
- Configure LogRhythm. Once LogRhythm is installed, you need to configure it to collect, analyze, and respond to security threats. This includes adding data sources, creating rules, and setting up alerts.
- Learn the basics of LogRhythm. LogRhythm is a complex platform, but there are some basic concepts that you need to understand in order to use it effectively. The LogRhythm documentation and training resources can help you learn about these concepts.
- Review the LogRhythm documentation. The LogRhythm documentation provides a comprehensive overview of the platform and its features. Be sure to review the documentation to understand how LogRhythm can be used to improve your security posture.
- Take advantage of LogRhythm training resources. LogRhythm offers a variety of training resources, including online courses, in-person training, and self-paced training. Taking advantage of these resources can help you learn how to use LogRhythm more effectively.
2. Collecting Data
- Identify the data sources that you want to collect. LogRhythm can collect data from a variety of sources, including SIEMs, firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS). You need to identify the data sources that you want to collect in order to configure LogRhythm to collect the data.
- Configure LogRhythm to collect the data. LogRhythm provides a variety of tools and wizards to help you configure data collection. You can use these tools and wizards to configure LogRhythm to collect the data from the sources that you identified.
- Verify that LogRhythm is collecting the data that you need. You can use the LogRhythm Console to verify that LogRhythm is collecting the data that you need. The LogRhythm Console provides a variety of tools and widgets to help you verify data collection.
3. Analyzing Data
- Create rules to analyze the data. LogRhythm provides a variety of rules that you can use to analyze the data that you collect. You can also create your own rules. Rules can be used to identify security threats, investigate security incidents, and monitor your security posture.
- Use the LogRhythm Console to analyze the data. The LogRhythm Console provides a variety of tools and widgets to help you analyze the data. You can use these tools and widgets to identify security threats, investigate security incidents, and monitor your security posture.
- Generate reports to summarize the data. LogRhythm provides a variety of reports that you can use to summarize the data. You can also create your own reports. Reports can be used to track your security posture over time, identify trends in your security data, and generate compliance reports.
4. Responding to Threats
- Use the LogRhythm Console to identify and investigate threats. The LogRhythm Console provides a variety of tools and widgets to help you identify and investigate threats. You can use these tools and widgets to investigate security incidents, identify the root cause of security incidents, and determine the best course of action to take.
- Use the LogRhythm Console to respond to threats. The LogRhythm Console provides a variety of tools and wizards to help you respond to threats. You can use these tools and wizards to contain security incidents, eradicate the threats that caused the security incidents, and recover from the security incidents.
- Work with other security tools to respond to threats more effectively. LogRhythm can be integrated with other security tools to help you respond to threats more effectively. For example, you can integrate LogRhythm with a security orchestration, automation, and response (SOAR) platform to automate the response to security incidents.
Some additional tips for using LogRhythm to improve your security posture:
- Use the LogRhythm community to get help and support from other LogRhythm users.
- Take advantage of LogRhythm support. LogRhythm offers a variety of support options, including paid support and community support.
- Regularly review your LogRhythm configuration and rules. It is important to regularly review your LogRhythm configuration and rules to ensure that they are still meeting your needs.
LogRhythm is a powerful SIEM platform that can help you to improve your security posture by helping you to collect, analyze, and respond to security threats. By following the steps above, you can learn how to use LogRhythm to improve your security posture.

👤 About the Author
Ashwani is passionate about DevOps, DevSecOps, SRE, MLOps, and AiOps, with a strong drive to simplify and scale modern IT operations. Through continuous learning and sharing, Ashwani helps organizations and engineers adopt best practices for automation, security, reliability, and AI-driven operations.
🌐 Connect & Follow:
- Website: WizBrand.com
- Facebook: facebook.com/DevOpsSchool
- X (Twitter): x.com/DevOpsSchools
- LinkedIn: linkedin.com/company/devopsschool
- YouTube: youtube.com/@TheDevOpsSchool
- Instagram: instagram.com/devopsschool
- Quora: devopsschool.quora.com
- Email– contact@devopsschool.com

